Introduction
In this post, You will learn what is p0f and how does the tool work and below is the video format of the post, check it out.
Video
What is p0f tool
p0f stands for Passive Traffic Analysis. Mostly this tool is used at the passive information gathering point.
P0f is an OS Fingerprinting and Forensics Tool that uses a variety of complex, absolutely uninvolved traffic fingerprinting systems to recognize the players behind any accidental TCP/IP correspondences (frequently as little as a solitary ordinary SYN) without meddling in any capacity.
Adaptation 3 is a finished change of the first codebase, fusing a critical number of enhancements to arrange level fingerprinting, and acquainting the capacity with reason about application-level payloads.
Advertisment
Features in p0f tool
- Exceptionally adaptable and very quick recognizable proof of the working framework and programming on the two endpoints of a vanilla TCP association – particularly in settings where NMap tests are impeded, excessively lethargic, questionable, or would essentially set off alerts.
- Estimation of framework uptime and organization hookup, distance (counting geography behind NAT or parcel channels), client language inclinations, etc.
- Robotized recognition of association sharing/NAT, load adjusting, and application-level proxying arrangements.
- Location of customers and servers that fashion decisive explanations like X-Mailer or User-Agent.( Forensics Tool)
How to use p0f tool
It is really very easy to use the tool, Firstly you should compromise the target’s network using the aircrack-ng.
Once you have compromised the target network just enter 👇🏾
p0f -i <network>
In this place i will enter eth0 as the network you may enter wlan0 or what ever wireless network you compromised you can enter.
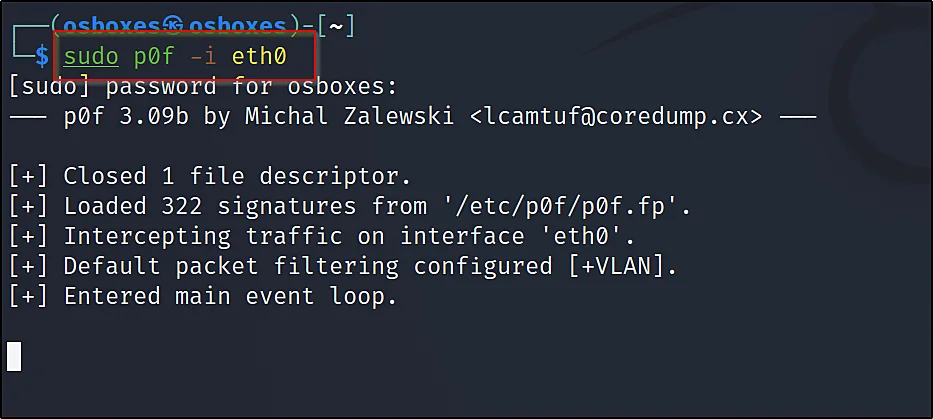
p0f -i eth0
If you are connected to the target networ wait for the target to access the web browser as soon as the target access you will get information such as the service and the OS.
In my case, As I am using eth0 I don’t want to wait for the target I just wanna open my browser.
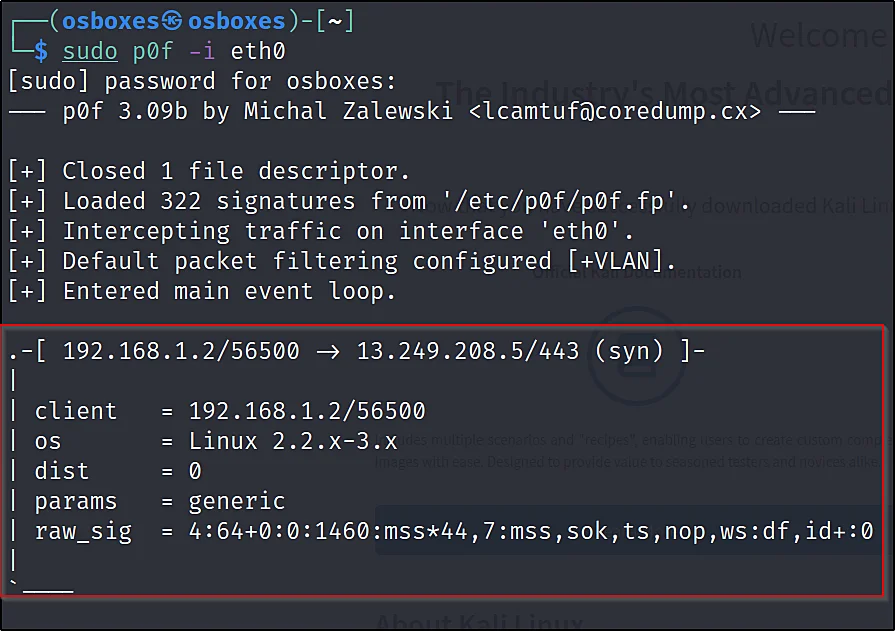
Conclusion
P0f is an awesome tool for information gathering and most of the cybersecurity expert use this tool. Even I like the tool and what are you waiting for just go and work with the tool.
Advertisment
Also Read: Information gathering using google dorks or google hacking
Also Read: Shodan full tutorial




