Introduction
Hey there, In this post, let’s see what is gophish and who created the tool and also let’s see how to use this tool.
Below is a video format of the post, Kindly Check it out and Support me by following in odysee and comment down below in this post.
What is GoPhish 🤔
Gophish is a free tool made for businesses and security testers. It helps set up and run phishing tests and training easily. You can use it on Windows or Linux.
In Simple, gophish is the best tool for phishing attacks and in this post I will do a demo on how to do phishing attack using gophish.
To Install gophish tool, follow the steps below 👇🏾
How to Install GoPhish ⬇️
Certainly! Here are the basic commands to install Gophish:
For Windows:
- Download the Windows version from the Gophish website.
- Open the downloaded file and follow the installation wizard.
- Once installed, navigate to the installation directory using the command prompt.
- Start Gophish by running the command:
gophish.exe
For Linux:
- Download the Linux version from the Gophish website.
- Open a terminal window and navigate to the directory where the downloaded file is located.
- Make the downloaded file executable using the command:
chmod +x gophish - Start Gophish by running the command:
./gophish
To Execute GoPhish You can follow the below command.
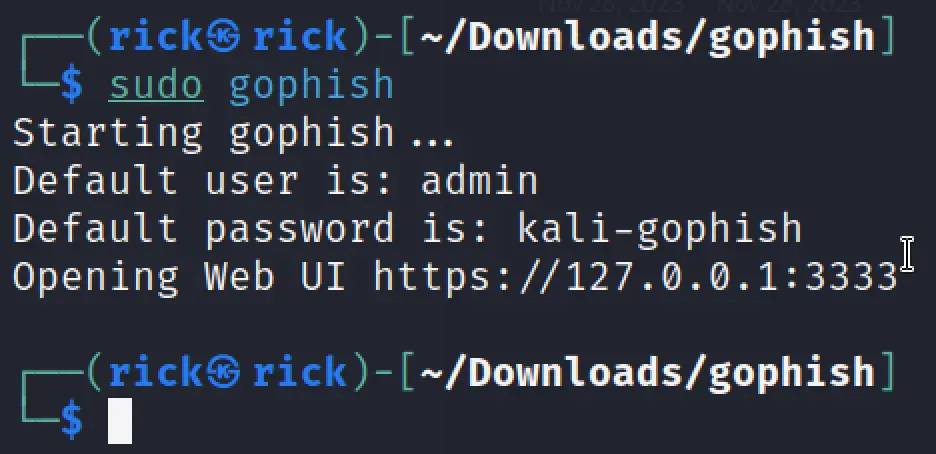
Default Username: admin Default Password: kali-gophish
You can access by going to https://127.0.0.1:3333
Who Developed GoPhish 🤔

Gophish, created by Jordan Wright and the team at Gophish, LLC, is a versatile phishing simulation tool designed for businesses and security experts.
It’s a collaborative project blending cybersecurity and software skills to build a user-friendly platform for testing defenses against phishing.
As an open-source initiative, Gophish evolves with contributions from a dedicated community, enhancing security awareness.
How to Use GoPhish
Follow the steps carefully and demonstrate with your own risk on your system, This is only for educational purpose.
Step 1: Login
Once you have downloaded GoPhish, Just past the link you get on the browser or open it and just enter the default username and password mentioned above.
username: admin password: kali-gophish
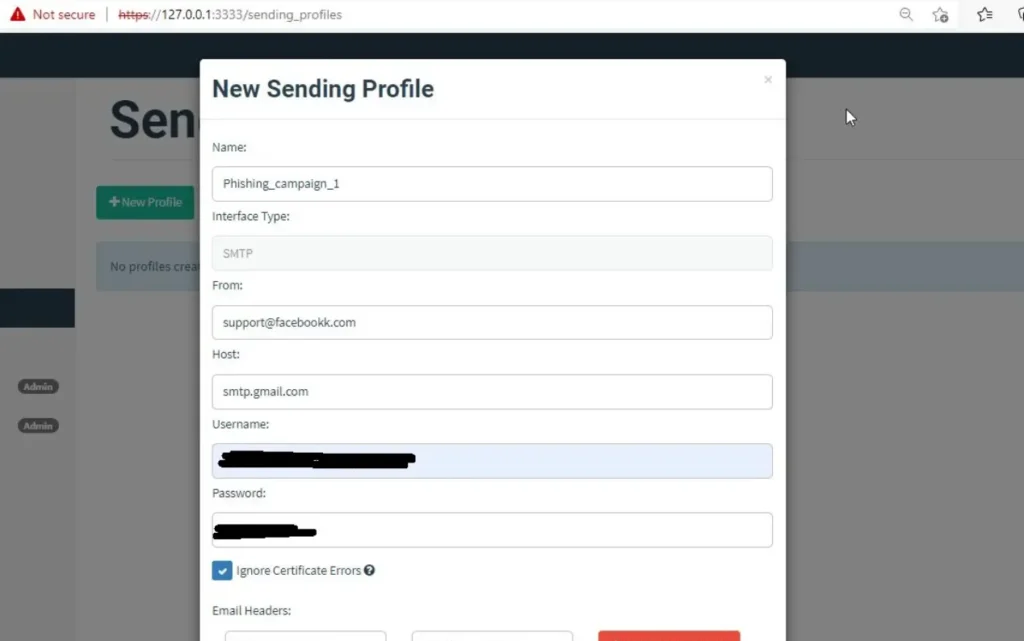
Step 2: Creating Profile
Now, just click on ‘Sending Profile’ to create a profile. With this profile, you’ll be sending a phishing link to the victim.

You can simply click on the new profile and fill in the content you want for your profile.
Let’s name it “phishing campaign 1.” We’ll use Gmail’s SMTP server for sending emails from a Gmail account. In real phishing, attackers typically use a new domain to create an appearance of genuineness. But here, we’re using the Gmail username and password.
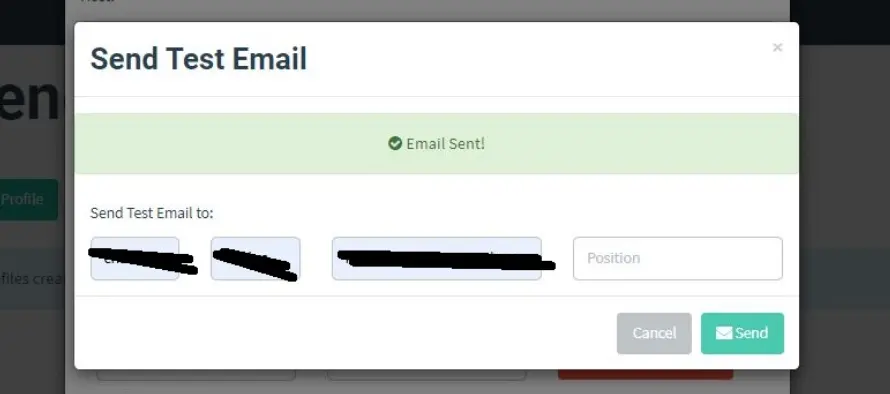
Save the changes you made. Send a test email to any email address you prefer to check if the phishing email looks as intended.
Step 3: Creating Users and Groups
Afterward, we’ll create Users and Groups. This step involves assigning target users for our phishing campaign.
To create a new batch of recipients, click on “New Group.” I’ve named this group as Target_1.
If you have many users, you can save them in a CSV file and import them using the “bulk import users” option.
Step 4: Creating Template
Now, let’s craft an email template. This step is crucial as the email body plays a vital role in convincing a victim to take action or click on links.
Prior to composing the spear phishing email, let’s set up a phishing website.
In this tutorial, we’ll create a fake website to capture credentials using the Social Engineering Toolkit in Kali Linux. Alternatively, we can use Weeman to create the phishing website.
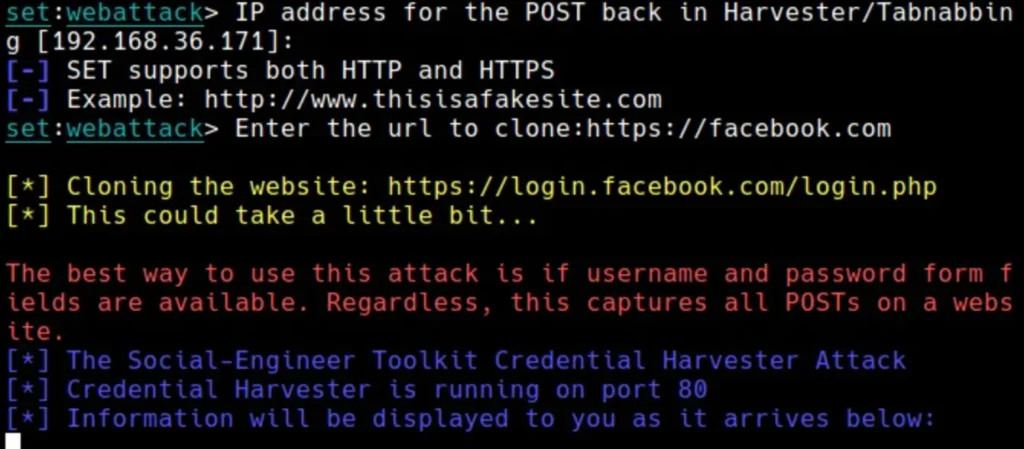
The phishing site is prepared and will show any captured credentials in this terminal. Return to Gophish. Click on “New Template” to craft a new email.
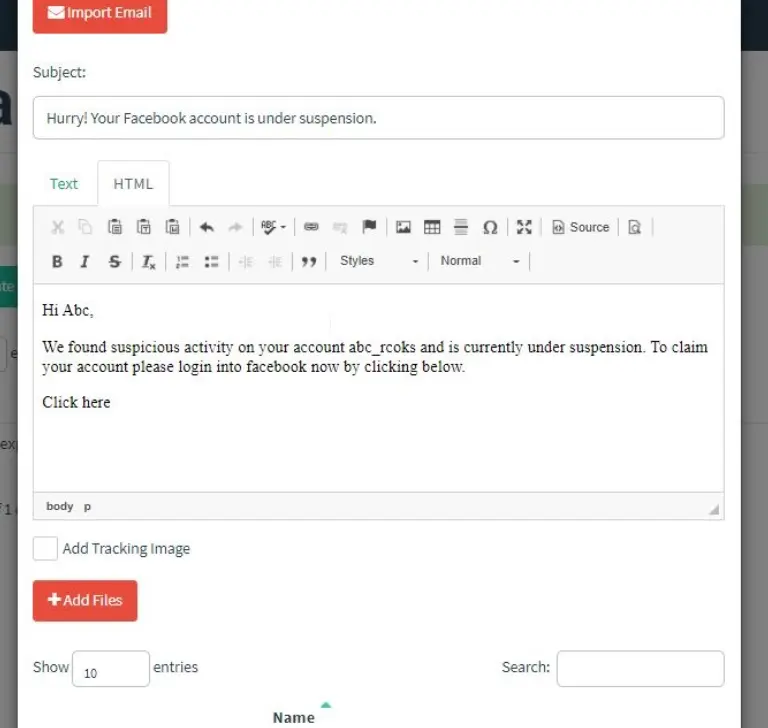
This part holds utmost importance; the email content must persuade the user to take the desired action.
Let’s examine some real-world spear phishing emails, often portraying account suspension notifications, to understand their approach.
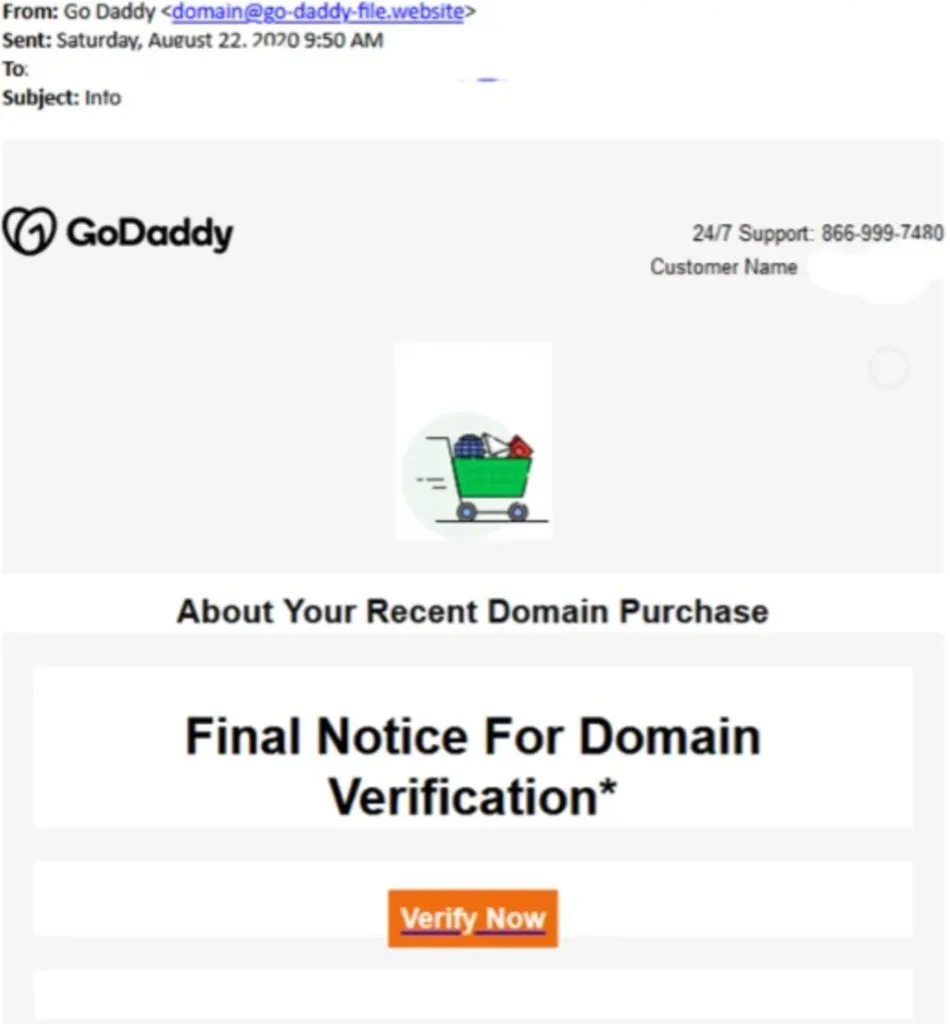
I’m sure readers have an idea of what phishing emails look like. If an email seems suspicious, try hovering over the links instead of clicking on them. Once the email body is finished, let’s add a hyperlink to the email content. Click on “source.”
Step 5: Landing Page
The email template is prepared. Now, it’s time to set up the landing page. In Gophish, the landing page is where the system directs users after they click a link in the email.
Select “New Page.” You have the option to create a new landing page or import one that’s already created. Let’s import the phishing site I made in SE Toolkit on Kali Linux. After it captures credentials,…

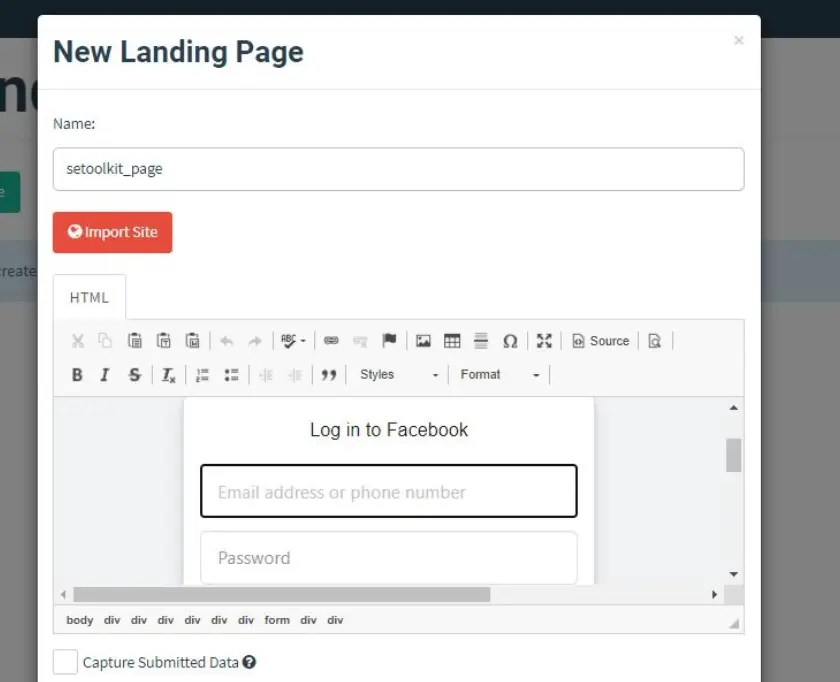
Similar to any phishing website, we can redirect users to another webpage after capturing their credentials.
I’d like the victims to be redirected to the authentic Facebook site.

Save the landing page settings.
Step 6: Campaigns
Everything’s set. Let’s kick off the phishing campaign. Head to the campaigns section and click on “New Campaign.”
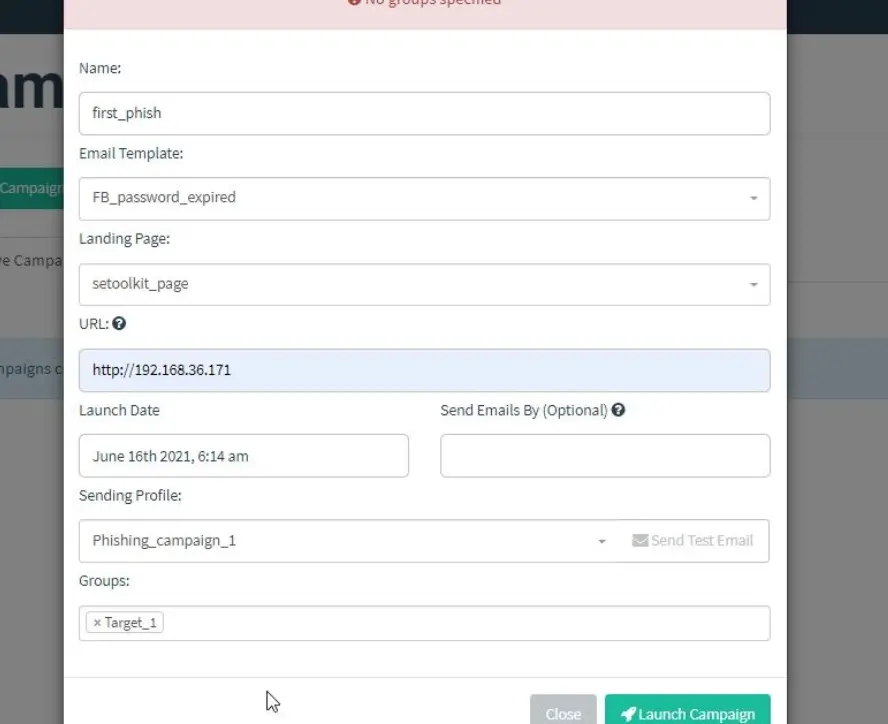
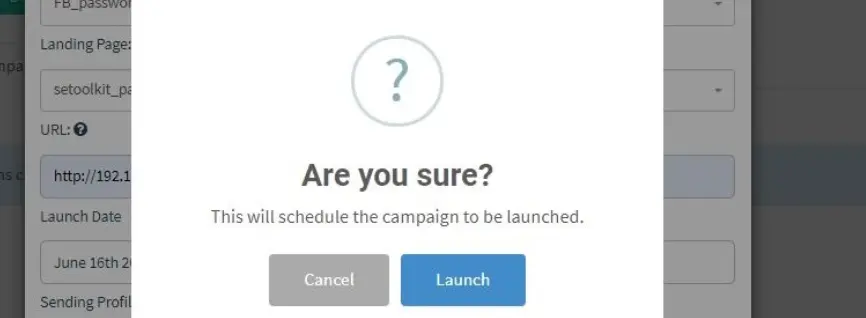
Specify all the details such as the URL, recipients, etc., then click on “Launch campaign.” You can set the date and time for the phishing campaign to start.
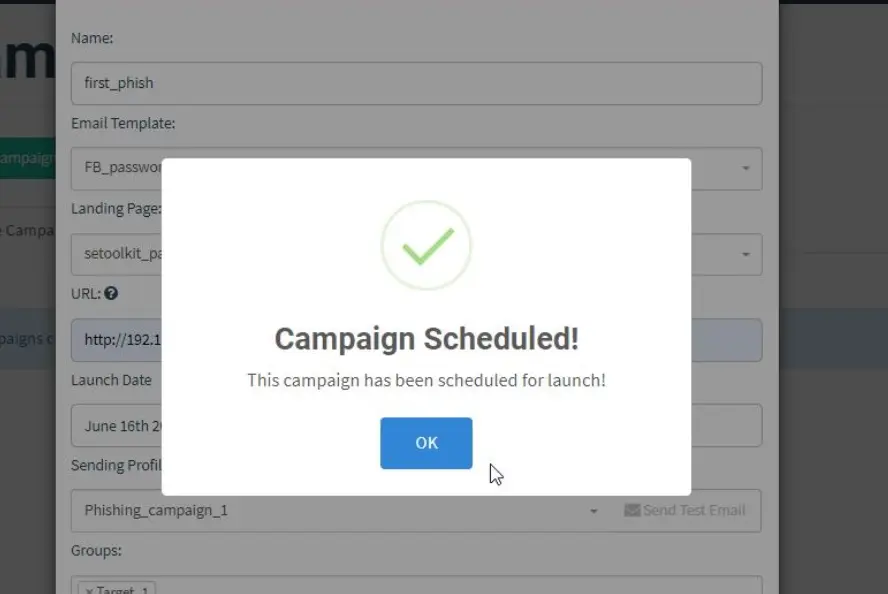
On the dashboard, you can check the campaign results. It displays how many recipients opened your email and how many were affected by the phishing campaign.

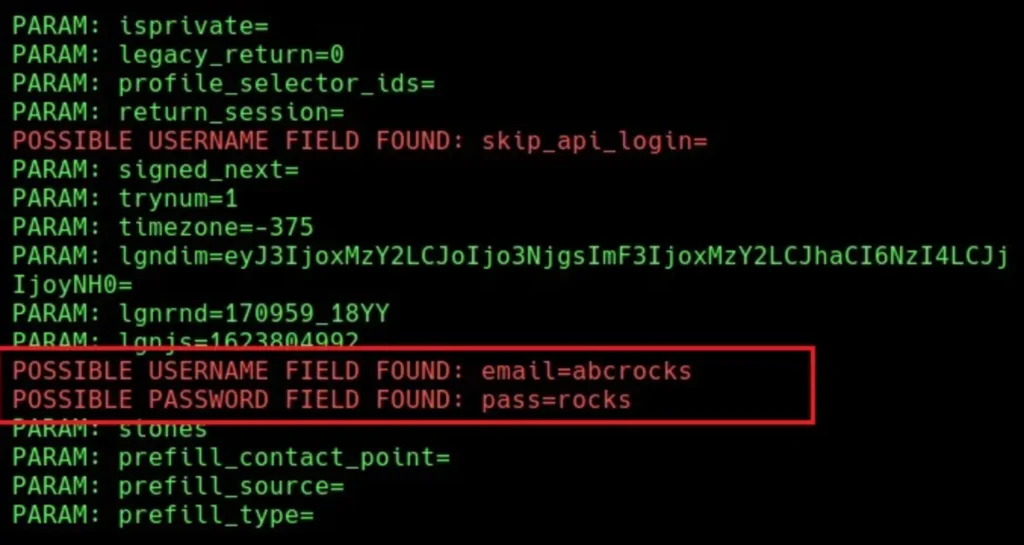
Once the email is harvested, the username and password appear on our terminal…
Conclusion
In short, Gophish is a handy tool that helps test how secure systems are against phishing. It’s user-friendly, making it easy to create and track simulated phishing campaigns. This helps organizations understand and improve their defenses against real phishing attacks.
Also Read: Radare 2 Full Tutorial


