Introduction
In this post, you will learn what is hping3 and how does it works and also I have written every command and do check the video format of the post . Don’t mind my Indian voice. Finally, support me by sharing this post DO IT IT’S MY ORDER. Just kidding
Video:
What is hping3?
Hping-3 is a tool that is pre-installed in a kali machine and In simple words, the tool can send packets throughout the network and could see the flow of the network in an organisation. This is the simplest explanation for a 5 yo kid
By sending the packets throughout the network the red team members will identify any problem in the network and even check for the firewall.
This tool is good in the good hands but if it is in EVIL hands then the tool is a devil ????????
Also Read: Information gathering using goofile
Advertisment
Who developed the hping3 tool
The tool was developed by Salvatore Sanfilippo and he seems to be a nerd and I have given the Author’s link and also the download from GitLab and if you want to install the tool in Linux distributaries just enter sudo apt-get install hping3
What all the hping3 tool can do
- Firewall testing
- Advanced port scanning
- Network testing.
- MTU discovery (Manual path discovery)
- Advanced traceroute,(All protocols are supported)
- Remote OS fingerprinting
- Remote uptime guessing
- TCP/IP stacks auditing
- hping can also be useful to students that are learning TCP/IP.
Useful commands in hping3 tool
- -c –count: packet count
- –faster: alias for -i u1000 (100 packets for second)
- –flood: sent packets as fast as possible. Don’t show replies.
- -V –verbose: verbose mode
- -0 –rawip: RAW IP mode
- -1 –icmp: ICMP mode
- -2 –udp: UDP mode
- -8 –scan: SCAN mode.
- -9 –listen: listen mode
- -a –spoof: spoof source address
- -C –icmptype: icmp type
- -K –icmpcode: icmp code
- -L –setack: set TCP ack
- -F –fin: set FIN flag
- -S –syn: set SYN flag
- -R –rst: set RST flag
- -A –ack: set ACK flag
- -X –xmas: set X unused flag (0x40)
- -Y –ymas: set Y unused flag (0x80)
Advertisment
How to use the hping3 tool?
Follow my steps to become a pro in this tool, Hmm it’s the truth
Example1: Standard scan
In this example let’s see how to send SYN packets to the target IP address
hping3 -S 192.168.149.1

In the place of -S you could add
-L –setack set TCP ack
-F –fin set FIN flag
-S –syn set SYN flag
-R –rst set RST flag
-P –push set PUSH flag
-A –ack set ACK flag
-U –urg set URG flag
-X –xmas set X unused flag (0x40)
-Y –ymas set Y unused flag (0x80)
Wait my friend stop here go and give a try on all the above commands first ????
Example2: Port scan
Now let’s specify for port let the port here be 80, there are 65,535 port try on only open ports
hping3 -S 192.168.149.1 -p 80
-p for specifying the port
-S is SYN , (You could enter any protocol you want as I mentioned in Example1)

Example3: No of packet
Now, let’s send the packets whatever you think. It’s like specifying how many packets to send.
hping3 -S 192.168.149.1 -p 80 -c 5
-S SYN flag
-p Specify the port
-c No of packets to send

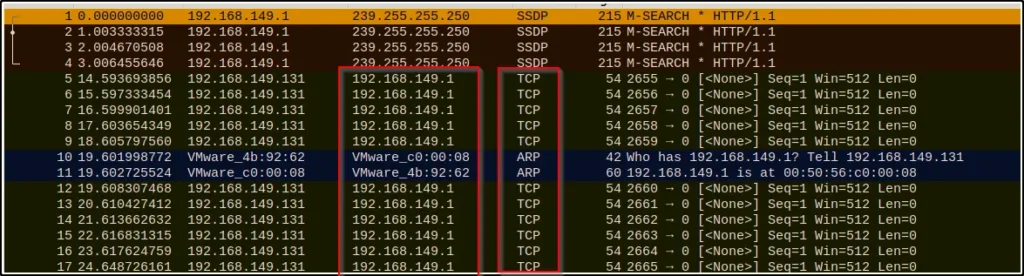
Example4: TCP
Let’s send some TCP packets through the target
hping3 192.168.149.1

Result in Wireshark ????
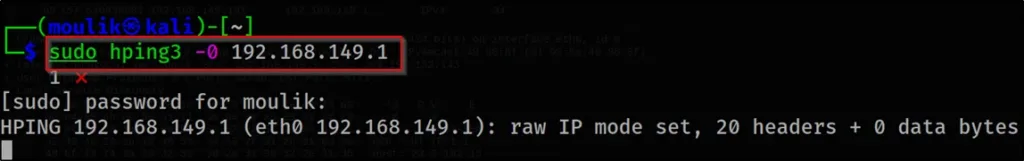
Example5: Raw IP
Now, Let’s send raw IP through the network
hping3 -0 192.168.149.1
Result viewed in wireshark????
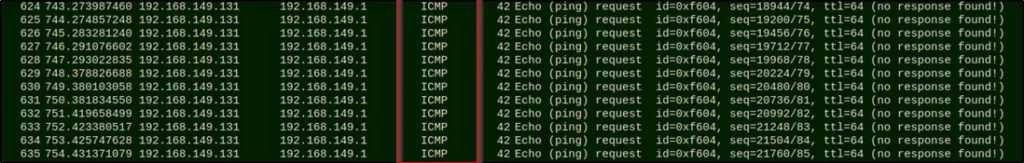
Example6: ICMP
Let’s send some ICMP packets through the IP address and let’s view in Wireshark
hping3 -1 192.168.149.1

Result in Wireshark ????????
Example7: UDP
Now let’s send some UDP packets through the target IP address and also let’s view the result in Wireshark
hping3 -2 192.168.149.1
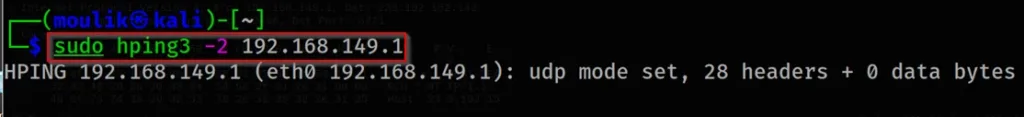
Result in Wireshark ????

Example8: Between port scan
Now let’s scan for a particular port in the target domain
hping3 -8 1-30 -A 192.168.149.1
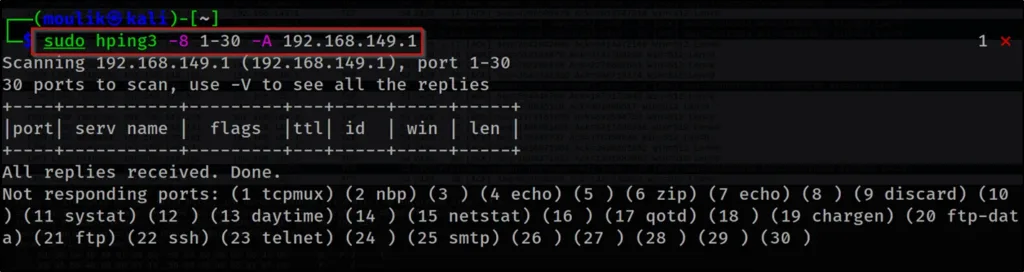
Example9: Listen
Okay now let’s see how to listen to an IP address
hping3 -9 192.169.149.1
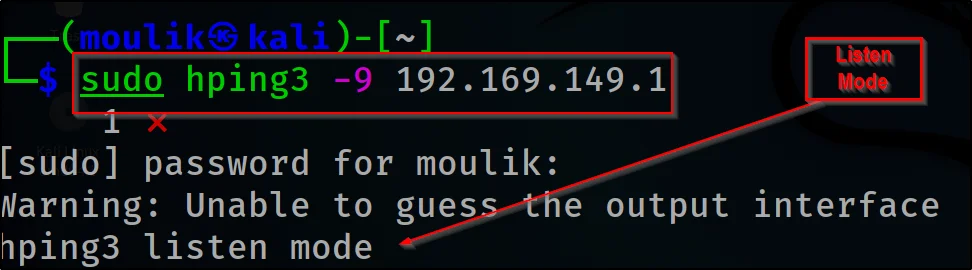
Example10: Verbose
Let’s enter verbose so, you could see what is all the packets are moving
hping3 -2 192.169.149.1 -V
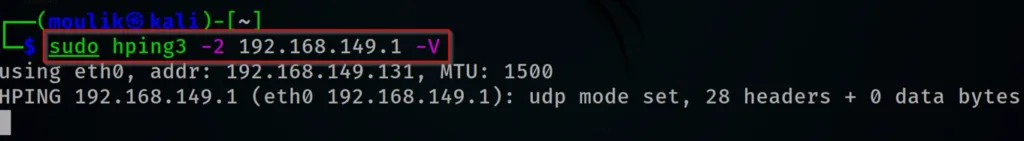
Advertisment
Example11: Specifying port
Scanning for specific ports in any packets it may be UDP, IP, TCP, ICMP whatever to scan a specific port in it just enter ????????
hping3 -1 192.168.149.1 -p 80
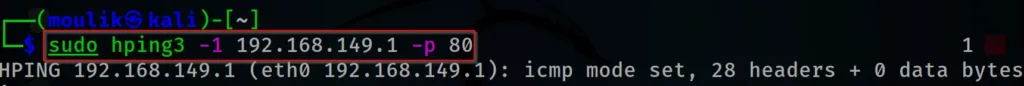
Example12: Sequence Number
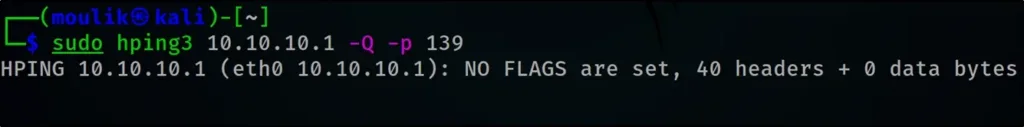
Collecting initial sequence number
hping3 192.168.1.103 -Q -p 139

Example13: Firewall
Let’s find firewalls and timestamps
hping3 -S 72.14.207.99 -p 80 --tcp-timestamp
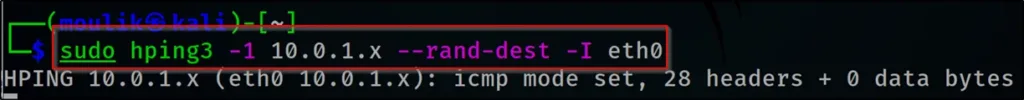
Example14: Subnet
Scanning an entire subnet for live host
hping3 -1 10.0.1.x --rand-dest –I eth0
Example15: HTTP
Intercepting all traffic containing HTTP signatures
hping3 -9 HTTP -I eth0

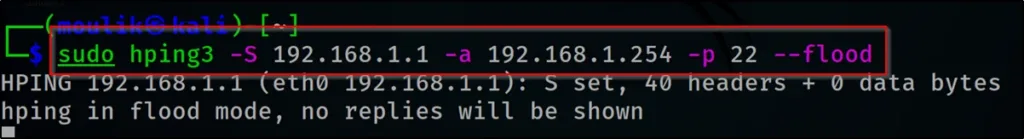
Example16: SYN Flood
Doing an SYN flooding on a victim
hping3 -S 192.168.1.1 -a 192.168.1.254 -p 22 --flood
Hping3 Conclusion
This is the best tool to learn the Protocols and how the packets are moving and so on… This is the best tool to learn TCP, UDP and IP. Comment down below if you like the post…
Advertisment
Also Read: Information gathering using Whatweb
Also Read: Wappalyzer information gathering



This is the best blog post for full tutorial on hping3.
This really helped me 👏
Thanks man. keep supporting
best hping3 content on the internet, Got every information in hping3 tool
Thanks bro keep supporting