Introduction
In this post, you will learn what is dnsrecon and how does the tool work and In additu=ion I have given extra information about the tool and I have also made a video of DNS recon to check it out 👇🏾.
Video:
What is dnsrecon?
Dnsrecon is an information-gathering tool widely used by the pentester and those who work in the red team and also by the hackers. The DNS recon stands for “Domain name service reconnaissance” So If you like my blog subscribe to our newsletter.
In simple, the DNS recon is used to gather DNS related information.
Also Read: DNS enum from scratch to pro
Advertisement
Who developed dns recon tool
The tool was developed by Carlos Perez and many others contributed to GitHub and the author seems to be cool but is he? Check out his site if he is cool or not. Nor Iam cool ????
What all the the dnsrecon can do
- NS Records for Zone Transfers
- Informations like (MX, SOA, NS, A, AAAA, SPF and TXT)
- SRV record enumerations
- Brute Force subdomain
- Enumerate Common mDNS records in the Local Network Enumerate Hosts and Subdomains using Google
Advertisement
Very much useful commands for DNSrecon
- -h, –help: show this help message and exit
- -d DOMAIN, –domain: Target domain
- -n NS_SERVER, –name_server: Domain server to use.
- -r RANGE, –range: IP range for reverse lookup brute force in formats
- -D DICTIONARY, –dictionary DICTIONARY: Dictionary file of subdomain and hostnames to use for Bruteforce
- -f: Filter out of brute force domain-lookup
- -t TYPE, –type TYPE Type of enumeration to perform
- –threads THREADS Number of threads to use in reverse lookups
- -v: Enable verbosely
Advertisement
How does the dnsrecon tool work?
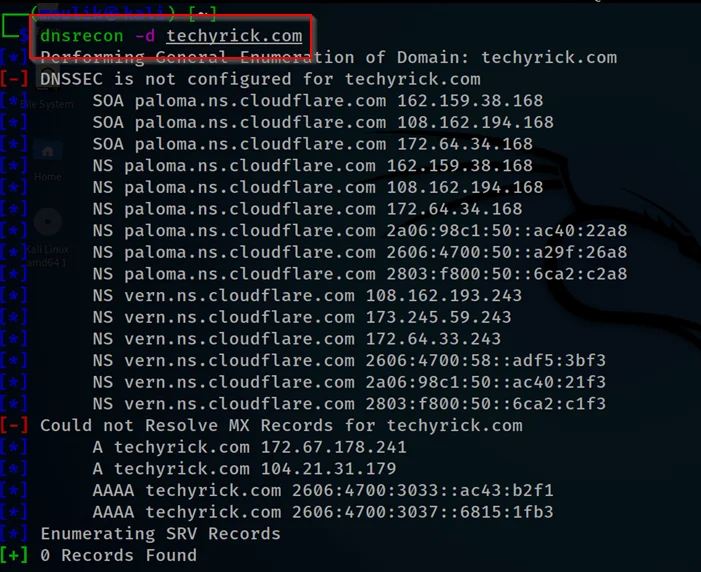
Example1: Default scan
Doing a normal domain search gathers cert and normal information
dnsrecon -d techyrick.com
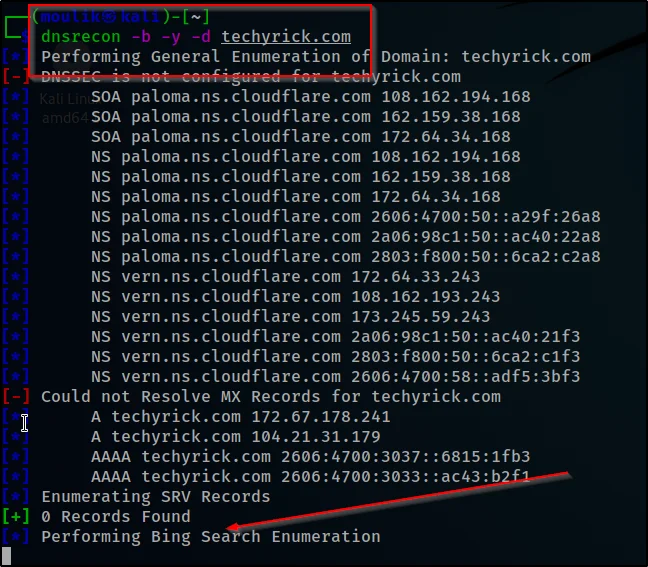
Example2: Bing scan
Let’s gather information from a specific search engine here let’s go with Yandex and bing
dnsrecon -b -y -d techyrick.com
Example3: IP range
Doing a reverse lookup using IP ranges, ????
dnsrecon -d techyrick.com -r 108.162.194.168-162.159.38.168

Example4: Brute force
Okay, get ready now we are doing DNS brute force attack ????
dnsrecon -d techyrick.com -D /usr/share/wordlists/metasploit/unix_passwords.txt -t brt -v

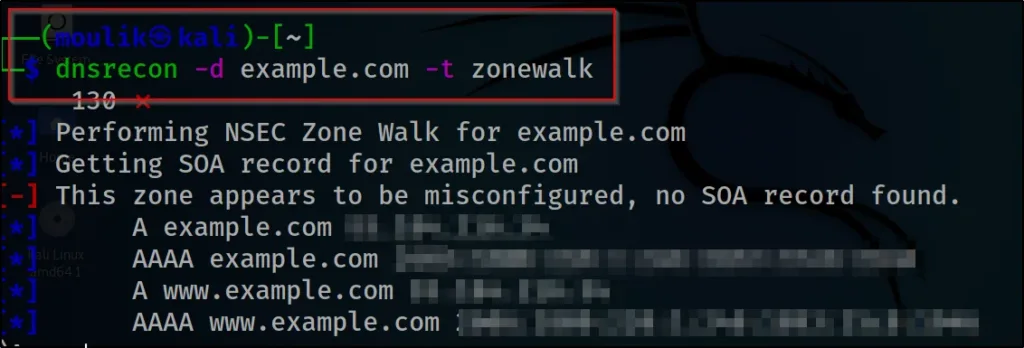
Example5: Zonewalk
In an example, 5 let’s see how to perform a zone walking
dnsrecon -d example.com -t zonewalk
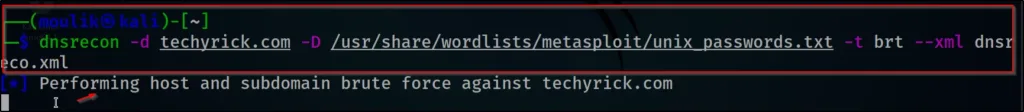
Example6: Save output
Finally, let’s see how to save the file ????
dnsrecon -d example.com -D /usr/share/wordlists/dnsmap.txt -t std --xml dnsrecon.xml
Conclusion
According to my knowledge, this is the best tool for DNS enumeration and we have already seen a DNS enum tool called dns enum which I am not satisfied with. So, compared to dnsenum tool DNS recon is best.
Advertisement
Also Read: certificate information gathering using crt.sh
Also Read: Weleakinfo site info gathering





You made several good points there. I did a search on the matter and found a good number of people will consent with your blog.
Thanks man by the way your IP is 172.255.125.167