Introduction
In this post, you will learn how to exploit weak service file permissions for privilege escalation. If you have any questions, feel free to comment down below.
In Windows environments, it’s common to find services running with SYSTEM privileges that lack proper permissions set by the administrator.
This misconfiguration can lead to a user having inappropriate permissions over the service itself, the folder where the service’s binary is stored, or even both. Such vulnerabilities are frequently found in third-party software and can serve as a point for escalating privileges from a standard user to an administrator.
Service File permissions Weakness
Did you know that weak service file permissions can be a big security risk? Imagine someone with bad intentions using this flaw to run their own harmful programs. They do this by taking over the files (binaries) that services use to operate.
Here’s how it works: In Windows, services often run with SYSTEM-level privileges, which are very powerful. If the permissions for these services aren’t set properly, someone might be able to replace the legitimate files the service uses with their own malicious files. When the service starts, it would then run the malicious file instead of the original, but with the same high-level permissions.
For example
Think about a tool like CCleaner. If you, as a user, have the ability to change the files CCleaner uses, and CCleaner runs with SYSTEM permissions, you could replace its files with something harmful. The next time CCleaner runs, your harmful file would execute with SYSTEM-level permissions. This could allow a hacker to gain control over the system or keep their malicious software running over a long time.
It’s a pretty sneaky way for someone to take control of a system, right? That’s why it’s so important to ensure permissions are set correctly on all service-related files and directories. This helps prevent unauthorized users from making these kinds of changes.
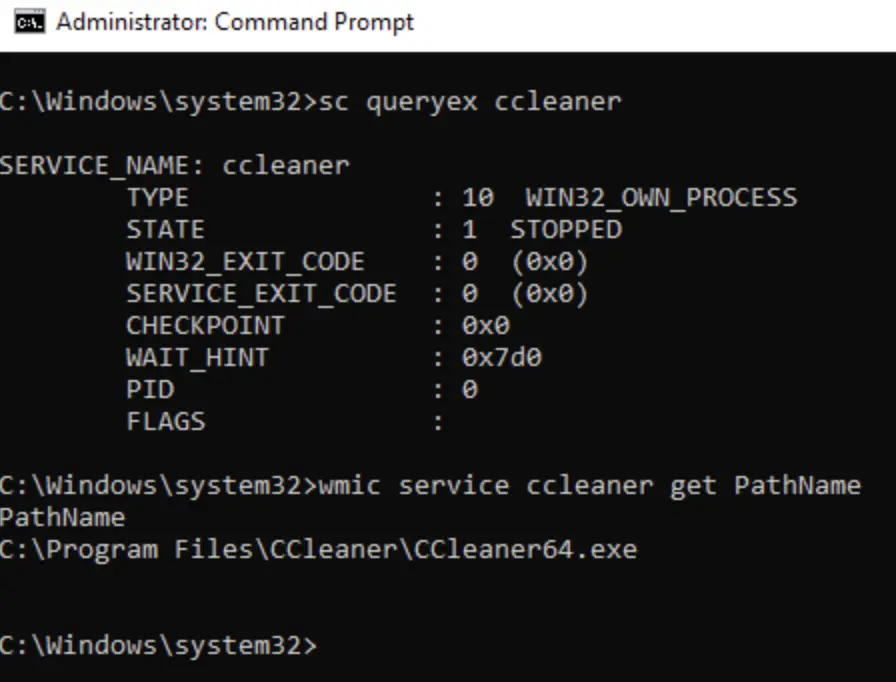
If a user has permission to change the binPath, they can easily point it to a malicious payload. When the service starts, it will run the malicious payload instead.
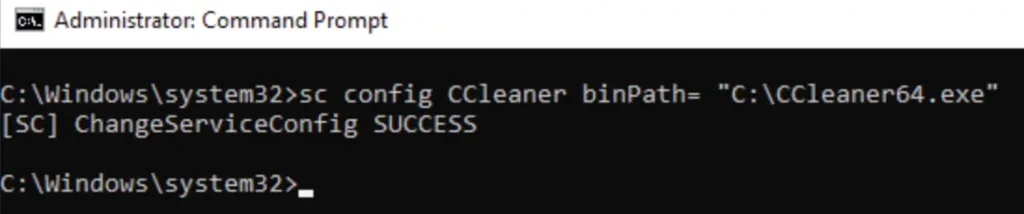
If a user has permission to change the binPath, they can simply redirect it to a malicious payload. When the service starts, it will run the malicious file instead.

Conclusion
In conclusion, the vulnerability stemming from weak service file permissions poses a significant threat to system security.
By allowing users to manipulate the binPath configuration, attackers can seamlessly substitute legitimate files with malicious payloads, ultimately granting them unauthorized access and potential control over the system.
It’s imperative for administrators to meticulously manage permissions on service-related files and directories to mitigate these risks effectively.
Vigilance in maintaining robust security measures is paramount to safeguarding against such exploitation and preserving the integrity of digital infrastructures.
Also Read: Weak Service Permission | Windows Privilege Escalation


