Introduction
In this post, you will learn what is Ransomware? And how it works and as a bonus I have mentioned some famous Ransom ware attacks. I didn’t explain the famous Ransom ware attack in this post. I think by this time I would have written, go to the search bar and type Top 9 Ransom ware attacks.
What is Ransomware?
Ransomware is a malicious software created by cybercriminals to get some money through cryptos. From the name Ransom, we could understand this particular malware demands money. This ransomware malware encrypts users whole device or encrypts specific files alone. To decrypt, the user should pay the cybercriminal in cryptos and most probably you will not get back your file or device.

So, if you can’t decrypt the file or device, then you should probably throw in dustbins. Even in the popular colonial pipeline attack, the US government paid 5Million to the hackers.
Also Read: What is Botnet? How they work exactly!
How Ransomware works?
Great question! First, let’s see how ransomware enters your device? There are four possible ways for ransomware to enter into your device.
- Spam e-mail
- Spear Phishing
- Watering hole
- Scare ware
Mostly ransomware enters into users devices by some untrained employees. The cybercriminals who spread ransomware are doing targeted attacks. They mainly target retail shops, hospitals, Police departments, Utilities and state and local government.
So, the cybercriminals targets are only organizations and well-known places, but some individuals may get stuck into this attack! Very unlucky.
How ransomware works?
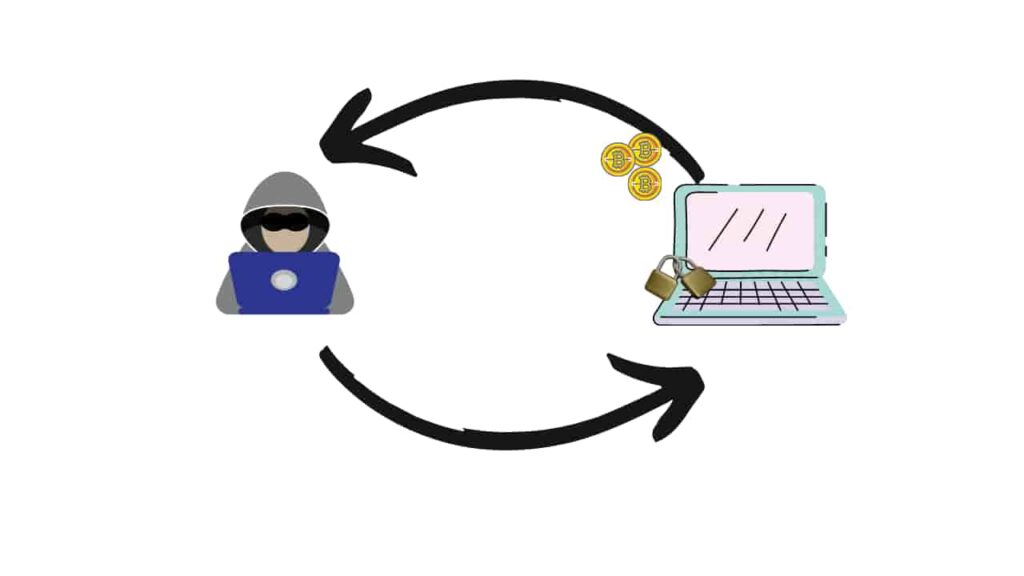
In the before paragraph, I have said how ransomware enters into a device and once it enters into a device it encrypts a particular file or the whole device. Initially, Ransomware encrypts only the user’s device, but later the cybercriminals found a crypto locker. Which encrypts a particular file.
Locker Ransomware:
Locker ransom ware encrypts your device and blocks some basic device functions. Once the malware enters, goes and interrupts the OS. And lock particular functions and the users either need the particular cryptographic key to recover the device. When I say, the device is encrypted. It will be encrypted in the form of ciphertext, to decrypt this we need the cryptographic key.
The key is not a real one, but we need the exact algorithm done while encryption, so we can decrypt the device.
Crypto Ransomware:
This crypto ransomware encrypts a particular file, later the cybercriminals understood encrypting the whole device is useless and started to encrypt the most needed file. The criminals can encrypt docs, videos, images. But not the basic computer functions.
In crypto ransom ware, you get a deadline you should have to pay the demanded ransom if not your file will be deleted or maybe those files will be sold in dark-web. This method also works by encryption and decryption method. Out of 100, you have 1 percent chance to recover your files if the criminal is goodhearted.
Also Read: What is Bot? How bot’s turn into botnet
Top 9 Ransomware attacks
- Sekhmet Ransom ware
- Tycoon Ransom ware
- Maze Ransom ware
- Ryuk Ransom ware
- SamSam Ransom ware
- Wanna Cry Ransom ware
- Petya Ransom ware
- AIDS Trojan or First Ransom ware
- CryptoLocker Ransom ware
Conclusion
In summary, I recommend you to not pay the ransom and even if you pay you are not going to get back your data. So, always recover your data in an offline system. Don’t visit unwanted sites and click unwanted links.
Also Read: What is Adware?
Also Read: What is CAPTCHA?




