Introduction
In this post, You will learn what is openvas and how to set it up and also you will be learning how to use this tool.
Below is the video format of the post, check that it also
Video
What is openvas ❓
OpenVAS (Open Vulnerability Assessment System) is a free and open-source vulnerability scanning and management platform.
It allows users to scan their networks and systems for known vulnerabilities and provides a set of tools for managing and mitigating those vulnerabilities.
OpenVAS is composed of several components, including a database of known vulnerabilities, a scanner that can detect those vulnerabilities, and a management interface for reviewing and addressing the vulnerabilities that are found.
It is designed to be used by network administrators and security professionals to help secure their systems and networks.
OpenVAS is available for a variety of platforms, including Linux, and can be downloaded and installed for free.
It is updated regularly with new vulnerabilities and security checks.
Advertisement
Who developed open-vas
OpenVAS (Open Vulnerability Assessment System) is a free and open-source vulnerability scanner developed by the German company Greenbone Networks GmbH.
It was originally developed as a fork of the Nessus scanner by Renaud Deraison and was later acquired by Greenbone Networks.
The openVAS is designed to provide a comprehensive and flexible solution for vulnerability assessment and management and is widely used by security professionals and organizations.
How to setup Openvas
To set up open vas open your terminal and enter the below command.
sudo gvm-setup
If it works you will be having the username and password. The username is going to be admin and the password is will be displayed in the terminal you can just copy that and save it.
If you are having a PostgreSQL problem then just watch this youtube video I have posted [click here] to watch.
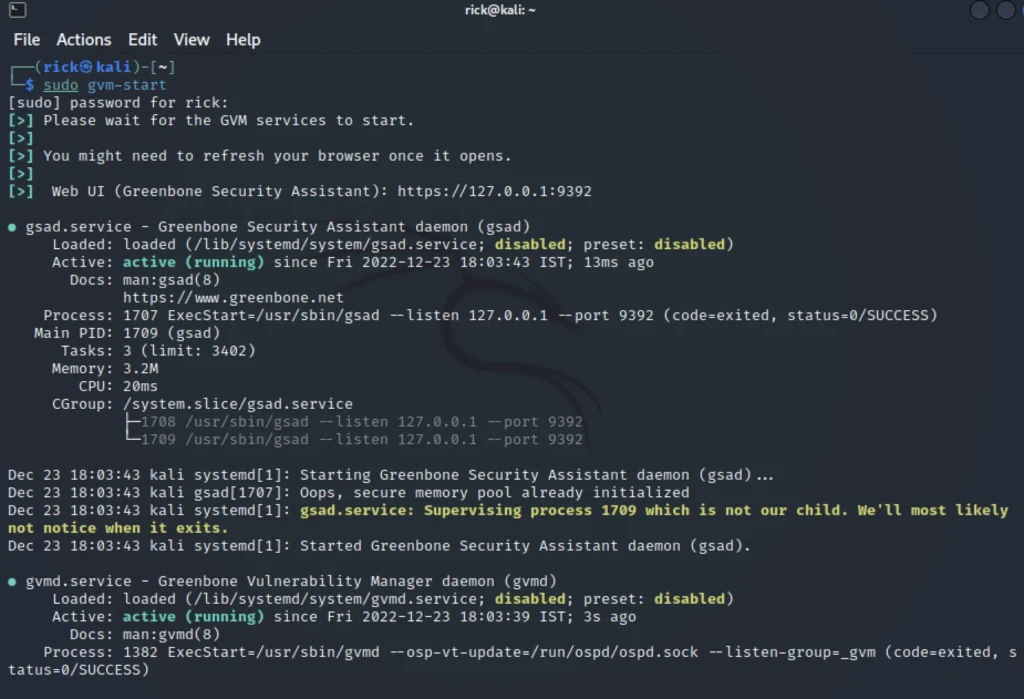
To run the open vas, Just enter the below command in terminal.
sudo gvm-start
You will be having a link and just copy it and past in the browser and then enter the username and password.
How to use open vas
It’s really damn easy to use openvas, At the top right corner you could see the profile where can log out and check the session duration etc.,
There are 8 menus in openvas they are;
- Dashboard
- Scans
- Assets
- Resilience
- Secinfo
- Configuration
- Administartion
- Help
Except for resilience and help menu all other menus are used regularly.
Dashboard
In the dashboard we can see information such as the scan which is in queue and which has been completed.
And also classify the severity of the vulnerability in the particular system etc.,
- Scanner management: This allows users to configure and manage the OpenVAS scanner, including setting up scan tasks, configuring scan settings, and monitoring the status of scans.
- Scan results and reports: The dashboard provides access to the results of completed scans, including details of any vulnerabilities that were identified. Users can also generate reports based on scan results, which can be useful for documenting findings or presenting results to stakeholders.
- Vulnerability management: Lastly the dashboard includes tools for managing vulnerabilities that are identified during scans, including the ability to track the status of vulnerabilities, assign them to specific users for remediation, and set deadlines for remediation.
Overall, the OpenVAS dashboard is a powerful and user-friendly tool that provides a comprehensive set of features.

Scans
In the scans, we could see 4 submenus they are,
- Tasks
- Report
- Results
- Vulnerabilites
Tasks
When creating a task in OpenVAS, users can specify a variety of options, including:
- Target: The target of the scan can be a specific host or network, or a range of IP addresses.
- Scanner profile: Users can choose from a range of predefined scanner profiles, which define the types of vulnerabilities that the scanner will look for and the level of detail that will be included in the scan results.
- Scan options: Users can configure a variety of options that control how the scanner performs the scan, including the level of intensity (speed versus thoroughness), the types of tests to be performed, and the level of access to the target system.
- Scheduling: Tasks can be set to run on demand, or they can be scheduled to run at a specific time.
Once a task has been created and configured, it can be launched through the OpenVAS dashboard and the result can be seen in the dashboard.

Reports
In the reports we can see the scan result and the different types of reports which can be extracted.
There are several types of reports that can be generated in OpenVAS, including:
- Executive summary: This type of report provides a high-level overview of the scan results, including a summary of the vulnerabilities identified and their severity. It is intended for non-technical audiences and is often used to present scan results to management or other stakeholders.
- Full report: This report provides a more detailed view of the scan results, including information about each individual vulnerability identified, along with recommendations for remediation.
- Host report: This report provides detailed information about the vulnerabilities identified on a specific host or system.
- Compliance report: This report compares the scan results against a set of compliance standards or requirements, and indicates which vulnerabilities are compliant or non-compliant.
OpenVAS reports can be generated in a variety of formats, including HTML, PDF, and XML etc.,

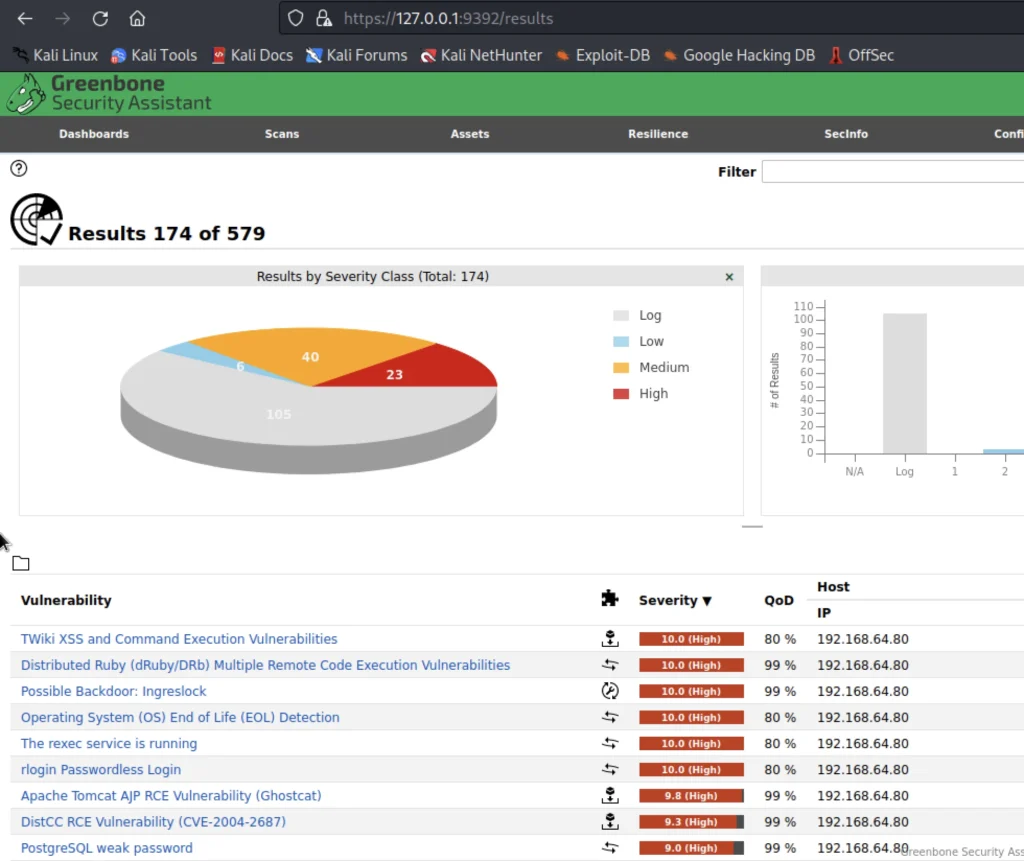
Results
In the resulting menu, we can see information such a vulnerability and level severity.
Vulnerabilities
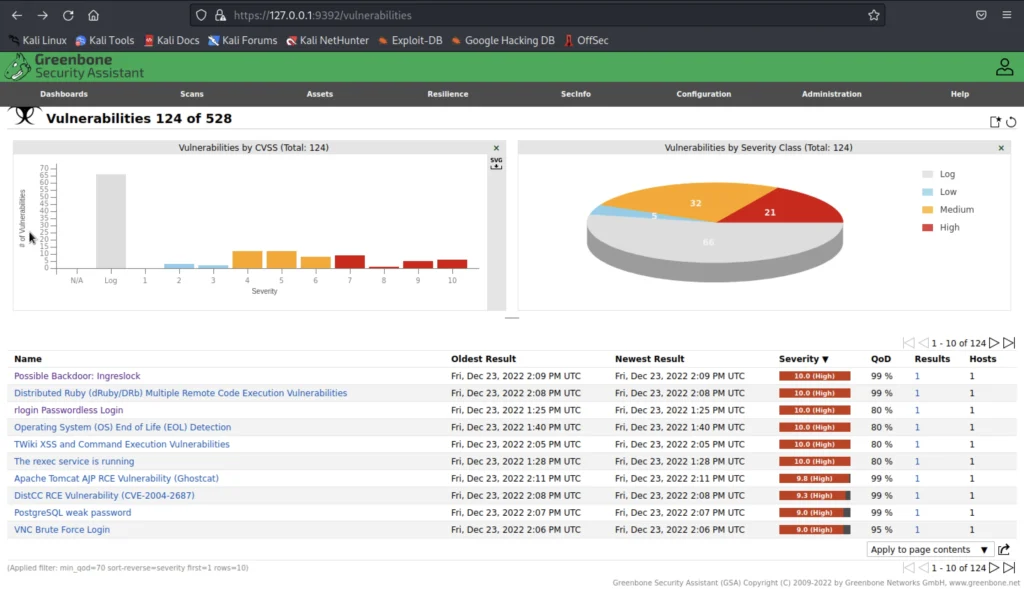
In the vulnerability sub-menu we could see information about the vulnerability found in detailed information.
If we click the vulnerability we could see more information about the specific vulnerability found.
Also, we could see a bar and pie chart which separates the level of severity.
Configuration
In configuration, we could see some sub-menus such as;
- Targets
- Port list
- Credentials
- Scan config
- Alerts
- Schedules
- Report formats
- Scanner
- Filter
- Tags
There are several configuration options available in OpenVAS that allow you to customize how the vulnerability scanner behaves. Some of the options you can configure include:
- Scan targets: Moreover specify the IP addresses, hostnames, or ranges of IP addresses that you want OpenVAS to scan.
- Scan options: You can choose the type of scan you want to run (e.g. a full scan, a quick scan, or a custom scan)
- Scan policies: OpenVAS includes a set of pre-defined scan policies that you can use to control how the scanner behaves. You can also create custom scan policies to fit your specific needs.
- Authentication: If you want to scan systems that require login credentials in addition you can configure OpenVAS to use those credentials during the scan.
- Alerts and notifications: You can configure OpenVAS to send alerts or notifications when it finds vulnerabilities.
It’s equally important to carefully review and configure these options to ensure that your scans are effective and efficient.

Adminstartions
There are several aspects of OpenVAS administration that you may need to consider.
Some common tasks that may be involved in OpenVAS administration include:
- Setting up and configuring the OpenVAS software: This may involve installing and configuring the OpenVAS software on a server, setting up scan targets, and configuring scan options and policies.
- Managing users and access: If you have multiple users accessing the OpenVAS system, you may need to manage user accounts and permissions, such as setting up user roles and defining what actions different users are allowed to perform.
- Running scans: You will need to regularly run scans using OpenVAS to identify vulnerabilities in your systems and networks. In addition, scheduling scans to run automatically or running scans manually as needed.
- Reviewing and prioritizing scan results: After a scan is complete, you will need to review the results and determine which vulnerabilities need to be addressed first. This may involve prioritizing vulnerabilities based on their severity level, and coordinating with other team members to ensure that vulnerabilities are fixed in a timely manner.
- Maintaining and updating the OpenVAS software: It’s important to keep the OpenVAS software up to date with the latest security patches and updates. In addition, updating the software and any related plugins or tools on a regular basis.

Conclusion
Finally, this is an awesome tool for vuln analysis and hope you like the post, If you have any doubts just comment down below or take a look at the video.
Advertisement
Also Read: Nikto full tutorial