Introduction
In this post, you will learn the security posture and the three postures in cybersecurity which is often spoken in the books and also the cybersecurity experts.
What is security posture?
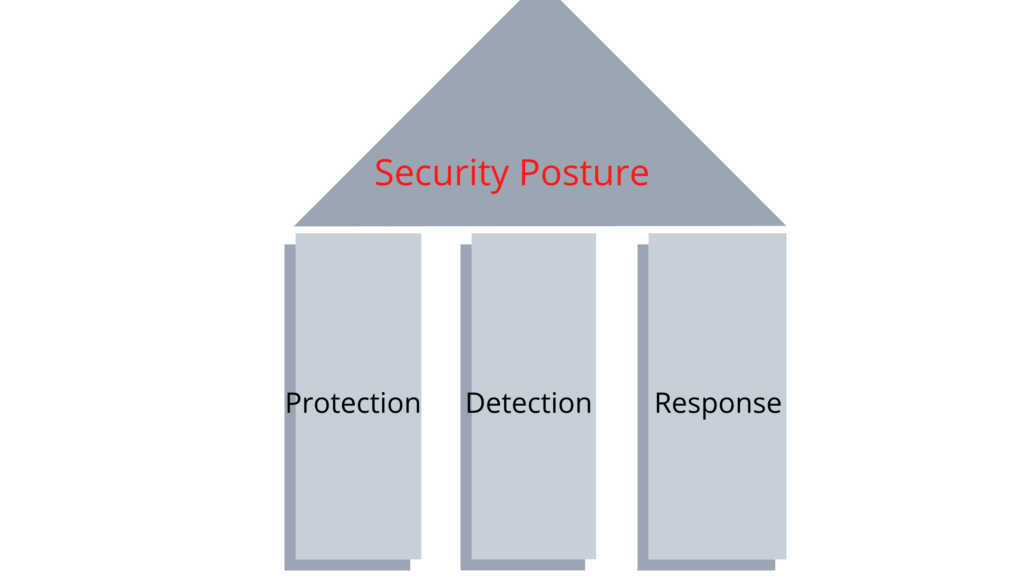
Security posture term means overall cybersecurity strength of an organisation. The security system is very important in an organisation. Three pillars hold the security posture. The three pillars are protection, detection and response.
The security of an organisation will reduce the cyberattacks against the company. When I say the term security posture it includes network, Internet, Infrastructure of a network, data security, red team, penetration testing, incident response team, assets etc.,
Without a security structure, the employee and the company and also the client’s data are very vulnerable. The client data is vulnerable and also it is very valuable If there is a breach of the client data. There is going to be a big headache for the company. Because the company should be responsible and also compensate the client.
So, the company should ensure security and give end-to-end encryption for the client.
Also Read: What is prismdump
The three security posture
- Protection
- Detection
- Response
Protection – security posture
The protection ensures the client’s assets and the company assets are safe. So, protection includes firewall, 2FA and MFA and also VPN, TOR, Encryption, HTTPS, Patching, SSH, SSL/TLS etc.,
Here asset means valuable data’s such as a file, email, identity, anonymity, privacy. Anything which is valuable data for the users is an asset.
Detection
Suppose the organisation or the targeted user is affected because of the cyberattacks and the detection is one of the security postures. The incident response(IR) team should be ready for an incident response attack at any time. And ready to detect any time of malware or attack.
Response
Responding is the final in security infrastructure. The blue and the red team should be able to give a proper response to the press and the clients in a neat report. Responding to the attack also giving a transparent response to their clients and the press.
Also Read: What is PCPdump
Also Read: What is Nessus an overview