Introduction
In this post, Let’s see about wfuzz. The wfuzz stands for web fuzzing. Fuzzing is a user can send a similar request multiple times to the server with a certain section of the request changed. When that certain section is replaced by a variable from a list or directory, it is called fuzzing.
Video
What is Wfuzz ❓
Wfuzz is an open-source tool for checking the security of web applications and is used to launch brute-force attacks against web applications.
By enabling them to fuzz input parameters of the web application, it is intended to assist penetration testers of web applications in identifying vulnerabilities.
The programme can identify various vulnerabilities, including XSS (cross-site scripting) flaws and file inclusion, command execution, and SQL injection flaws.
Wfuzz Installation
The wfuzz comes pre-installed in Kali Linux and in Parrot So, You no need to worry about the installation process.
Anyways install wfuzz. You can enter the below command.
sudo apt-get update sudo apt-get install wfuzz
Who Developed Wfuzz
The wfuzz tool was developed by xavi mendez. Though he has created many repos only this wfuzz repo was very useful. Below are some of the important links.
How the Wfuzz works
Wfuzz is based on a simple concept: it replaces any reference to the FUZZ keyword with the value of a given payload.
A payload in Wfuzz is a source of data. This simple concept allows any input to be injected in any field of an HTTP request, allowing it to perform complex web security attacks in different web application components such as parameters, authentication, forms, directories/files, headers, etc.
Wfuzz Features
- Subdomain Fuzzing
- Directory Fuzzing
- Cookie fuzzing
- Header fuzzing
- HTTP OPTIONS fuzzing
How to use Wfuzz
If you have any doubts about this tool, comment below or watch the youtube video. Join our discord server and ask doubts and stay in touch with us.
Discord: https://discord.gg/uekQW7RQZ8
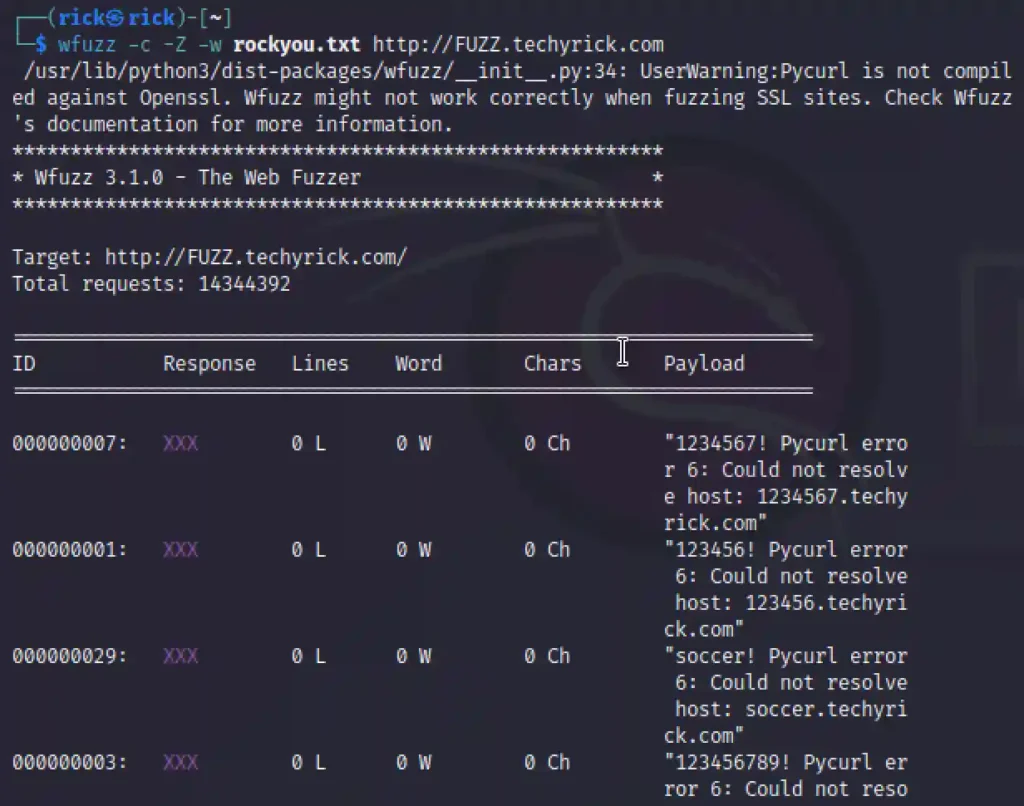
Subdomain Fuzzing
The subdomain fuzzing is pretty easy but to know the vulnerable subdomains used by the client we should use a proper wordlists.
Most of the subdomains will be using common words, So you can go with the rockyou.txt
wfuzz -c -Z -w rockyou.txt http://FUZZ.techyrick.com
- -c: colour output
- -Z: Ignores connection error
- -w: wordlists
- FUZZ: It’s parameter for fuzzing
Directory Fuzzing
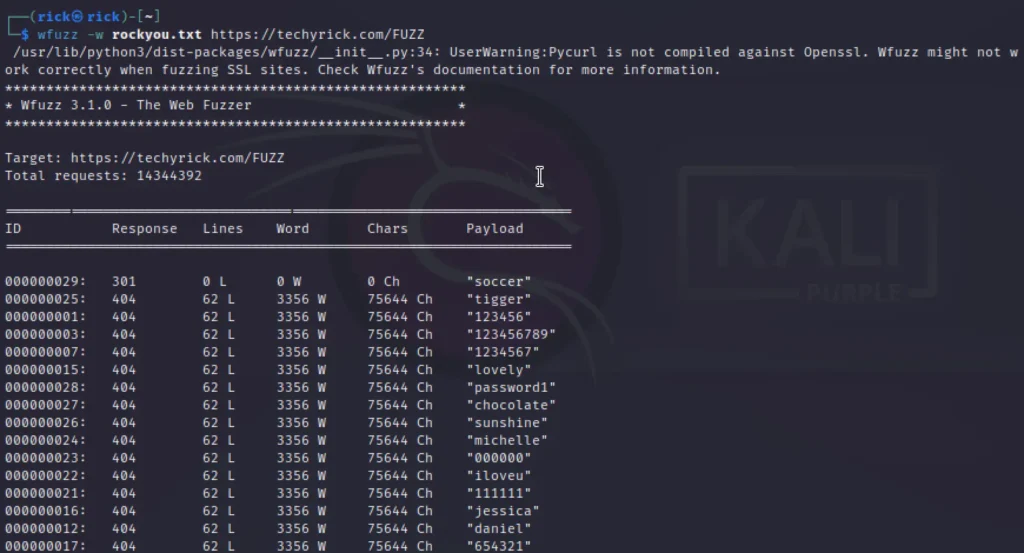
To do directory fuzzing, We have to add the FUZZ parameter at the end of the domain after a slash.
wfuzz -w rockyou.txt http://techyrick.com/FUZZ
Status Code
We can also specify the header code to filter the success response and the error response.
wfuzz -w rockyou.txt --sc 400,200,301 http://techyrick.com/FUZZ

Saving the Output
To save the FUZZing output we can use the -f command or go with the old school method using the arrow.
wfuzz -w rockyou.txt --sc 400,200,301 -f /home/rick/him.txt http://techyrick.com/FUZZ

Double Fuzzing
Precisely like a parameter in a cargo can be overcast utilizing the keyword “FUZZ” multitudinous fuzzing is also practicable by defining keywords.
FUZ2Z – 2nd parameter
FUZ3Z – 3rd parameter
FUZ4Z – 4th parameter
And each parameter can be distributed its own wordlist. The first “- w ” stands for first FUZZ. Alternate “- w ” holds for the alternate FUZ2Z and consequently on.
wfuzz -w rockyou.txt -w rockyou.txt https://FUZ2Z.techyrick.com/FUZZ
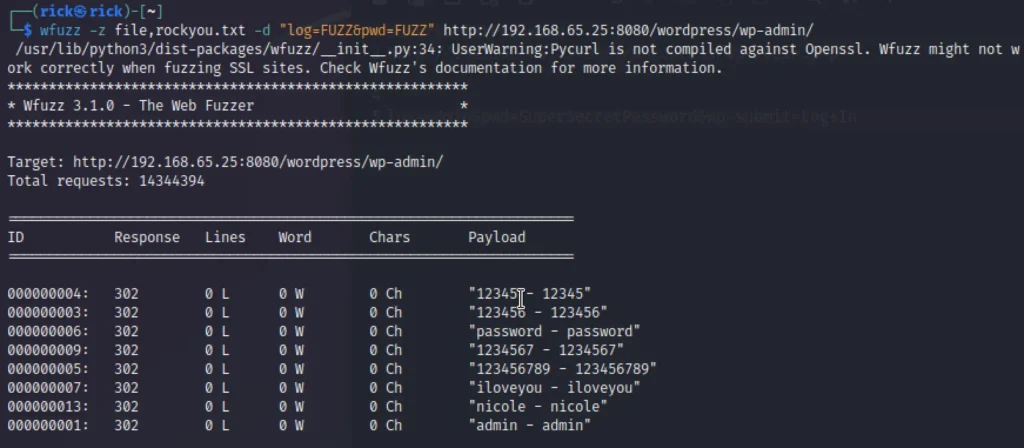
Login Bruteforce
To do a login bruteforce using wfuzz we need to know the login parameters, Here it’s log and pwd.
-d: Use post data
wfuzz -z file,rockyou.txt -d "log=FUZZ&pwd=FUZZ" http://192.168.65.25:8080/wordpress/wp-admin/
Conclusion
In my opinion wfuzz is a great tool for fuzzing and its very stealthy. If its used with burpsuite we may be amazed with the results.
An alternative for wfuzz is going to be fuff, Hope you like the post. See you in the next post ❤️
Also Read: Sqlmap Full Tutorial
Also Read: Dirb Full Tutorial


