Introduction:
In this post, you will learn what is nikto and how does it work and a full command tutorial and by end of this post, you will be more familiar with the tool. There is also video format of the post below check that also
Video:
What is Nikto
Nikto is a web-based vulnerability scanner, It is open-source software written in Perl language. The primary target of the tools is to do vulnerability scanning.
This tool scans 6,800 vulnerabilities that are commonly available on the sites. The tool also scans 250 platforms from an unpatched site. Also finds some vulnerability in the webserver files. I will use this tool very often, Mostly this tool will be caught in IDS (Intrusion detection sensor) or IPS (Intrusion Prevention sensor).
Also Read: Zenmap full tutorial
There are some alternative tools such as Metasploit, comparing to Metasploit, Nikto is the best tool. Bug bounty hunters use this tool a lot and even hackers use this tool.
Advertisement
Who developed the nikto tool
The tool was developed by Chris Sullo & David Lodge and I wonder how they kept the logo for this tool. And I am in love with this logo. Below are the links to the tool
Features in nikto tool
- SSL Support (Unix with OpenSSL or maybe Windows with ActiveState’s
- Perl/NetSSL)
- Full HTTP proxy support
- Checks for outdated server components
- Save reports in plain text, XML, HTML, NBE or CSV
- Template engine to easily customize reports
- Scan multiple ports on a server, or multiple servers via input file (including nmap output)
- LibWhisker’s IDS encoding techniques
- Easily updated via command line
- Identifies installed software via headers, favicons and files
- Host authentication with Basic and NTLM
- Subdomain guessing
- Apache and cgiwrap username enumeration
- Mutation techniques to “fish” for content on web servers
- Scan tuning to include or exclude entire classes of vulnerability
- checks
- Guess credentials for authorization realms (including many default id/pw combos)
- Authorization guessing handles any directory, not just the root
- directory
- Enhanced false positive reduction via multiple methods: headers,
- page content, and content hashing
- Reports “unusual” headers seen
- Interactive status, pause and changes to verbosity settings
- Save full request/response for positive tests
- Replay saved positive requests
- Maximum execution time per target
- Auto-pause at a specified time
- Checks for common “parking” sites
Advertisement
Useful commands in Nikto tool
-config+ :Use this config file
-Display+ :Turn on/off display outputs
-dbcheck : check the database and other key files for syntax errors
-Format+ :save file (-o) format
-Help : Extended help information
-host+ :target host/URL
-id+ : Host authentication to use, the format is id: pass or id:pass: realm
-output+:Write output to this file
-nossl : Disables using SSL
-no404 : Disables 404 checks
-Plugins+ :List of plugins to run (default: ALL)
-port+ :Port to use (default 80)
-root+ :Prepend root value to all requests, the format is /directory
-ssl : Force SSL mode on port
-timeout+ :Timeout for requests (default 10 seconds)
How to work with the Nikto tool ❓
Just follow the below example and I am sure by end of this post you will be familiar with the tool and If you need any additional information on the Nikto tool then watch the YT video at the top.
Example1:
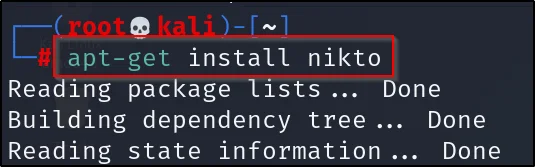
Installing the Nikto tool
sudo apt-get install nikto
Example2:
Let’s do a standard scan in nikto, which is directly scanning the target
nikto -h <IP/domain>
nikto -h example.com
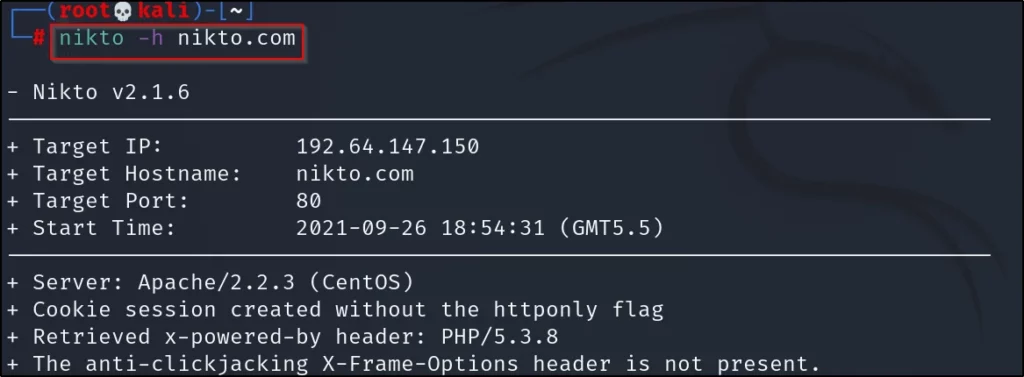
*Sorry about the scan it is nikto.com, you can enter your own target
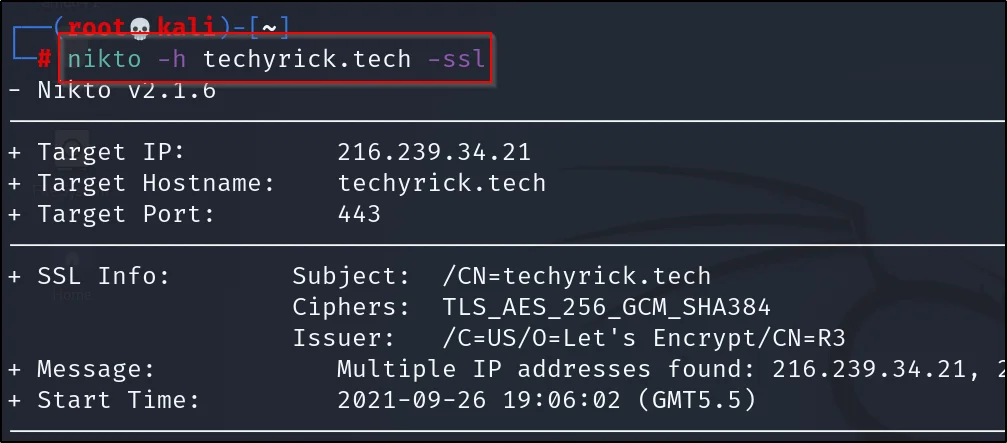
Example3:
Running a scan on target SSL or TLS
nikto -h example.com -ssl
Advertisement
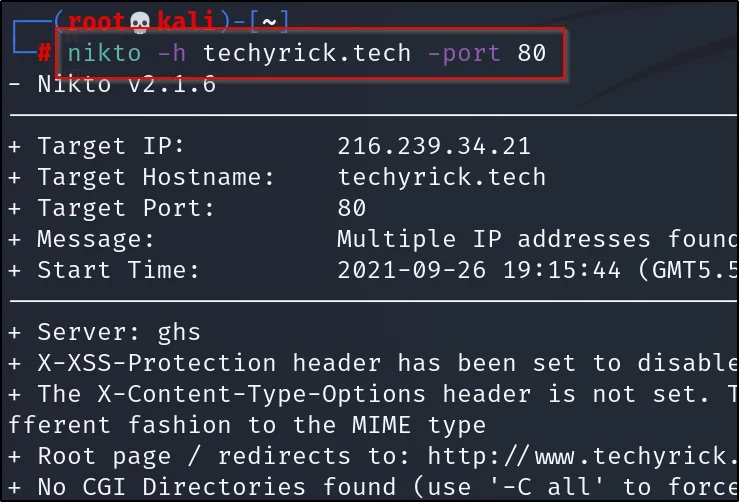
Example4:
Scanning specific port on nikto
nikto -h example.com -port 80
Example5:
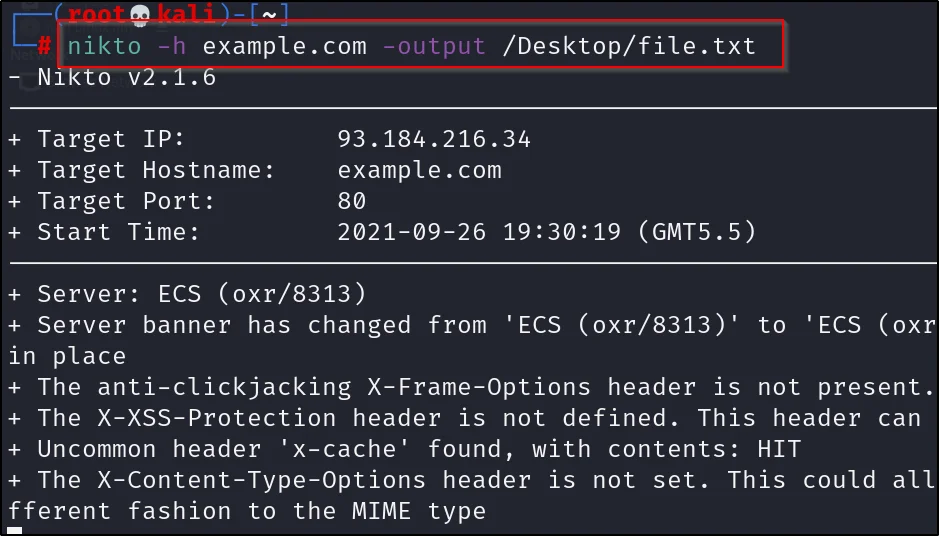
Saving the scan in an output
nikto -h example.com -output /Downloads/file.txt
You can specify the path you want
Example6:
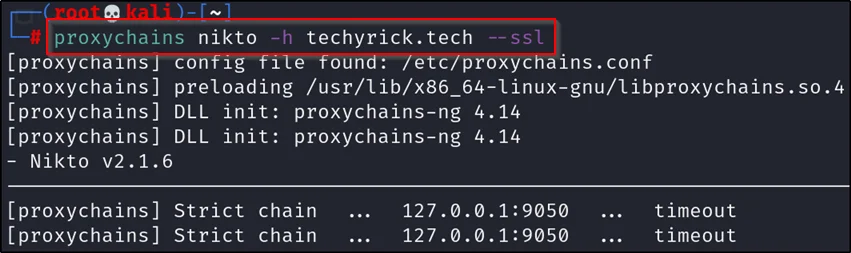
Scanning anonymously using Nikto is very easy just add proxychains in front of the command
proxychains nikto -h example.com
Example7:
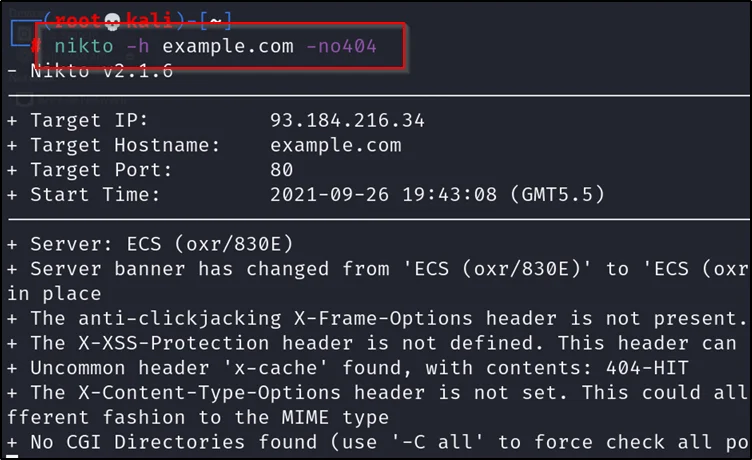
Ignoring certain codes HTTP codes
nikto -h example.com -no404
Example8:
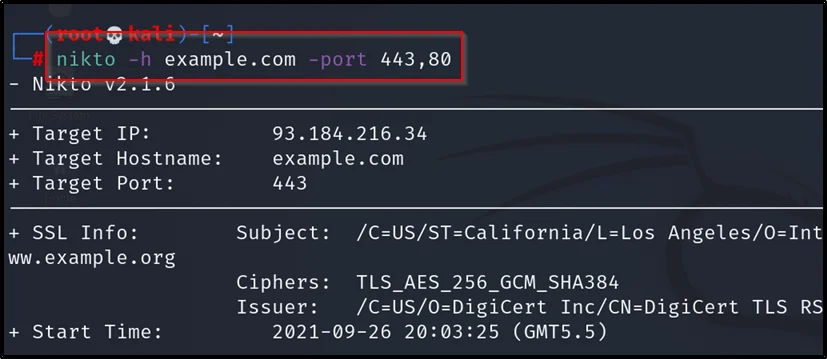
Scanning multiple ports
nikto -h example.com -port 44,80,22
Conclusion:
Some alternatives for Nikto is Arachni, ZAP, searchsploit, Nessus, openVAS and I specifically love this nikto tool and just give it a try to this tool. Overall this is one of the best tools to scan for vulnerabilities and see you in the next post.
Advertisement
Also Read: Legion full tutorial from noob to pro
Also Read: Angry IP scanning full tutorial




