Introduction
CrackMapExec, also known as CME, is a helpful tool for checking how safe Windows networks are, especially during internal pentesting assessments.
It’s used to explore networks, finding out what computers are connected and what services they’re running. It also looks for shared folders, user accounts, and groups within the network.
In this article, we’ll talk about the first steps in gathering information about a network, particularly focusing on finding details from machines that allow anonymous access. We’ll use examples from Hack The Box Academy to illustrate.
Enumerating SMB Information
This tool collects important info from SMB (Server Message Block) connections.
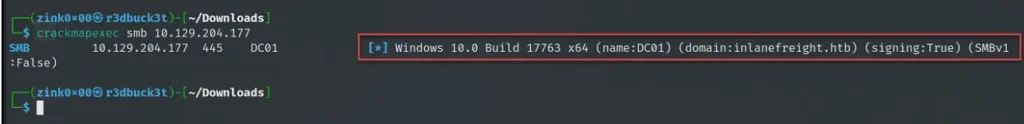
It grabs details like the machine’s full domain name to see if it’s part of a domain or standalone, what version of Windows it’s running (like 32-bit or 64-bit), and which version of SMB it’s using.
It can also tell us if SMB signing, a security feature, is turned on. This helps us figure out which machines might be vulnerable to attacks like stealing login info or relaying messages.
To get all this SMB info, just run crackmapexec, tell it to use the SMB protocol, and give it the IP addresses (either in a file or using CIDR ranges).
crackmapexec smb 10.129.204.177
Enumerating Users Accounts
During the first phase of checking out the network, it’s important to find out about user accounts.
We can make a list of users from computers that allow anyone to connect without logging in, and then try to guess their passwords.
Alternatively, we can search for accounts vulnerable to a type of attack called AS-REP, which we can crack to get into the domain.
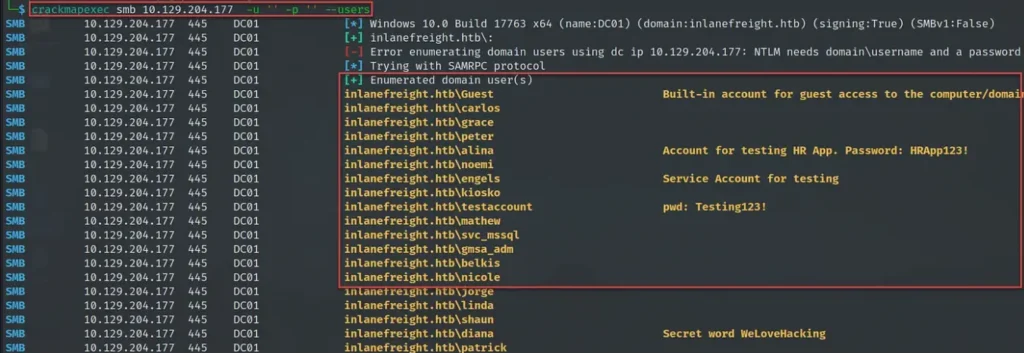
To find out about users, we use crackmapexec with the option “–users” to list all the users on the computers we’re interested in, and we save that list to a file using “–export.”
The tool doesn’t have a specific setting for anonymous connections.
Instead, we can just leave the username and password fields empty when we run it (“-u” for username and “-p” for password).
crackmapexec smb 10.129.204.177 -u '' -p '' --users
One thing I appreciate about the “–users” option is that it doesn’t just show the usernames, but also gives us extra details like descriptions. Sometimes, we might find useful credentials or learn about the type of account, like if it’s a service account.
Enumerating Password Policies
During network pentests, a common mistake is forgetting about the password rules when trying to crack passwords. This can lead to accounts getting locked or causing chaos in the network 🔥.
Understanding the password rules, especially things like how many failed attempts before a lockout, how complex passwords need to be, and how long they can be, is really important for planning password attacks.
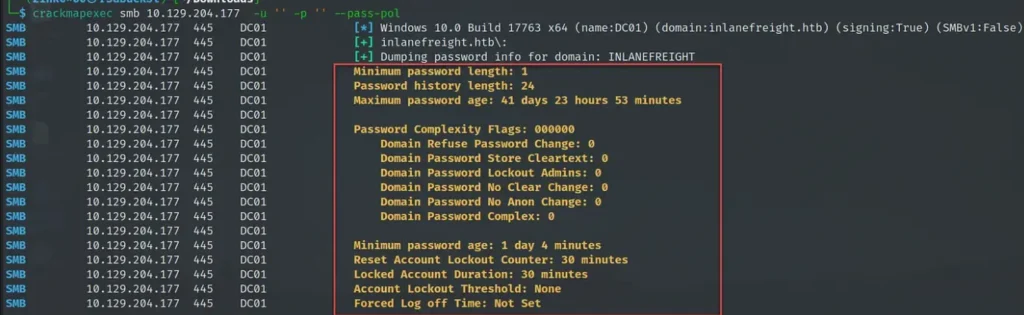
To find out about the password rules, we use crackmapexec with the “–pass-pol” option.
In the example below, the lockout threshold is set to “None,”
which means accounts won’t get locked no matter how many wrong passwords are tried.
In real situations, some organizations might set the threshold low, like 3 or 5 failed attempts.
while others go for higher numbers, like 10 or more, to avoid accidental lockouts.
crackmapexec smb 10.129.204.177 -u '' -p '' --pass-pol
Enumerating SMB Shares
Shared folders are gold mines for finding important stuff. You might stumble upon confidential files, financial records, or even special user logins that can help you dig deeper into the network.
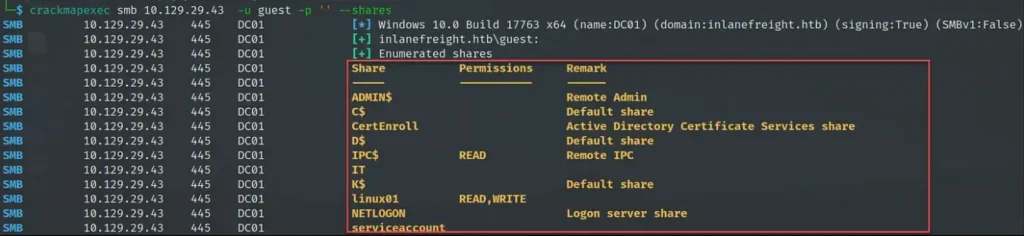
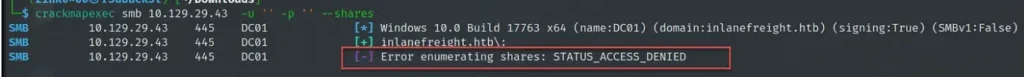
To see what shared folders are available, use crackmapexec with the “–shares” option. When you do this, you’ll need to put in a username, like “guest,” using the “-u” option. Just remember, the tool won’t work if you leave the username blank, so pick any username to get it going.
crackmapexec smb 10.129.29.43 -u guest -p '' --shares
The screenshot below displays an “access denied” error that occurs when leaving the username field blank.
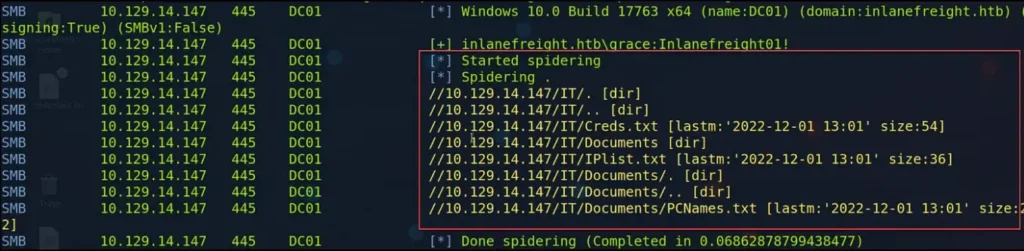
Additionally, to show the files and folders in a shared folder, we can use the options “–spider” with the name of the share and “–regex .” In the example provided, we displayed the contents of the “IT” share.
crackmapexec smb 10.129.203.121 -u guest -p '' --spider IT --regex .
Conclusion
As a pentester, having the CrackMapExec tool is invaluable for understanding a network and its hosts.
In future articles, we’ll delve into more ways to use the tool for authenticated enumeration, password spraying, and relay attacks.
Thanks for reading!
Also Read: Windows Privilege Escalation with DNSAdmins Group


