Introduction
In this post, we will learn about one of the powerful password cracking tool Hashcat, its features, how it works and how to use it. Happy Learning!
What is Hashcat ?
Hashcat is a powerful password recovery tool used for cracking passwords. It is mainly designed to help security professionals and penetration testers to assess the strength of the passwords by attempting to crack them by trying out various attack methods.
Hashcat supports wide range of hashing algorithms such as :
- MD5
- SHA1
- SHA265
- bycrypt and many others…
Hashing is a mathematical function and this process will generate a random alphanumeric string for a password given as input string. It’s not reversible and we can’t use a key to decrypt it back like used in the encryption process.
So, Hashcat uses precomputed dictionaries, rainbow tables and even brute-force approaches to find an effective and efficient way to crack hashes and recover the password.
This tool is used for various scenarios such as:
- Recovering lost passwords
- Testing the security of password-protected systems
- Auditing the strength of user passwords
Hashcat is one of a very few tools that can work with GPU. Which has powerful parallel processing capabilities. This will speed up the process making password cracking faster.
Hashcat also supports CPUs and other hardware accelerators on Linux, Windows and MacOS.
Hashcat is developed by Jens ‘atom’ Steube.
You can checkout the repository:
Github link: https://github.com/hashcat/hashcat
Features of Hashcat
- Its free
- Fully open source
- Supports over 300 highly-optimized hashing algorithms!
- Supports Windows, Linux and Mac.
- Supports cracking multiple hashes in parallel
- Built- in benchmarking system.
How does Hashcat work ?
Hashcat takes password hashes as input and identifies the type of hash algorithm used.
Then it tries to crack the password using various techniques which I will explain further.
And if those methods fail it resorts to brute-force and tries every possible combination until it finds the correct password.
Hashcat utilises the GPU power to speed up the cracking process.
And when the password is successfully cracked it will report the recovered password.
Advertisement
How to install Hashcat ?
Hashcat is pre-installed in Kali and Parrot OS. But if you want to install it in Ubuntu/Debian based systems use the below command:
apt install hashcatTo install it in a Mac use HomeBrew. The command is:
brew install hashcatHow to use Hashcat ?
Firstly let’s see the options that Hashcat uses:
hashcat -h/--help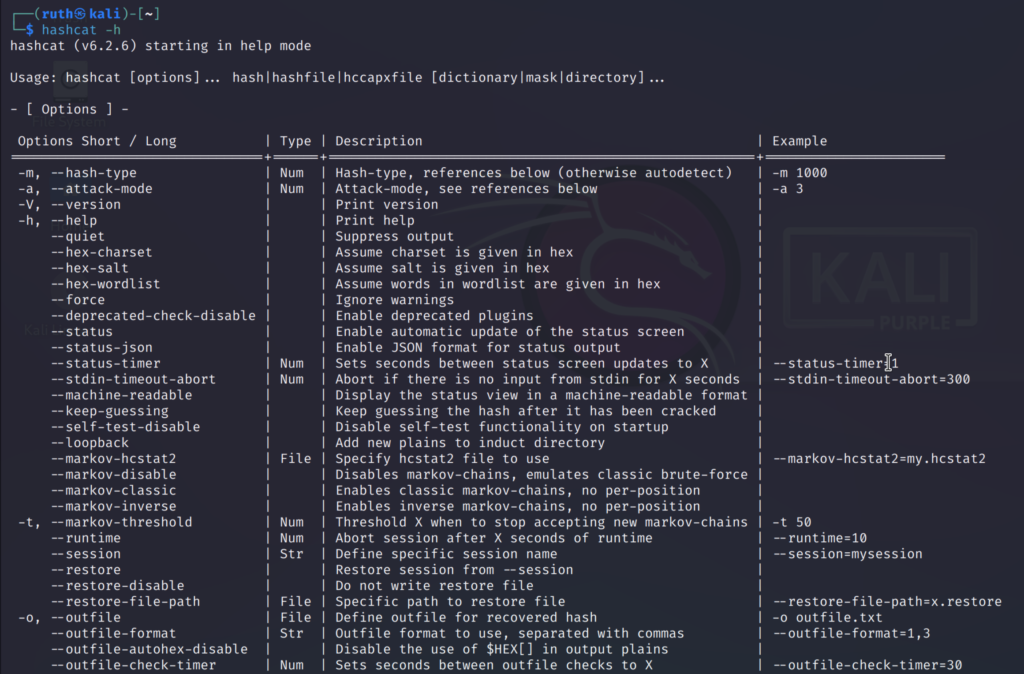
These are some of the mostly used options, you can run the help command and scroll down to explore more options.
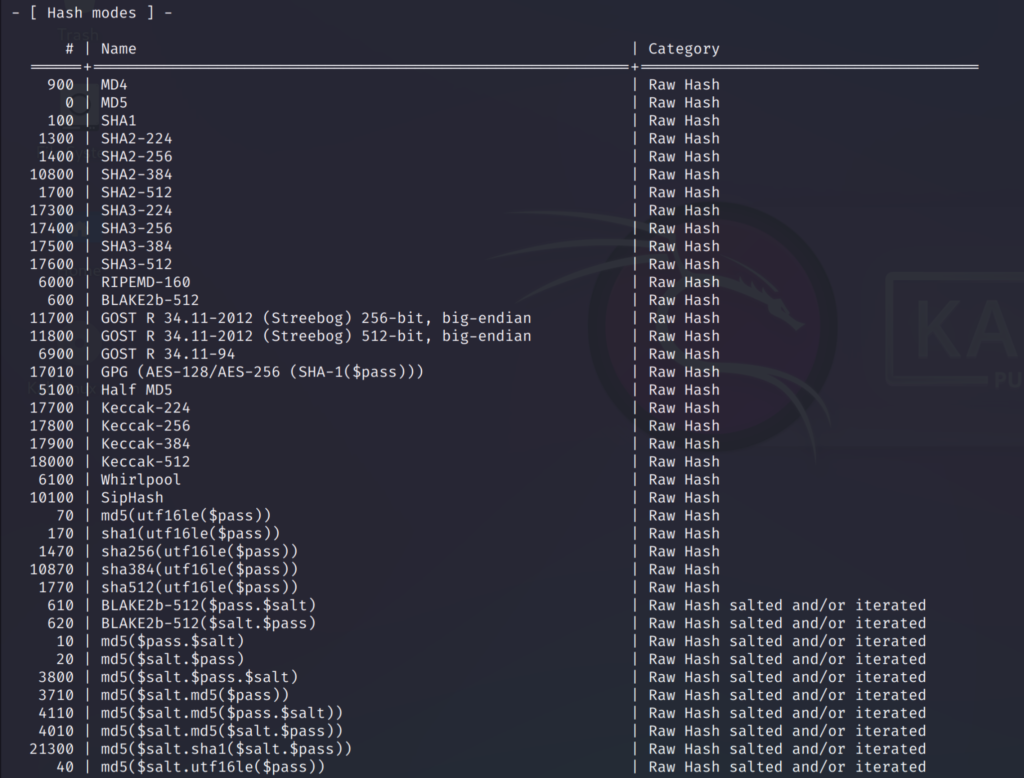
If you scroll down you can check out the hashing algorithms that hashcat uses. You can see that the hash algorithms are categorised according to their purpose.
It might be quite confusing at first since there are over 300 hashing algorithms so we might not know which one to use.
But for easy understanding I have given a link to the fully detailed mind map of the hashcat tool which will help you.
Mindmap link: https://github.com/Ignitetechnologies/Mindmap/blob/main/hashcat/Hashcat.pdf
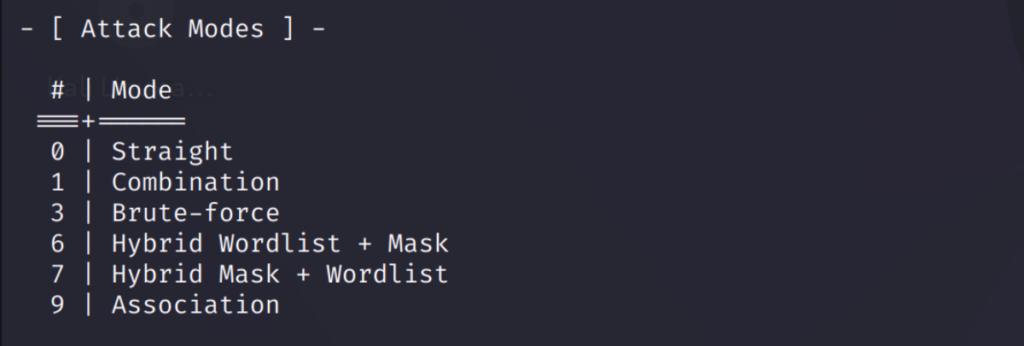
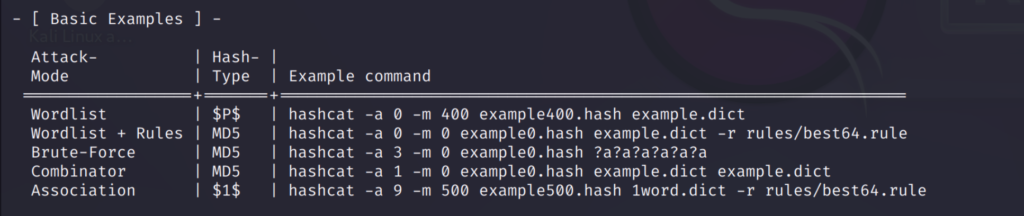
If you scroll down further you can find the attack modes, other important stuffs and some examples on how to use the different modes for different hash types.
Attack modes in Hashcat
We will be seeing some of the attack modes. First, let us create a text file to store the hashes we need to crack.
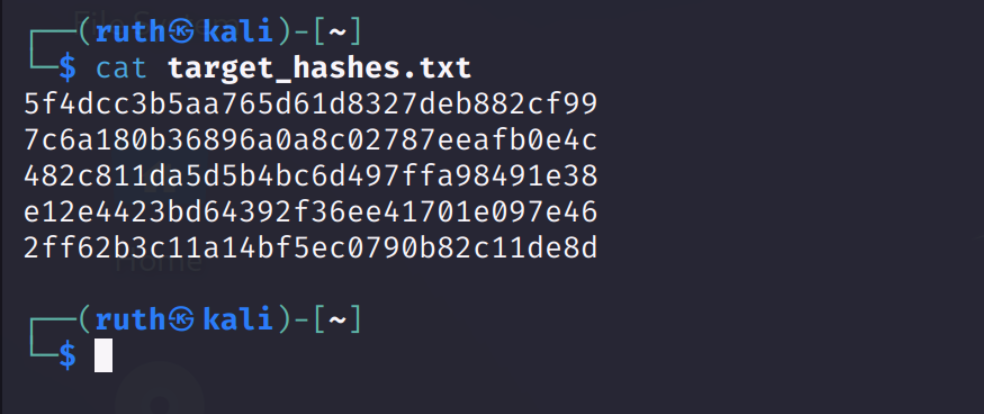
I have used some simple passwords and converted them to MD5 hashes using a converter for demonstrating. I’ll also be using other hash types to store in this file.
Now, let us start hashcat to crack these hashes!
Firstly, we need to know some of the important hashcat options used to crack passwords.
Generally, we will be using -m and -a options mostly.
-m is used to specify the hash type and
-a is used to specify the attack mode
Hashcat uses specifically designed rules to use on a wordlist file. A wordlist file is also known as dictionary file which contains a list of passwords or phrases which are very commonly used.
Advertisement
This serves as a reference for hashcat password cracking tool which will try each word from the file as a potential password and try to find the right password.
Kali linux has numerous wordlists built in it. So, we will be using one of them as a reference file for our hashcat tool.
The wordlist we will be using is rockyou.txt. It contains around 14 million various kinds of random and commonly used password.
You can find the file in the given directory:
/usr/share/wordlists
Straight Attack
The first attack we are going to perform is straight attack or dictionary attack. It’s the default method that hashcat uses.
This attack is faster on simple passwords.
The hash type I and using is MD5 and in the command I have specified the hash type, attack mode, path of the text file containing hashes and the path of the wordlist.
The command is:
hashcat -m 0 -a 0 /home/ruth/target_hashes.txt /usr/share/wordlists/rockyou.txt.gz
-m 0 is for MD5 hash type
-a 0 is for straight attack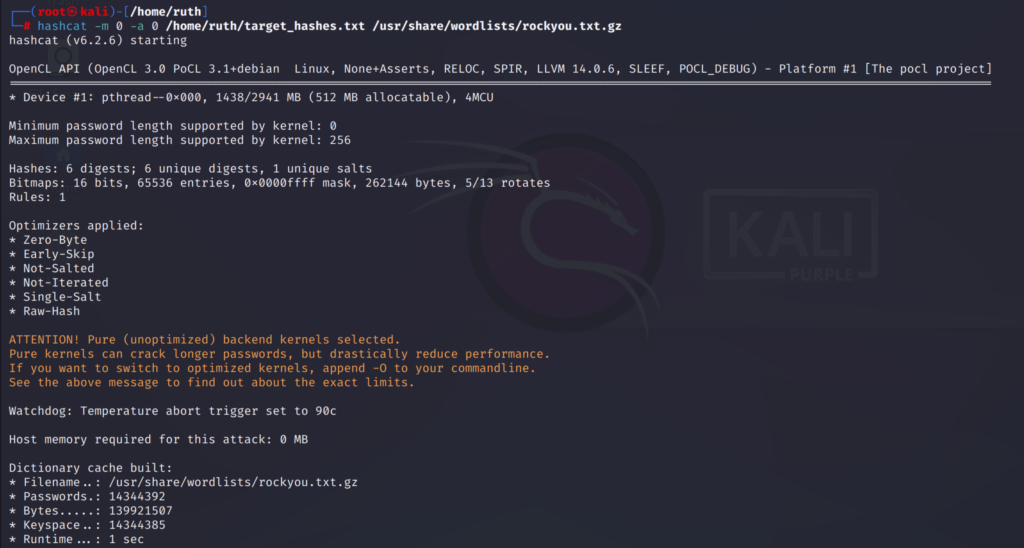
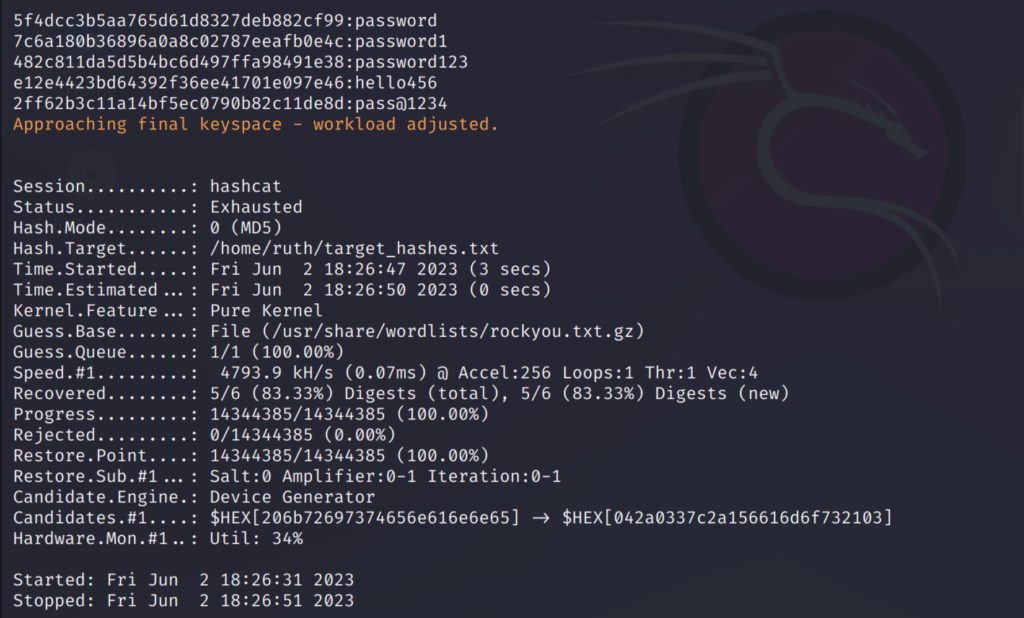
As you can see all the 5 hashes has been cracked and these are the right passwords it found.
Since the passwords were simple it was quick to crack them.
If they are complex then it will take some time to crack them.
After performing the crack command you can checkout the cracked passwords using —show option added to the previous command.
hashcat -m 0 -a 0 /home/ruth/target_hashes.txt /usr/share/wordlists/rockyou.txt.gz --show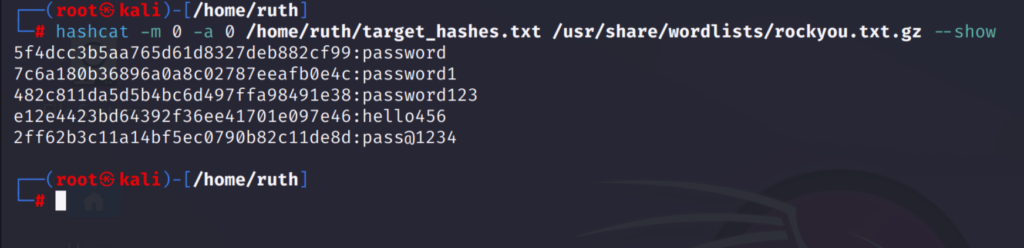
I have also cracked a SHA1 hash using the same attack mode:
hashcat -m 100 -a 0 /home/ruth/target_hashes.txt /usr/share/wordlists/rockyou.txt.gz
-m 100 is for SHA1 hash type
-a 0 for straight attack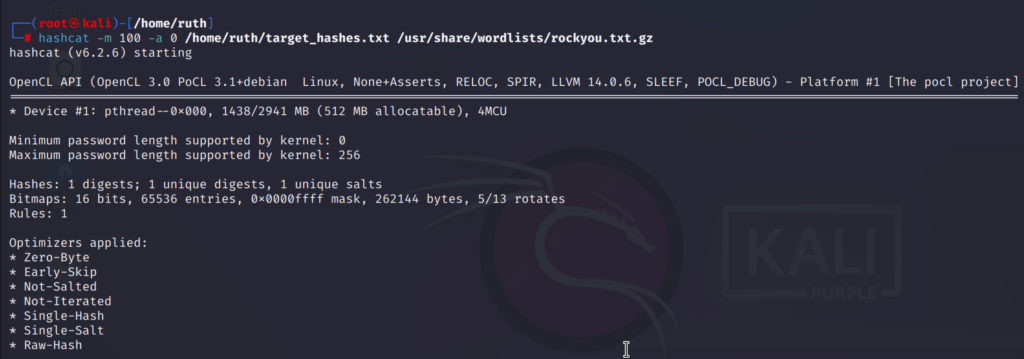
Combination Attack
This attack is used to crack passwords that are two words joined together. Such as ‘passpass’ or ‘blue-bike’.
Hashcat exploits this using the combination attack that takes two wordlists (dictionaries).
So the two wordlists we will be using must contain the left and right parts of passwords.
The word list I’m using contains both the words from the password so I’ll be using the same for left and right side.
The command is :
hashcat -m 0 -a 1 <path_of_hashfile> <path_of_wordlist1> <path_of_wordlist2>
hashcat -m 0 -a 1 /home/ruth/target_hashes.txt /usr/share/wordlists/rockyou.txt.gz /usr/share/wordlists/rockyou.txt.gz
-m 0 for MD5 hash type
-a 1 for combination attack
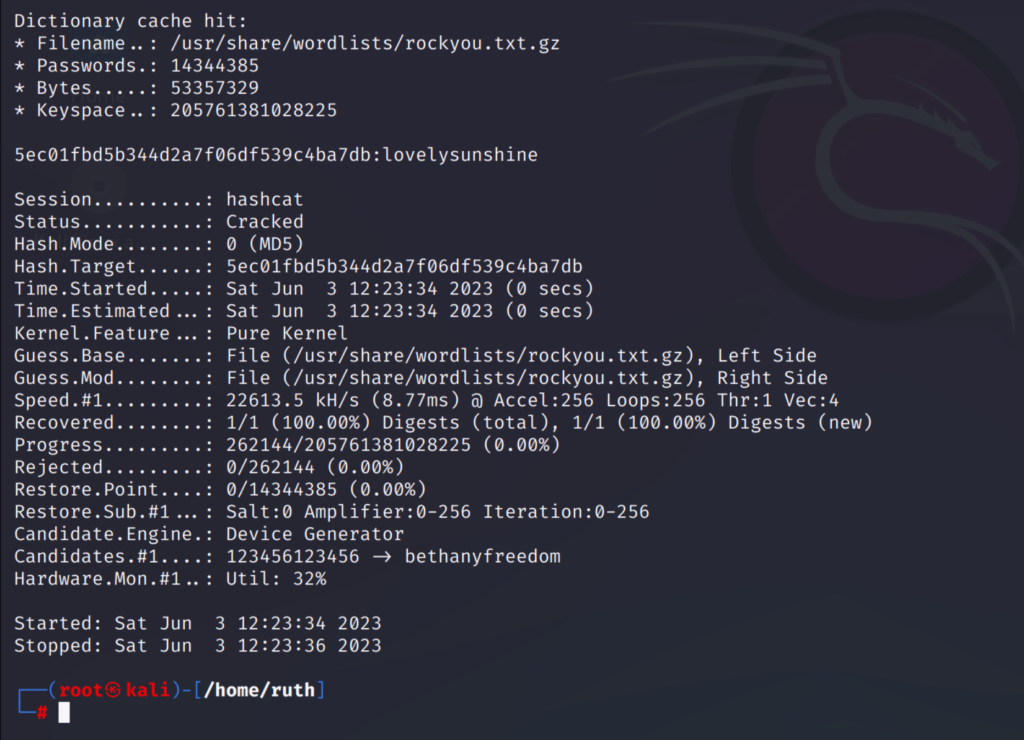
As seen above the password I wanted to find was ‘lovelysunshine’ which the hashcat cracked using the combination attack.
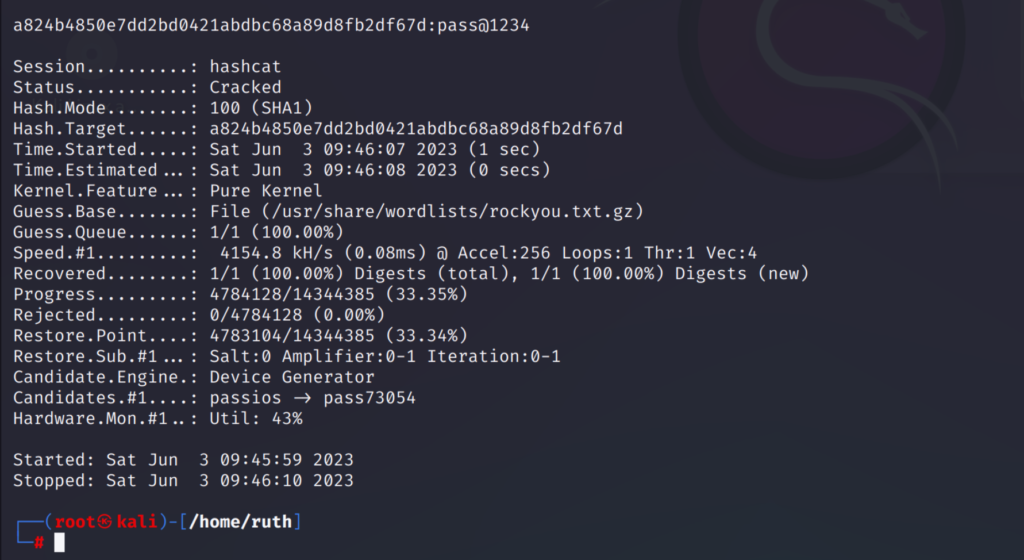
Similarly I tried the same attack mode on a SHA1 hash:
hashcat -m 100 -a 1 <path_of_hashfile> <path_of_wordlist1> <path_of_wordlist2>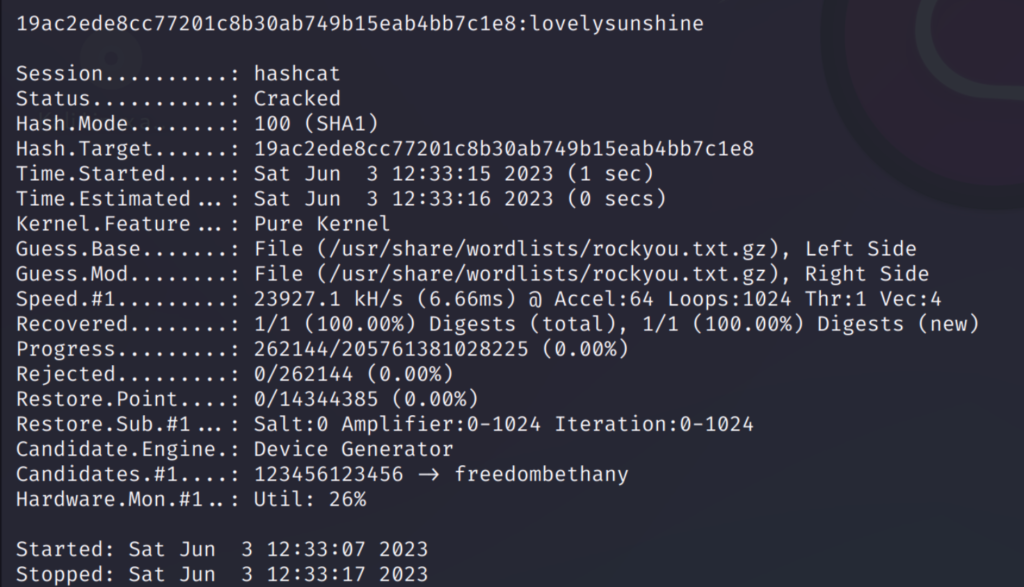
Mask Attack
Mask attacks are similar to brute-force attacks since it tries out all possible combinations from a set of characters.
In brute-force attack all possible characters that exist are tried out but Mask attacks are more specific as the set of characters you try is reduced based on the information you know.
For example, if you know the last character in a password is a number, you can configure your mask to only try numbers at the end.
We know about humans and how they design passwords. For example the password I’m going to use: ‘zaq123’ is a name and a 3 digit number which is commonly used. Mostly lower-case letters will be used as the first letter in many passwords.
We will be using the built-in charsets (character sets) to specify how our password is like.
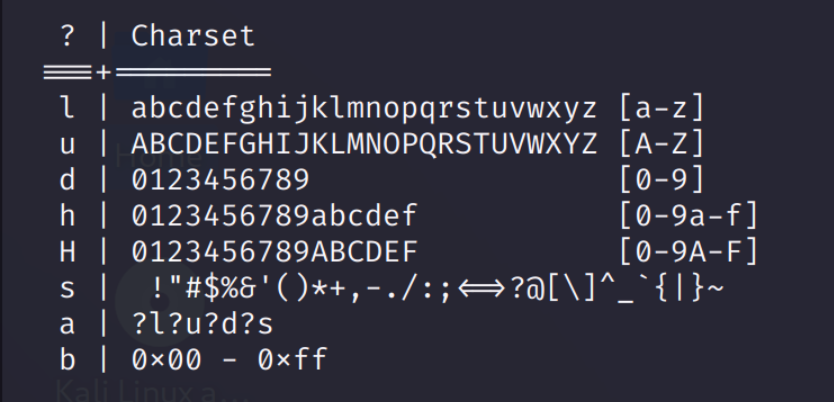
We will be creating different charsets using ‘?’ Followed by the options ‘l’, ‘d’ given above.
The custom charsets will be like:
-1 ?l -2 ?l?u?d -3 ?dThese custom charsets are equal to:
-1 abcdefghijklmnopqrstuvwxyz
-2 abcdefghijklmnopqrstuvwxyz
ABCDEFGHIJKLMNOPQRSTUVWXYZ
0123456789
-3 0123456789
Now after defining these, we need to specify for every character which charset to use.
For example, the first character of my password is a lowercase. So for the first character I will use the charset ‘-1’. And I know that the last 3 characters will be a number so I will using charset ‘-3’ for those.
Now I will specify the charsets for all the 6 characters of the password and the mask will look like this:
?1?2?2?3?3?3I’ll be using the brute force mode here so the command will be like:
hashcat -m 0 -a 3 -1 ?l -2 ?l?u?d -3 ?d /home/ruth/target_hashes.txt ?1?2?2?3?3?3
-m 0 for MD5 hash type
-a 3 for brute force mode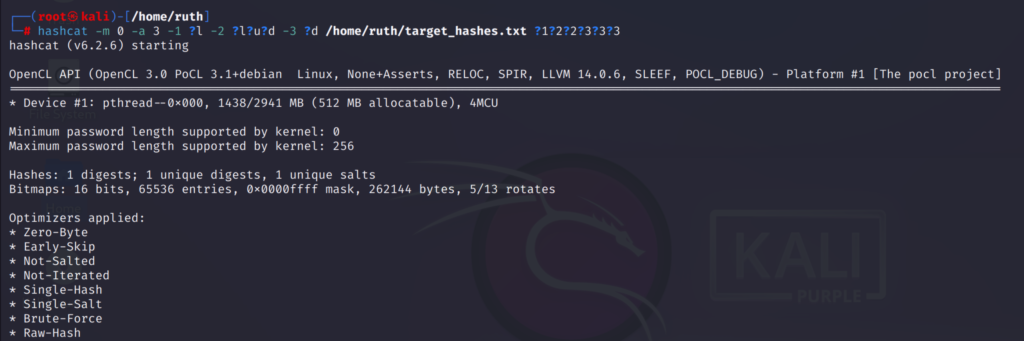
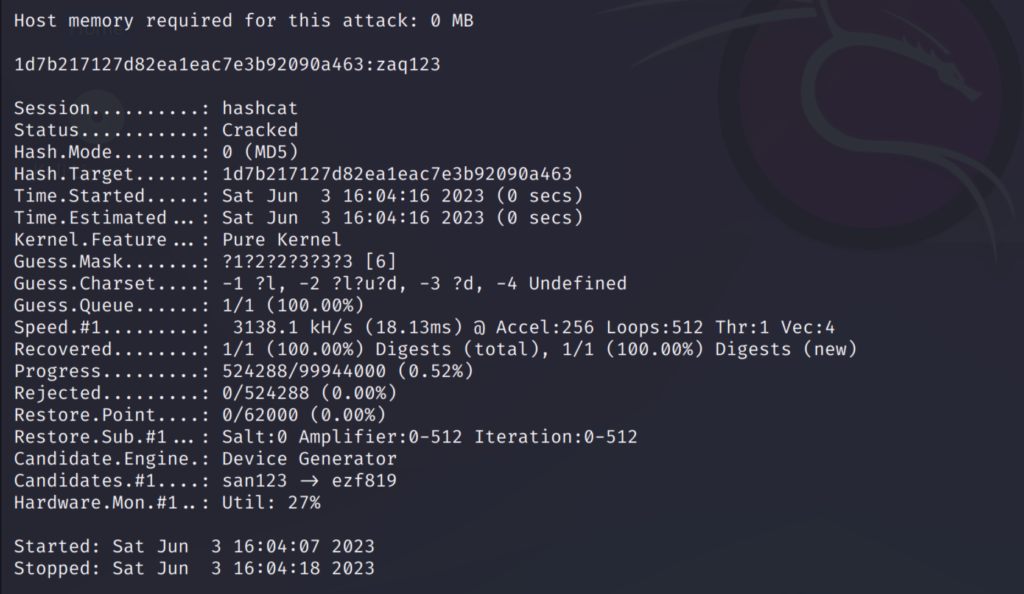
As seen above we can see the cracked password ‘zaq123’
There is an option called —increment this is quite useful because the mask we specified above will only check the passwords of that specific length.
But this —increment option will go though all possible combinations from 1 to 6 characters which is the length of the password I have used above.
Add this option to the command to increment:
hashcat -m 0 -a 3 -1 ?l -2 ?l?u?d -3 ?d /home/ruth/target_hashes.txt ?1?2?2?2?2?3?3?3 --increment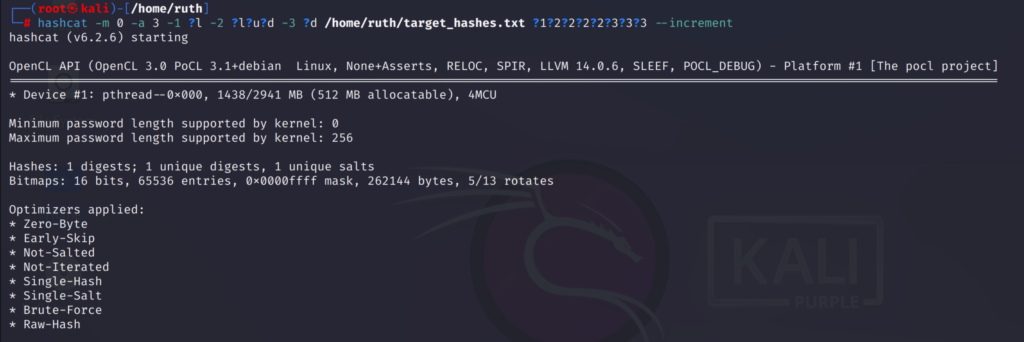
The increment option will go through all possible combinations like this:
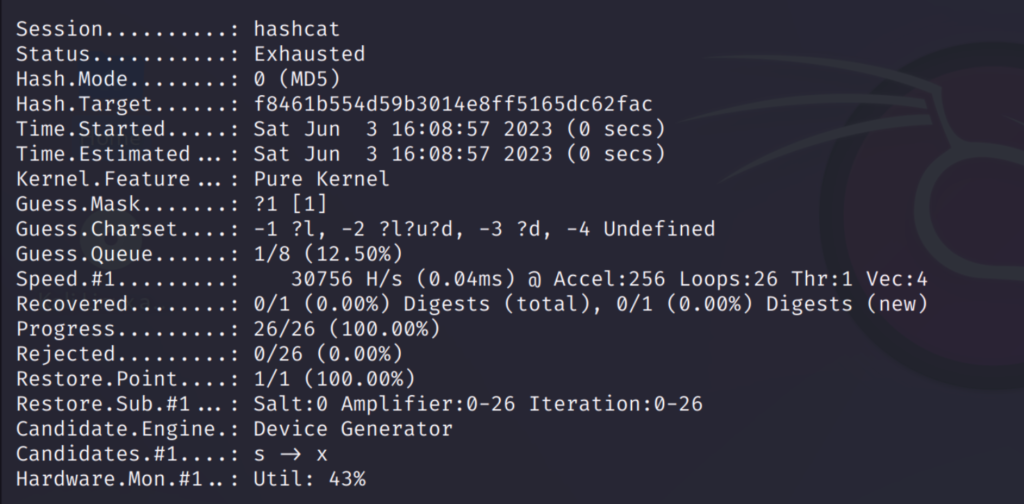
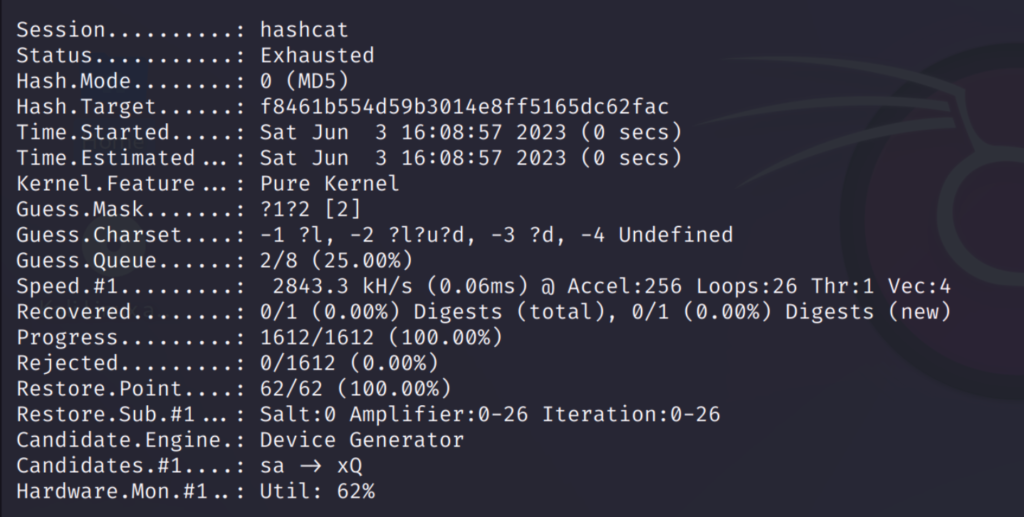
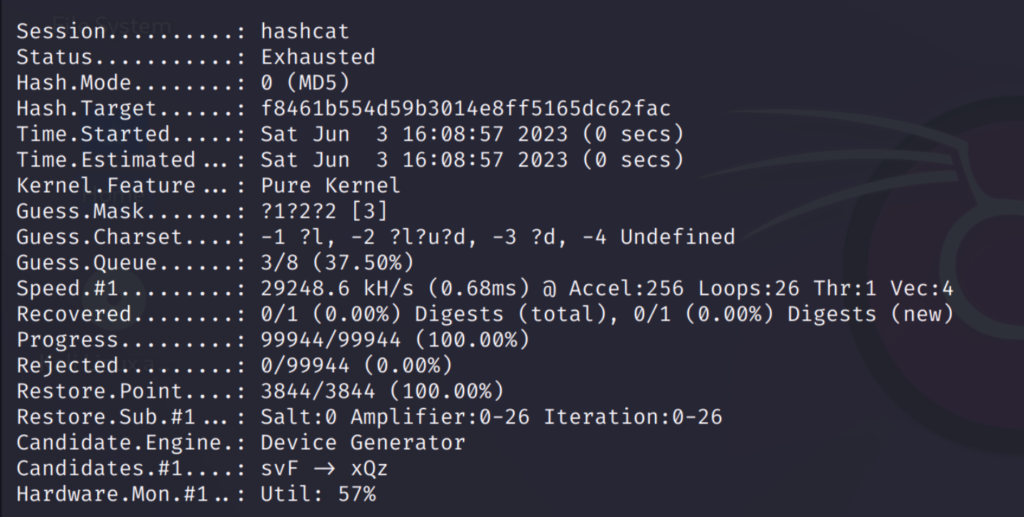
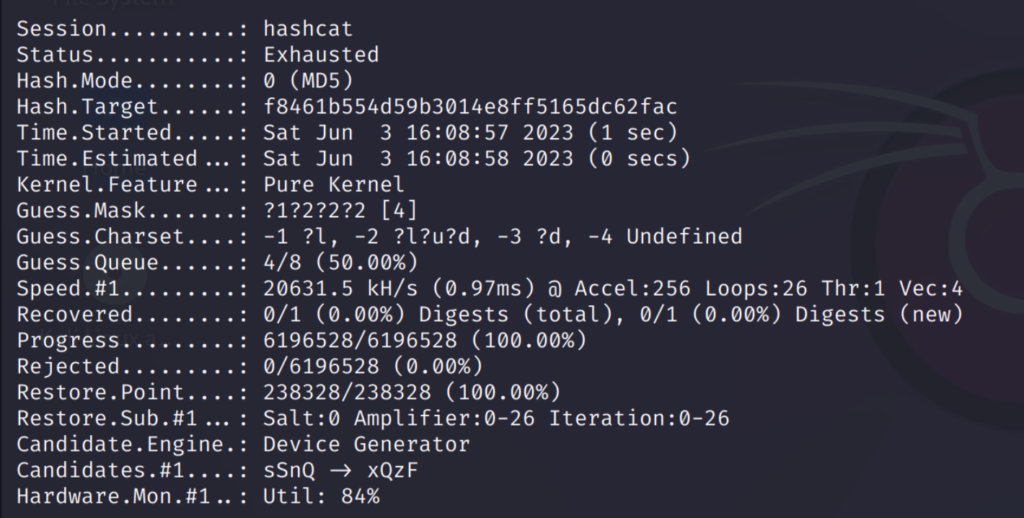
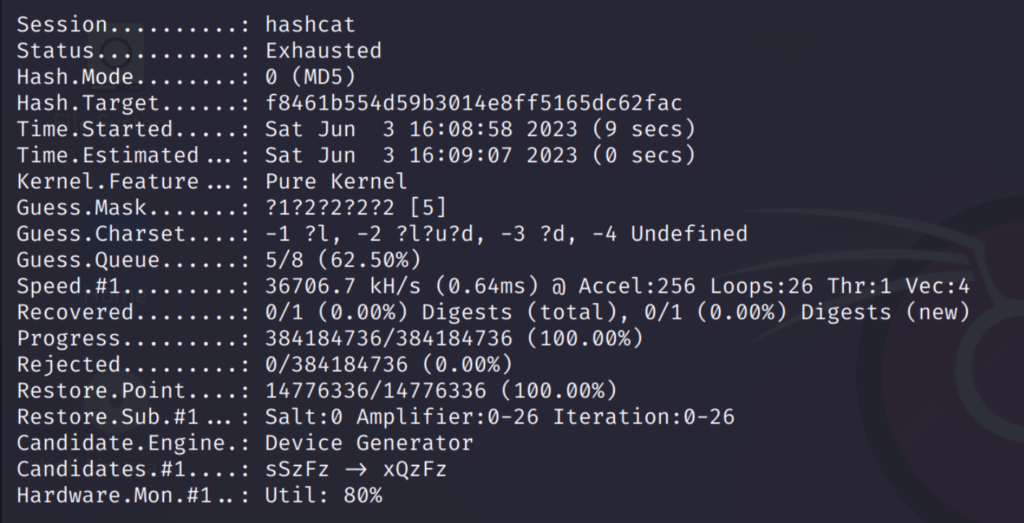
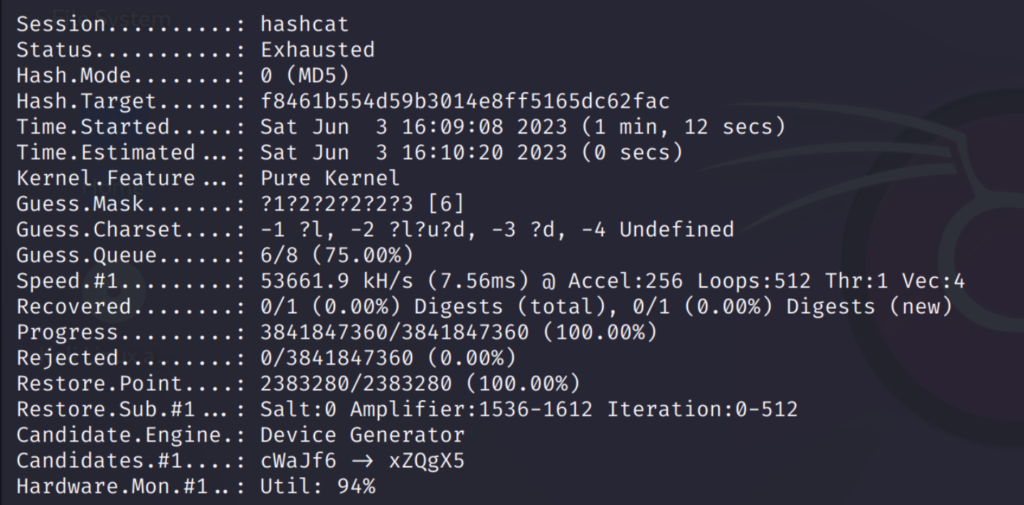
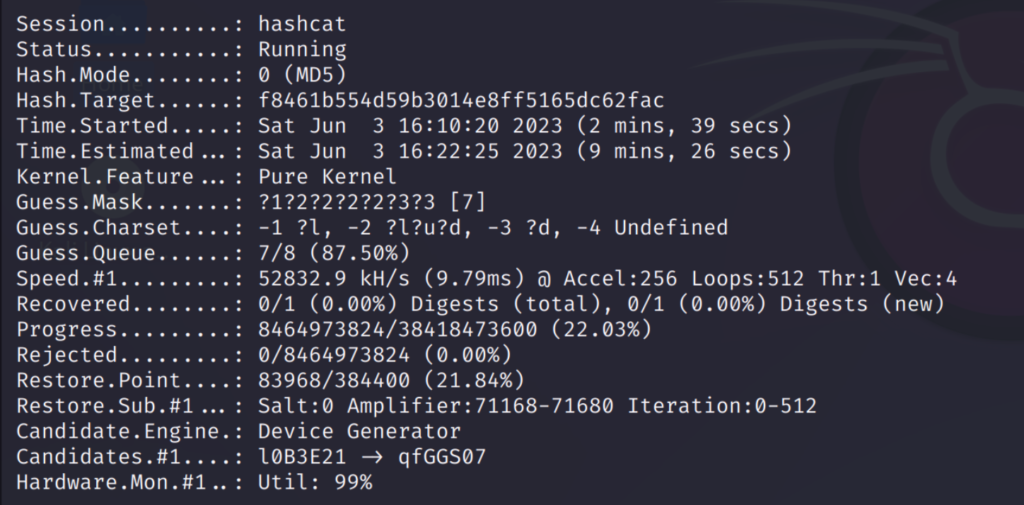
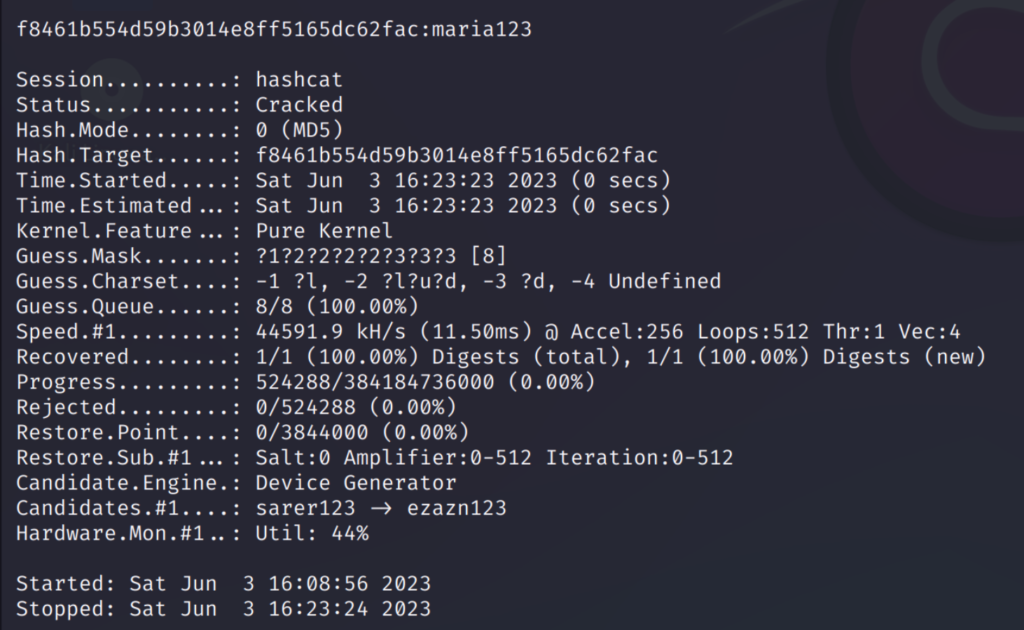
I have used the password ‘maria123’ which is shown above. As you can see it has gone through all possible words from 1 to 7 character passwords.
This took some time because going though all possible combinations is a lengthy process. But this option is very useful in finding the accurate password.
Rule Based Attack
This type of attack is used to form patterns in passwords using certain rules. This will help to generate new passwords in our present wordlist instead of manually adding them.
For this method we only need our original wordlist and a file containing the rules to form patterns.
A rule based attack allows us to form patterns which are applied to existing passwords to quickly generate new passwords to use.
firstly I will create a rule-set which I will use on my wordlist.
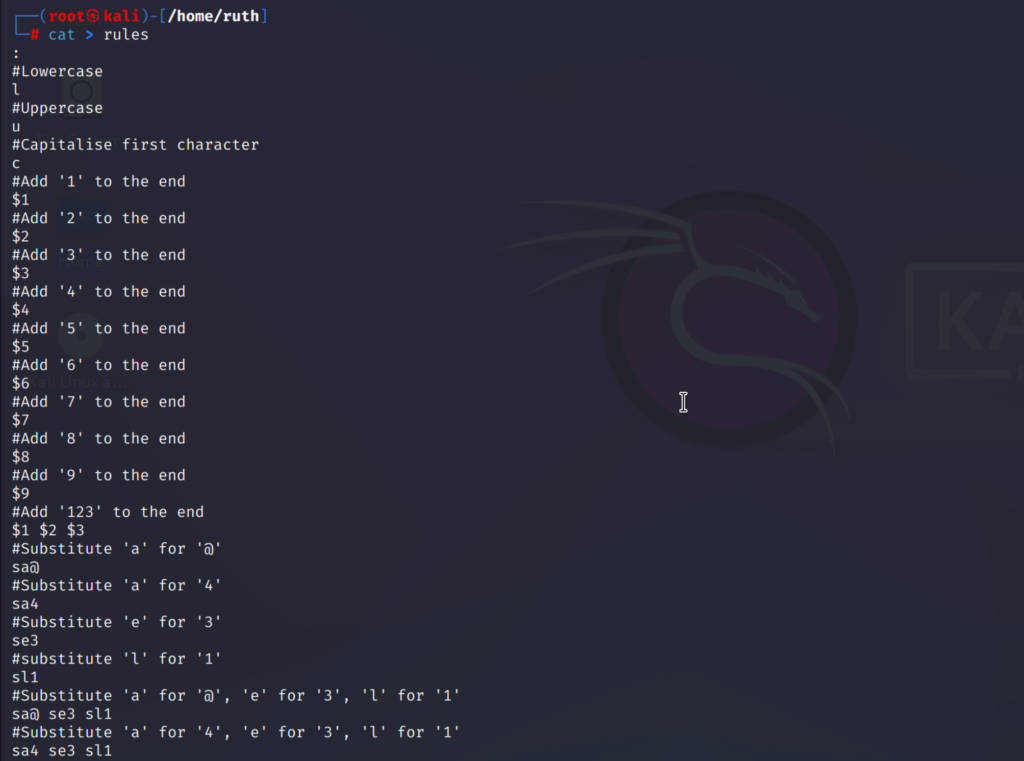
This is the file I’ll be using.
The rules I have added are:
- The ‘:’ will instruct the hashcat to try the original word before applying the rule.
- l, u and c stands for the lower, upper and capital case letters
- $1 will add a ‘1’ to the end of password and same for other numbers
- $1 $2 $3 will add ‘123’ to the end
- sa@ will replace ‘a’ with ‘@‘ and same for others
Advertisement
You can also use the existing rule files that hashcat contains by default. These are located in the below given path:
/usr/share/hashcat/rulesNow that we are done with the rules let’s launch our rule-based attack!
The command is:
hashcat -m 0 /home/ruth/bfield.dic /usr/share/wordlists/rockyou.txt.gz -r rules --debug-mode=1 --debug-file=matched.rule
-r specifies the rules file
--debug-mode=1 this writes a rule whenever it cracks a password
--debug-file=matched.rule the file name where the matched rules are stored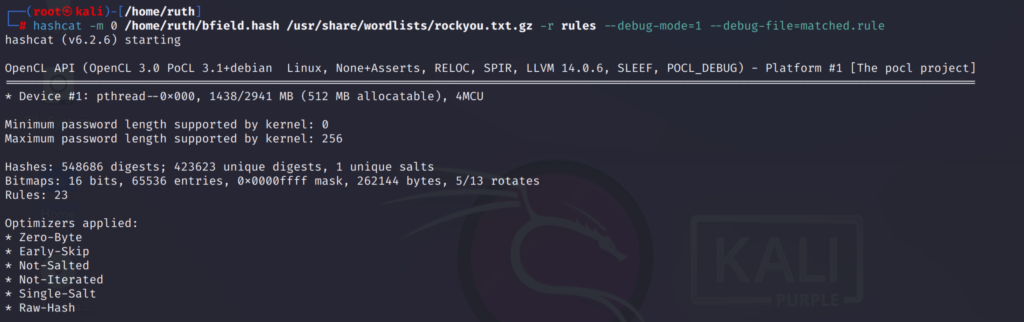
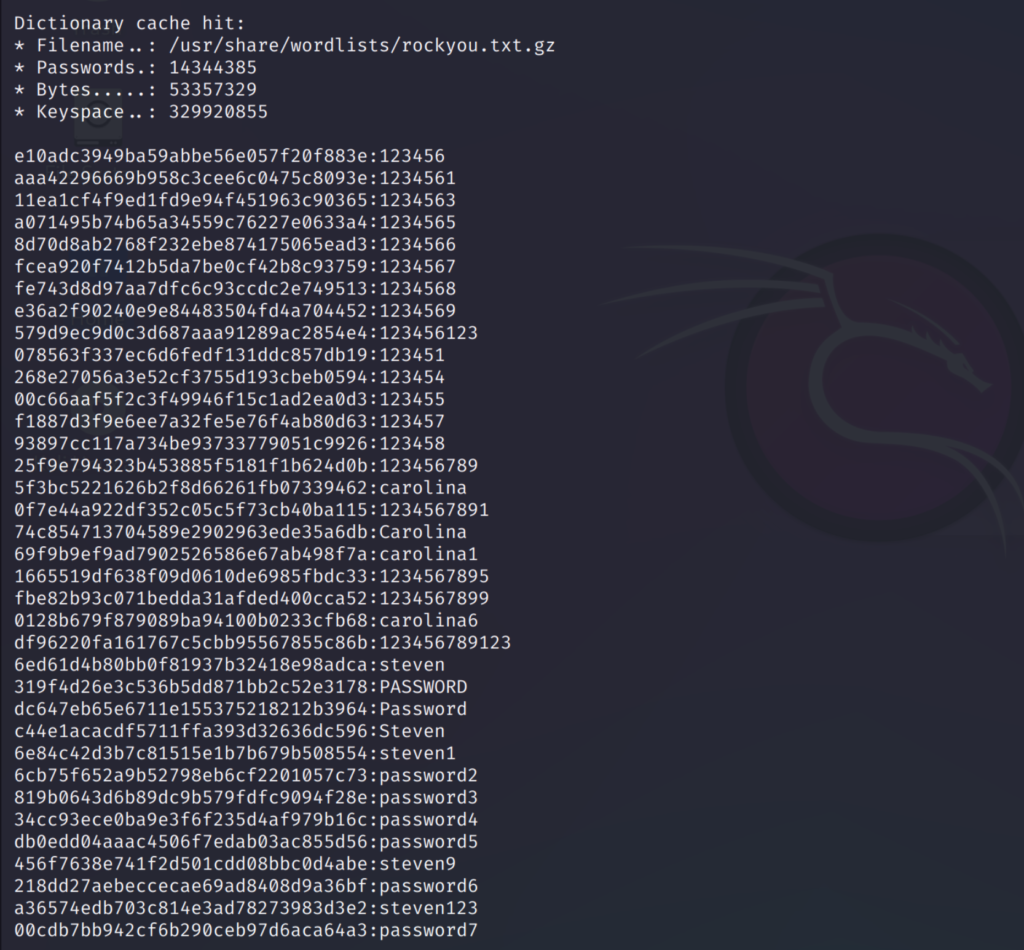
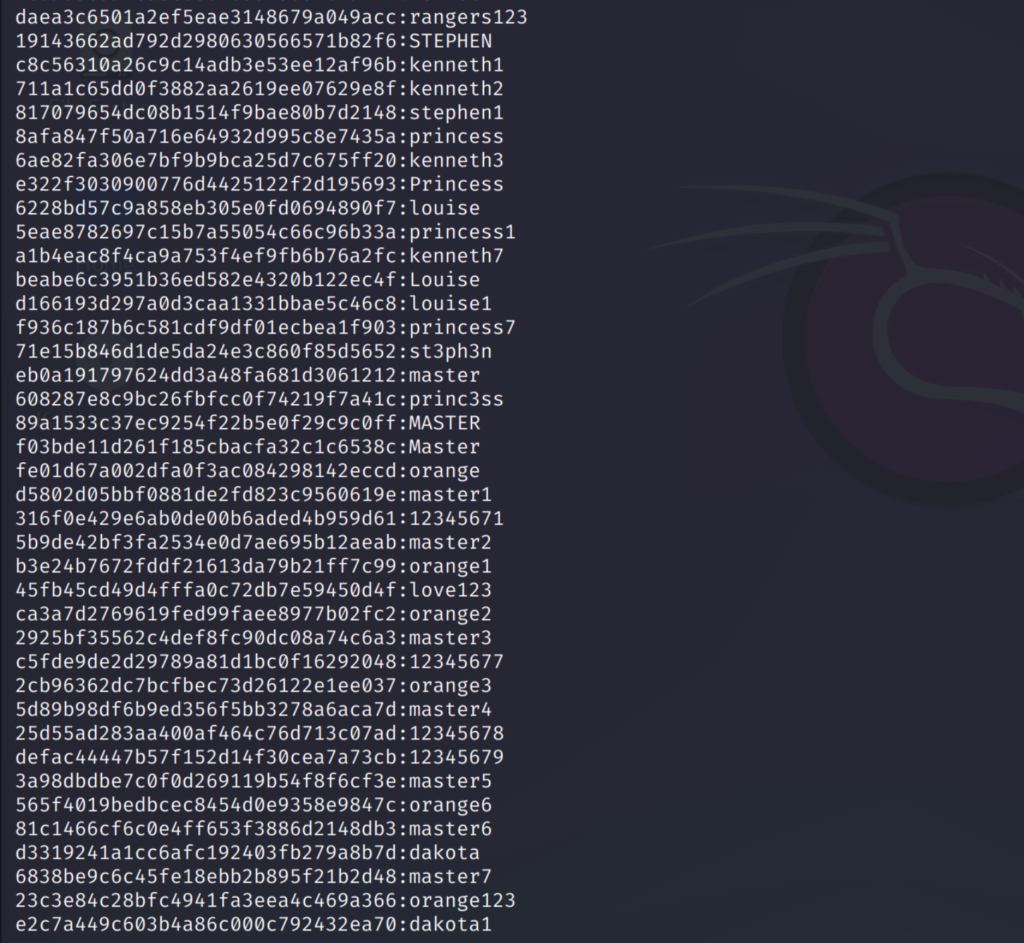
As you can see above, the rules I have previously set has been applied to the passwords. And new patterns has been generated. This is very useful since we don’t have to manually add these.
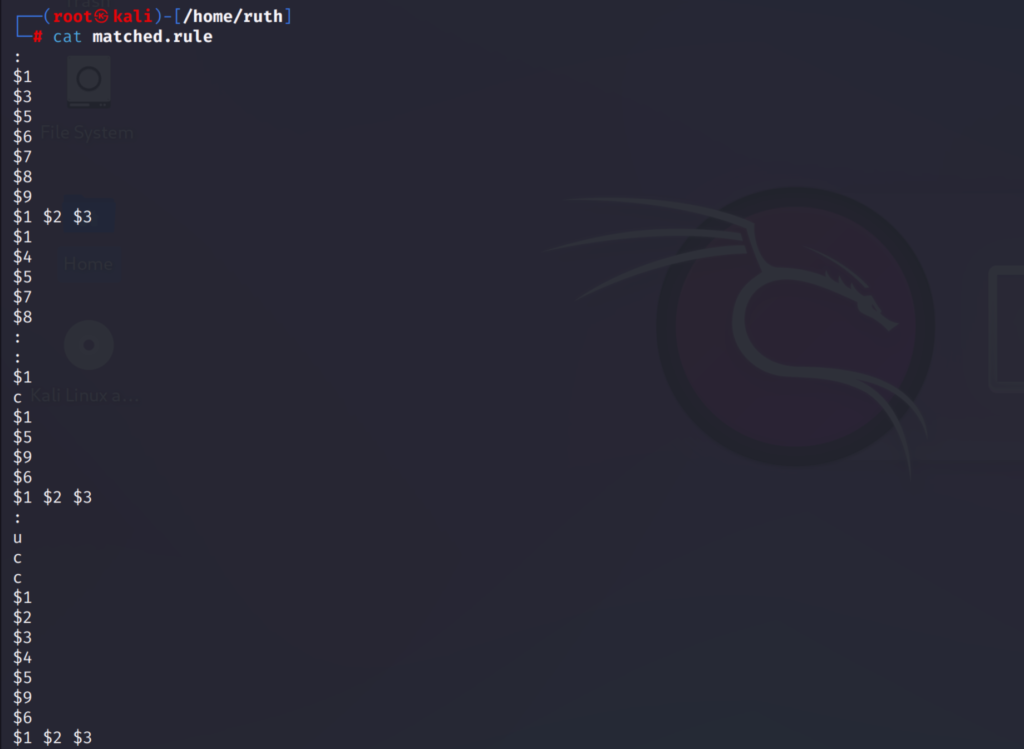
This is the file where the matched rules are stored. We can use this to check which rule has been applied to the password.
Conclusion
Hashcat is a great tool for security professionals to test the strength of passwords. And you guys can also test it out to see if your passwords are safe.
Anyways, we have pretty much learned a lot about hashcat and almost all its attack modes. It was a bit lengthy but it was fun to learn.
I hope this was useful and informative. Sayonara! 💜
Advertisement


