Introduction
Feroxbuster is a powerful and versatile tool that helps uncover hidden directories and files on web servers through brute-force scanning. Widely used in penetration testing and security assessments, it plays a crucial role in identifying concealed paths and resources that could pose potential vulnerabilities. In this guide, we’ll explore the various tasks you can efficiently accomplish with Feroxbuster, showcasing its utility in enhancing web server security.
Lab setup
Target Machine: 192.168.1.4
Attacker Machine: 192.168.1.31 (running Kali Linux)
Once the web server is configured on the target machine, the next step is to perform enumeration using Feroxbuster on the attacker machine. First, ensure Feroxbuster is installed on your Kali Linux system. With the setup complete, you’re ready to uncover hidden directories, files, and other resources that may provide valuable insights into the target’s web server structure. Let’s dive into the process of using Feroxbuster for effective enumeration.
Also Read: Dirb full tutorial for beginners from noob to pro | 2024
Installation
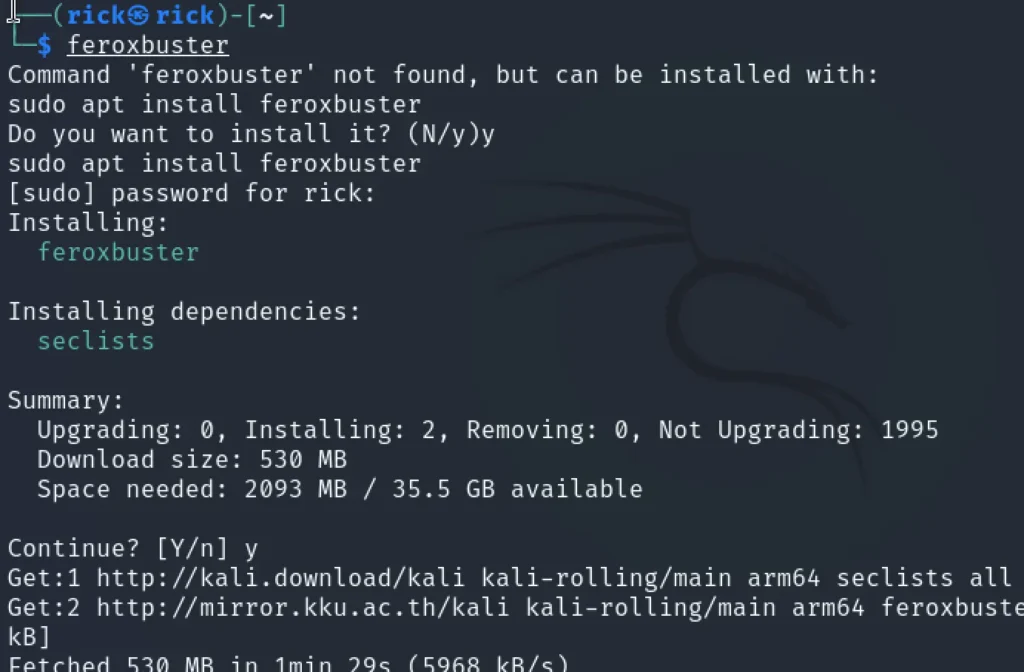
To install Feroxbuster on Kali Linux, you can use the following command:
sudo apt install feroxbuster
Default mode
After successfully installing Feroxbuster, you can move on to the enumeration phase. To perform a default directory brute force scan, use the following command:
feroxbuster -u http://192.168.1.4
Here’s a breakdown of the command:
- feroxbuster: Launches the tool.
- -u http://192.168.1.4: Specifies the target URL for the enumeration process.
This command initiates a basic scan to identify accessible directories and files on the target web server. You can enhance the scan further by adding options based on your requirements.
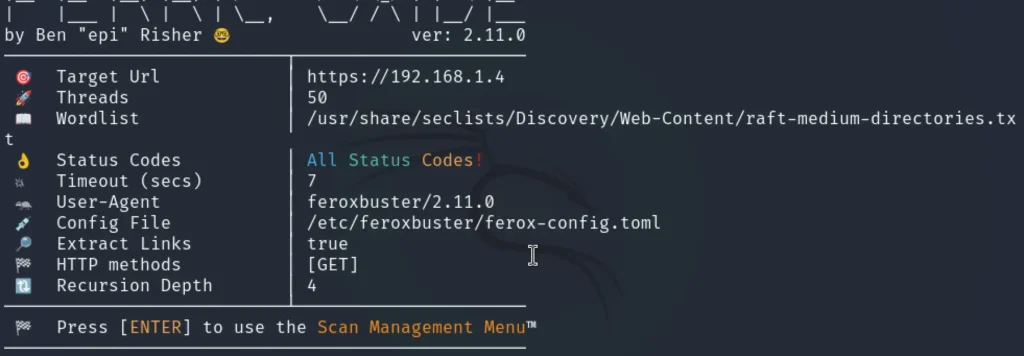
As seen from the default scan, Feroxbuster uses the raft-medium-directories.txt wordlist to perform the enumeration. This wordlist is pre-configured for efficient directory discovery.
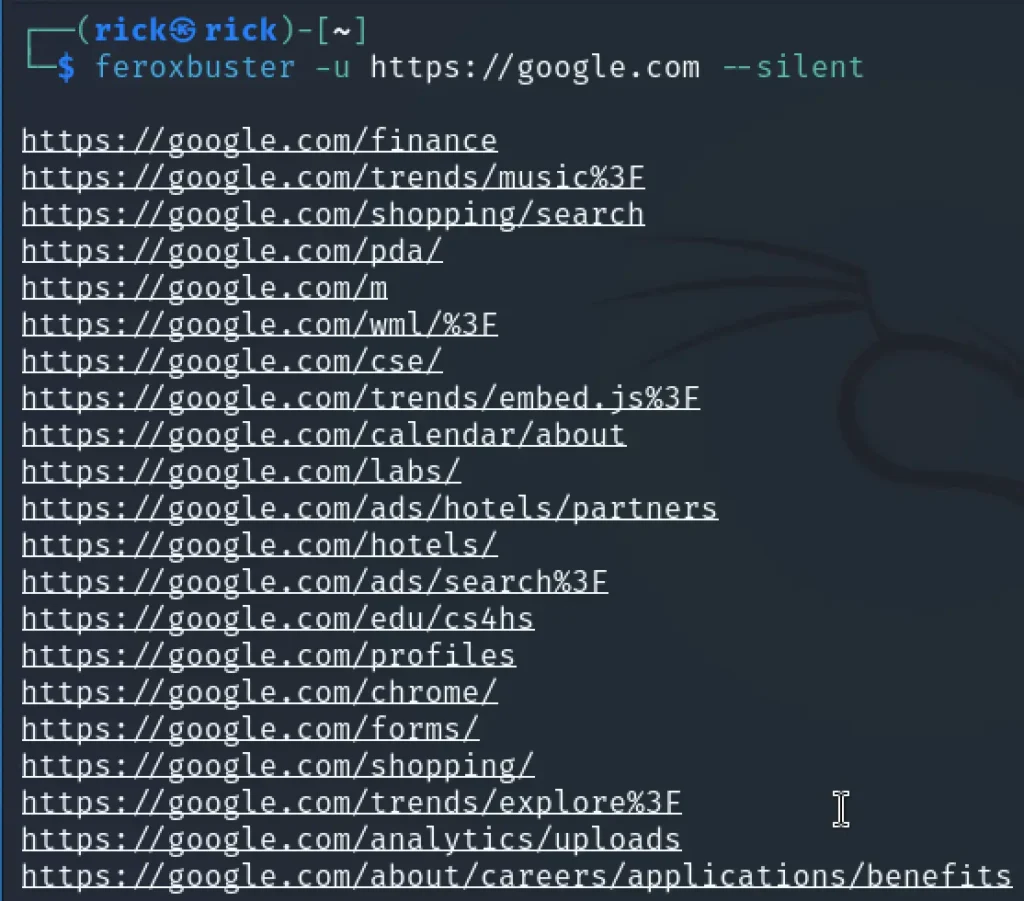
If you prefer a cleaner, less verbose output, you can use the --silent flag. This option hides non-essential data and focuses on displaying only the critical findings. Here’s an example:
feroxbuster -u http://192.168.1.4 --silent
This command ensures the output is concise, making it easier to identify key results without unnecessary noise.
Redirects
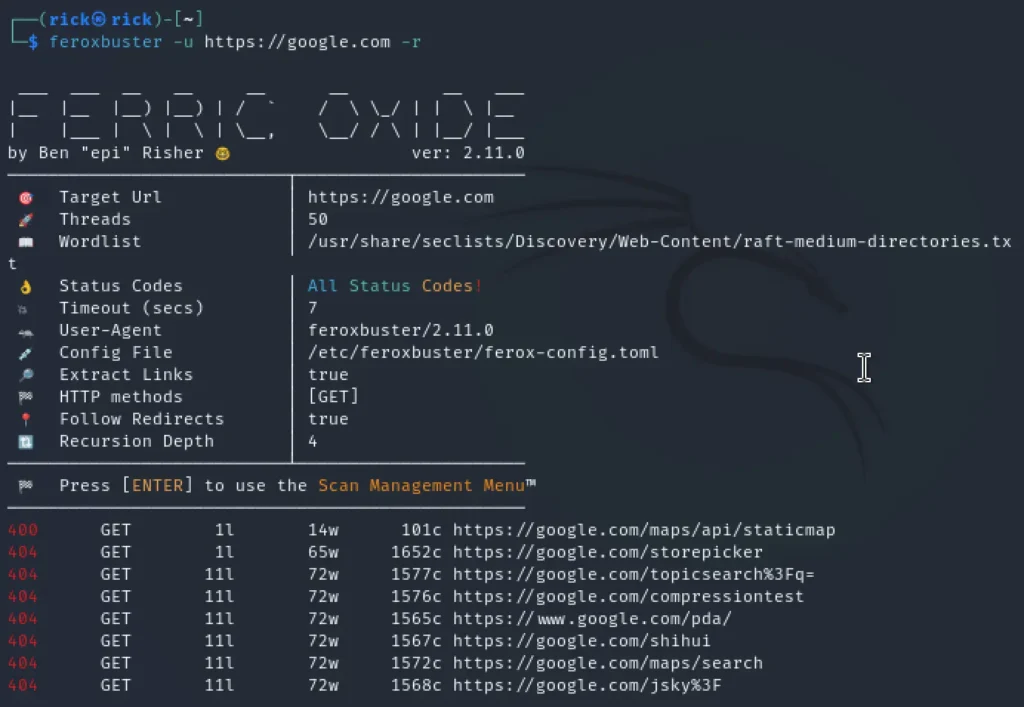
To ensure that Feroxbuster continues directory brute-forcing even when the target URL redirects to a new location, you can use the -r or --redirect flag. This allows the tool to follow redirections seamlessly and continue the scan on the redirected URL.
Also Read: Dirbuster: Full command tutorial for beginners
For instance, if http://192.168.1.4 redirects to http://192.168.1.4/newpath, the following command ensures Feroxbuster follows the redirection and proceeds with scanning the new path:
feroxbuster -u http://192.168.1.4 -r
This feature is particularly useful for handling HTTP-to-HTTPS redirections or when the target URL dynamically routes to a different endpoint.
Extension
To specifically target files with certain extensions during brute-force scanning, you can use the -x or --extensions flag in Feroxbuster. This allows you to narrow the search to specific file types, making the enumeration more focused and efficient.
For example, to scan for .php and .txt files on the target server, use the following command:
feroxbuster -u http://192.168.1.4 -x php,txt --silent
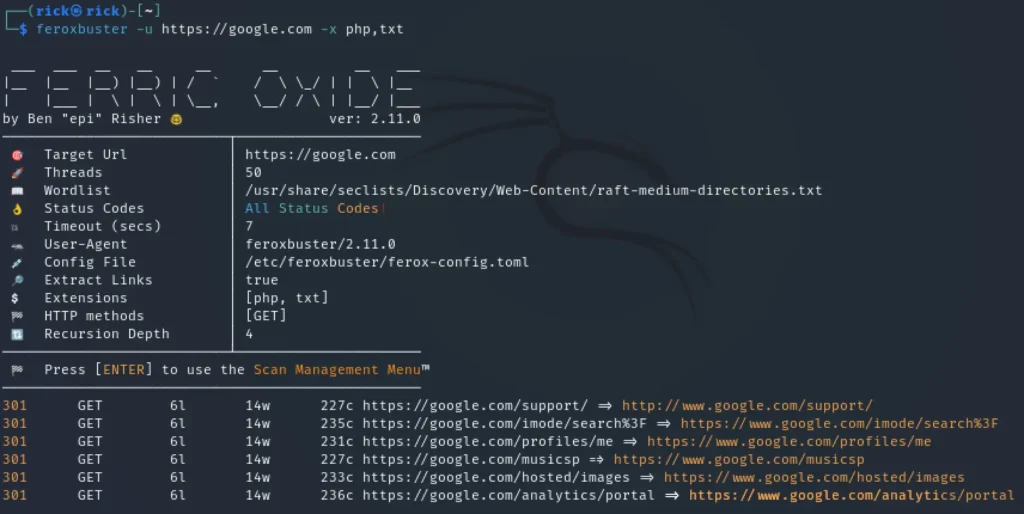
Result output
To save the scan results to a file for future reference, you can use the --output flag followed by the desired file name. This is particularly useful for documentation or detailed analysis.
For example, to log the output of a scan to a file named results.txt, use the following command:
feroxbuster -u http://192.168.1.4 --silent --output results.txt
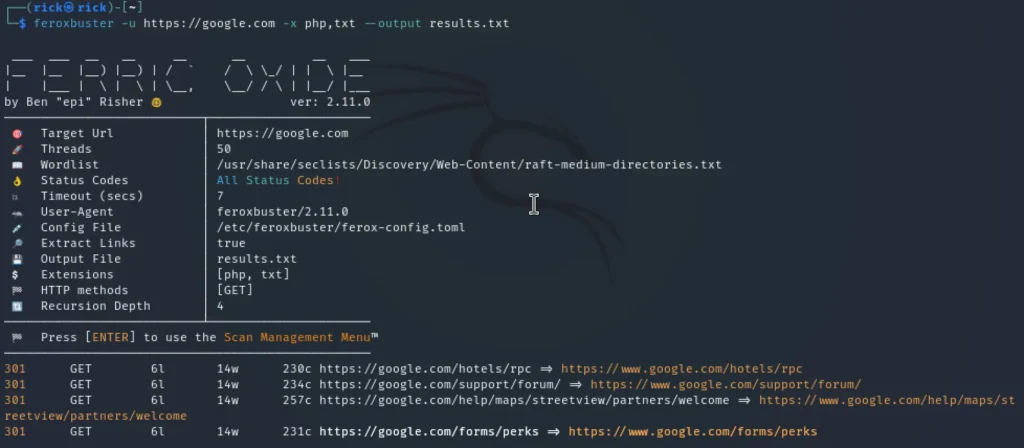
User agent
To customize the User-Agent string sent with each request to the target server, you can use the -a or --user-agent flag in Feroxbuster. By default, the tool uses a User-Agent string in the format feroxbuster/<version>. Changing it can help avoid detection by server-side security measures or simulate requests from a specific browser or device.
For example, to use a User-Agent string resembling a Windows 10 browser, run:
feroxbuster -u http://192.168.1.4 -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64)"
Comparison Between Feroxbuster and Other Tools
Feroxbuster stands out among web directory and file brute-forcing tools due to its comprehensive set of features. It offers advanced response filtering, Burp Suite integration, and a high degree of customization, making it ideal for penetration testers who need detailed, nuanced control over their scans. Its blend of advanced functionality with user control sets it apart as a powerful tool for uncovering hidden resources on web servers.
DirBuster: Known for its user-friendly graphical user interface (GUI), DirBuster is accessible for beginners. However, it may not match the speed or flexibility of command-line tools like Feroxbuster, which offer greater performance and configuration options.
Gobuster: Gobuster is optimized for speed and efficiency, making it a solid choice for quick scans. However, it lacks some of the advanced features and customization options that Feroxbuster provides, which could limit its usefulness for more complex penetration testing scenarios.
ffuf: ffuf offers high performance and extensive filtering, allowing users to fine-tune their brute-forcing process. However, its configuration can be more complex, making it less beginner-friendly compared to Feroxbuster.
Conclusion
In conclusion, Feroxbuster is an excellent choice for users seeking precise control over their scanning processes. It excels with its advanced filtering capabilities, Burp Suite integration, and the ability to customize scans based on specific needs. When compared to other tools, Feroxbuster strikes a balance between performance, flexibility, and user control, making it a powerful option for directory and file brute-forcing tasks.
Frequently Asked Questions (FAQ)
1. What is Feroxbuster used for?
Feroxbuster is a directory and file brute-forcing tool used in penetration testing to find hidden files and directories on web servers.
2. How does Feroxbuster compare to DirBuster and Gobuster?
Feroxbuster offers more features and flexibility than DirBuster, which is GUI-based, and is more customizable than Gobuster, which focuses on speed.
3. Can Feroxbuster integrate with other tools?
Yes, Feroxbuster can integrate with tools like Burp Suite to enhance its functionality in security testing.
Reference: Github
