Introduction
Hello, everyone! Welcome to techyrick. Today, I’m going to show you how to track anyone’s IP using Transparent Images! Yes, you heard that right. We’ll begin by understanding the concept thoroughly and then move on to a step-by-step guide on how to use it.
While you could technically do this manually using custom-developed payloads, there’s a much easier way. I’ll walk you through it today with simple steps you can follow. So, let’s get started with our learning journey.
Understanding Canarytokens
Canarytokens serve as digital traps for your computer systems. They operate by monitoring specific actions, such as file reads, database queries, process executions, or the identification of particular patterns in log files.
They’re akin to those tracking pixels in emails, except instead of monitoring opens, they track actions within your system.

What’s interesting is that we can employ Canarytokens to establish these traps in our everyday computer systems, somewhat akin to installing alarms in various areas of your house… quite amusing, if you ask me.
Now, why should you bother with these Canarytokens? Well, hackers sometimes infiltrate computer networks, and it’s something that happens to large corporations, governments, regular individuals—basically, everyone.
That aspect is understandable. However, what’s not acceptable is only discovering it much later, perhaps months or even years down the line, which can lead to disappointing and unpleasant surprises!
Canarytokens provide a free, simple, and quick method to promptly alert you if there’s any unauthorized activity in your systems. It’s akin to hackers inadvertently tipping their hand and letting you know of their presence.
- Web bug / URL token: Receive an alert when a URL is visited.
- DNS token: Trigger an alert when a hostname is requested.
- AWS keys: Get notified when an AWS key is utilized.
- Azure Login Certificate: Receive alerts when an Azure Service Principal certificate is used for login.
- Sensitive command token: Be alerted when a suspicious Windows command is executed.
- Microsoft Word document: Get notified upon the opening of a document in Microsoft Word.
- Microsoft Excel document: Receive alerts when a document is opened in Microsoft Excel.
- Kubeconfig token: Trigger an alert when a Kubeconfig is employed.
- WireGuard VPN: Receive alerts when a WireGuard VPN client configuration is utilized.
- Cloned website: Be alerted when your website is cloned.
- QR code: Generate a QR code for physical tokens.
- MySQL dump: Get notified when a MySQL dump is loaded.
- Windows folder: Receive alerts when a Windows Folder is browsed in Windows Explorer.
- Log4Shell: Trigger alerts when a log4j log line is vulnerable to CVE-2021–44228.
- Fast redirect: Receive alerts when a URL is visited and the user is redirected.
- Slow redirect: Trigger alerts when a URL is visited, providing additional information is obtained.
- Custom image web bug: Be alerted when an image you uploaded is viewed.
- Acrobat Reader PDF document: Receive alerts upon the opening of a PDF document in Acrobat Reader.
- Custom exe / binary: Trigger alerts when an EXE or DLL is executed.
- Microsoft SQL Server: Get notified when MS SQL Server databases are accessed.
- SVN: Receive alerts when someone checks out an SVN repository.
- Unique email address: Trigger alerts when an email is sent to a unique address.
Step-by-Step Usage
Head over to canarytokens.org and select your Canarytoken. Think of it as setting a digital trap. Enter an email address where you’d like to receive notifications, and jot down a note to help you remember where you’ve placed it.
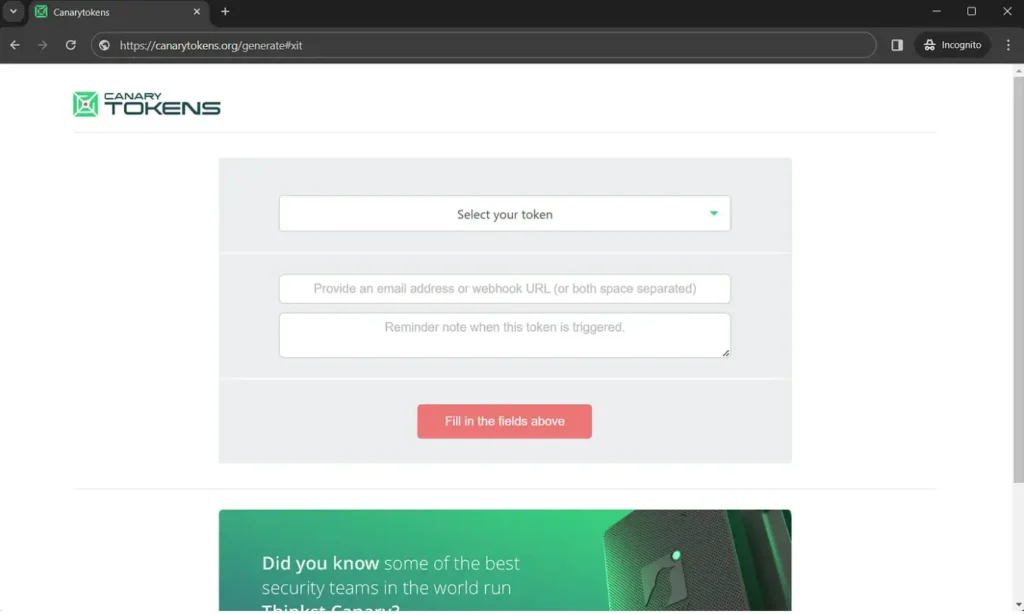
Sure, let’s create a Fast redirect Canarytoken. Think of it as crafting a secret link that will sound the alarm if anyone clicks on it. In this blog, I’ll demonstrate how to set up a Fast redirect as an illustration.
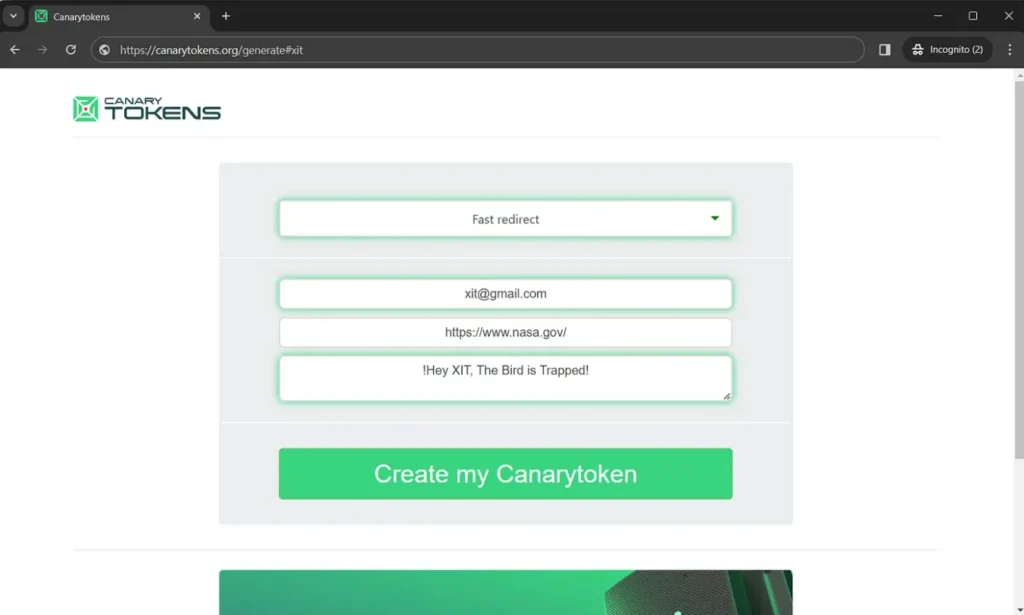
Once you’ve generated the Canarytoken, place it in a strategic location and send it to your target. This could be within an email, a document, or even embedded in an image. If the target interacts with it, you’ll receive an email notification, signaling that something is amiss.
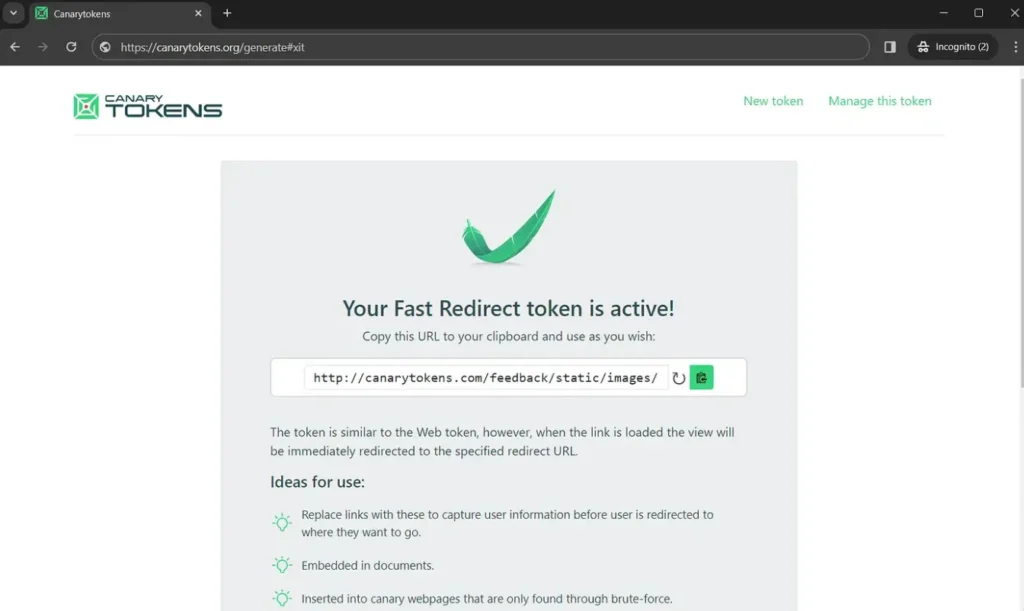
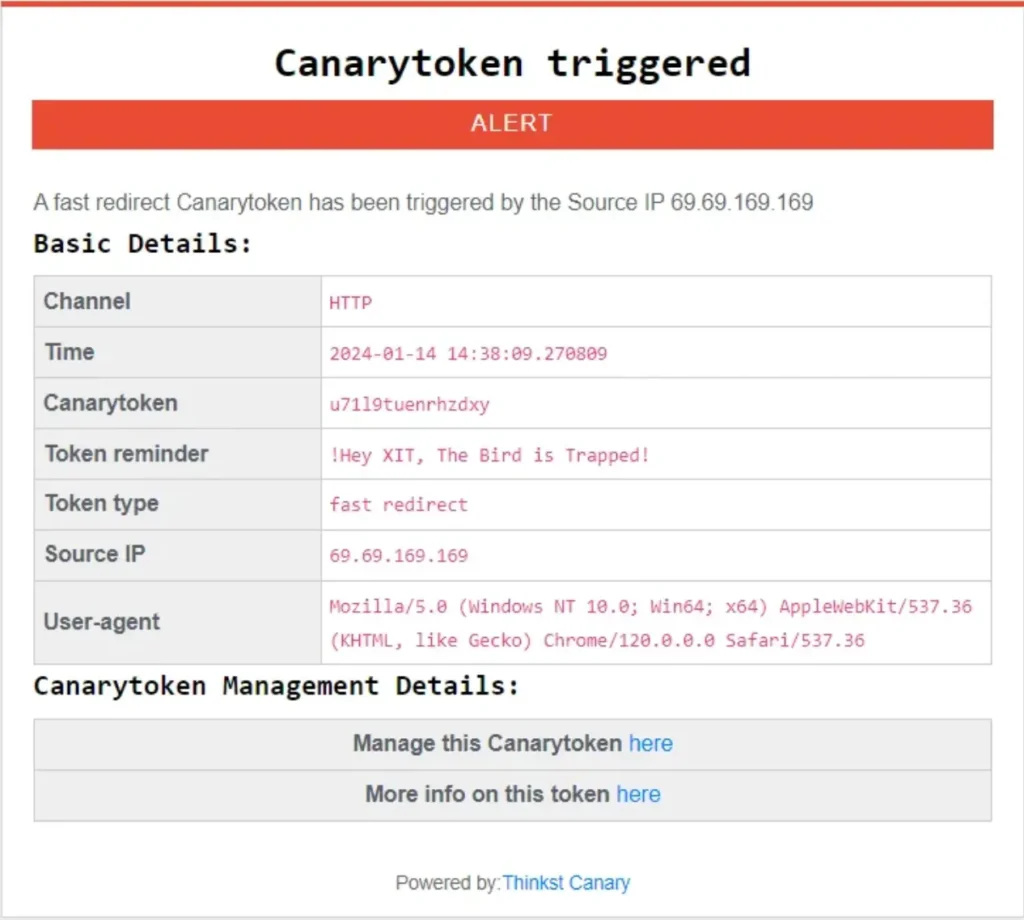
Clicked..

If your target accesses the URL or file, similar to the example provided earlier, your token becomes activated and triggers an alert via email or webhook, as demonstrated below:
You can rename the generated PDF, Excel, or Word document without impacting its functionality.




