Introduction
Hi everyone!! Welcome back to the series of Introductory topics in ceh v10. So, this post is the continuation of my last post, kindly check it out. I am sure it will be useful for you. Anyways, let’s get started! Happy Learning! 😊
Phases of Hacking
Hacking is a step-by-step process and it requires the use of proper methods and tools. It’s planned well and executed. There are phases followed when hacking into a system, they are:
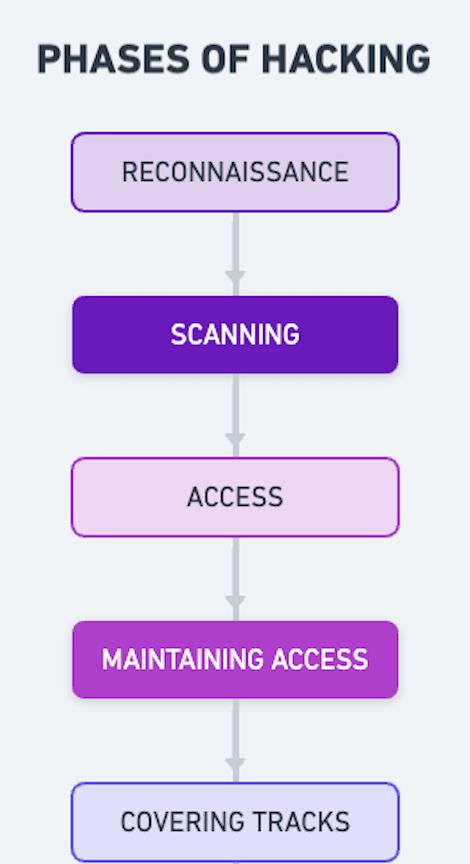
Reconnaissance
This is the information gathering phase.
Reconnaissance is the active or passive gathering of information.
Passive Recon: It’s the idea where we are not engaged in any way to the target.
- We are not directly engaging in the target.
- It’s the information which is available to everyone.
Active Recon: It’s the direct interaction with the target such as social engineering.
Scanning
Directly making a connection with the target. It is similar to active recon. Since we are using a scanning tool in this phase, it is called the scanning phase in hacking.
- It looks for vulnerabilities or any misconfiguration in the target system.
Access
The vulnerabilities are exploited to gain access to the target system.
- Privilege Escalation is also part of the access phase. This will give the root/administration access to the attacker.
- Some techniques are:
- injection attacks
- cross-site scripting
- security misconfigurations
- buffer overflows
- brute forcing
- social engineering
Maintaining Access
The access gained can be maintained and used to access other systems on the network.
Such as installing backdoors in the compromised machine to regain access whenever the attacker wants.
Covering Tracks
If the attacker has set up any backdoors or installed malware in the target system, they camouflage so that the victim won’t notice it. These might be located in some least expected kind of locations with normal file names.
They may also remove their logs from the log system to remain hidden.
Ethical Hacking: Who, When, Why and How?
Who?
Ethical hackers are cyber security professionals who use their skills and knowledge to find flaws within systems and networks and then patch them to avoid any attacks.
They are known as white hat hackers or penetration testers.
When?
Organizations hire ethical hackers to check the security of their systems through penetration testing before any potential attack occurs.
They can also investigate a security breach, find the root cause and prevent any future attacks.
Why?
Ethical hacking is important for the security of organizations’ confidential data. If any vulnerabilities are found before the attackers can they can be patched up quickly thus preventing a disaster.
It is also important that organizations conduct regular security assessments such as ethical hacking to ensure the safety of their data.
How?
Ethical hackers use their high technical skills and follow a structured method to conduct security assessments such as the hacking phases I have explained above:
- Information gathering
- Vulnerability Scanning
- Exploitation
- Privilege Escalation
- Maintaining Access
- Covering attacks
They also use a wide range of tools for various purposes to discover vulnerabilities and document them.
It is very important that ethical hacking must always be conducted with legal permission and adhere to a strict ethical code.
So guys, please don’t go around and hack others’ systems as you want 😅 it’s a very serious issue. Only a proper professional and that too with legal permission can hack into systems.
Conclusion
So, that’s it for today’s post. It was short but I believe it was informative and useful. There will be more posts in this series coming up! See you guys soon. Thank you for reading this far. Sayonara! 💜


