Introduction
Hi again everyone!! This is the second post in series where I will be talking about hacking and types of hackers. And also some of the approaches used in securing systems. So, basically these are all just some useful information which will be helpful for you. Anyways, Happy Learning! 😄
What is hacking?
Hacking is manipulating a system to make it do something that was not intended.
It’s a process of gaining unauthorised access to steal data and cause problems.
What makes a good hacker?
- they are smart
- they have a deep understanding of computer systems and networks
- they like challenges
Hacker Classifications
Script Kiddies/Skiddies
- People who can download exploits/scripts/tools and may have a basic understanding of computer network systems and misuse the tools against a live system not knowing what it is.
White hat
- They are professional ethical hackers who check for vulnerabilities in the system by hacking ethically with permission.
Black hat
- They are hackers who exploit vulnerabilities for their gain and get money by unethical means.
Grey hat
- These kinds of hackers may sometimes report the vulnerabilities to the organization although their hacking method is not legal. They may work as a professional or a criminal. It’s like a mix of both white hat and black hat.
Hacktivists
- These people use their hacking skills for sociopolitical ideologies. They protest using their technical knowledge and computers.
State-sponsored
- They are hackers who work for the government. They are very highly skilled in their work.
Cyber Terrorist
- They terrorise organisations by stealing their data. Such as holding ransoms.
Suicide Hacker
- They are not afraid of committing attacks and stealing data which will put people’s privacy at risk.
Key Approaches to Securing Systems
There are two key approaches to securing systems:
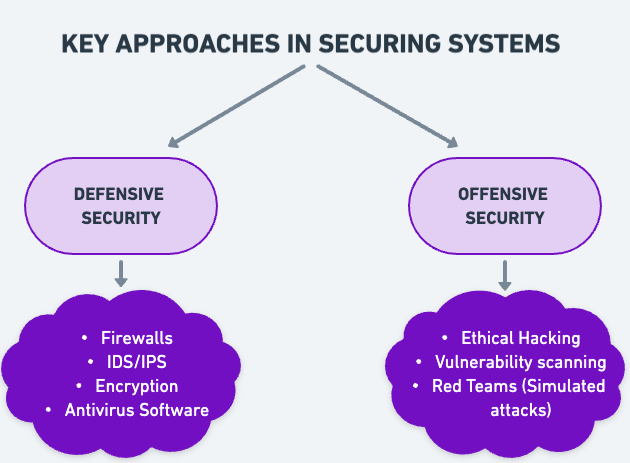
Defensive Security
The main goal is to build walls to prevent damage from attack. So, it’s just protecting the data from being stolen when an attack takes place.
Methods: The methods include
- Implementing firewalls
- Using Intrusion Detection and Intrusion Prevention System
- Using antivirus software
- Encryption of data
This kind of approach mainly focuses on creating a resilient system which means that the system must be able to recover quickly from challenging situations.
So who is responsible for this?
Security analysts, administrators and incident responders are required for this method of security.
Offensive Security
The main goal of this approach is to proactively identify vulnerabilities and weaknesses before the attackers do. Such as ethically hacking into the system, finding possible flaws and fixing them before they can be exploited by hackers.
Methods: The methods include:
- Penetration Testing (Ethical Hacking)
- Vulnerability scanning
- Security code reviews
- Simulated attacks
This approach also makes use of simulating attacks to find the attack methods that hackers can possibly use.
So who is responsible for this?
Ethical Hackers, penetration testers, security consultants and red team operators are mainly responsible for offensive security approaches.
Offensive security also has three types of offences:
Annoyance: Some of the penetration testing might cause some disruption to the attackers and not let them attack and also using honey pots and make them waste their time.
Attribution: Identify the possible attack methods and tools which the hacker could use.
Attack: Simulating attacks to test defences and identify weaknesses.
Conclusion
The world of hacking is very interesting and there is a lot to learn so it will be continued further..I hope it was useful for you. See you in next post. Sayonara! 💜


