Introduction
In this post, Let’s see how to decrypt https traffics using wireshark and SSLKEYLOGFILE and below is the video format if the post, Check it out 👇🏾
Video
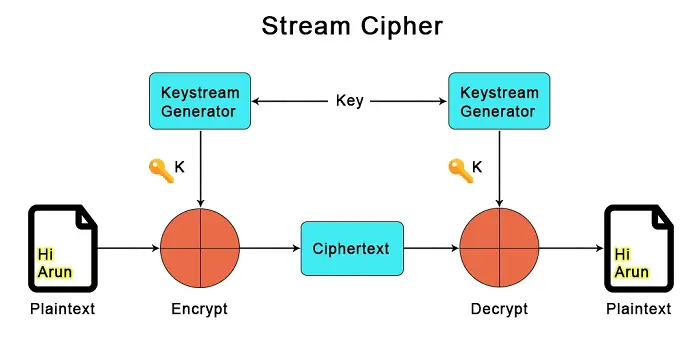
Understanding HTTPS Encryption
Before diving into the decryption process, it’s crucial to comprehend the basics of HTTPS encryption.
Hypertext Transfer Protocol Secure (HTTPS) is a secure version of HTTP, designed to ensure secure communication between a user’s browser and the web server.
Advertisement
This is achieved through cryptographic protocols that encrypt data during transmission, safeguarding it from unauthorized access.
Prerequisites
To decrypt HTTPS data effectively, certain prerequisites must be in place:
1. Wireshark Installation
Firstly, you need to have Wireshark installed on your system. Wireshark is a widely used network protocol analyzer that enables the capture and examination of network traffic.
2. SSL Key
To decrypt the HTTPS data, you will require the SSL key used by the web server. This key is essential for decrypting the encrypted traffic. It’s important to note that accessing the SSL key must be done with utmost caution, as it holds the key to your website’s security.
Advertisement
SSL session keys on Linux
Before doing the below step make sure you have did the update and upgrade ????????
sudo apt-get update
- Log in to Linux.
- Close all Firefox and Chrome browsers.
- Open a terminal for command line access.
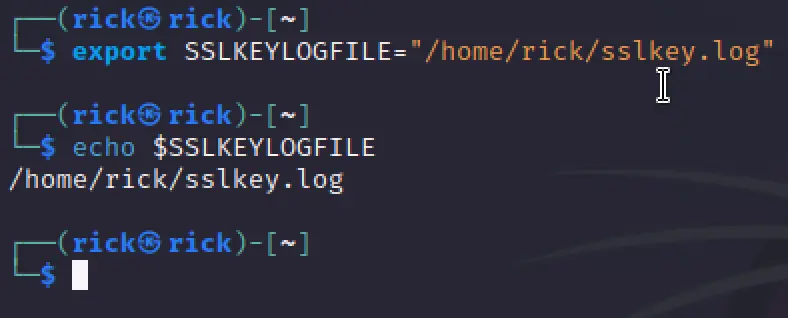
- Set the SSLKEYLOGFILE environment variable for your account by using the following command syntax:
export SSLKEYLOGFILE="/home/<account_name>/sslkeyfile" export SSLKEYLOGFILE="/home/rick/sslkey.log"
To check if the SSLKEYLOGFILE path is set properly use the below command.
echo $SSLKEYLOGFILE
Unfortunately in my kali linux chrome didn’t work properly so I installed chromium for this task.
Now open Wireshark and start capturing the any interface. Then on terminal type chromium&
Now you can see the packets capturing in the wireshark after entering chromium&. If we open the sslkey.log we can see session logs.
We can add theses session logs to wireshark to decrypt the HTTPS traffics.
Load the SSL key log file in Wireshark
- Open Wireshark on your client system.
- Go to Edit > Preferences > Protocols > TLS.Note: For Wireshark versions earlier than 3.0.0, go to Edit > Preferences > Protocols > SSL. For Mac go to Wireshark > Preferences > Protocols > TLS.
- For the (Pre)-Master-Secret log filename, select Browse and locate the SSL log file you created.
- Select OK.
- Open the packet capture file in Wireshark.
- In the Wireshark packet window, select previously encrypted packets to view unencrypted application data.

Conclusion
It’s so simple and If you have any doubts ask me in discord and if you dont know how to set env for
Well we have successfully decrypted the https traffics and hope you like it. See you in next post.
Advertisement



A fascinating discussion is worth comment. I believe that you ought to publish more about this topic, it might not be a taboo subject but usually people do not talk about these issues. To the next! Cheers!!
דירות דיסקרטיות בתל אביב
Thankyou ❤️