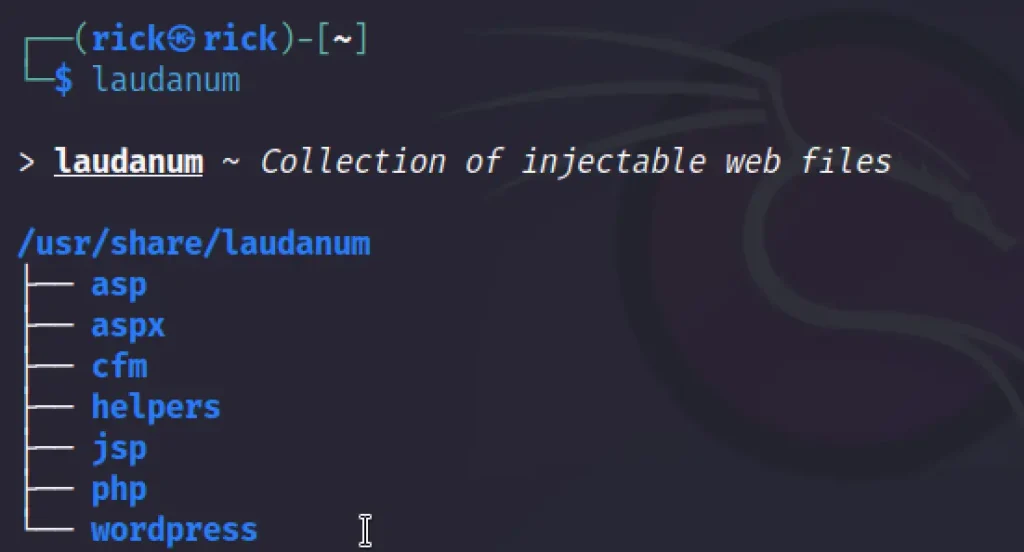
Introduction Laudanum
Laudanum, is a collection of scripts and binaries tailored for auditing and exploiting security vulnerabilities in web applications.
We must emphasize that Laudanum serves exclusively for ethical hacking and security testing purposes. Unauthorized or malicious use of such tools can have severe legal consequences, so responsible usage is paramount.
To Install and Know More About Laudanum [Click Here]
Advertisement
Video
Key Features of Laudanum
1. Web Application Testing
Laudanum specializes in identifying and exploiting vulnerabilities in web applications. Its extensive toolkit of scripts and tools allows ethical hackers to comprehensively assess the security of web servers, web applications, and web services.
2. Versatile Payloads
Laudanum offers a range of payloads for various web vulnerabilities, including SQL injection, cross-site scripting (XSS), and remote code execution. This versatility allows security professionals to adapt to different testing scenarios effectively.
3. Customization
One of Laudanum’s strengths lies in its flexibility. Users can customize payloads and scripts to target specific vulnerabilities or scenarios, enhancing its effectiveness in security assessments.
4. Educational Value
Beyond its practical applications, Laudanum serves as an educational tool. Security enthusiasts and professionals can learn about common web vulnerabilities and attack vectors by studying its source code and documentation.
Responsible Usage
It cannot be stressed enough that the ethical and legal use of Laudanum, and all hacking tools, is essential. Always obtain explicit authorization before conducting security assessments on any system or application. Responsible usage not only ensures compliance with the law but also upholds ethical standards within the field of cybersecurity.
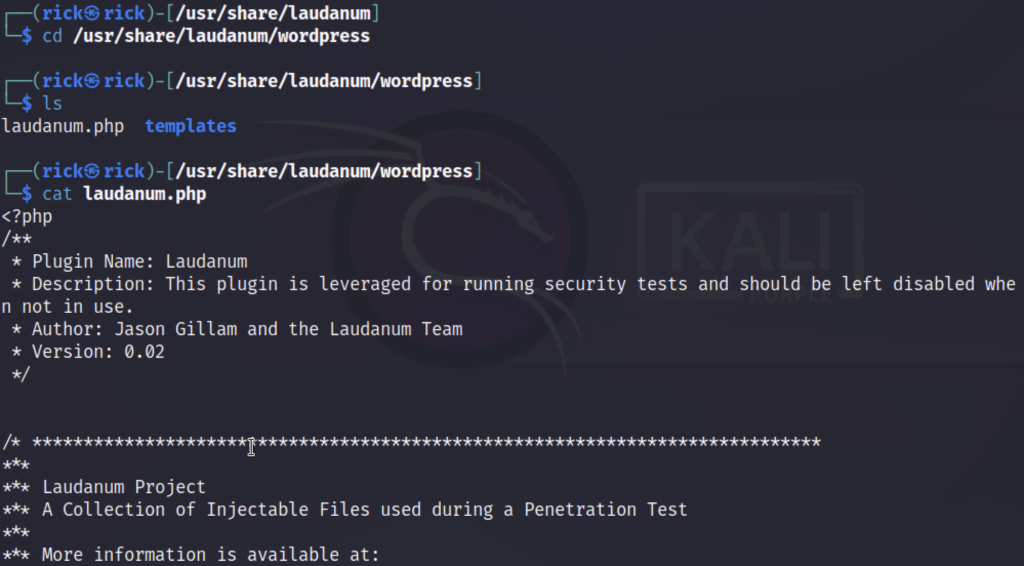
Getting Started with Laudanum
For those interested in exploring Laudanum as part of their ethical hacking endeavors, here’s a simplified guide to help you get started:
- Install Kali Linux: Begin by installing Kali Linux on a dedicated system or within a virtual machine.
- Update and Upgrade: Ensure your Kali Linux installation is up to date by running
sudo apt-get updateandsudo apt-get upgradecommands. - Accessing Laudanum: Laudanum can be found within Kali Linux’s extensive toolset. Locate and run it through the terminal or the Kali Linux menu.
- Documentation: Familiarize yourself with Laudanum’s documentation to understand its capabilities and usage instructions thoroughly.
- Practice Ethical Hacking: Before using Laudanum in a real-world scenario, practice on controlled environments or intentionally vulnerable web applications to hone your skills.
Conclusion
In the realm of cybersecurity, tools like Laudanum play a crucial role in helping security professionals identify and mitigate potential threats.
When used responsibly and with proper authorization, Laudanum can be a valuable asset in a cybersecurity professional’s toolkit.
However, ethical hacking is a complex field that requires continuous learning and adherence to ethical standards. Always remember to obtain permission and follow legal guidelines when using hacking tools like Laudanum.
Read More: SQLMAP Tutorial


